Secure device, information processing terminal, server, and authentication method
A security device and server technology, applied in key distribution, can solve problems such as complex calculation of authentication information, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
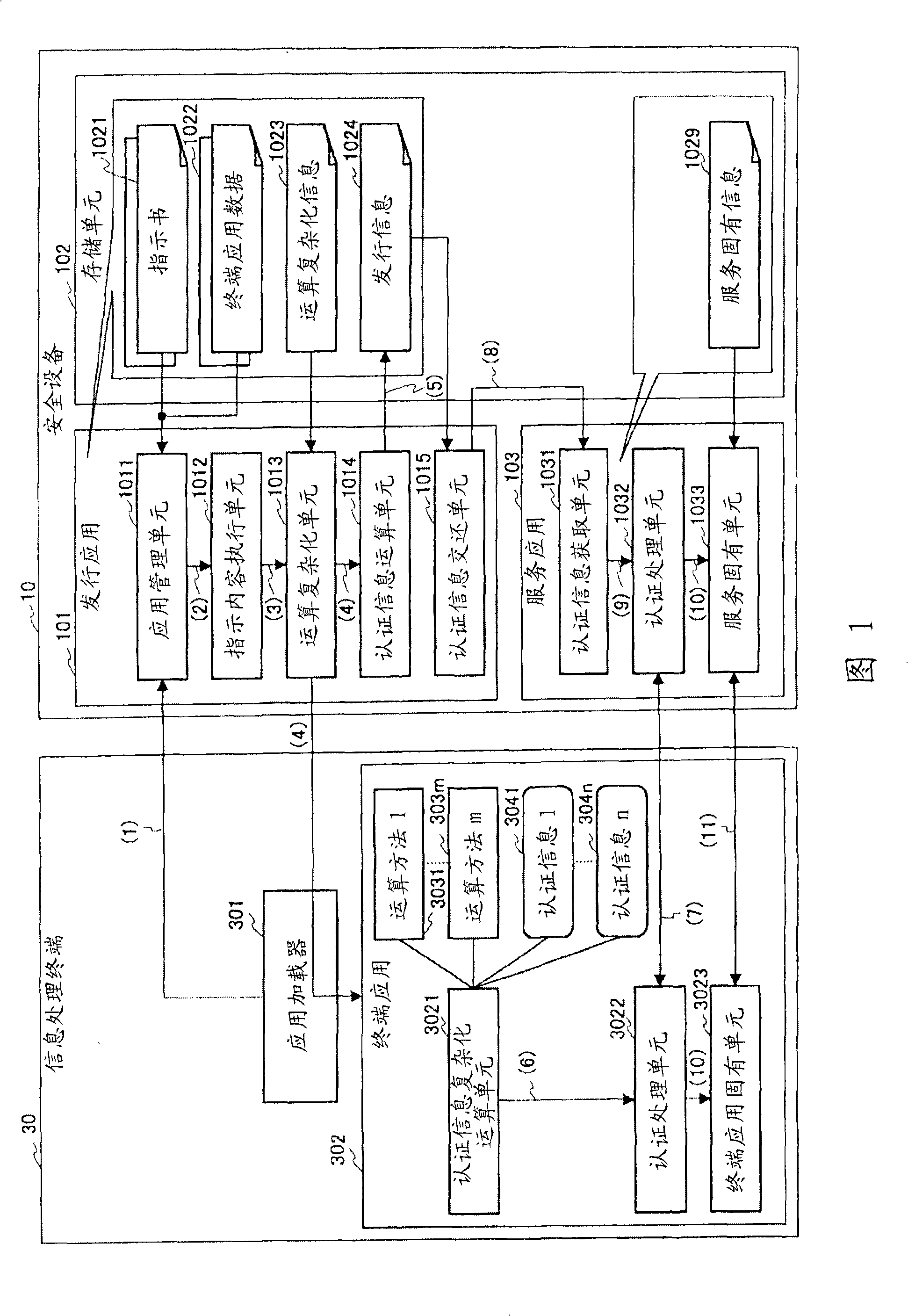
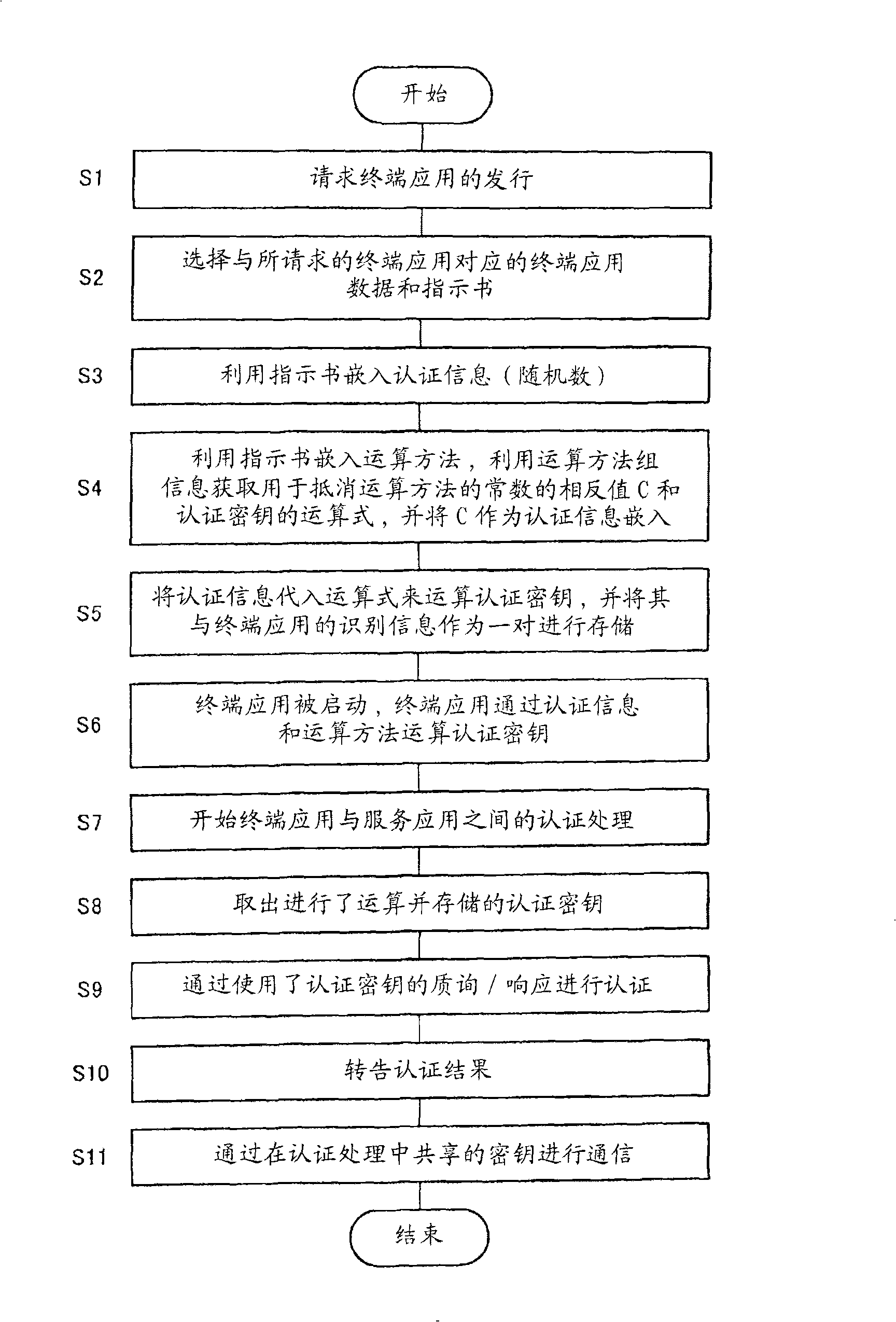
[0044] In Embodiment 1 of the present invention, a security device for holding terminal applications will be described. This security device is installed in the information processing terminal, and when the information processing terminal requests the start-up of the terminal application, the terminal application embedded with the method (method) and authentication information for performing the authentication information complicated by the security device is released. operation. Then, if the information processing terminal starts the terminal application, the terminal application calculates the authentication key through more complicated calculation and processing than the security device, and then the security device calculates the authentication key through simpler calculation and processing, so that there is a connection between the security device and the information processing terminal. authentication using the authentication key.
[0045] FIG. 1 is a diagram showing a ...
Embodiment approach 2
[0095] The configurations of information processing terminal 30 and security device 10 in Embodiment 2 are the same as in Embodiment 1 in FIG. 1 . However, the content of the calculation complexity information 1023 and the operation of the calculation complexity unit 1013 that processes the content are different.
[0096] First, an outline of the principle of making the operation of the authentication information complex operation section 3021 more complex and the operation of the authentication information operation section 1014 simpler will be described. To simplify the description, the number n of authentication information 3041 to 304n is set to 4, and the authentication information 3041 to 3044 are respectively set to a, b, c, and d. However, unlike the first embodiment, the authentication information 3041 is not set as the inverse value C. At this time, the values of the authentication information 3041 to 3044 are all 64 bits. In a specific example of Embodiment 2, t...
