Network access authentication method and its USIM card
A technology of network access and authentication algorithm, applied in the field of network access authentication method and its USIM card, to achieve the effects of low implementation cost, reduced security risk and less changes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] First, describe the characteristics of the present invention:
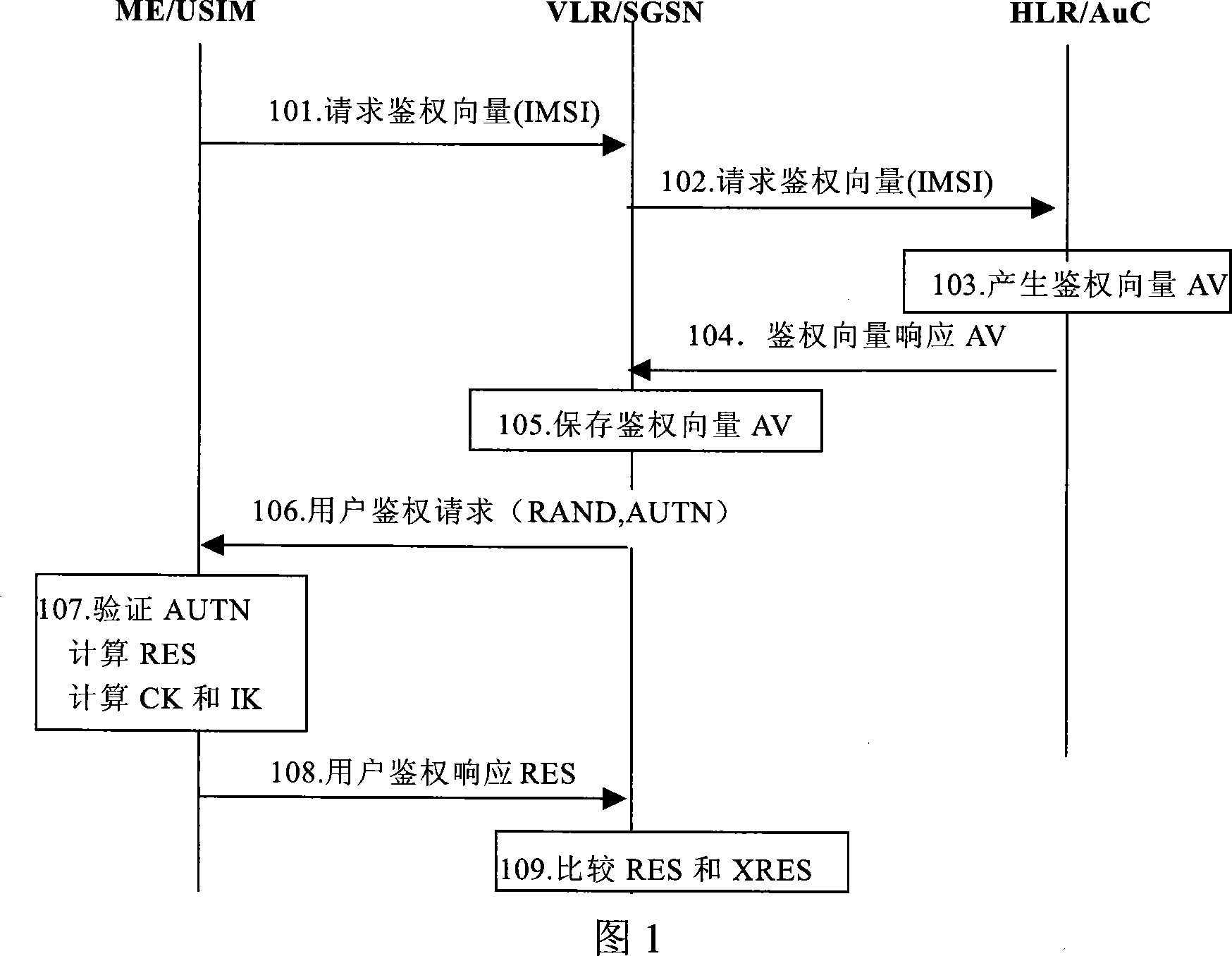
[0050] 1. A specific implementation method of 3G authentication algorithm negotiation and authentication key negotiation based on the existing 3G network access authentication process without adding new signaling or changing the existing authentication protocol is proposed.
