Method, device and system for generating forwarding address and improving route optimization security
A care-of address and security technology, which is applied in the field of generating care-of addresses and improving the security of routing optimization, can solve problems such as increased communication delay, reduced data transmission security, forged BU messages, etc., and achieves the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
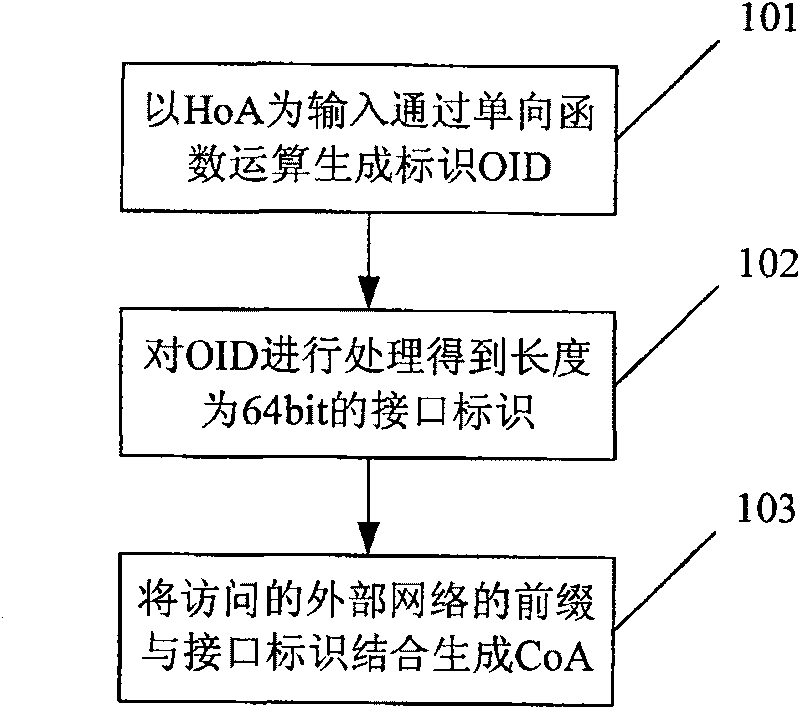
[0077] see figure 2 , the embodiment of the present invention provides a method for generating a care-of address, which specifically includes:
[0078] Step 101: taking the HoA of the MN as an input to generate an OID through a one-way function operation.
[0079] Among them, the formula for performing calculations using the one-way function PRF (Pseudo Random Function) is as follows:
[0080] OID = PRF(Expression);
[0081] Wherein Expression can be HoA of MN, also can be the combination of network prefix (SubnetPrefix) and HoA of the external network visited by MN; PRF is a one-way cryptographic function, it can be MD5, SHA-1, SHA256 or AES-XCBC - One-way functions such as PRF. So the above formula can have various forms, for example:
[0082] OID = SHA-1(HoA);
[0083] Or OID=MD5(HoA|Subnet Prefix) and so on.
[0084] Step 102: After generating the OID, the MN processes the OID to obtain an interface ID (Interface ID) with a length of 64 bits.
[0085] If the length...
Embodiment 2
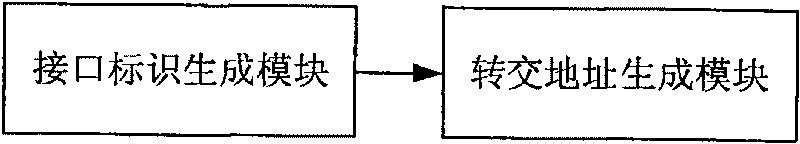
[0100] see image 3 , an embodiment of the present invention provides a device for generating a care-of address, which specifically includes:
[0101] (1) an interface identification generation module, used to generate an interface identification through a one-way function operation with the home address of the mobile node as input;
[0102] (2) A care-of address generating module, used to combine the interface identifier generated by the interface identifier generating module with the prefix of the external network accessed by the mobile node to generate a care-of address.
[0103] The interface identification generation module may specifically include:
[0104] 1) a combination unit, for combining the prefix of the external network visited by the mobile node with the home address of the mobile node;
[0105] 2) The generation unit is used to use the data obtained after the combination unit is combined as an input, and generate an interface identifier through a one-way func...
Embodiment 3
[0117] see Figure 4 , the embodiment of the present invention provides a method for improving the security of route optimization, which specifically includes the following steps:
[0118] Step 201: The MN uses the HoA as an input to generate an interface identifier through a one-way function operation.
[0119] Step 202: The MN combines the interface identifier with the prefix of the external network accessed by the MN to generate a CoA.
[0120] Further, duplicate address detection can also be performed on the generated CoA, that is, it is judged whether the generated CoA is the same as the IP address already used in the network, if they are the same, that is, an address conflict is found, and the interface identification Interface ID is regenerated according to the following steps, And then regenerate a usable CoA:
[0121] Modify the value of the start bit n used for the first time, and increase the increment on the original basis, that is, n=n+increment, where the incre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com