Data transmission encryption method of MANET network
An encryption method and data technology, applied in the field of communication security, can solve problems such as the inability of a single node to undertake encrypted computing tasks, large communication delays, etc., and achieve the effects of balancing work load, reducing communication delays, and reducing computing loads
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
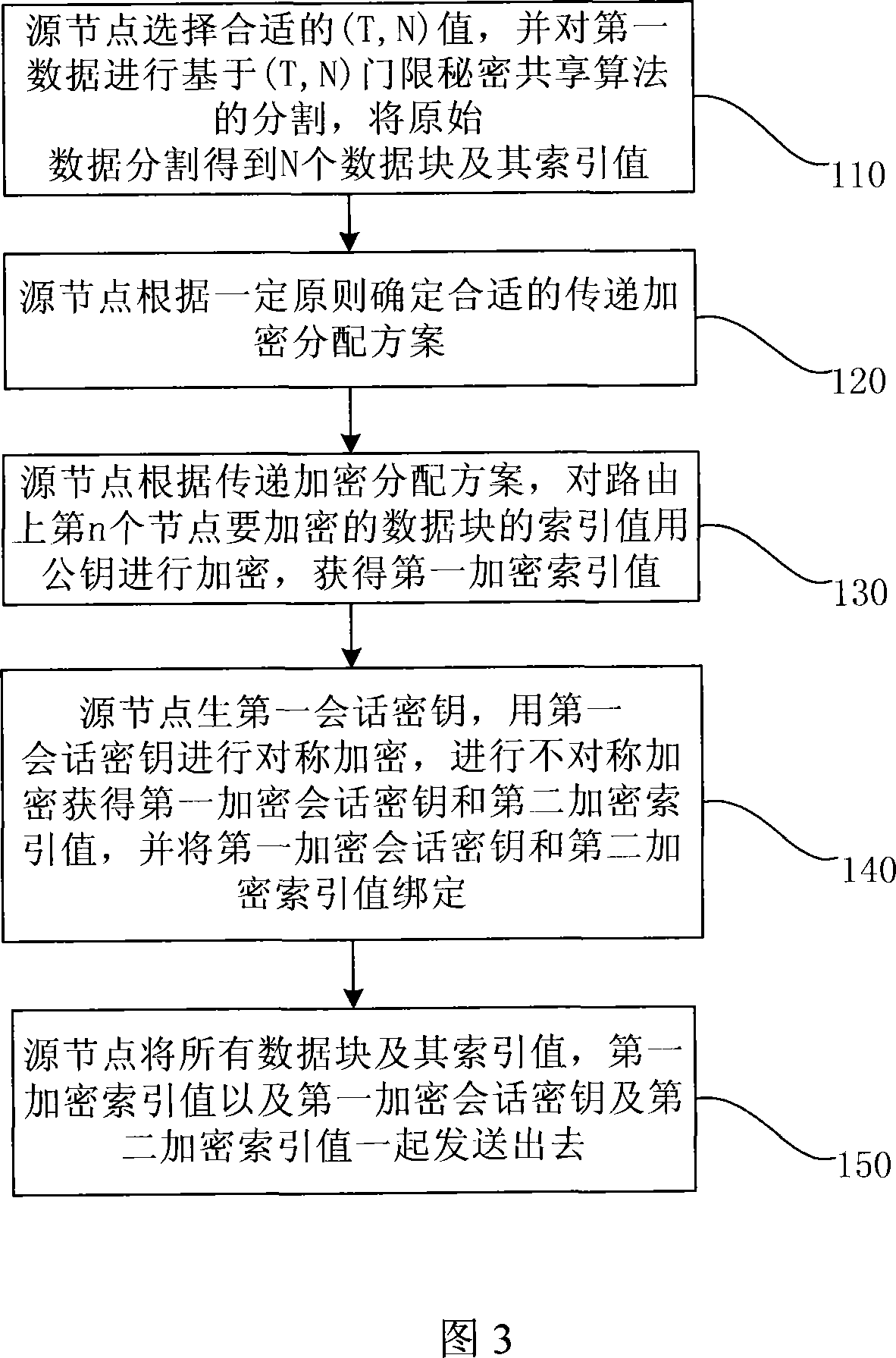
