Method for transmitting and receiving safe mobile message
A technology of mobile information and receiving methods, applied in security devices, wireless communications, messages/mailboxes/notifications, etc., can solve problems such as only considering information encryption methods, not considering the protection of information integrity, and not involving short message security protection, etc. , to achieve the effect of protecting the integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
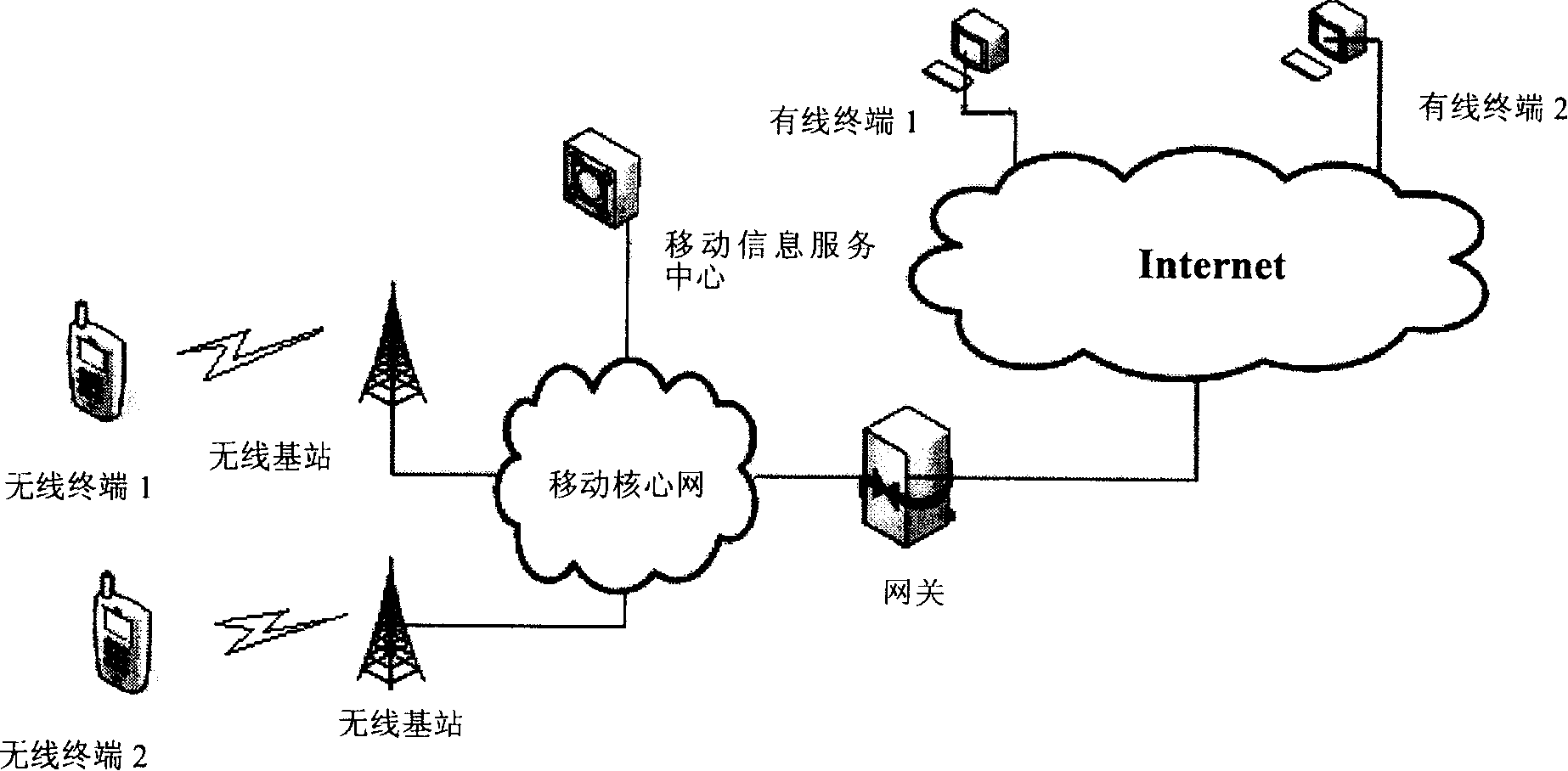
