Secure printing system and method for the same
A technology for secure printing and printers, applied in the field of secure printing systems and secure printing, which can solve problems such as inability to execute printing, inability to know whether a printer is connected, inability to give instructions by the printer, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
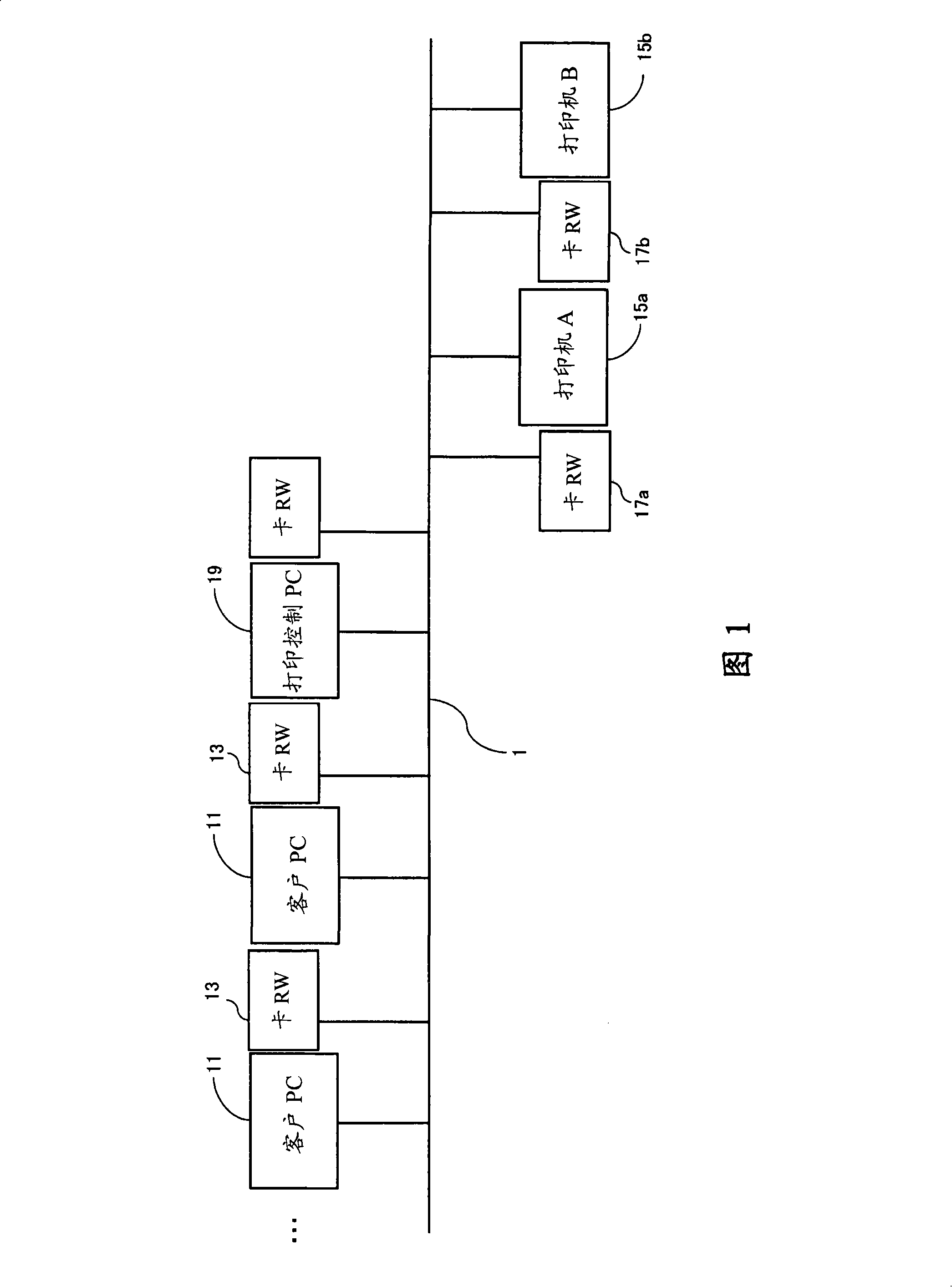
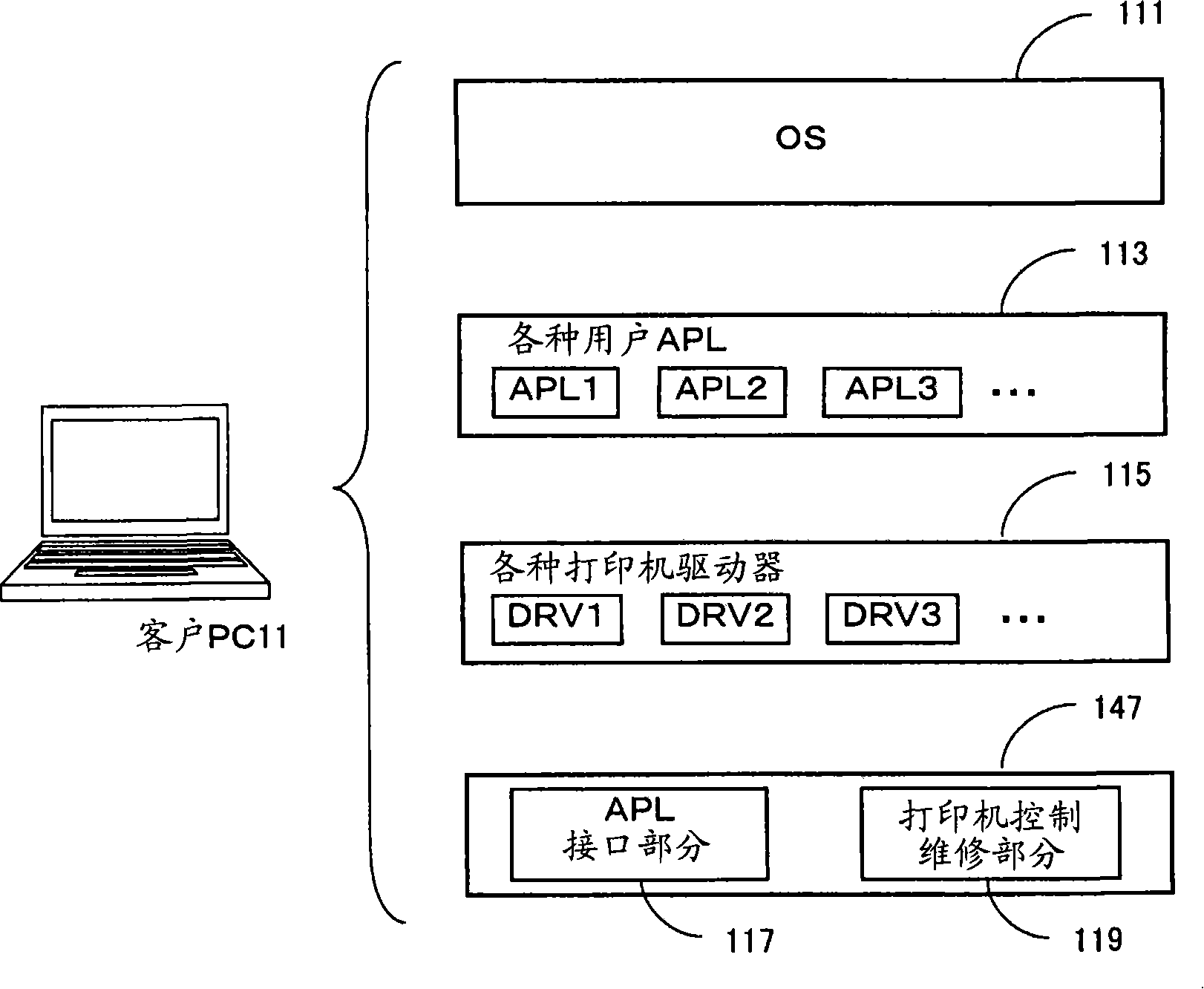
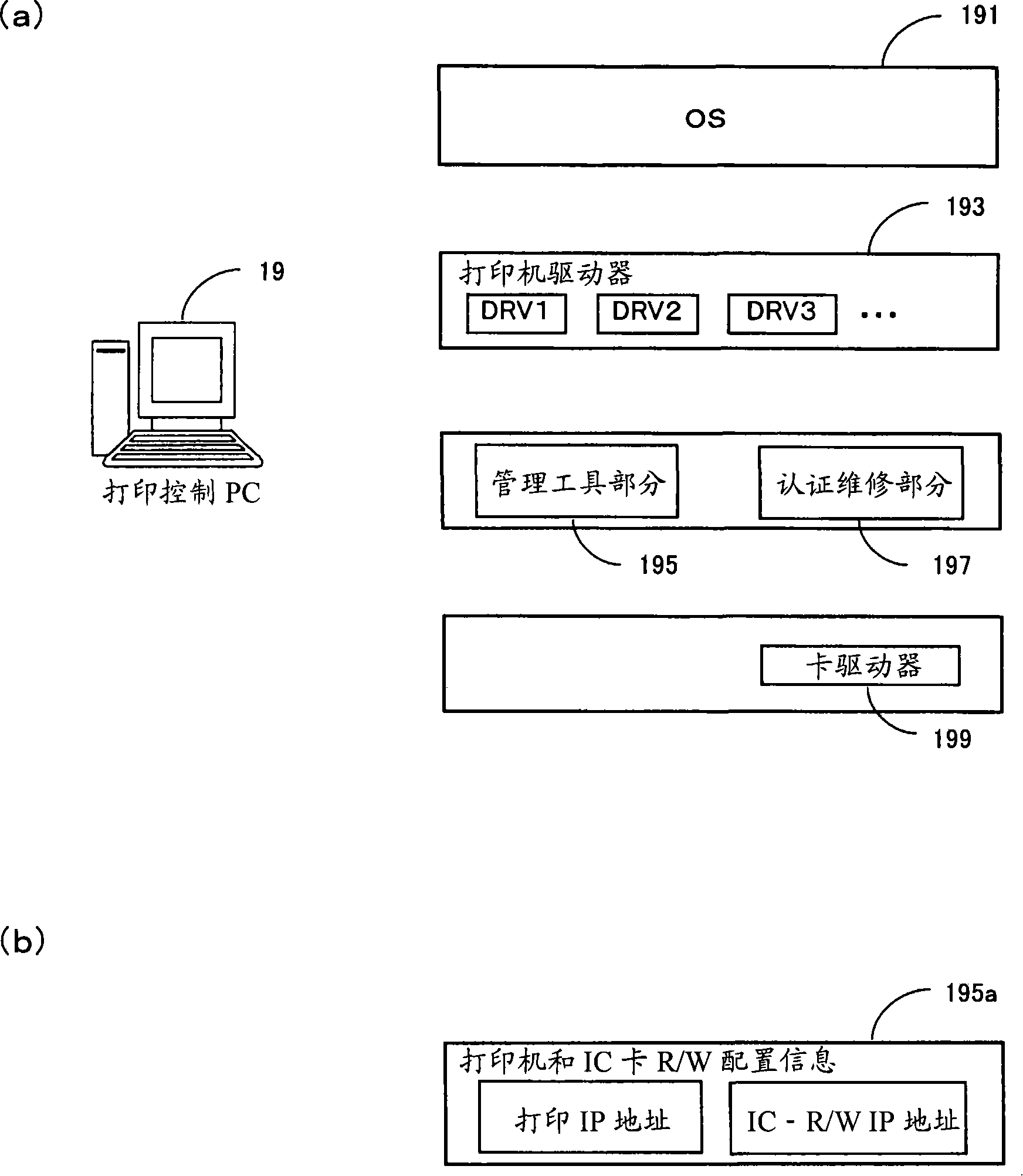
[0056] FIG. 1 is a schematic diagram showing the configuration of Example 1 according to the present invention. The secure printing system in this example is configured as, for example, an office LAN, which includes: one or more client PCs 11, a card reader / writer (hereinafter referred to as card RW) 13 for each client PC, connected to the network One or more printers 15 of 1, a card RW17 providing each printer, and a print control PC19.
[0057] Since this example provides a secure printing system using an IC card, either one of the cards RW13 and 17 is described as a contact type IC card reader / writer. However, another example may employ a configuration using a magnetic