Identification authentication method and system
An identity authentication and authentication request technology, applied in the field of information security, can solve the problems of limited storage space, cumbersome authentication process, time delay, etc., and achieve the effect of simplifying the identity authentication process, saving storage space overhead, and improving response speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
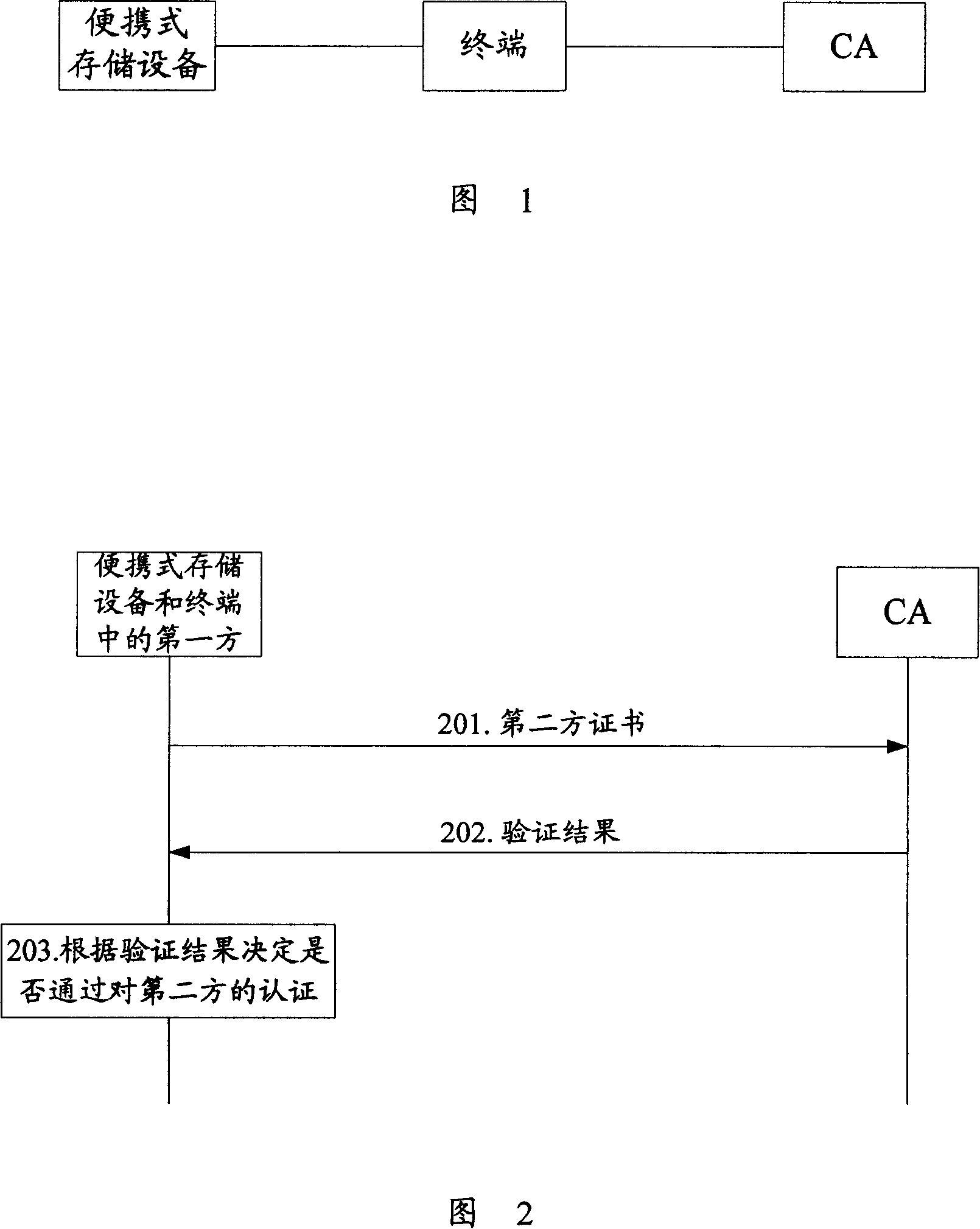
[0061] Taking the terminal to authenticate the portable storage device, and the portable storage device is a mobile storage card (hereinafter referred to as the card) as an example, as shown in Figure 3, the identity authentication process in this embodiment mainly includes the following steps:
[0062] Step 301: the card sends an authentication request to the terminal, requesting the terminal to authenticate the card, and the request information carried in the authentication request includes: card certificate.
[0063] Step 302: After receiving the authentication request sent by the card, the terminal sends a verification request to the CA, and the request information carried in the verification request includes: the card certificate.
[0064] Step 303: After receiving the verification request sent by the terminal, the CA verifies the validity of the card certificate carried in the verification request, and returns the verification result to the terminal in a verification resp...
