Method and wireless network controller for enabling encryption in call establishment process
A technology for call establishment and encrypted parameters, which is applied in wireless communication, communication between multiple stations, security devices, etc., can solve the problems of running water and data that cannot be analyzed by the other party, so as to avoid running water and ensure synchronization performance and guarantee the voice quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
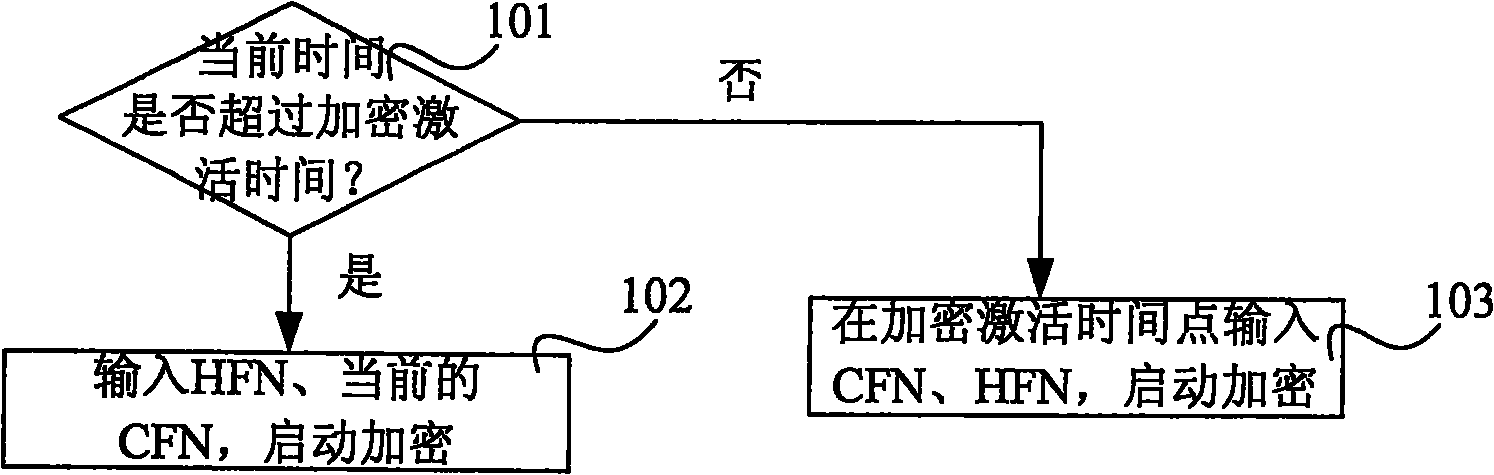
[0033] figure 1 The flow chart of Embodiment 1 of the method for starting encryption during the call setup process of the present invention includes:
[0034] Step 101: After the RNC receives the "RB SETUP COMPLETE" message sent by the terminal, the RNC calculates the encryption activation time provided by the terminal according to the HFN and CFN contained in the "RB SETUP COMPLETE" message, and compares it with the time maintained by itself to judge Whether the current time exceeds the encryption activation time provided by the "RB SETUP COMPLETE" message; if so, it indicates that the terminal has started encryption, and the RNC executes step 102; otherwise, it indicates that the "RB SETUP COMPLETE" message is not delayed, and executes step 103.
[0035] Step 102: The RNC uses the HFN in the "RB SETUP COMPLETE" message and the current CFN maintained by the RNC as encryption parameters to start encryption, avoiding the CFN cycle caused by the RNC waiting and causing the encr...
