Method, device and system for accessing to certificate revocation list
A certificate revocation list and access certificate technology, applied in the field of digital certificate management, can solve the problem that the certificate client cannot obtain the certificate revocation list in time, and can not obtain the certificate revocation list in time, so as to avoid uncertainty and ensure normal processing. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
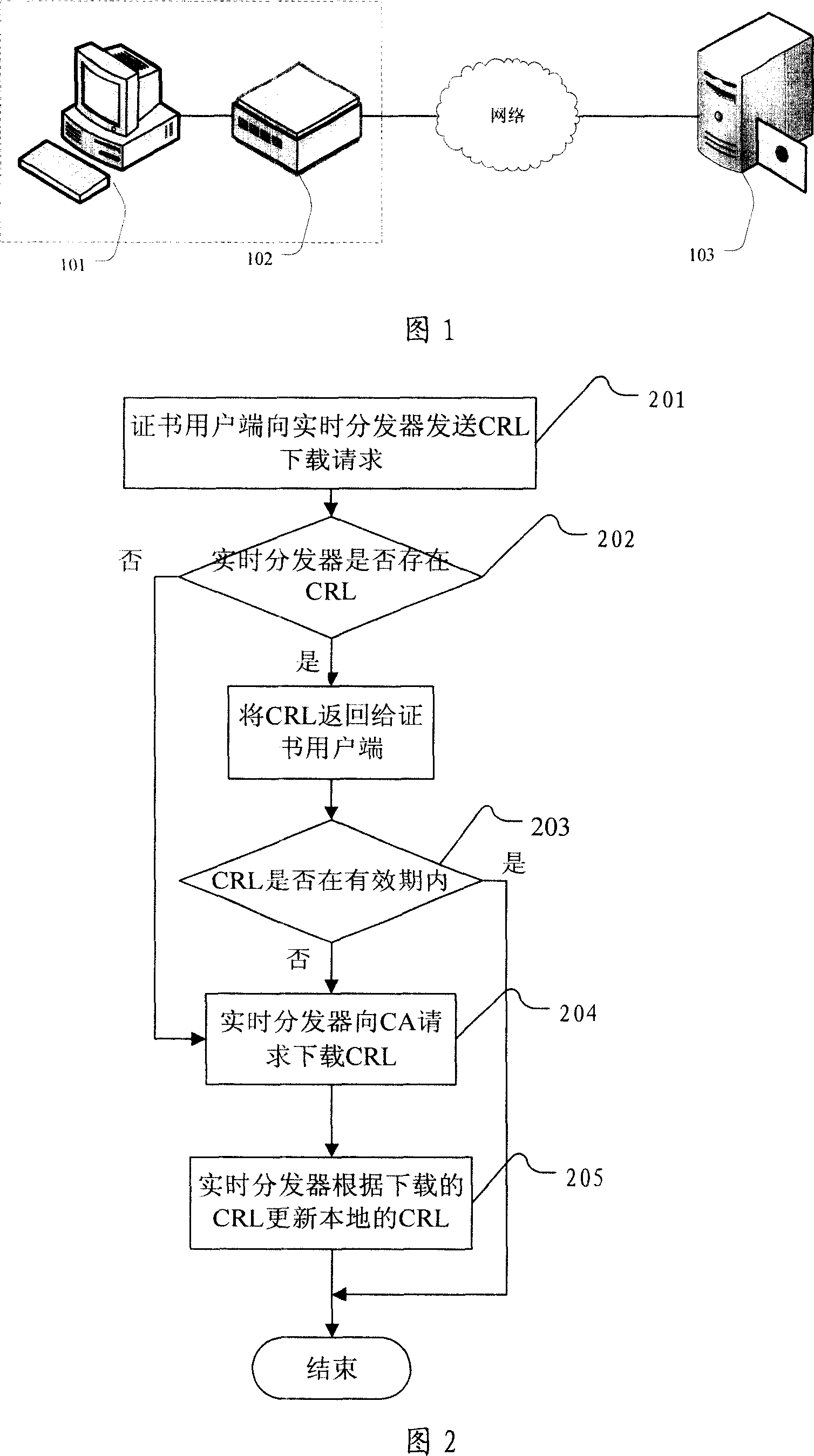
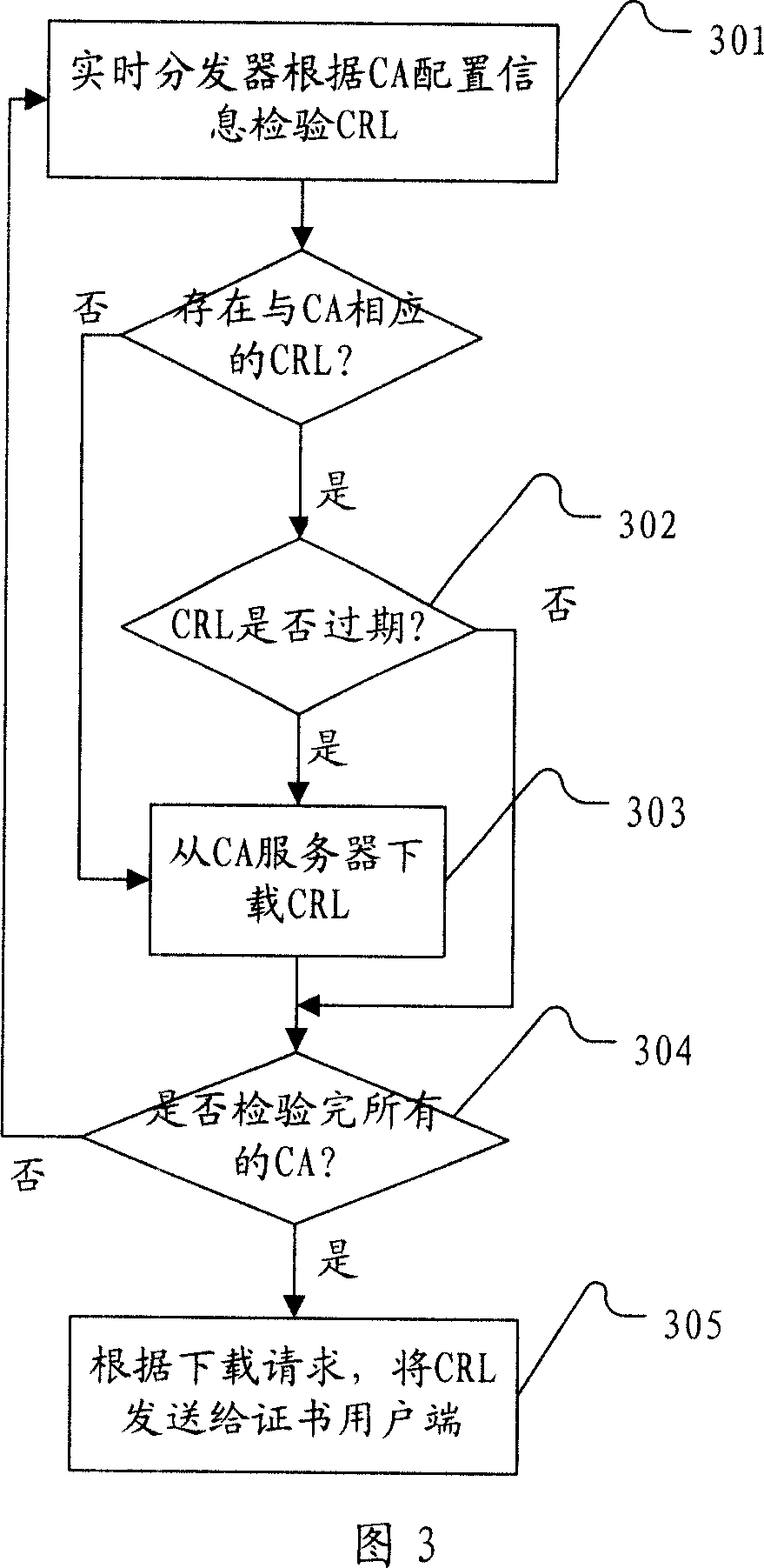
