Method and apparatus for data protection of memory device
A technology for storing devices and data, applied in program control devices, preventing unauthorized use of memory, program loading/starting, etc. It can solve hidden partitions that are easy to be mounted, lack of MBR protection, and it is difficult for third-party tools to clear HPA, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
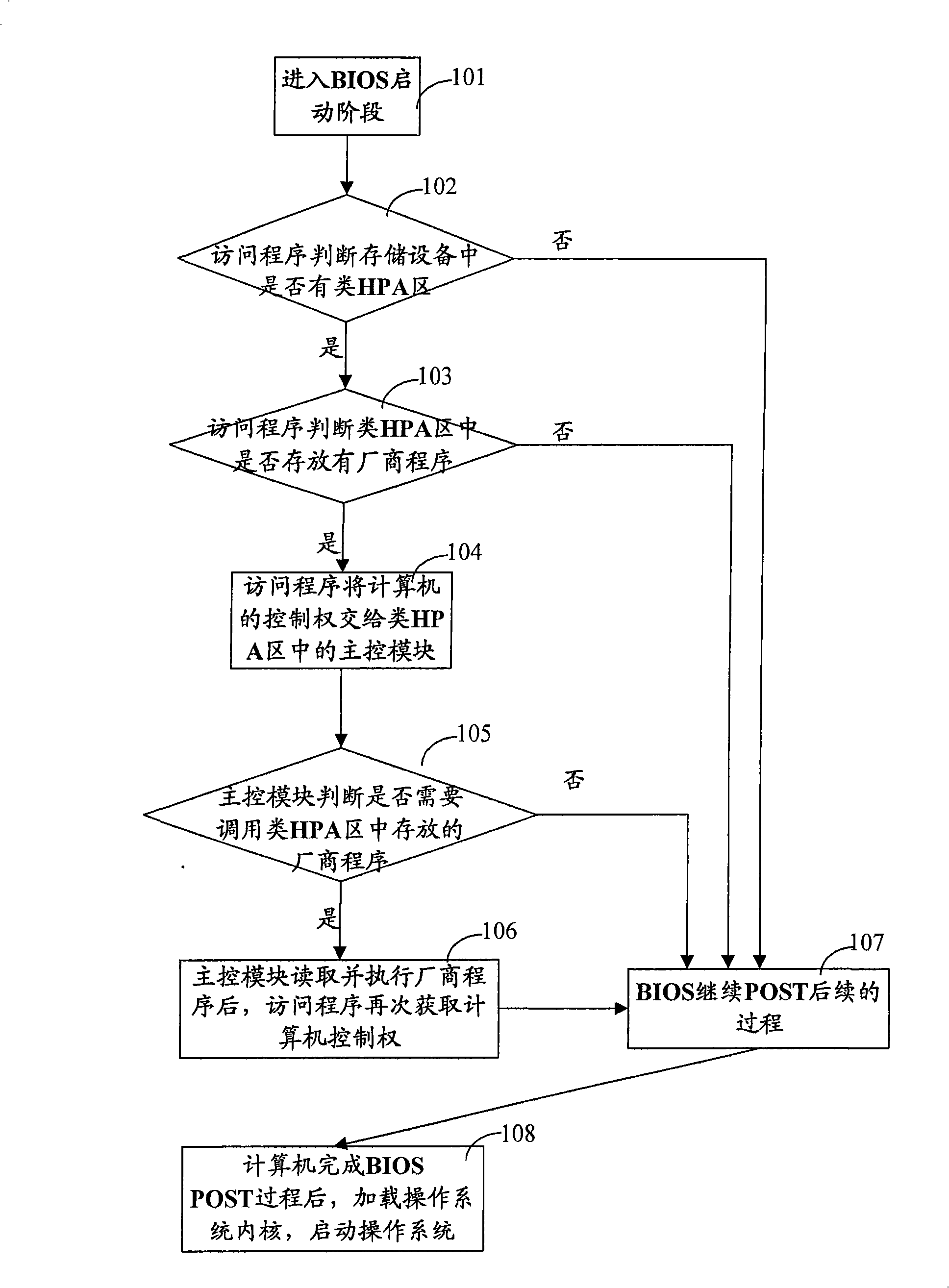
