Method for ciphering, deciphering and rewriting external data memory
A technology of external data and memory, applied in the direction of preventing unauthorized use of memory, printing device, printing, etc., can solve the problems of paper waste, printer P3 impact, error, etc., to avoid waste of chips and be conducive to environmental protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
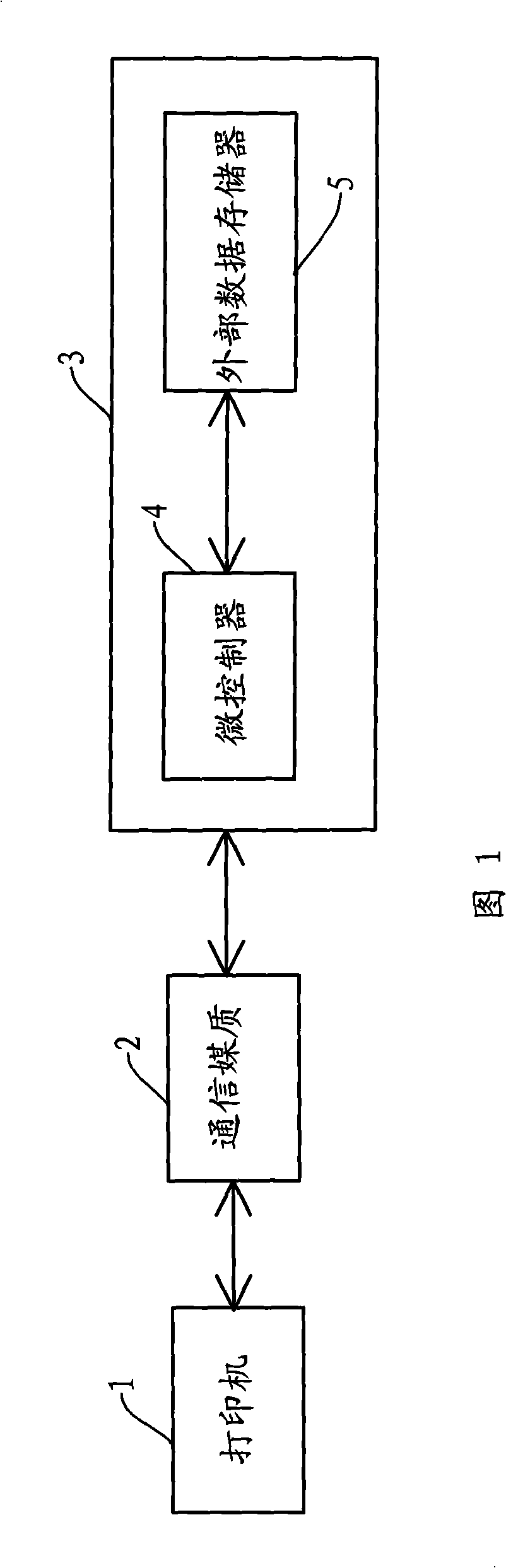
[0017] Referring to Fig. 1, Fig. 1 discloses a schematic diagram of the connection between a conventional printer and a consumable container chip. The encryption and decryption methods of the present invention are also realized according to the connection relationship between the printer and the consumable container chip in the figure. After