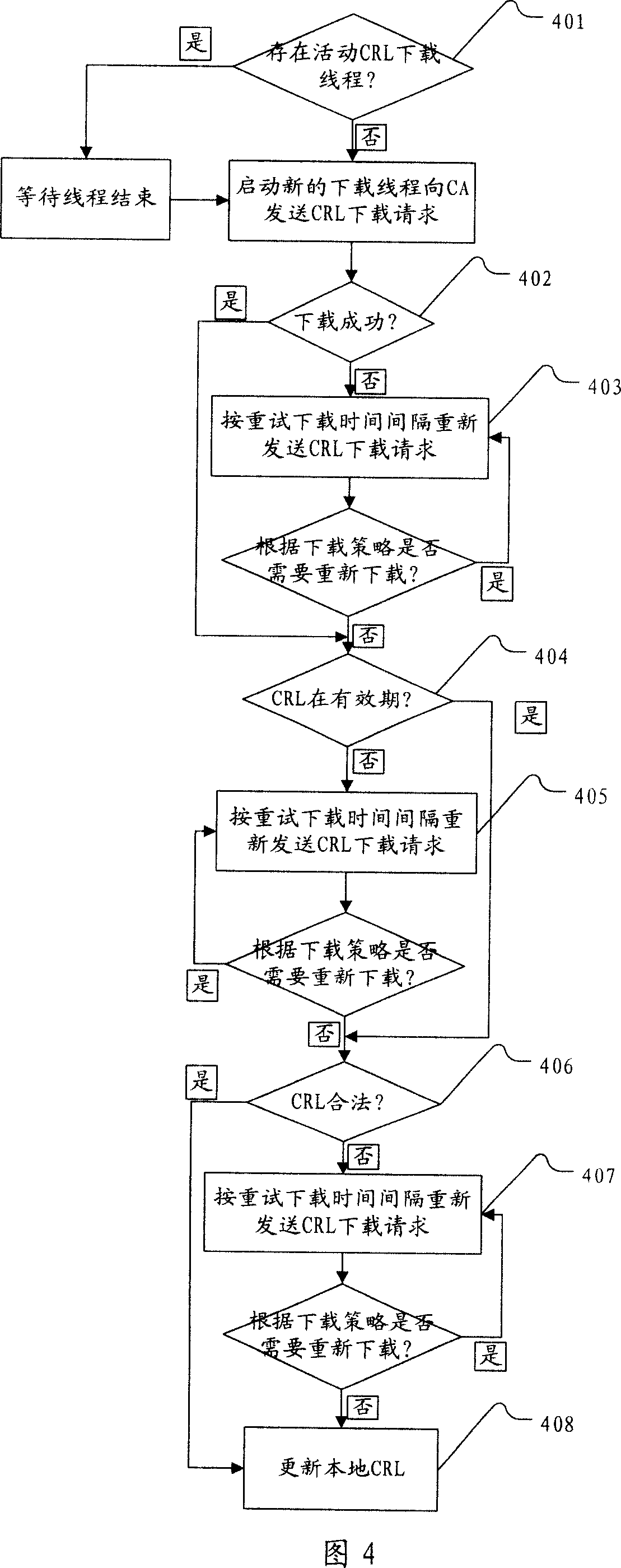
[0064] Before describing the method, device and system of the present invention in combination with specific embodiments, firstly introduce several concepts involved in the complete certificate authentication process, and understand the functions and relationships of each subject in the authentication process through a specific example.
[0065] In an e-commerce activity, all entities participating in the transaction must clearly indicate their identities. Only when this mutual trust relationship is established can the transaction be carried out normally. The digital certificate is an effective means for participating entities to show their identity to each other.
[0066] Asymmetric encryption algorithm is the basis for realizing digital certificate. The algorithm uses a private / public key pair, and data encrypted with the private key can only be decrypted with the corresponding public key, and vice versa. Typically, a CA signs a certificate so that it confirms that the publ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com