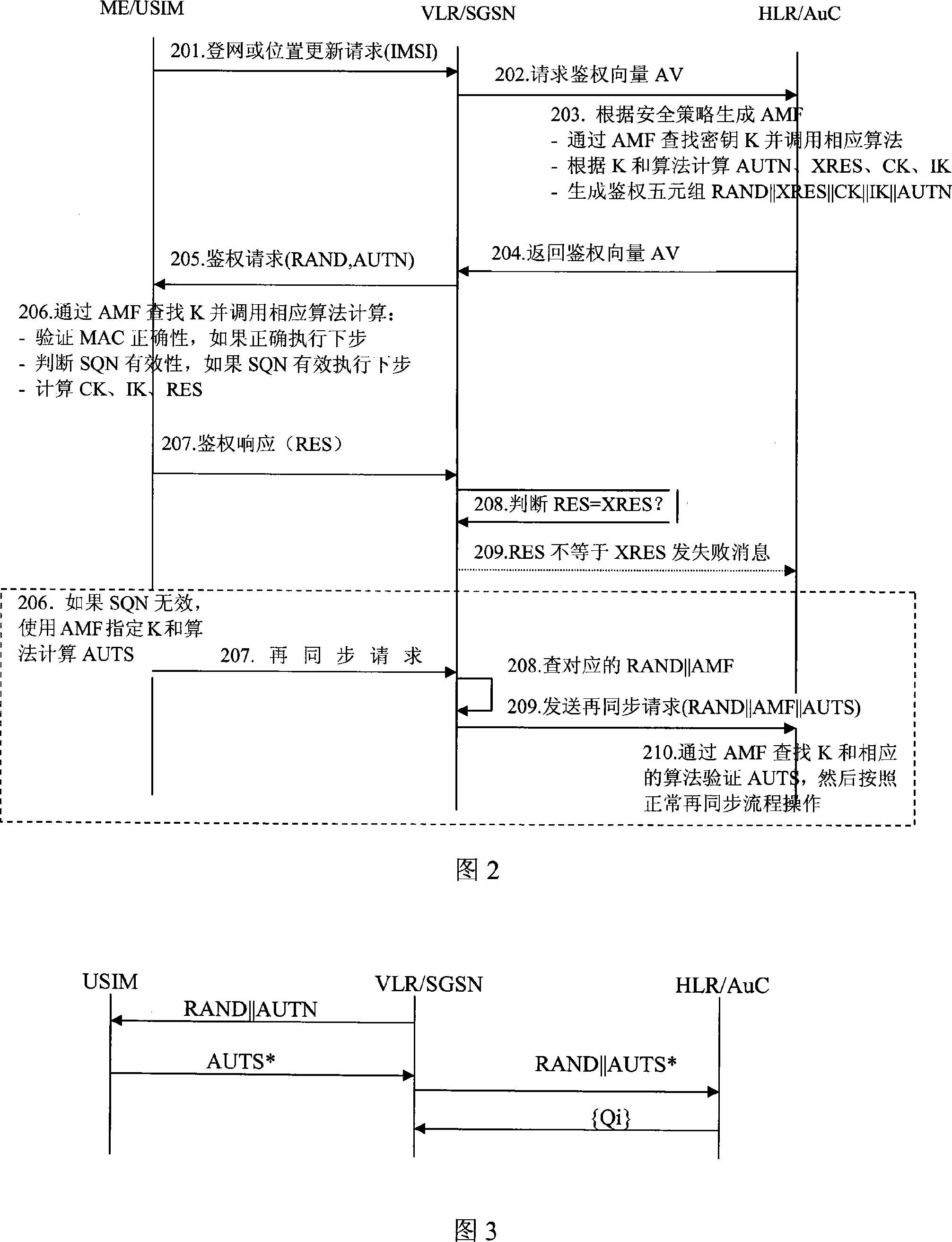
[0051] 2. In the process of 3G authentication and resynchronization, the USIM card and the network side can use the default key instead of the negotiated key for resynchronization authentication, thus ensuring complete consistency with the existing VLR / SGSN equipment.
