Secret key processing method for switching between different mobile access systems
A processing method and access system technology, applied in the field of mobile communications, can solve problems such as increased handover delay, unresolved key processing issues, and impact on user service continuity, and achieve the effect of improving configuration management efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0044] Example 1: UE handover from EUTRAN to non-3GPP IP access network
[0045] like Figure 4 In this case, the following processing is included:
[0046] Step S402 (step 1), the UE reports its non-3GPP IP access network access capability information after attaching through EUTRAN;
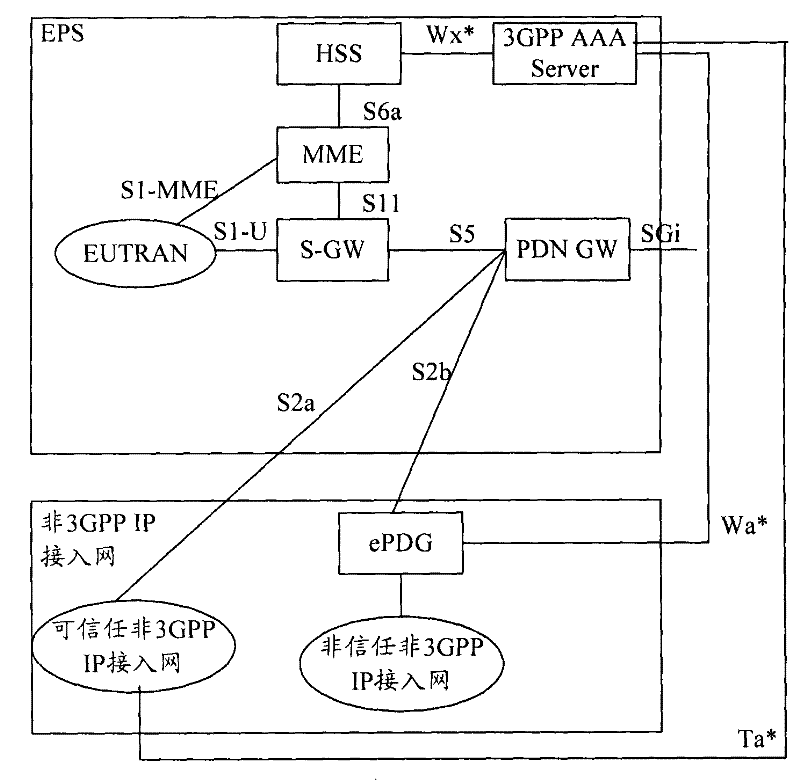
[0047] Step S404 (step 2), if the UE supports non-3GPP IP access network access, then after the authentication is successful, the HSS and the UE use the key derivation function and the access security management entity key (K ASME ), respectively derive the master key (MK) required by the non-3GPP IP access network; wherein, when the UE supports non-3GPP IP access network access, and the UE is a non-3GPP IP access network subscriber, derive the non-3GPP IP access network The MK required by the 3GPP IP access network;
[0048] Step S406 (step 3), the HSS sends the MK to the 3GPP authentication, authorization and accounting server (3GPP AAA Server), and the UE and the 3GPP AAA Server use the MK...
example 2
[0064] Example 2: UE handover from non-3GPP IP access network to EUTRAN
[0065] like Image 6 In this case, the following processing is included:
[0066] Step S602 (step 1), the UE reports its own EUTRAN access capability information after initializing access through the non-3GPP IP access network;
[0067] Step S604 (step 2), if the UE supports EUTRAN access, after the authentication is successful, the HSS and the UE use the key derivation function and the master key (MK) and public land mobile network identity (PLMN) generated during the authentication process, respectively K needed to export EUTRAN ASME ; Among them, only when the UE supports EUTRAN access and the UE is a EUTRAN subscriber, the K required by EUTRAN is derived ASME ;
[0068] Step S606 (step 3), the HSS sends K ASME Sent to MME, when UE and MME switch to EUTRAN, use K ASME ; Specifically, the UE initiates an attach request to the MME, which includes deriving the K ASME information; the MME requests ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com