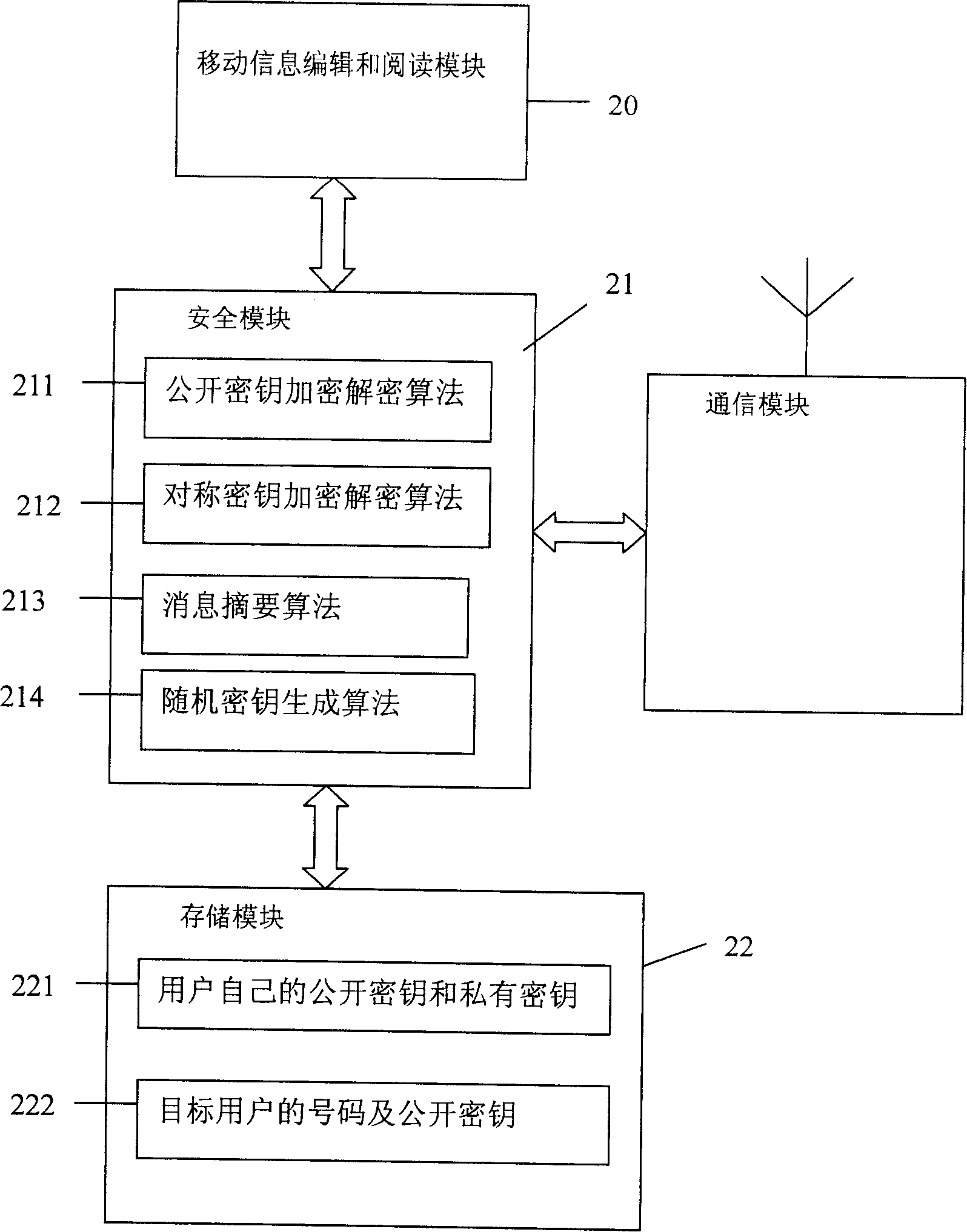
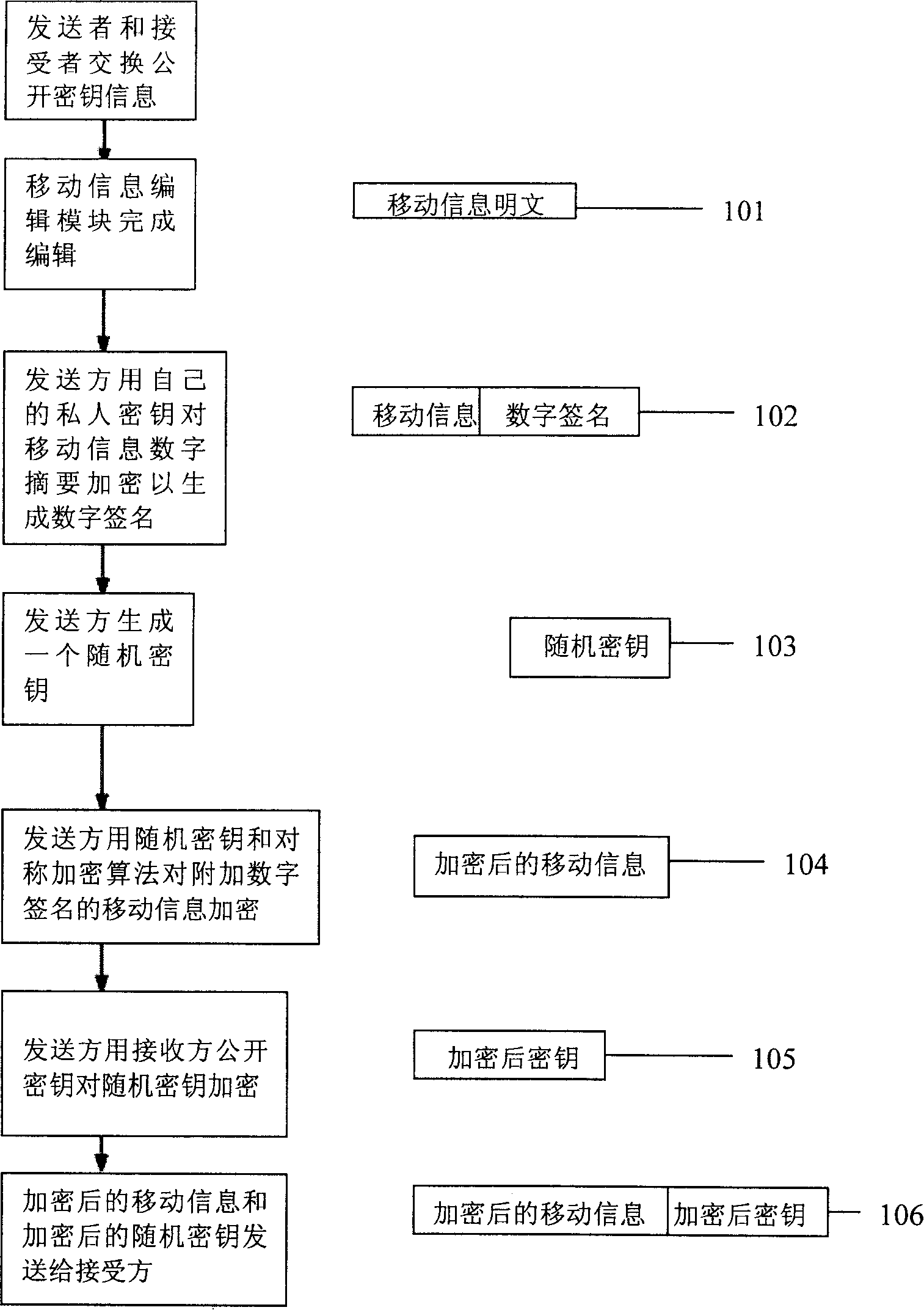
[0029] The following is based on Figure 2 ~ Figure 4 A preferred embodiment of the present invention is given and described in detail so that those skilled in the art can more easily understand the method features and functional characteristics of the present invention, rather than to limit the scope of the method of the present invention.
[0030] The encryption and decryption algorithms involved in the present invention include public key encryption and decryption algorithms and symmetric key encryption and decryption algorithms.
[0031] In the public key encryption and decryption algorithm, each user has two keys: a public key and a private key, the confidentiality of the algorithm is completely guaranteed by the private key, and the public key can be transmitted publicly without would affect confidentiality. When a user sends confidential information to another user, he encrypts the information with the receiver's public key, and only the receiver who has the private ke...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com