Embodiment 2
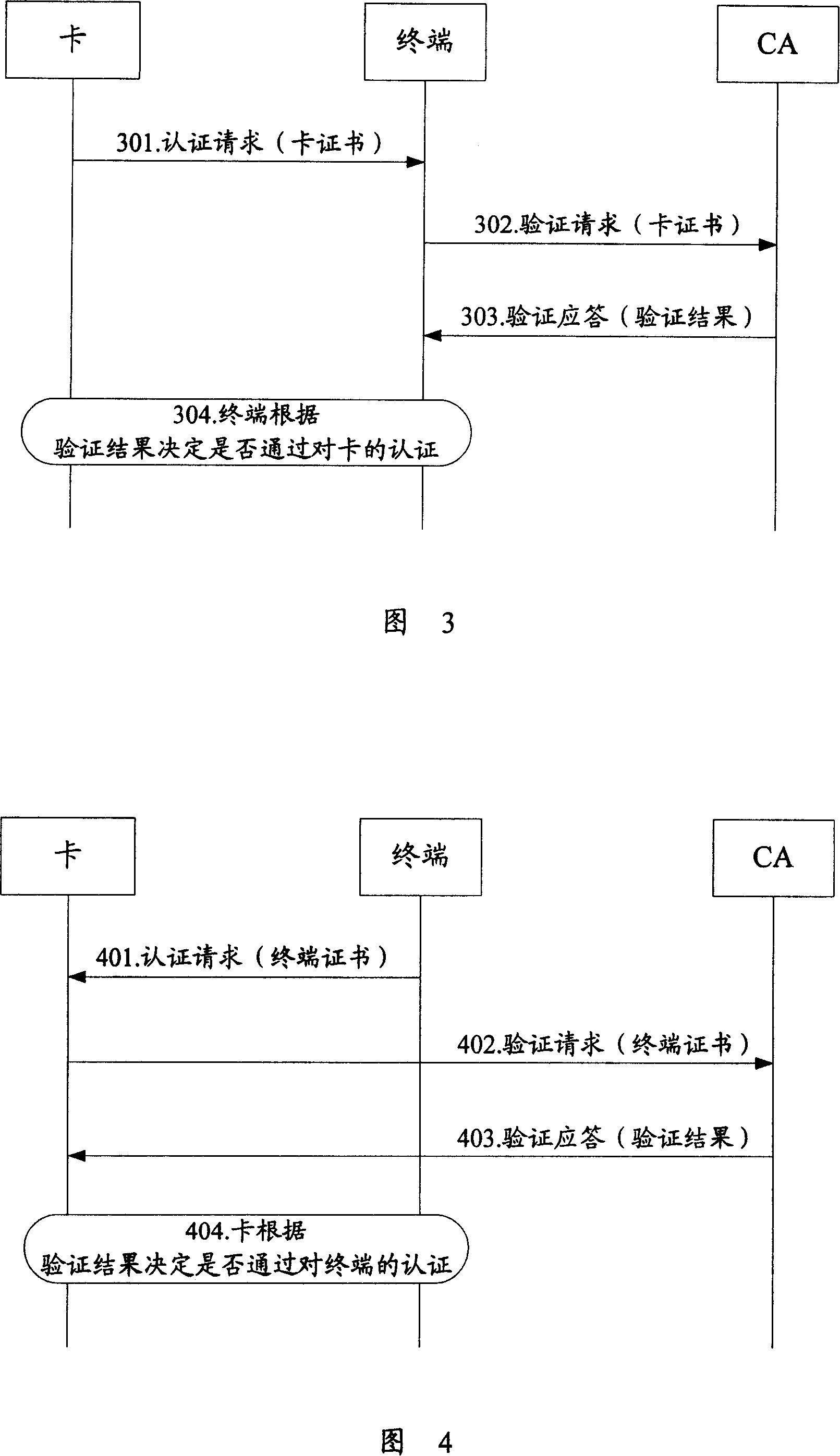
[0073] Taking the portable storage device to perform identity authentication on the terminal, and the portable storage device is a mobile memory card (hereinafter referred to as the card) as an example, as shown in Figure 4, the identity authentication process in this embodiment mainly includes the following steps:
[0074] Step 401: The terminal sends an authentication request to the card, requesting the card to authenticate the identity of the terminal, and the request information carried in the authentication request includes: terminal certificate.
[0075] Step 402: After receiving the authentication request from the terminal, the card sends a verification request to the CA through the terminal, and the request information carried in the verification request includes: terminal certificate.
[0076] Step 403: After receiving the verification request sent by the card, the CA verifies the validity of the terminal certificate carried in the verification request, and returns the...