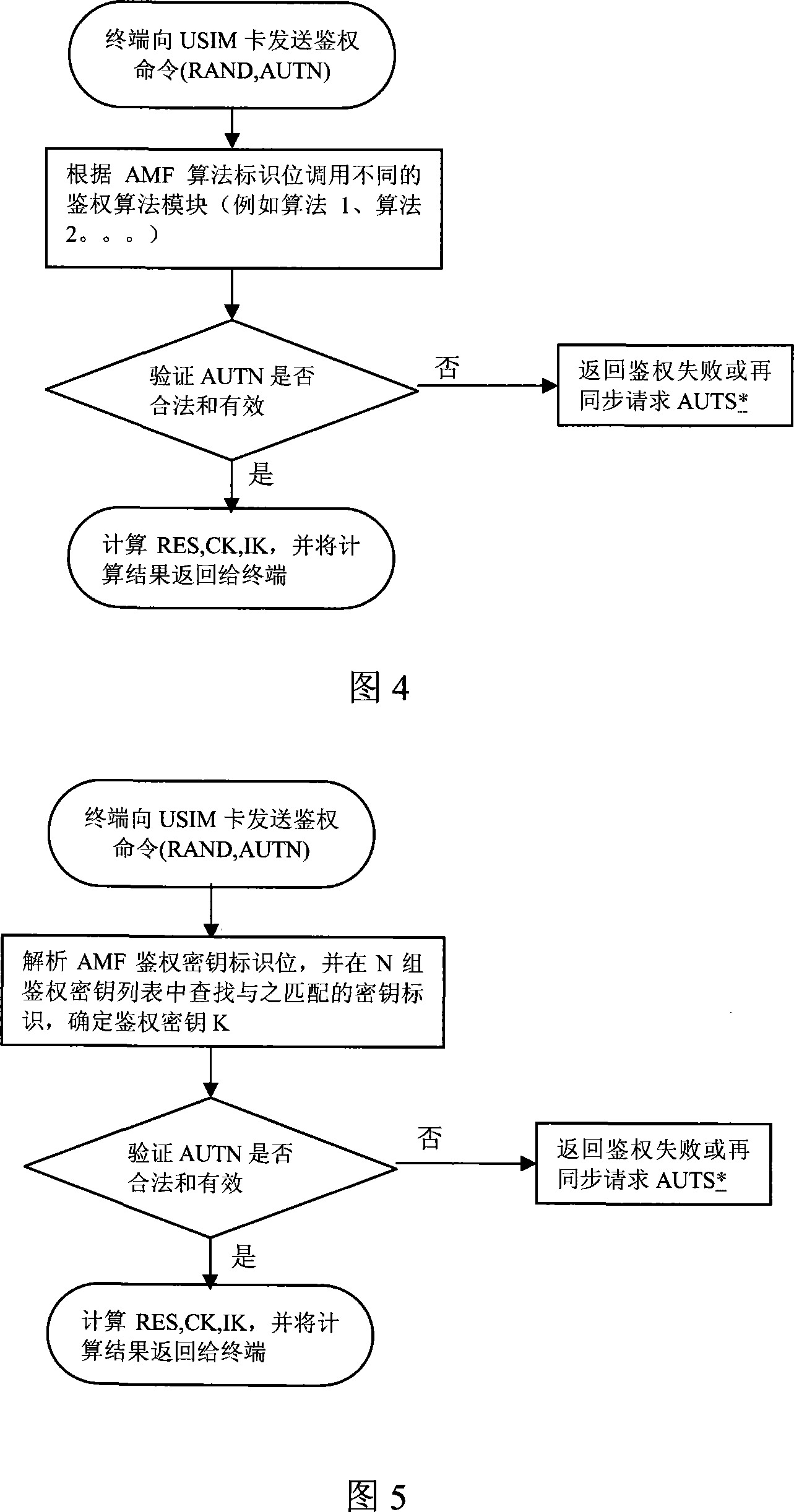
[0052] 3. This solution inherits the original 3G authentication protocol to the greatest extent. This solution only involves upgrading the authentication center AuC and the USIM card, and has no impact on the mobile terminal and other network elements.
[0053] 4. This solution also proposes a security strategy for key negotiation and algorithm negotiation. Operators c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com