A method for redirecting network attack by combining route with the tunnel
A network attack and redirection technology, which is applied in the direction of network interconnection, data exchange network, data exchange through path configuration, etc., can solve the problems of difficult software implementation, reduced gateway forwarding speed, troublesome operation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
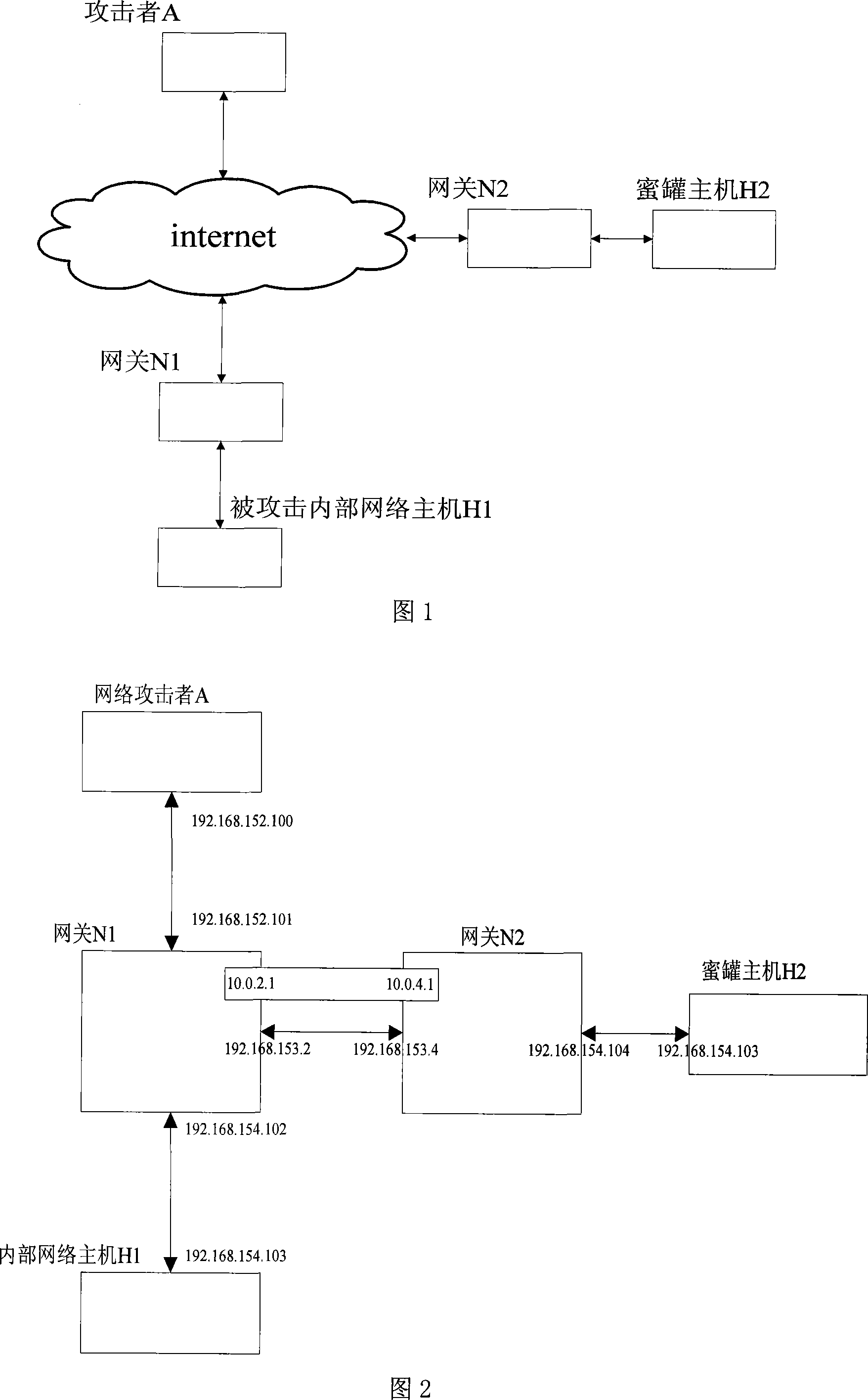
[0048] Referring to Fig. 2, the present invention will be described in detail in conjunction with examples. The gateway N1 and the gateway N2 in FIG. 2 both run a common version of the linux operating system, and are configured in a router mode rather than a bridge mode. Use LAN 192.168.152.* and 192.168.153.* to simulate the internet, which will not affect the universality of the experiment. Use the LAN 192.168.154.* to connect the internal network host H1, but this LAN and the LAN 192.168.154.* connected to the honeypot host H2 are physically and logically separate networks, and the IP address of the honeypot system is the same as the internal network have the same IP address.
[0049] The specific implementation is as follows:
[0050] 1. Run the following command on the gateway N1 to configure:
[0051] ip tunnel add rd_rt mode ipip remote 192.168.153.4 local 192.168.153.2 ttl 255
[0052] ip link set rd_rt up
[0053] ip addr add 10.0.2.1 dev rd_rt
[0054] ip route...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com