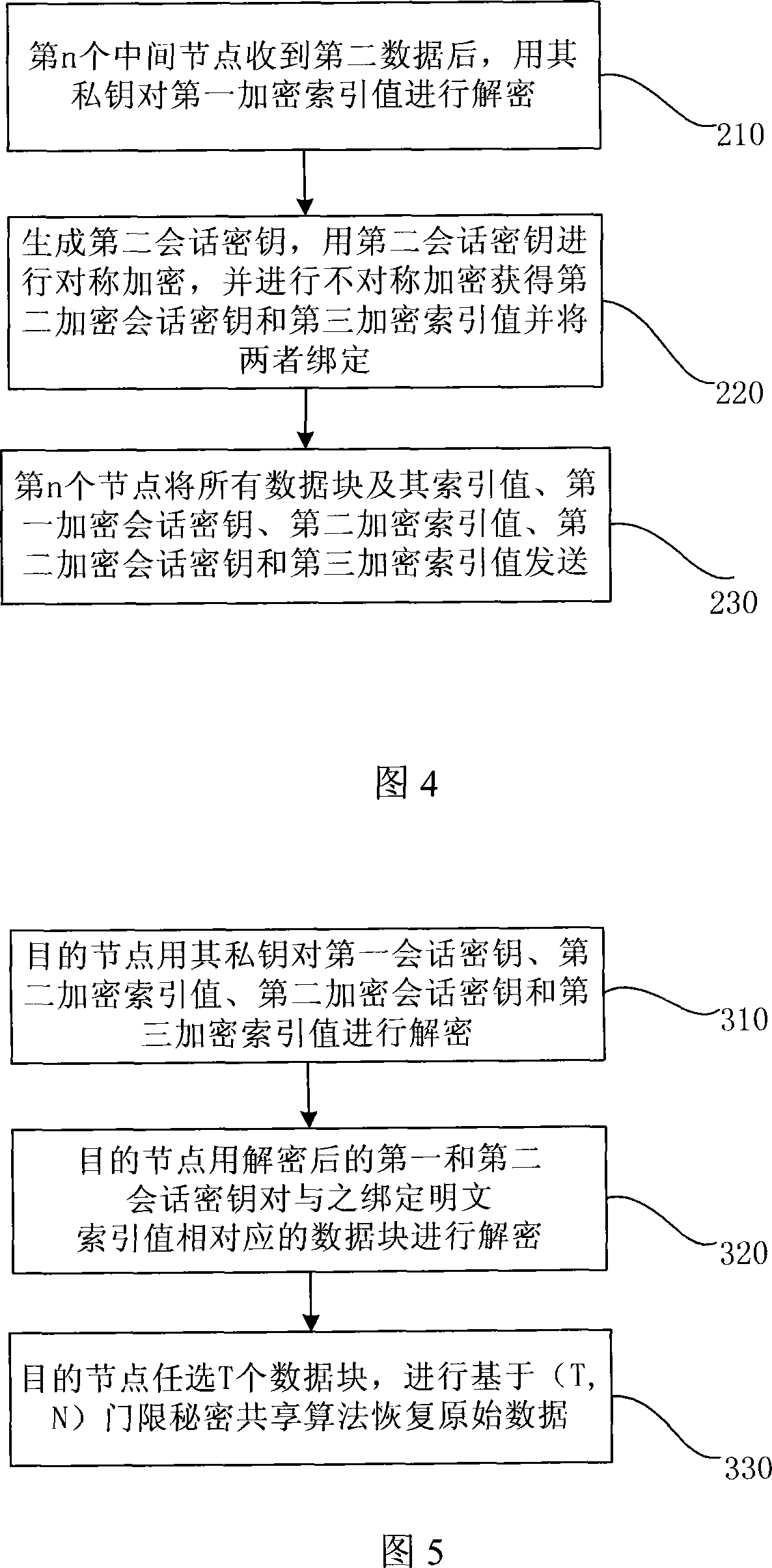
[0045] The invention provides a data encryption method in a MANET network. When two nodes in the MANET network need to communicate through a certain communication route, the communication source node (also called the first node), the destination node (also called The so-called second node) and the intermediate nodes on the communication route jointly perform step-by-step transfer encryption on the transmitted data to complete the entire encryption work.