the consumable material container is installed on the printer 1, the printer 1 will communicate with the chip 3 of the consumable material container. The printer 1 first sends information to the microcontroller 4, and the microcontroller 4 judges the information. If it is necessary to write or read data to the external data storage 5, the microcontroller 4 will write to the external data storage 5. The operation of encrypting data and decrypting the read data.
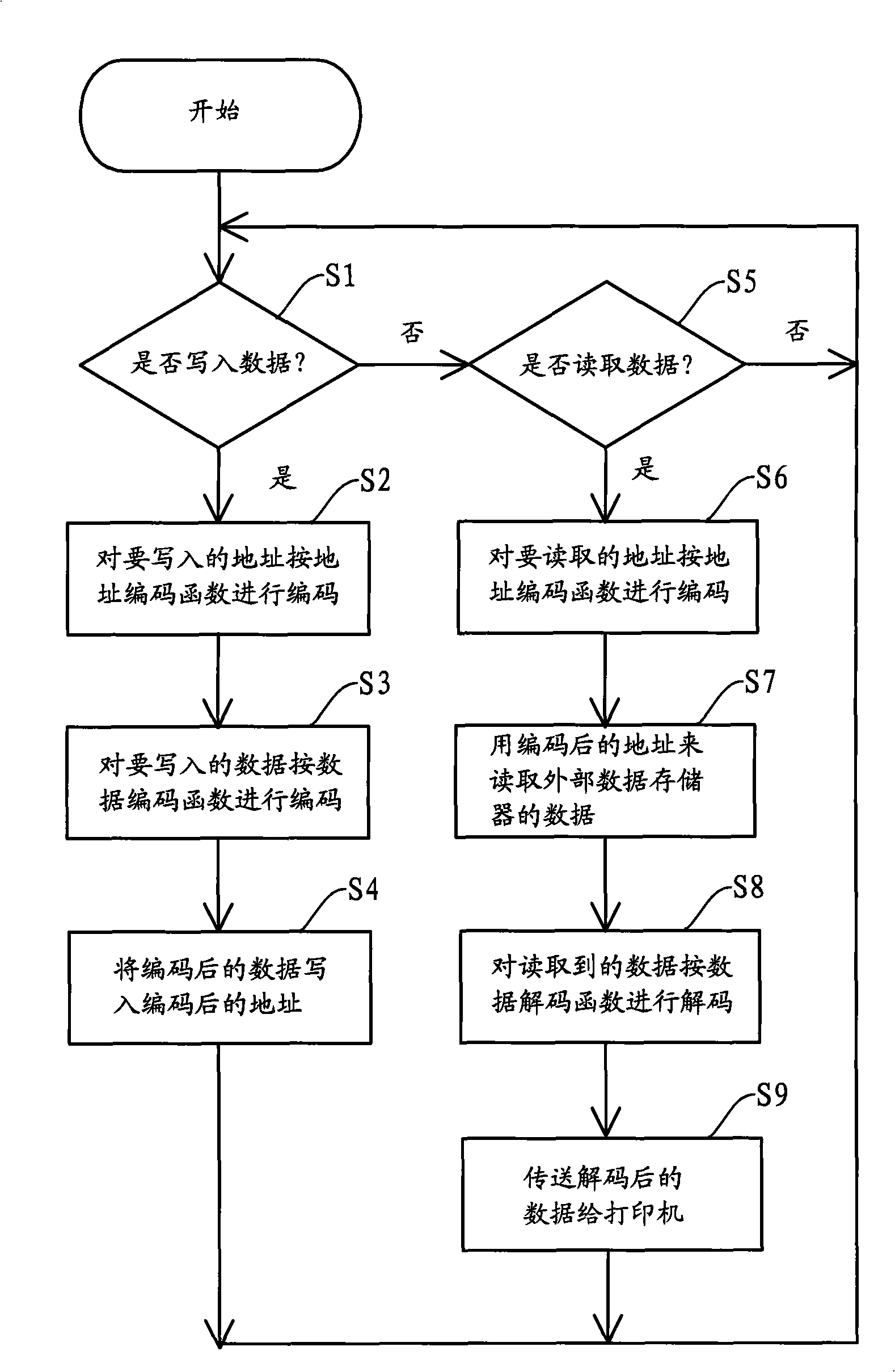
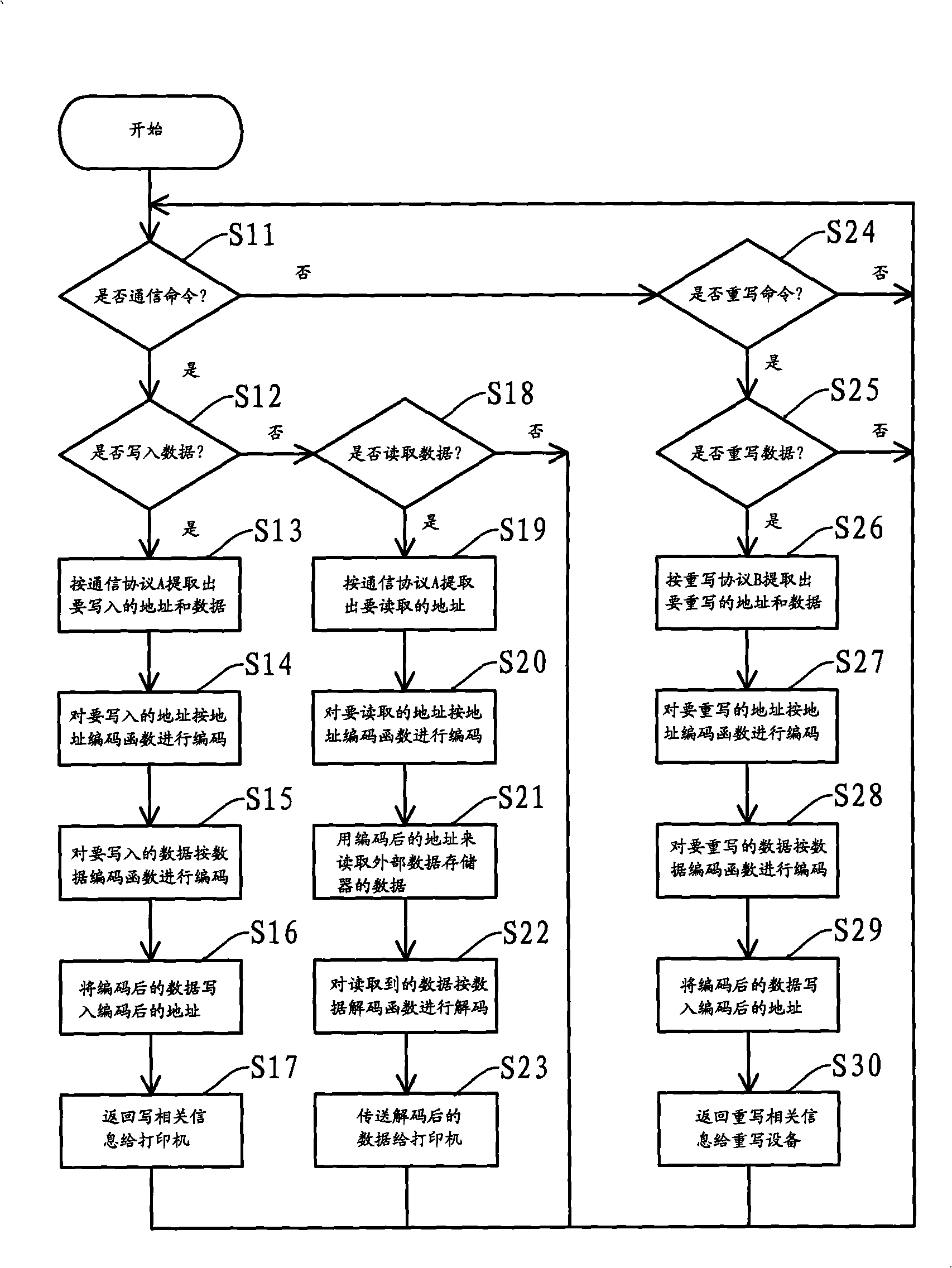
[0018] see figure 2 , figure 2 The work flow chart of the microcontroller in the first embodiment of the encryption method and the decryption method of the present invention is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com