Embodiment approach 3
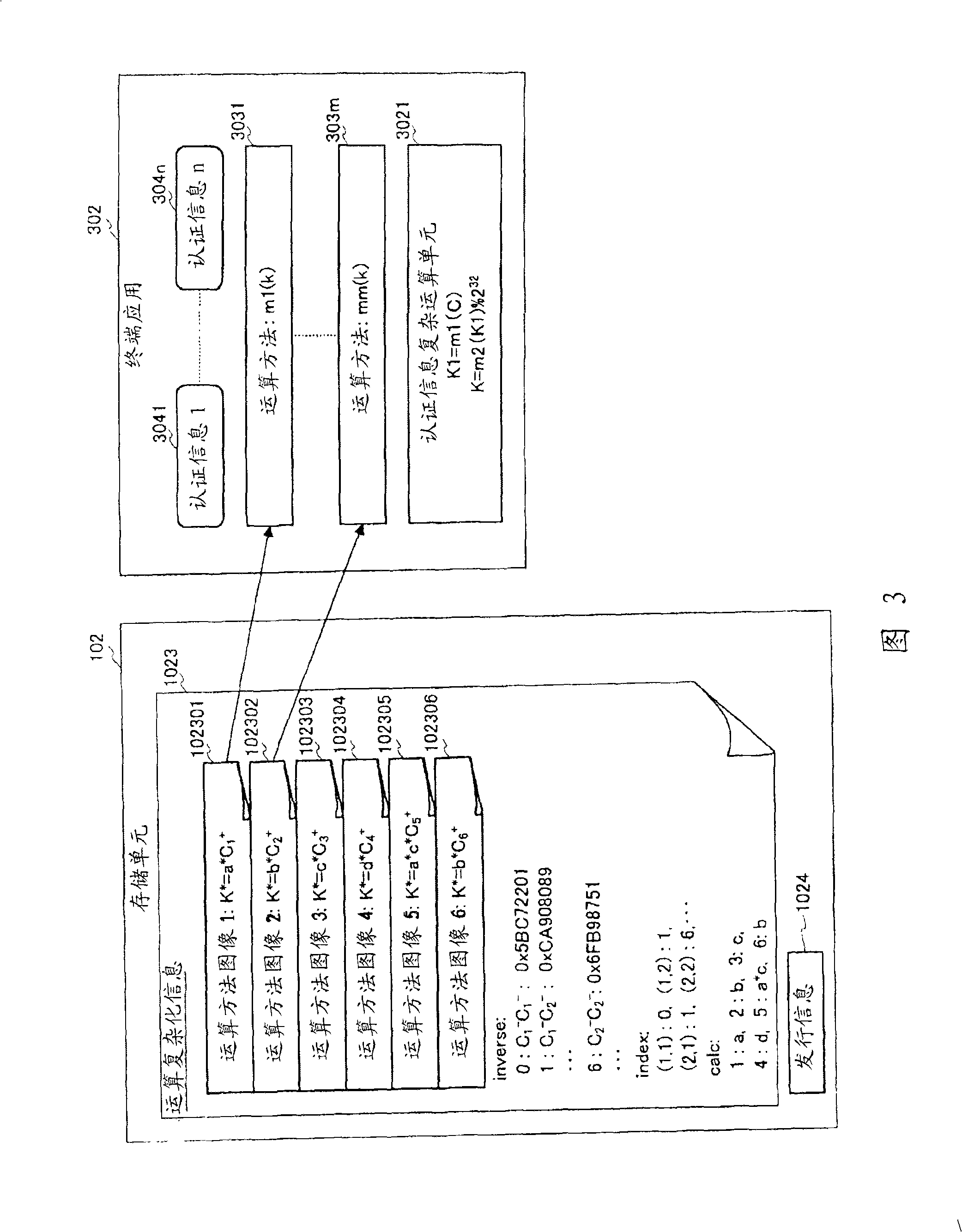
[0112] The configurations of the information processing terminal 30 and the security device 10 according to the third embodiment are the same as those of the information processing terminal 30 and the security device 10 according to the first embodiment shown in FIG. 1 . However, the contents of the computation complexity information 1023 and the operation of the computation complexity section 1013 processing the contents are different from those of the first embodiment.
[0113] FIG. 6 is a configuration diagram showing an example of the calculation complexity information 1023 used by the calculation complexity means in Embodiment 3 of the present invention. The calculation complexity information 1023 will be described using FIG. 6 . The difference from Embodiment 2 is that not only a pair that is multiplied to 1, but also a pair of arbitrary numbers can be described. The result of the multiplication is the information of 'answer' of 'pair2' in Figure 6, which indicates that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com