or other type of card. Also, it is assumed that the printer 15 of this example is a network printer having a printer server function and is directly connected to the network 1 , but may be a printer connected to any PC in the network 1 . In addition, the card RW13 for client PCs may be incorporated into the...
example 2
[0078] Example 2 of the present invention will now be described in detail with reference to FIG. 7 . Fig. 7 is a schematic configuration diagram of a security printing system according to Example 2 of the present invention. In this example, in addition to the configuration in FIG. 1 , a document management server 21 for temporarily storing documents to be printed is connected to the network 2 . Figure 8 The software configuration in the document management server 21 is shown. Such as Figure 8 As shown, the document management server 21 includes: an OS 211, various printer drivers 213, an APL interface section 215, a print control maintenance section 217, and a preset editing application program 219 for general image or document files. The document management server 21 also includes a storage device 22 having sufficient capacity to temporarily store general-purpose image / document files sent from each client PC 11 . In addition, although not shown in this example, the same ...
example 3
[0087] Fig. 10 is a schematic diagram showing the configuration of Example 3 of the present invention. This example provides an application to a secure printing system in a configuration in which two remote LANs 3 and 4 are connected via WAN 5, for example, networks in the Tokyo office and Osaka office of the same company network in . As shown in FIG. 10 , LAN 3 and LAN 4 are connected via WAN 5 . Both the LAN 3 and the LAN 4 have the same configuration as the network 1 shown in FIG. Cards RW 13 and 17 for each client PC and each printer. The print data of each printer 15 on the LANs 3 and 4 is managed by the print control PC 19 in the LAN to which each printer belongs. In addition, the system has a document management server 21 . The document management server 21 in this example is connected to the wide area network 5;
[0088] In this system, the document management server 21 and each print control PC 19 can share at least network configuration information as shown in F...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com