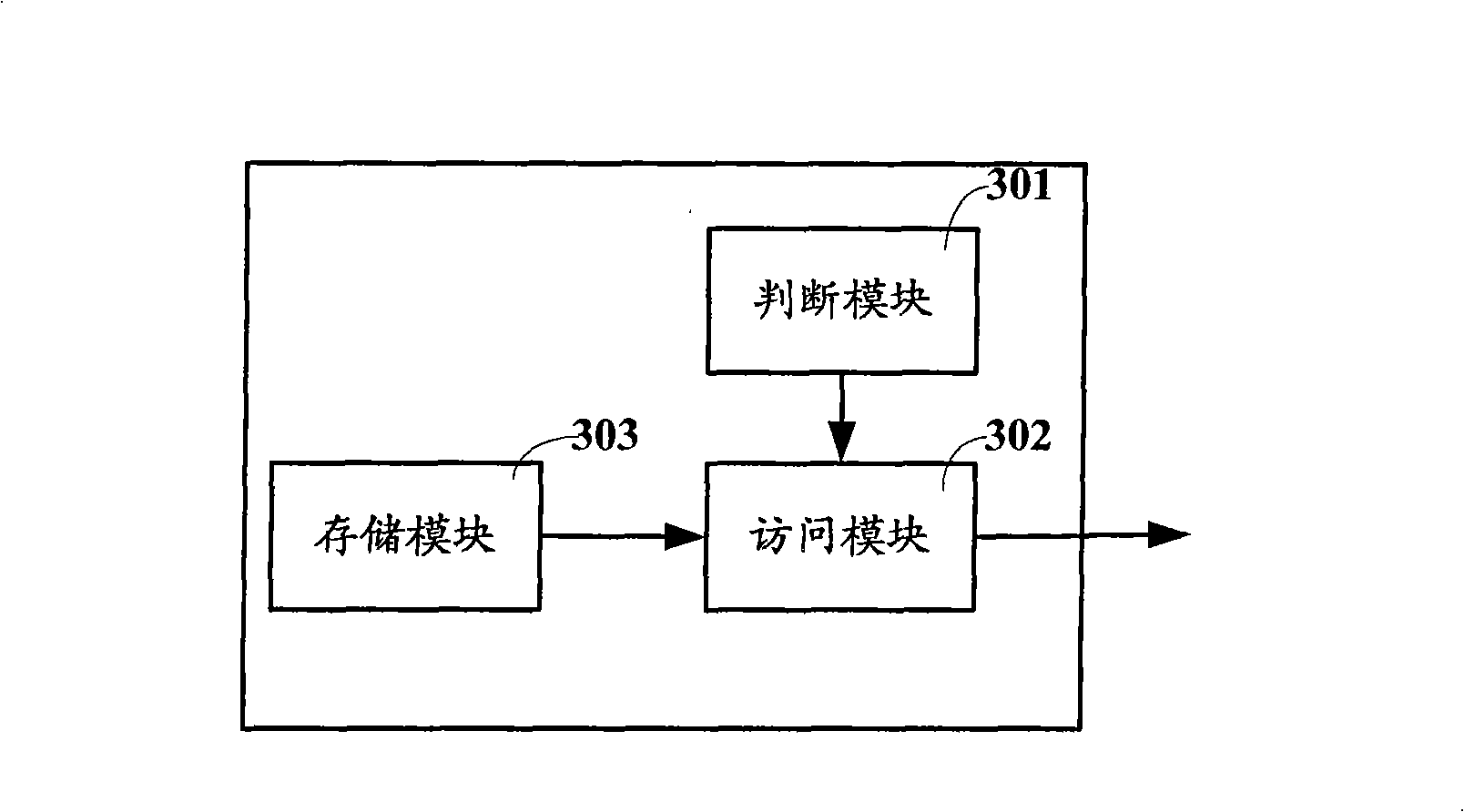
[0030] In order to be able to provide more reliable protection for the manufacturer’s programs stored in the computer storage device, the present invention proposes a method for protecting the data in the storage device. At the same time, in order to describe the technical solution of the present invention more clearly, implement The specific data in the example specifically refers to the manufacturer's program.
