Embedded 'wood horse' dedicated network game system, and virus inquiring and killing method
A technology for online games and Trojan horses, which is applied in the field of online game systems, can solve the problems of not strong pertinence in checking and killing Trojan horses, ineffectiveness of Trojan horse viruses, and untargeted queries, so as to increase directness and convenience, and highly efficient antivirus time, the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
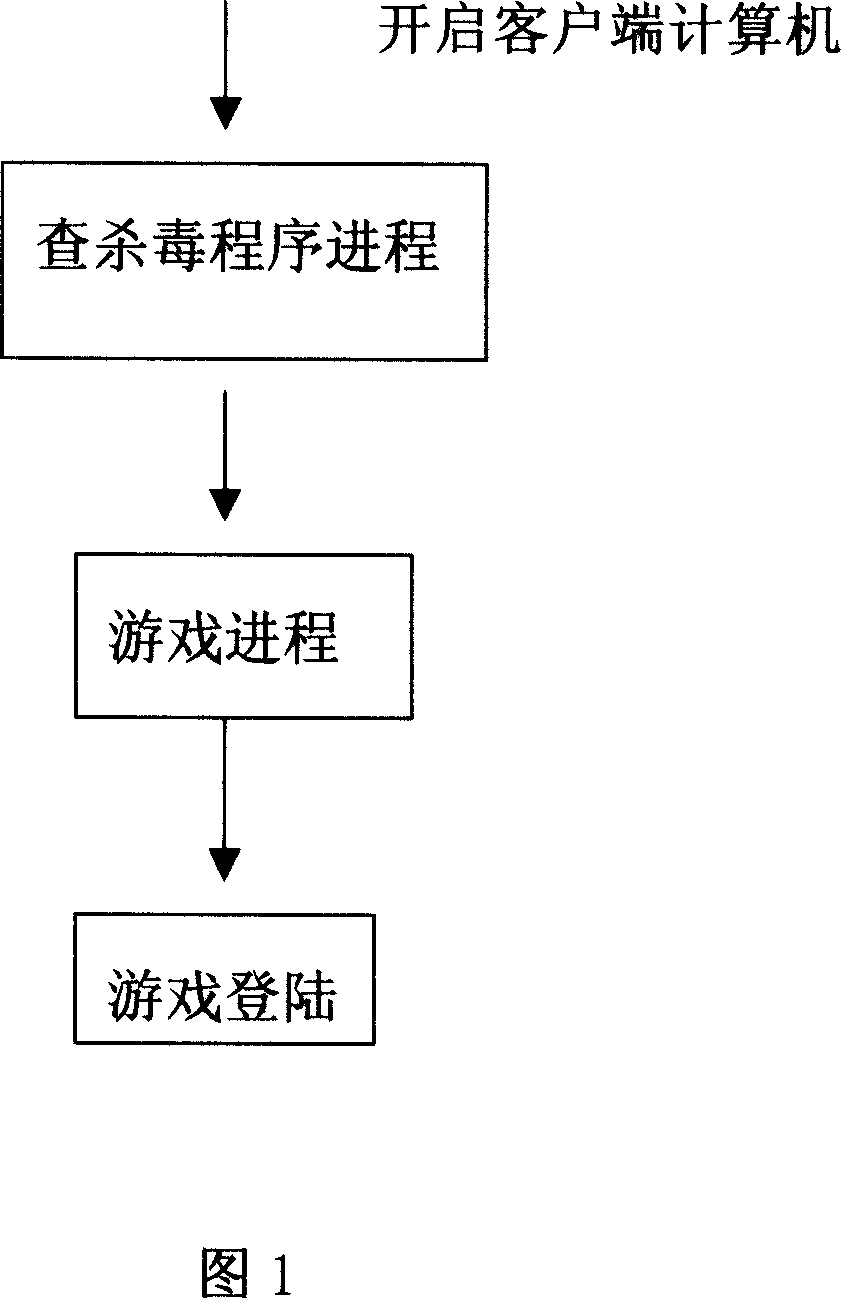
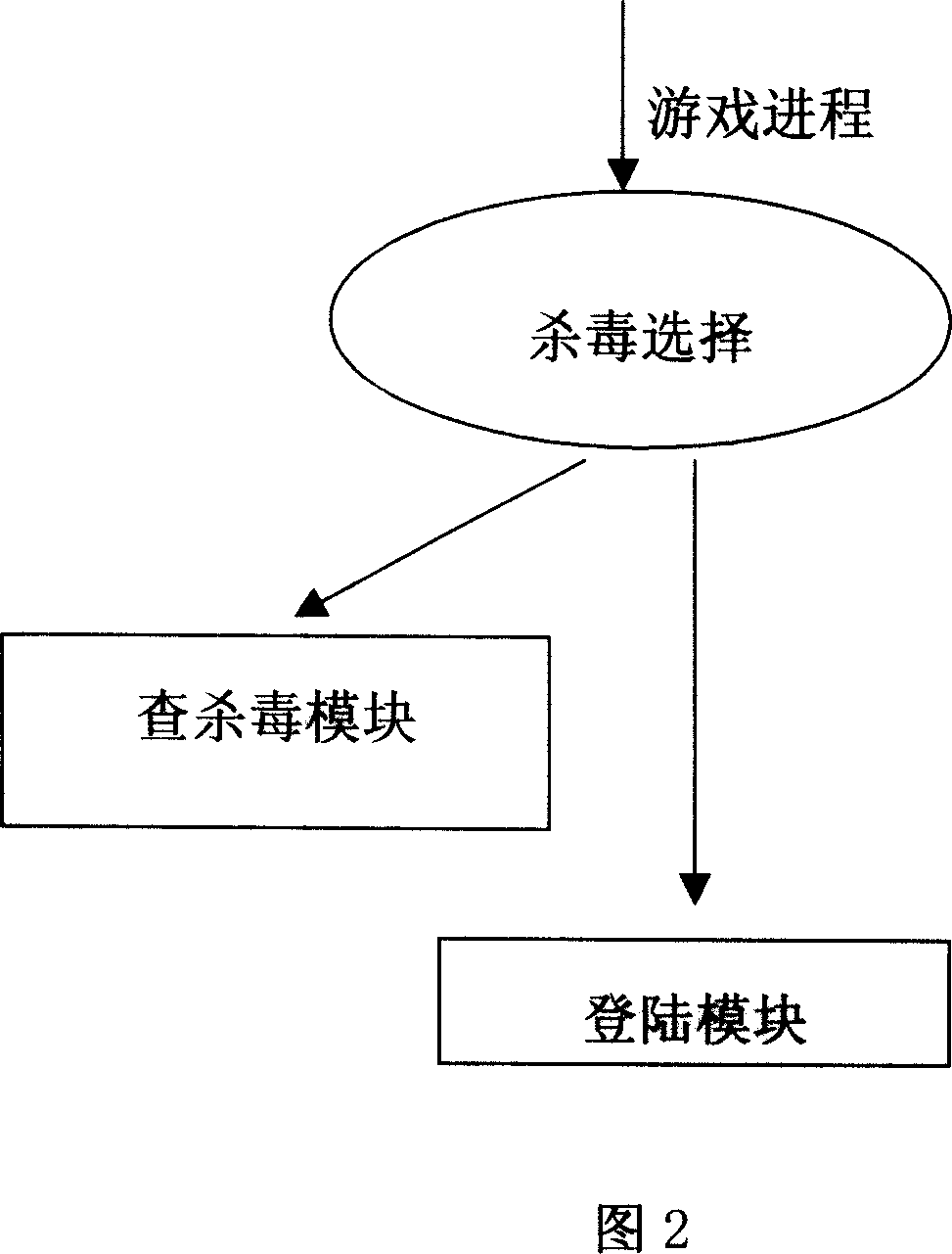