Embodiment 2
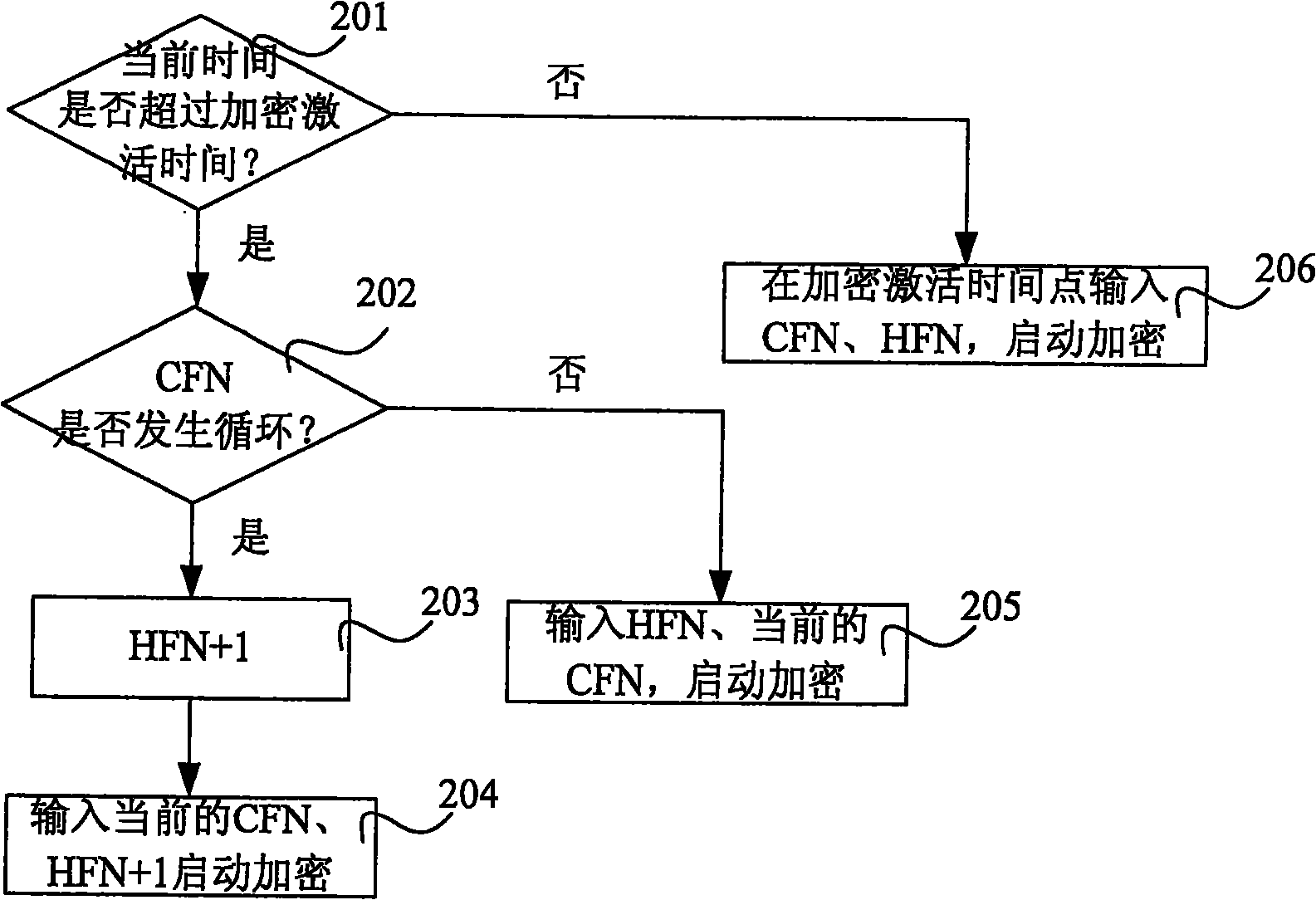
[0038] image 3 The flow chart of Embodiment 2 of the method for starting encryption during the call setup process of the present invention specifically includes the following steps:
[0039] Step 201: After receiving the "RB SETUP COMPLETE" message sent by the terminal, the RNC judges whether the current time exceeds the encryption activation time provided in the "RB SETUP COMPLETE" message; if so, execute step 202; otherwise, execute step 206.
[0040] Step 202: The RNC judges whether the CFN cycle occurs during the transmission of the "RB SETUP COMPLETE message. If so, in this embodiment, it is assumed that the CFN has cycled once, and step 203 is performed; otherwise, step 205 is performed.
[0041] Step 203: RNC calculates HFN according to the "START VALUE" value given in the "RB SETUP COMPLETE" message, and adds 1 to HFN. Then go to step 204 .
[0042]Step 204: Use HFN+1 and the current CFN maintained by the RNC as encryption parameters to start encryption. Such as ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com