[0046] The data transfer encryption method of the present invention will be described below by taking a specific data transmission process between communicating parties in a MANET network as an example.
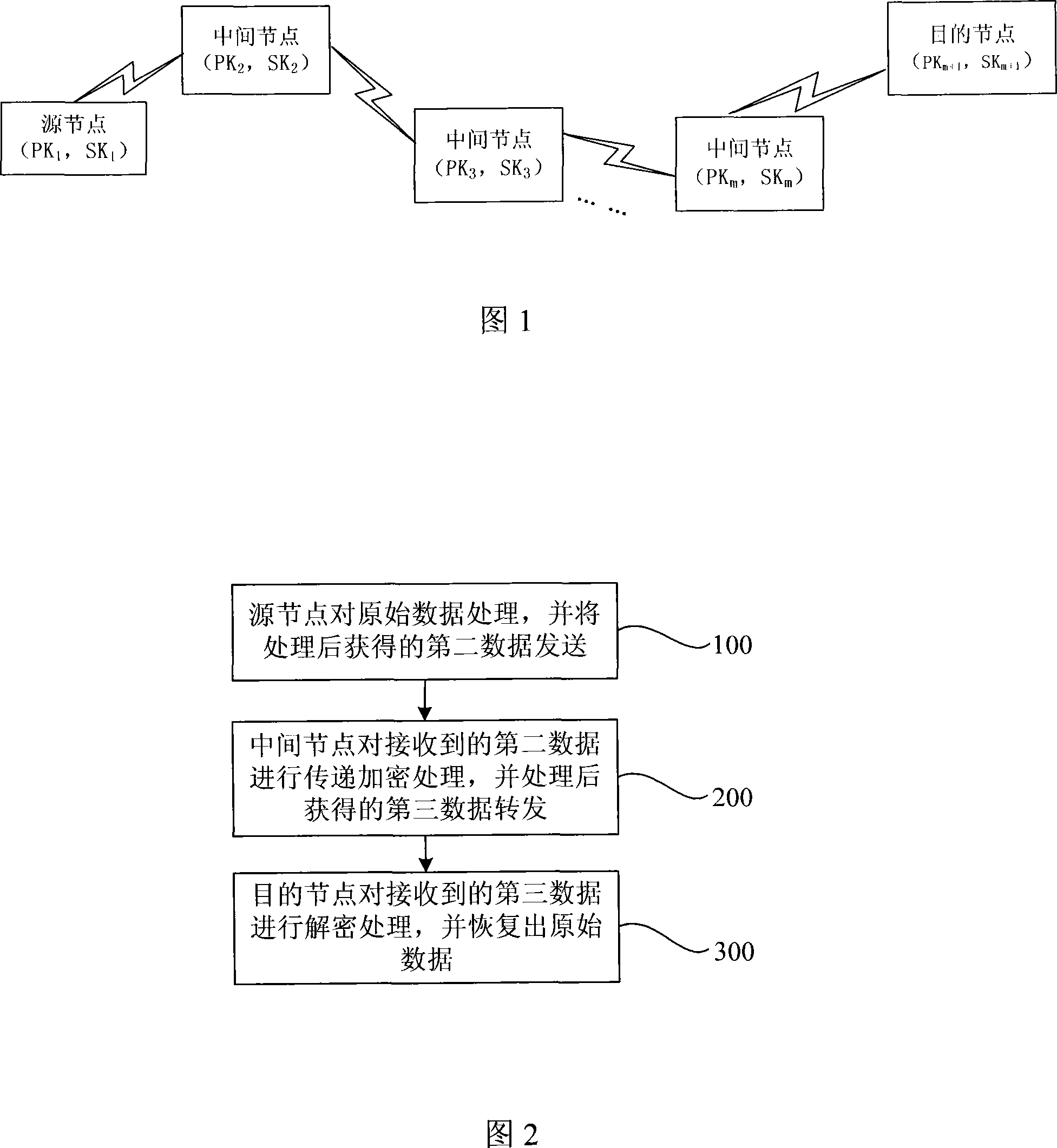
[0047] FIG. 1 is a schematic diagram of the communication route and the public-private key pairs owned by each node in the following example of the data transfer encryption method of the present invention. Among them, it is assumed that the transmission route between the two nodes has been determined through an effective sec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com