Method for positioning specific memory illegally rewritten by function
A function and memory technology, which is applied in the field of locating a specific memory that is illegally rewritten by a function, can solve problems such as not prohibiting other tasks from running, tasks cannot be run, and external events of the system clock cannot be handled correctly, so as to achieve the effect of improving stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
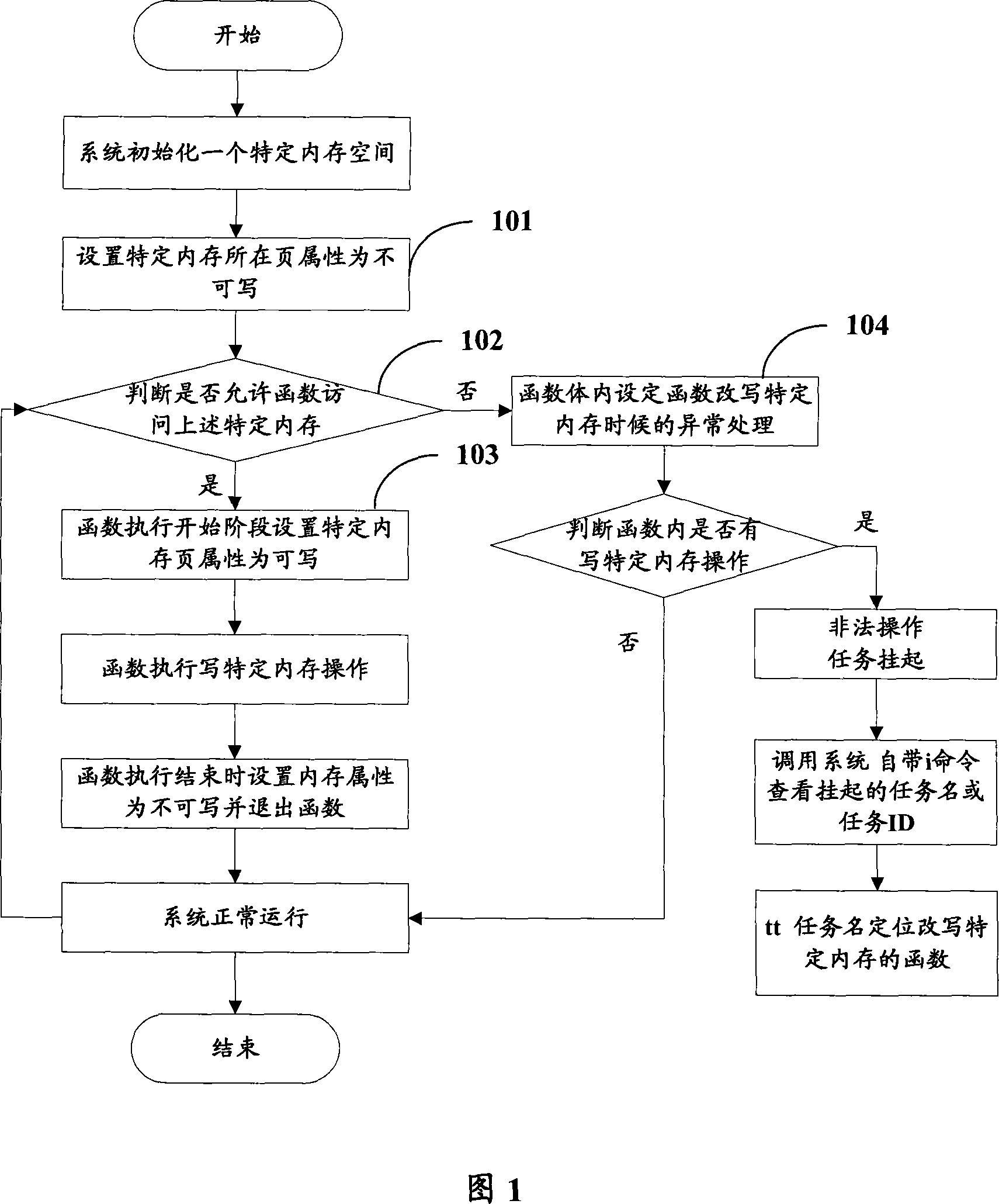
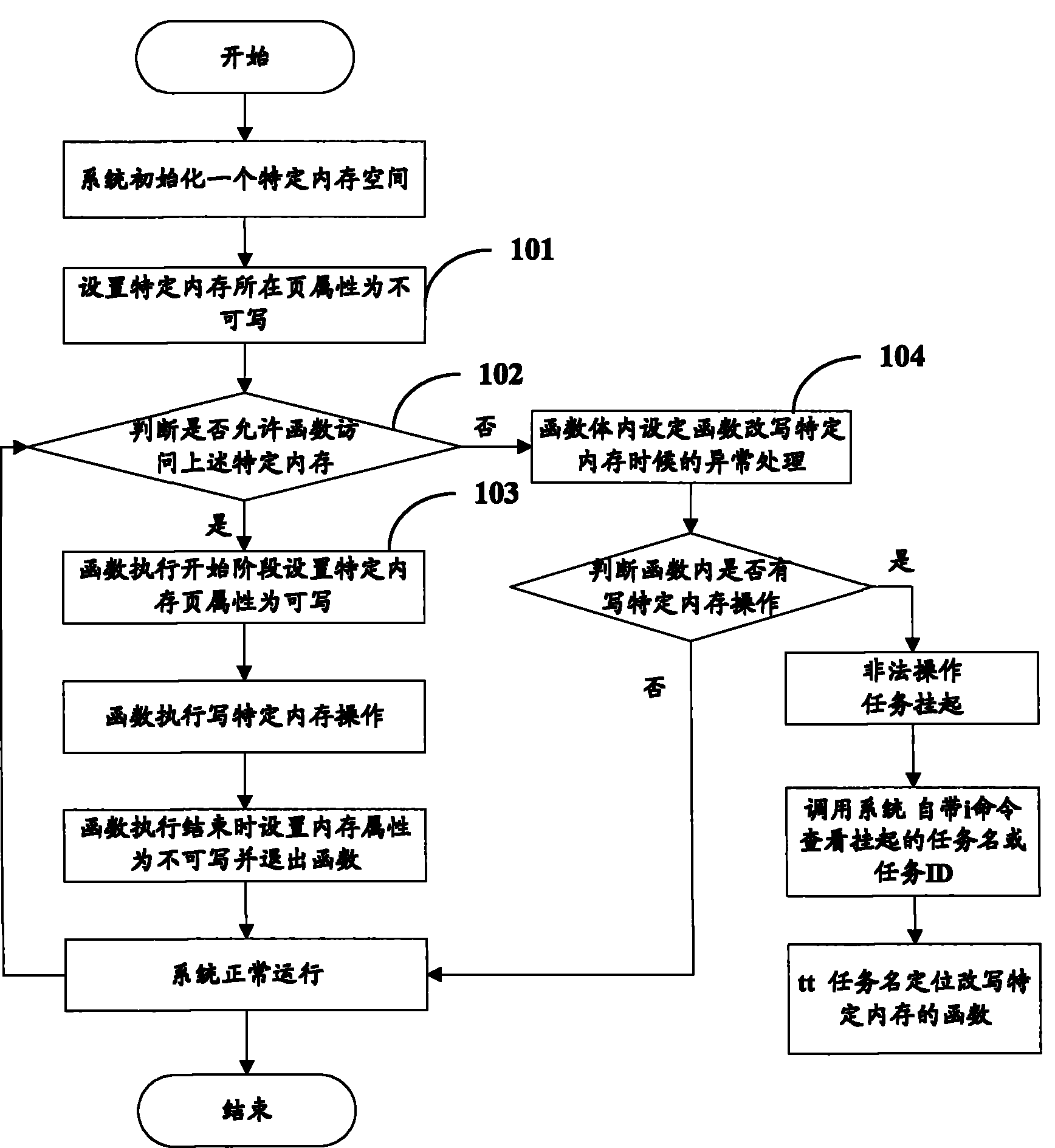
[0019] Hereinafter, the method for locating a specific memory illegally rewritten by a function of the present invention will be described in detail with reference to the accompanying drawings.
[0020] The core idea of the present invention is: for the embedded real-time operating system, the task is represented as a function, and this function is the entry function of the task, each task has its own stack, and the operating system uses preemptive scheduling or round-robin scheduling to perform Scheduling, all tasks run in a unified linear address space. Therefore, many debugging functions in the system can be used to view the information when the system is running abnormally, such as when the task is suspended, and locate the cause of the task suspension based on this information, so as to quickly solve the problem.
[0021] Hereinafter, only the VxWorks system is taken as an example to describe the method for locating a specific memory illegally rewritten by a function of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com