Method of defense against DDoS attacks in P2P stream media system
A streaming media, media server technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as benign node service impact, single DoS attack, and inability to prevent server and system DDoS attacks at the same time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
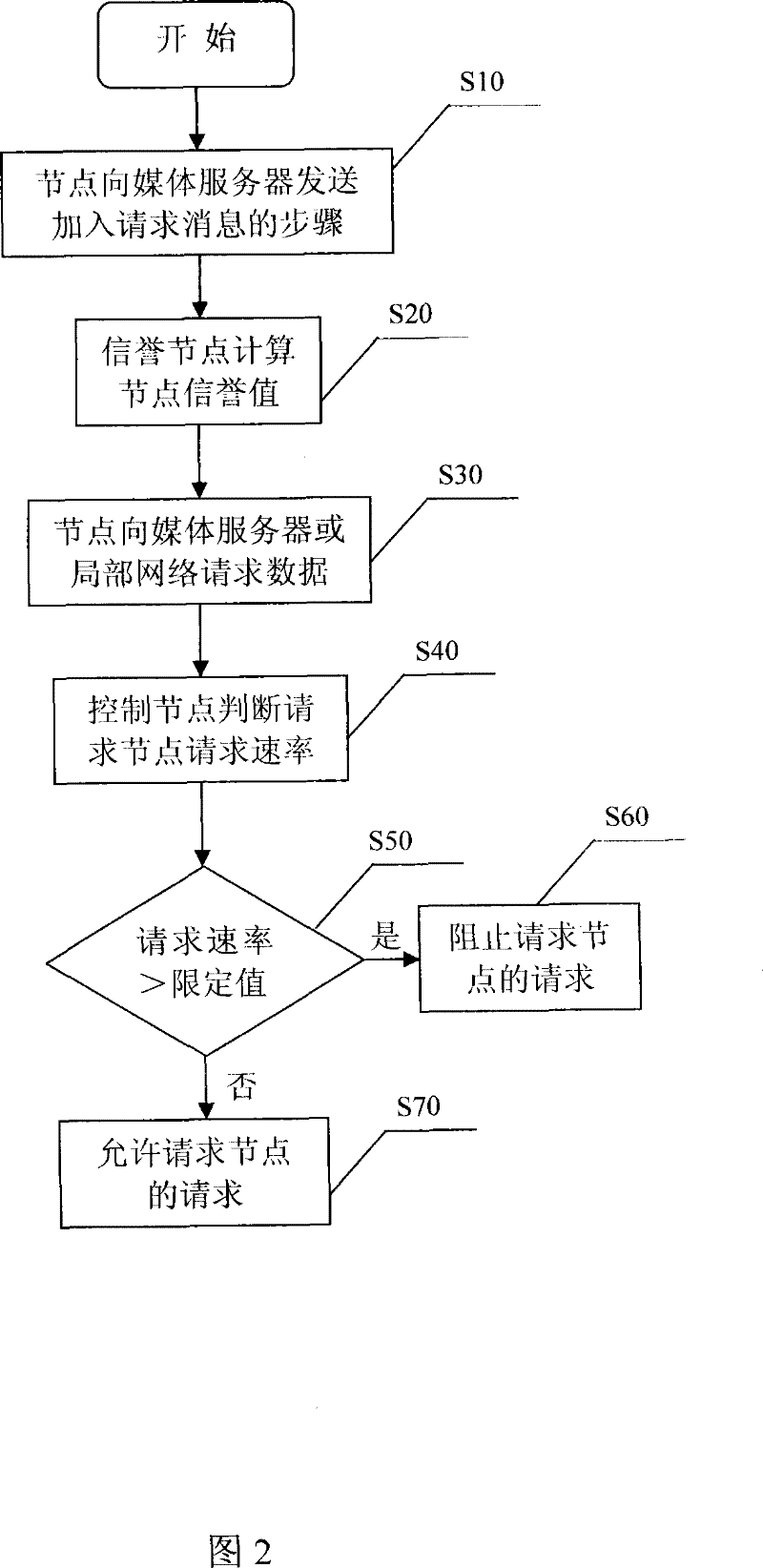
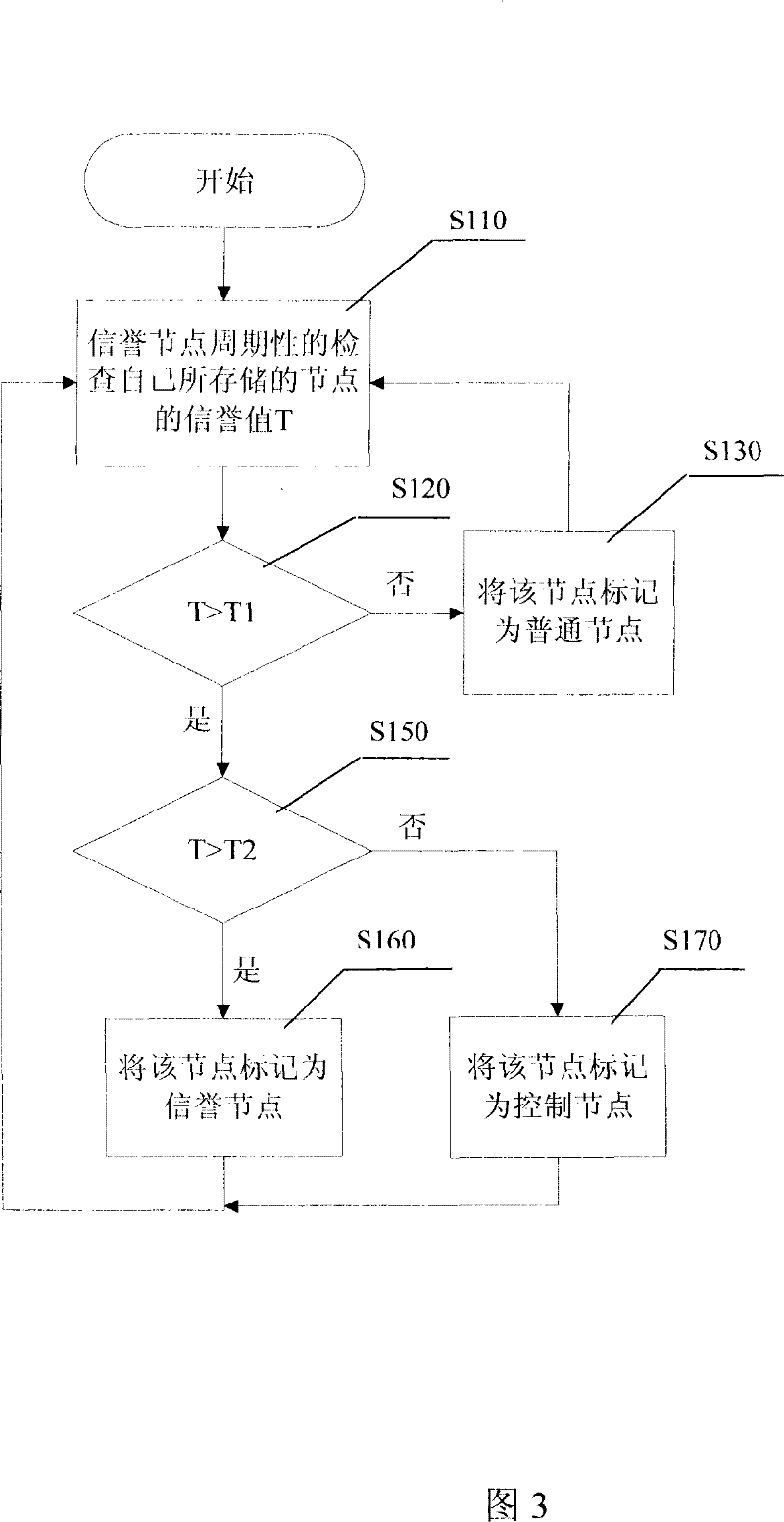
[0026] The specific implementation of the method for defending against DDoS attacks in the P2P streaming media system of the present invention will be described in detail below with reference to the accompanying drawings.
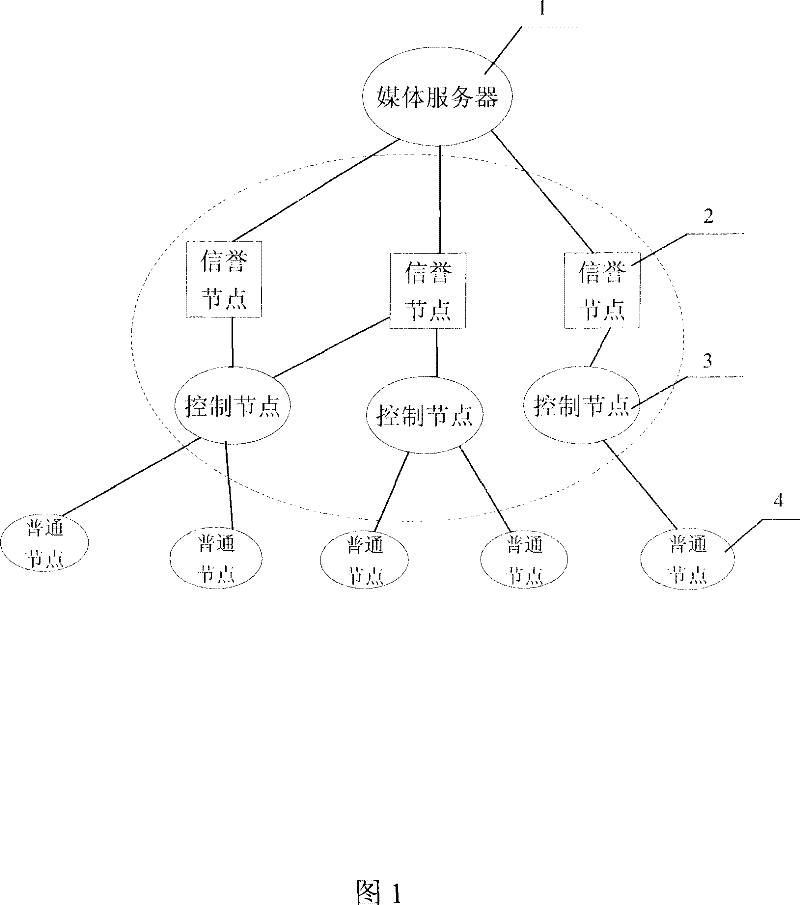
[0027] figure 1 It is a system topology diagram implementing the method for defending against DDoS attacks in the P2P streaming media system of the present invention. like figure 1 Shown, in the method for defending against DDoS attack in the P2P streaming media system of the present invention, the node is divided into three grades according to the node reputation situation, reputation node, control node, common node, reputation node is because the reputation grade is the highest, it can dynamically Check the reputation status of ordinary nodes, control nodes, and reputation nodes, mark nodes whose reputation level reaches reputation nodes as reputation nodes, and mark nodes whose reputation level reaches control nodes as control nodes, and others as ordin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com