An operation right judgment system and method realized by introducing right judgment client end
A business authentication and client technology, applied in the field of authentication system, can solve the problem of heavy load on the authentication server, achieve the effects of reducing construction and expansion costs, speeding up processing speed, and improving scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
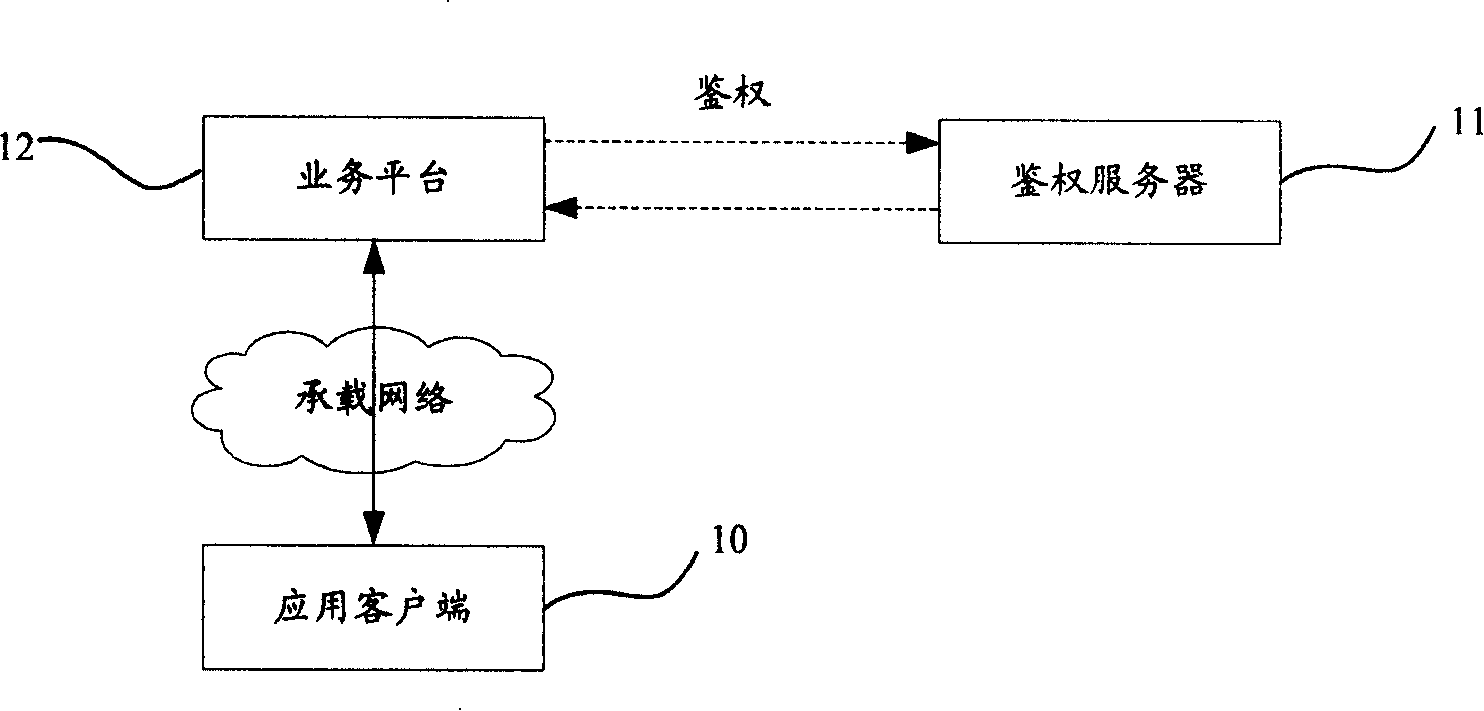
[0045] The first implementation mode: the authentication data is a token, the token is generated by the authentication server, the authentication client stores the token, the service request carries the token, and the service platform only verifies the validity of the token;
[0046] The second implementation mode: the authentication data is a token and / or connection information, the token is generated by the authentication server, and the connection data is preset on the service platform, the authentication client stores the token and related connection information, and the service request carries Connection information, the service platform compares the connection information in the service request with the preset connection data to verify the validity;
[0047] The third implementation mode: the authentication data is a token, the authentication client downloads the necessary service authentication information from the authentication server, the authentication client stores ...
