Wireless network security transmission method, system and equipment
A wireless network and secure transmission technology, applied in the field of communication, can solve the problem of principle-dependent security services, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
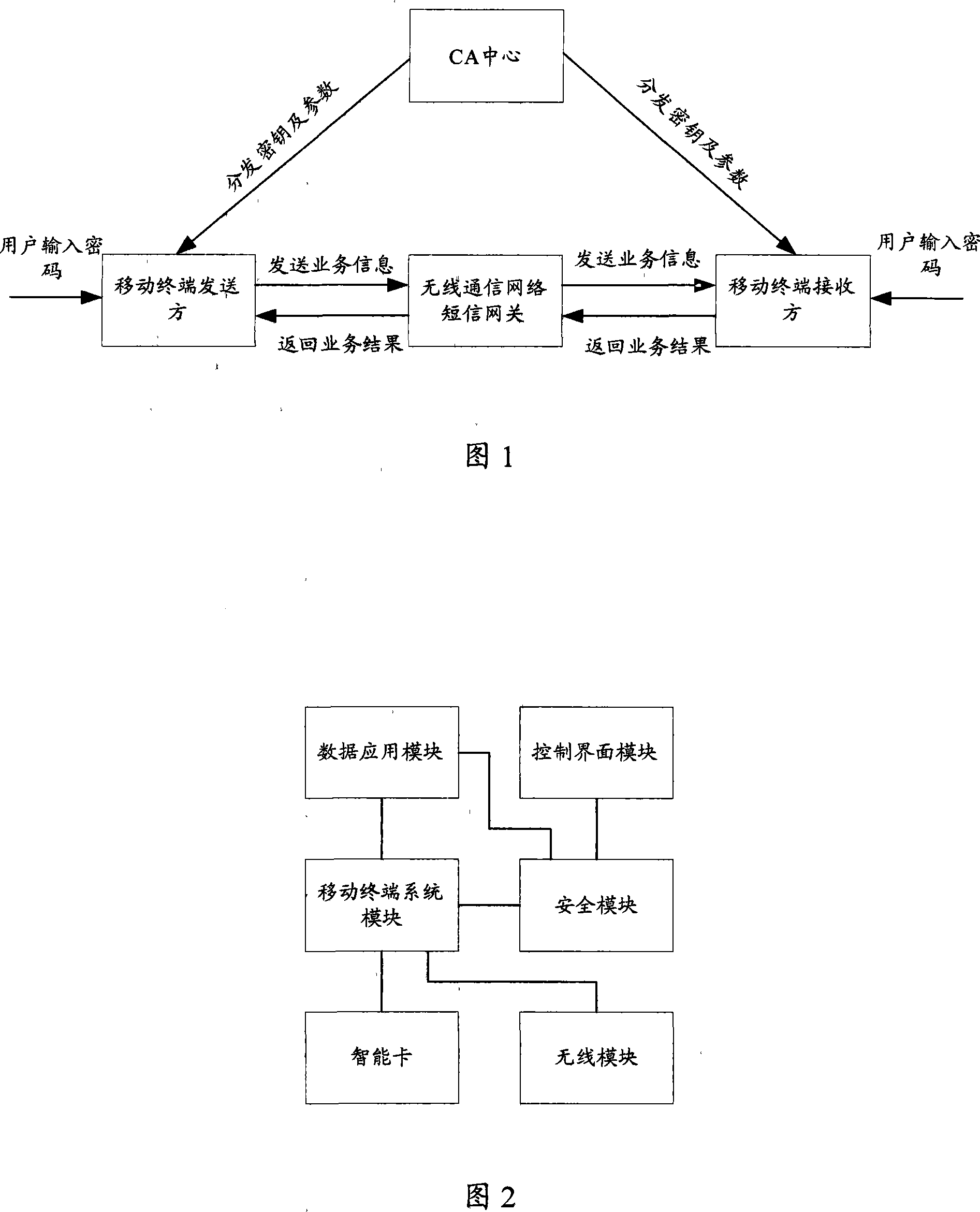
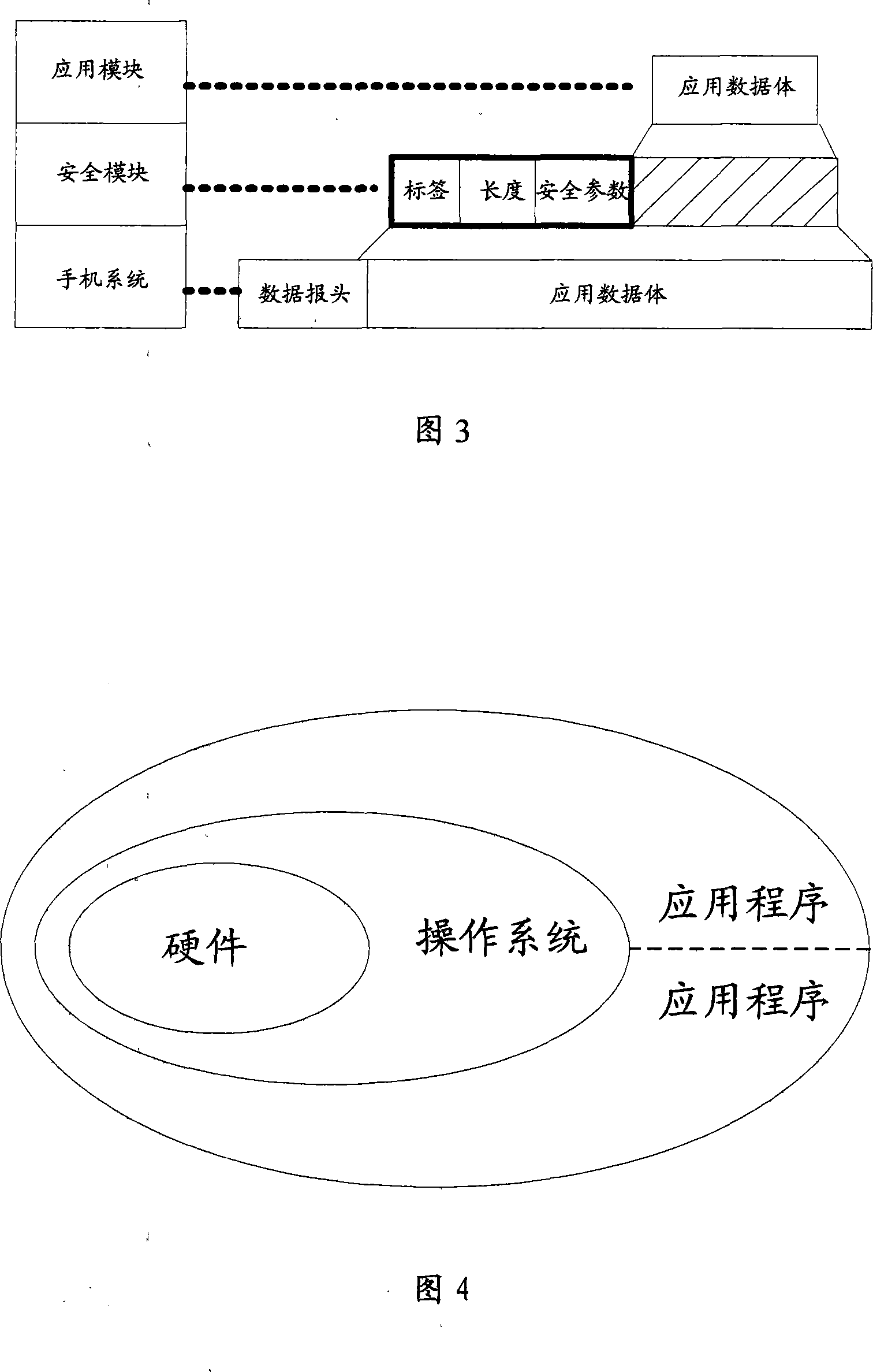
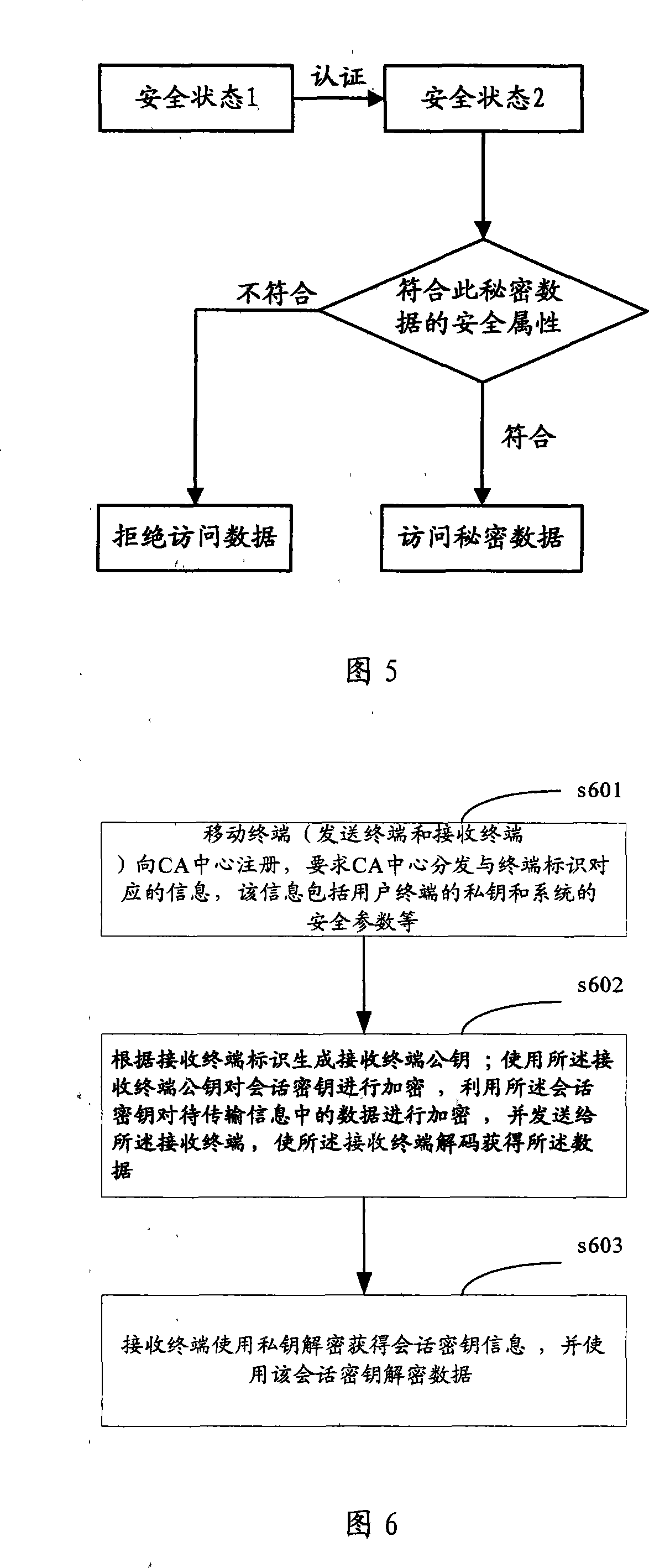
[0042] In the embodiment of the present invention, the end-to-end secure transmission architecture of the wireless communication network is shown in FIG. 1 , including: a CA (Certificate Authority, authentication and authorization) center, multiple mobile terminals, and a wireless communication network short message gateway. In order to describe clearly, the mobile terminals are divided into mobile sending terminals and mobile receiving terminals below. The mobile sending terminals are used to encrypt the data to be sent, and send them to the mobile receiving terminals through the SMS gateway of the wireless communication network; the mobile receiving terminals encrypt the encrypted data. Decrypt to obtain plaintext data.
[0043] Among them, the CA center only assigns the private key associated with the mobile terminal identity and other system security parameters to the mobile terminal used by the user when the user registers, and records the private key and security paramete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com