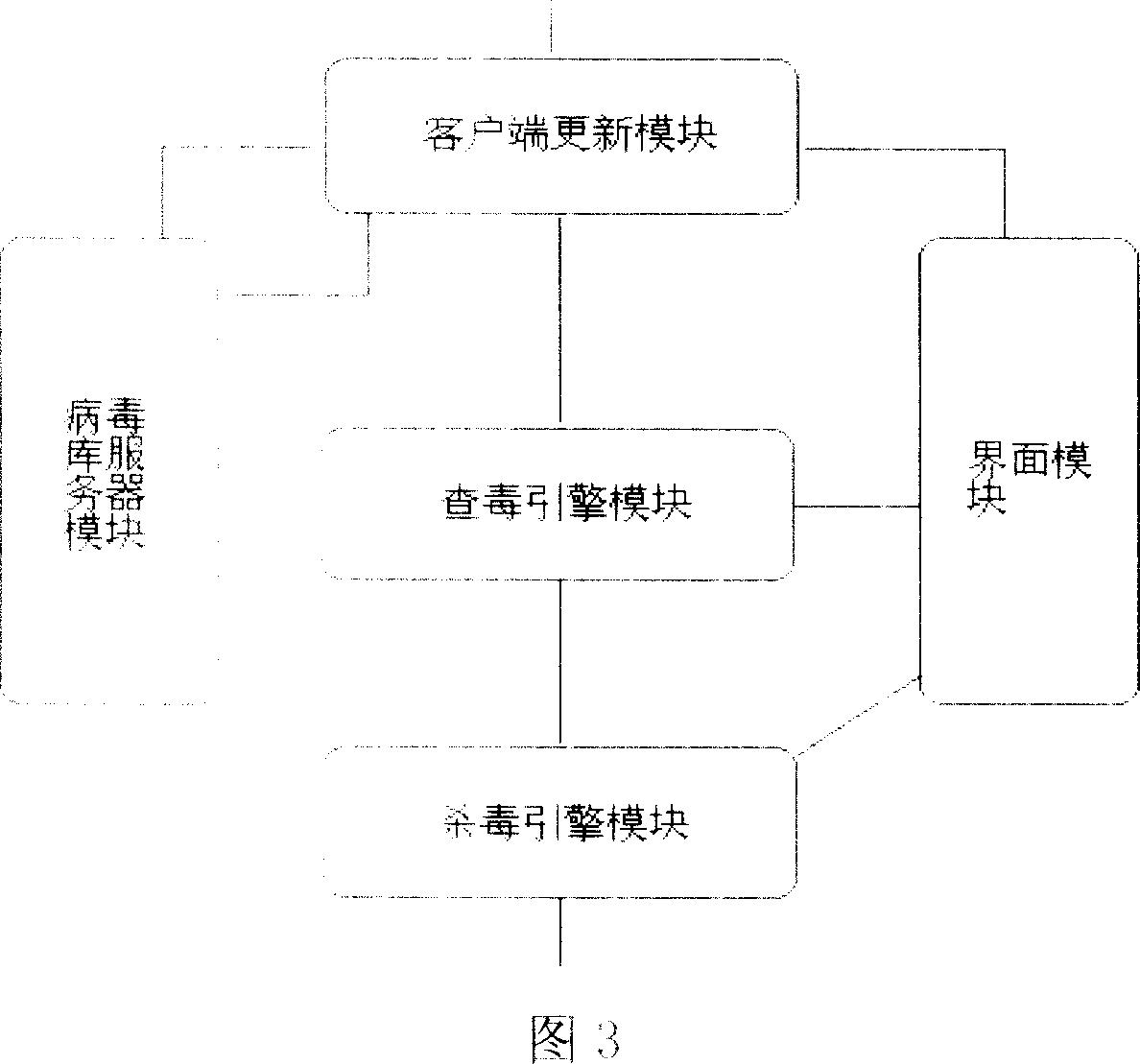
[0032] An online game system with built-in Trojan horse killing disclosed by the present invention includes a server and a plurality of clients, data interaction is performed between the server and each client through a communication network, and each client can be played by a player Control; each client includes an input device connected to each other, a display device, and a host computer; the server includes a single or multiple CPUs and memory devices, wherein:
[0033] The online game system includes a game starting module, a virus checking module and a login module, the game starting module and the virus checking module run as the same process of the online game, and the game starting module and the virus checking module share the same code area and the data area; when the player starts the game software, the antivirus module is turned on at the same time for virus inspection and protection processing; after the game system client end virus inspection and protection proce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com