[0031] In the computer architecture, the computer's boot loader is composed of BIOS and the boot loader located in the storage device MBR; and the BIOS is actually a piece of firmware program.
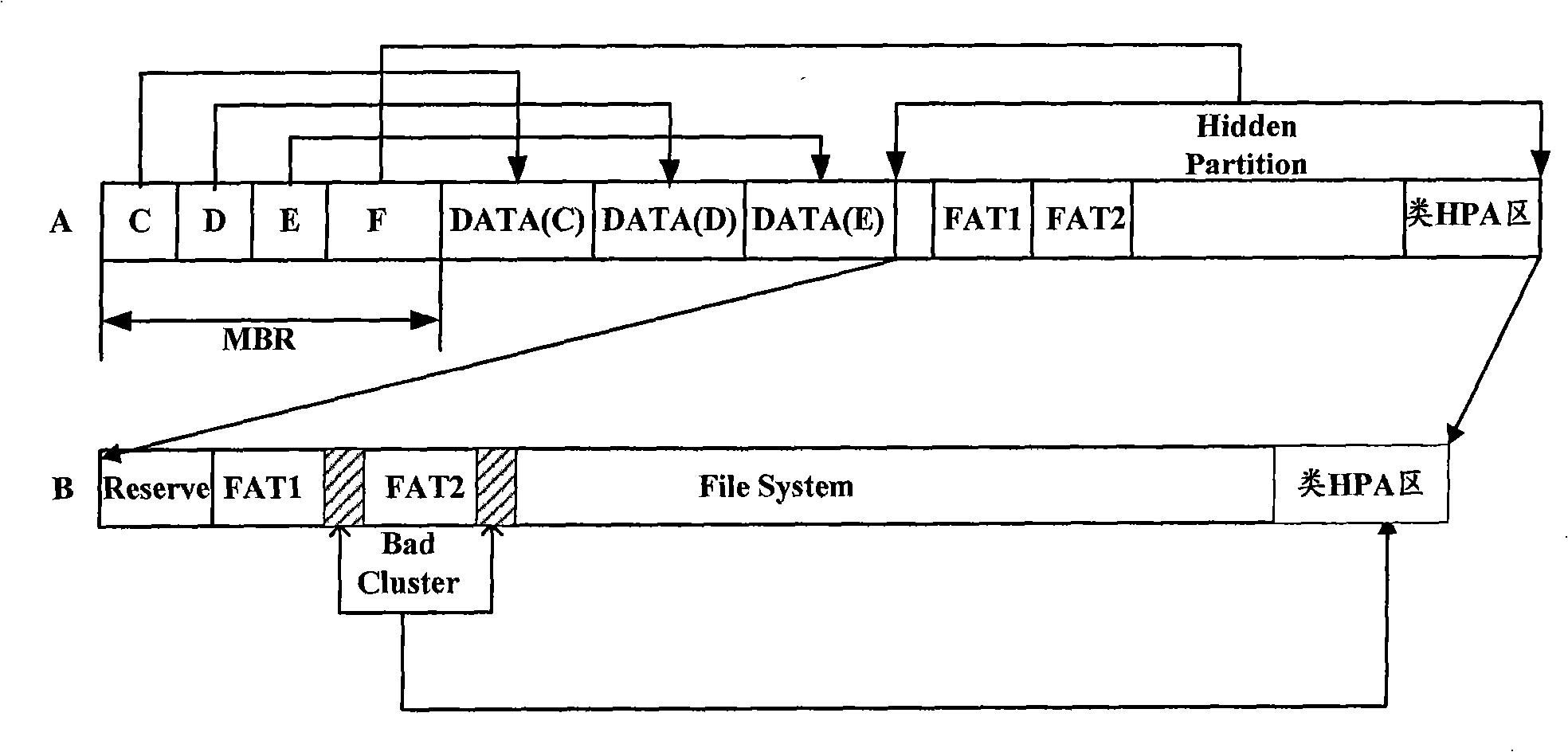
[0032] The MBR part of the storage device mainly includes the bootloader, the end flag and the partition table; the partition table is such as figure 1 As shown in A, each partition table corresponds to a partition. The number of partition tables is usually four or less than four. Each partition table contains an index pointing to the corresponding partition and several bytes of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com