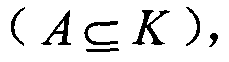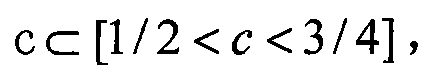Method for fast searching, positioning and matching access control list
An access control list, fast technology, applied in the field of computer communication, can solve problems such as not supporting fast matching well, achieve fast search, positioning and matching access control list, high efficiency, and reduce product cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
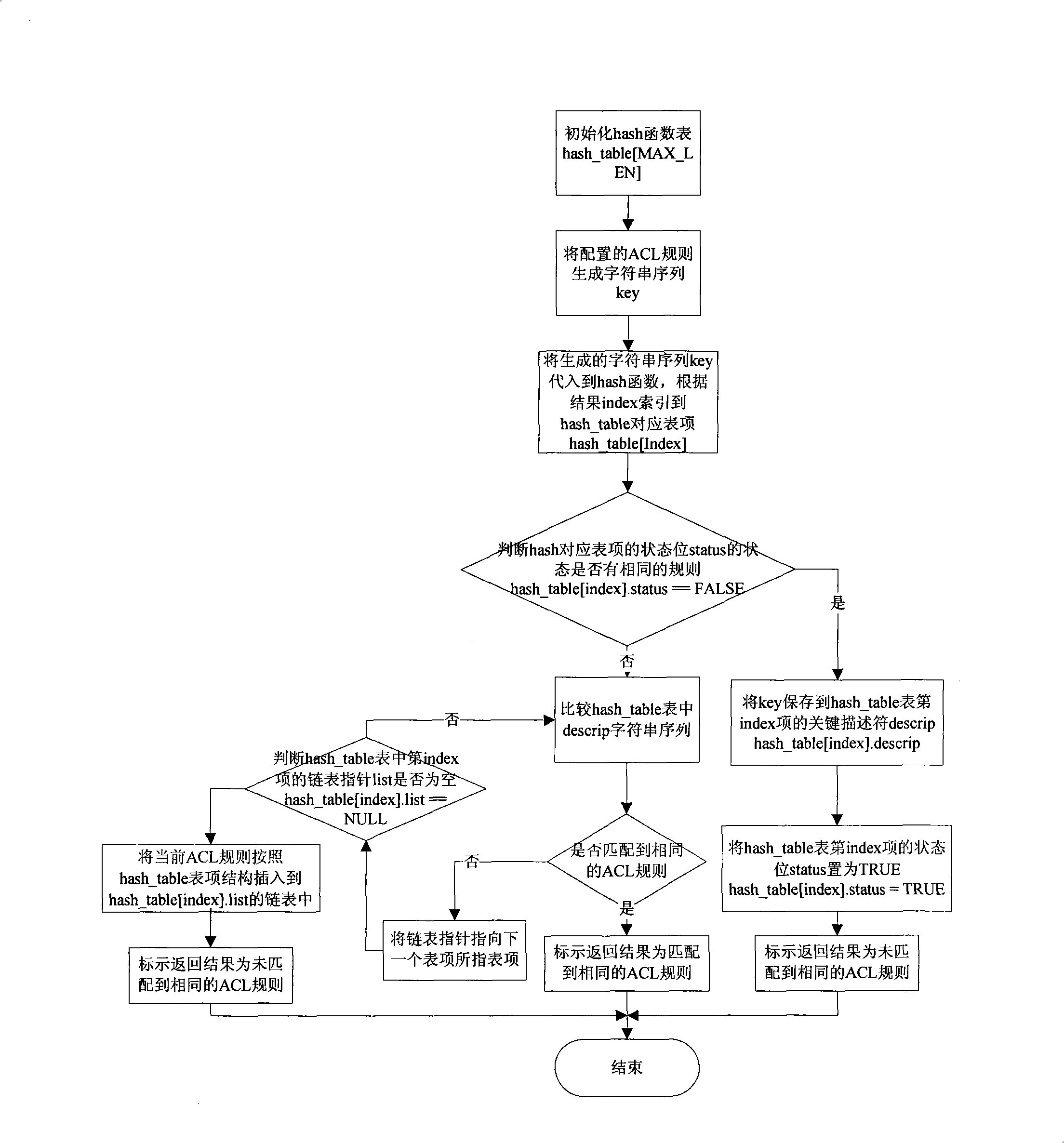
[0020] According to the hash principle, there are three ways to avoid hash conflicts: first, make the bucket capacity of the hash table much larger than the actual entries that need to be accommodated; second, maintain a linked list for the hash table to save all conflicting entries; Third, design a hash function that can correspond one-to-one. Usually for the above method 1, we choose the parameters in this way, if the key value space of the hash table is K, and the value space of the actual key value is A ( A ⊆ K ) , The bucket size space of the hash table is T, then the hash should satisfy the relationship of |A|<c|T|, and c represents the scaling factor. In practical applications, take the proportional factor c to satisfy the relationship 1 / 2<c<3 / 4 and try to make the bucket size T of the hash table a prime value, so that the hash table can be evenly distributed, and hash table c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com