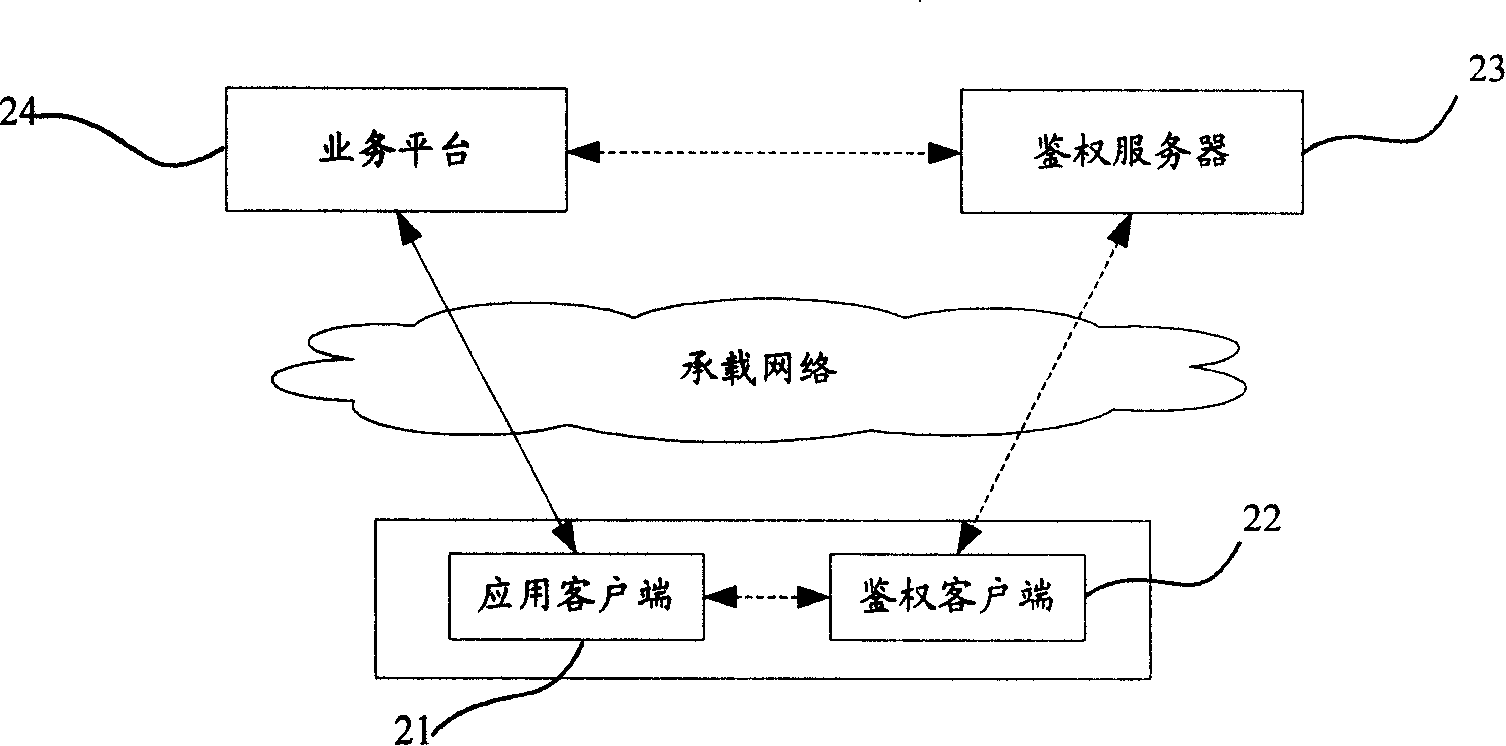
specific Embodiment 2
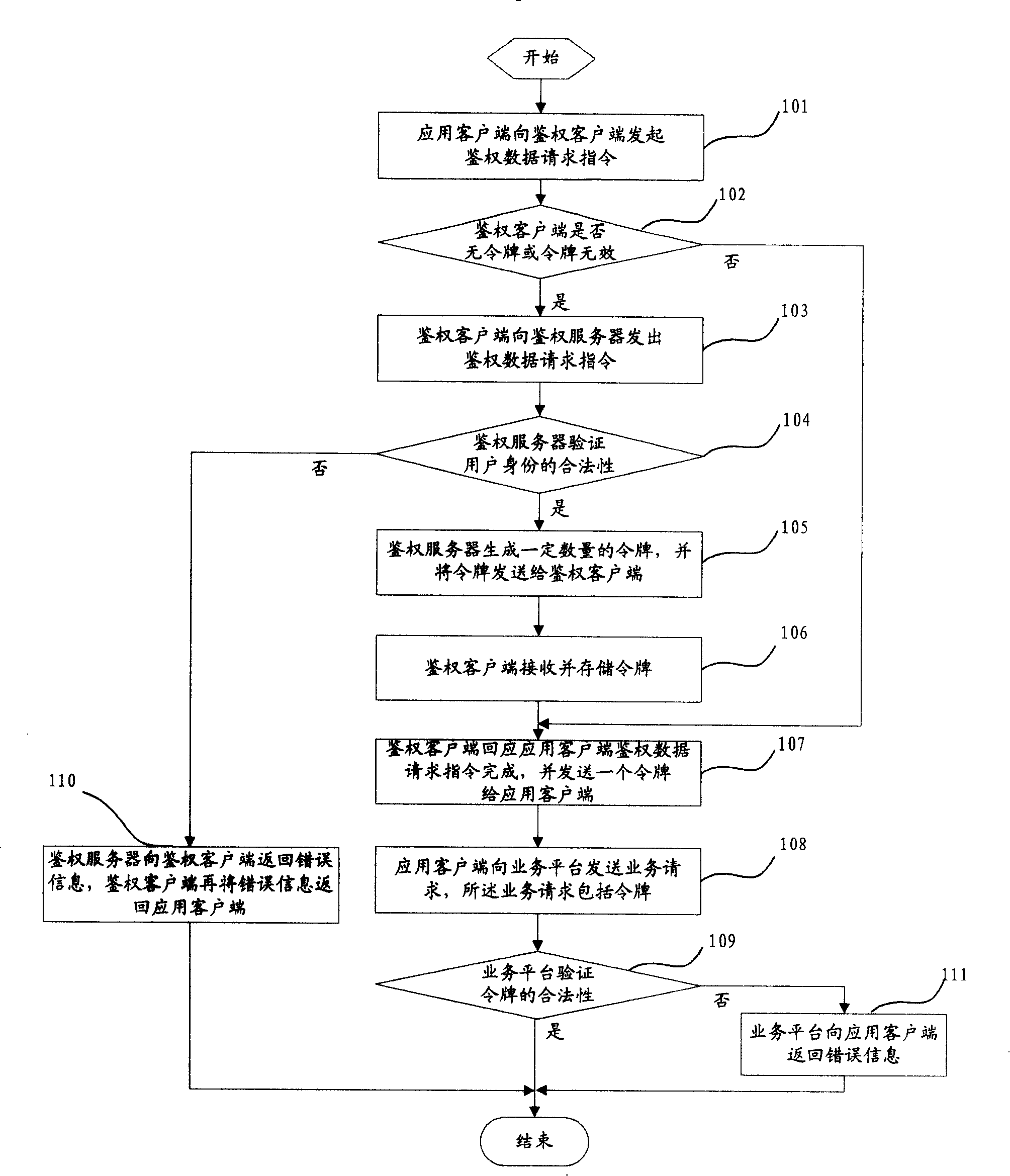
[0061] Specific embodiment two specifically comprises the following steps:
[0062] Step 201: the application client initiates an authentication data request instruction to the authentication client;
[0063] Step 202: After receiving the authentication data request instruction, the authentication server checks the status of the saved token, if it finds that there is no token or the token is invalid, execute step 203, and if the token is valid, execute step 209;
[0064] Step 203: the authentication client sends an authentication data request instruction to the authentication server;
[0065] Step 204: The authentication server verifies the legitimacy of the user's identity after receiving the authentication data request instruction, if it is legal, execute step 205, otherwise execute step 212;
[0066] Step 205: the authentication server notifies the service platform to establish relevant connection information;
[0067] Step 206: The service platform establishes and saves ...
specific Embodiment 3
[0076] Specific embodiment three comprises the following steps:
[0077] Step 301: the application client initiates an authentication data request instruction to the authentication client;
[0078] Step 302: After receiving the authentication data request instruction, the authentication client checks the status of the stored authentication information. If no authentication information is found or the authentication information is invalid, execute step 303; otherwise, execute step 306;
[0079] Step 303: the authentication client sends an authentication data request instruction to the authentication server;
[0080] Step 304: The authentication server generates corresponding authentication information after receiving the authentication data request instruction, and sends the authentication information to the authentication client;
[0081] Step 305: the authentication client stores the authentication information;
[0082] Step 306: The authentication client verifies the legit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com