Embodiment 3
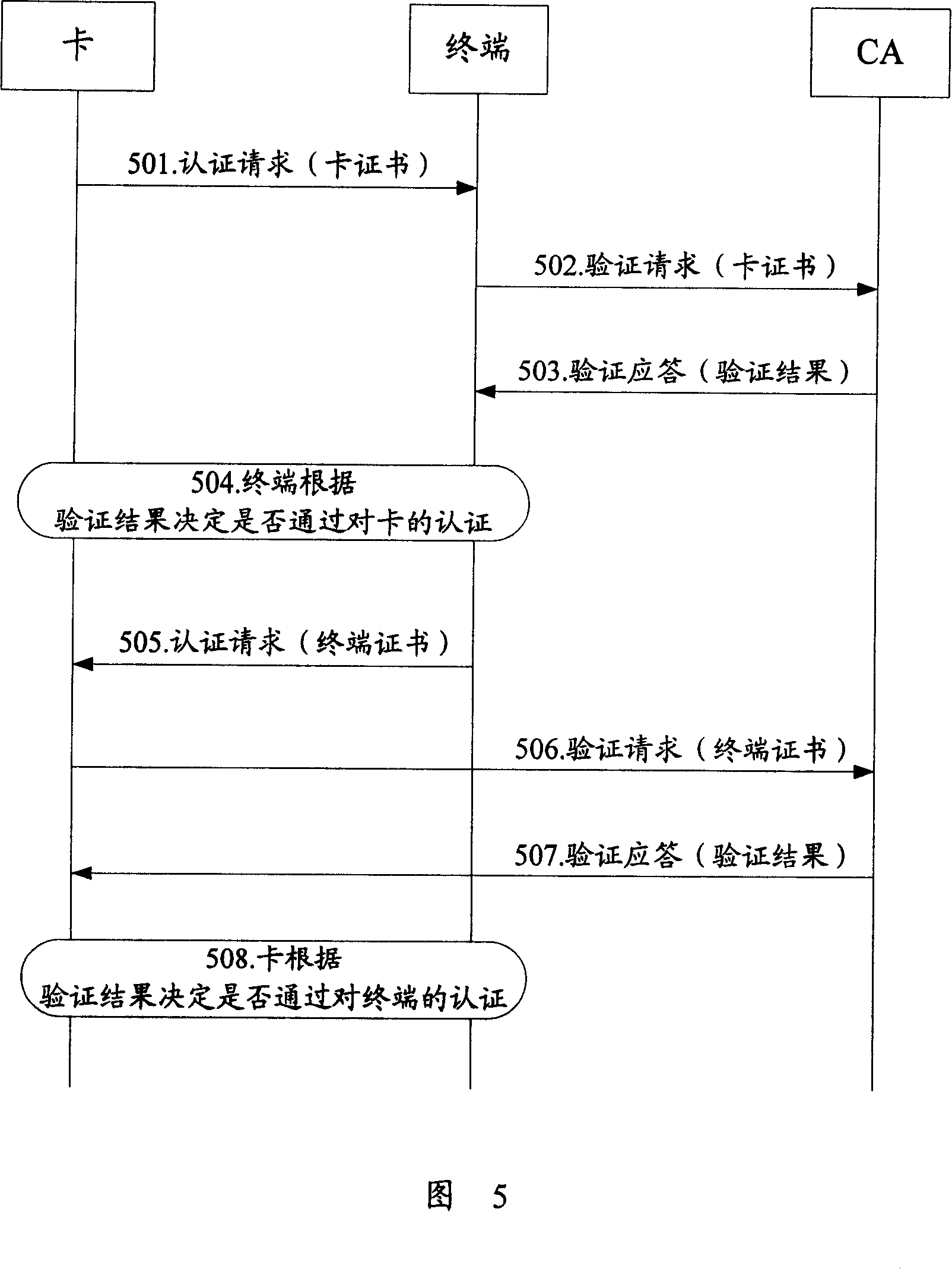
[0094] Take the mutual identity authentication between the portable storage device and the terminal, and the portable storage device is a mobile memory card (hereinafter referred to as the card) as an example, as shown in Figure 5, the identity authentication process in this embodiment mainly includes the following two parts:
[0095] Step 501-Step 504: the process of the terminal authenticating the card;
[0096] Step 505-Step 508: the process of the card authenticating the identity of the terminal.
[0097] It should be noted that steps 501 to 504 and steps 505 to 508 are two different processes, and there is no strict sequence relationship in time. The specific processing process of steps 501 to 504 is consistent with steps 301 to 304 in the first embodiment; the specific processing of steps 505 to 508 is consistent with the steps 401 to 404 in the second embodiment, and will not be repeated here. repeat.
[0098] When both parties pass the authentication, then the sessio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com