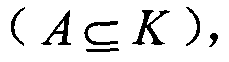Patents
Literature
191 results about "Function computation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
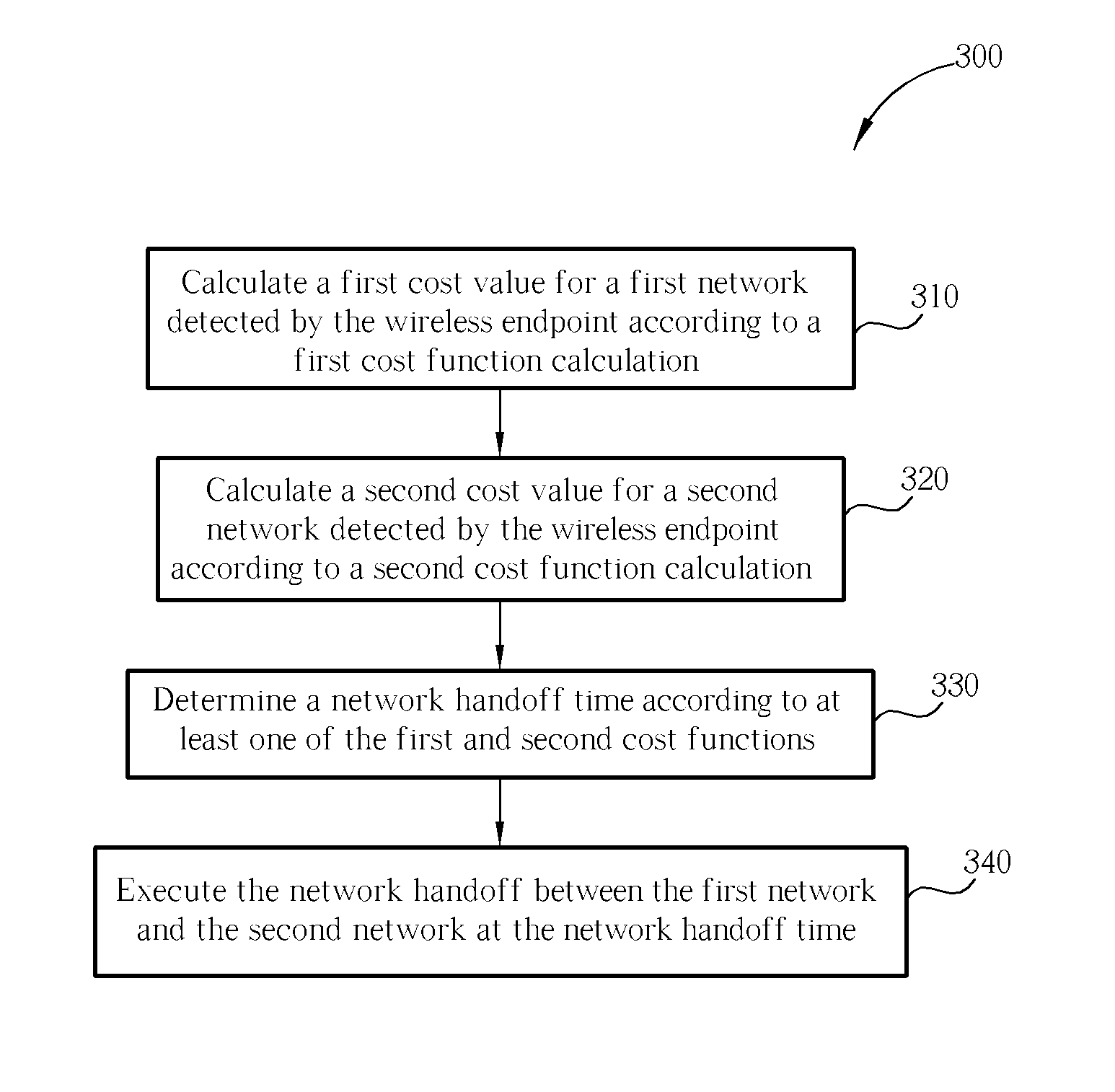
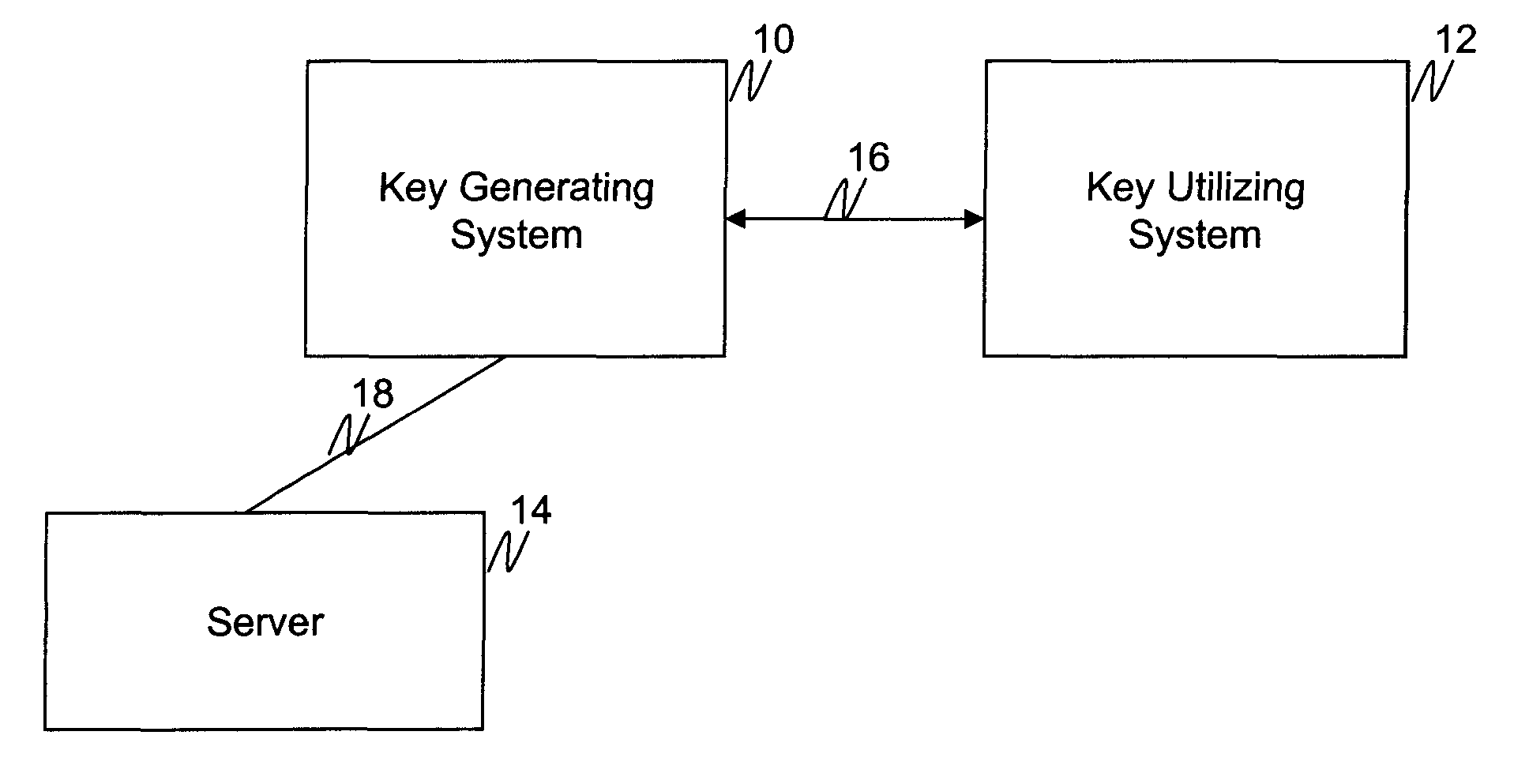
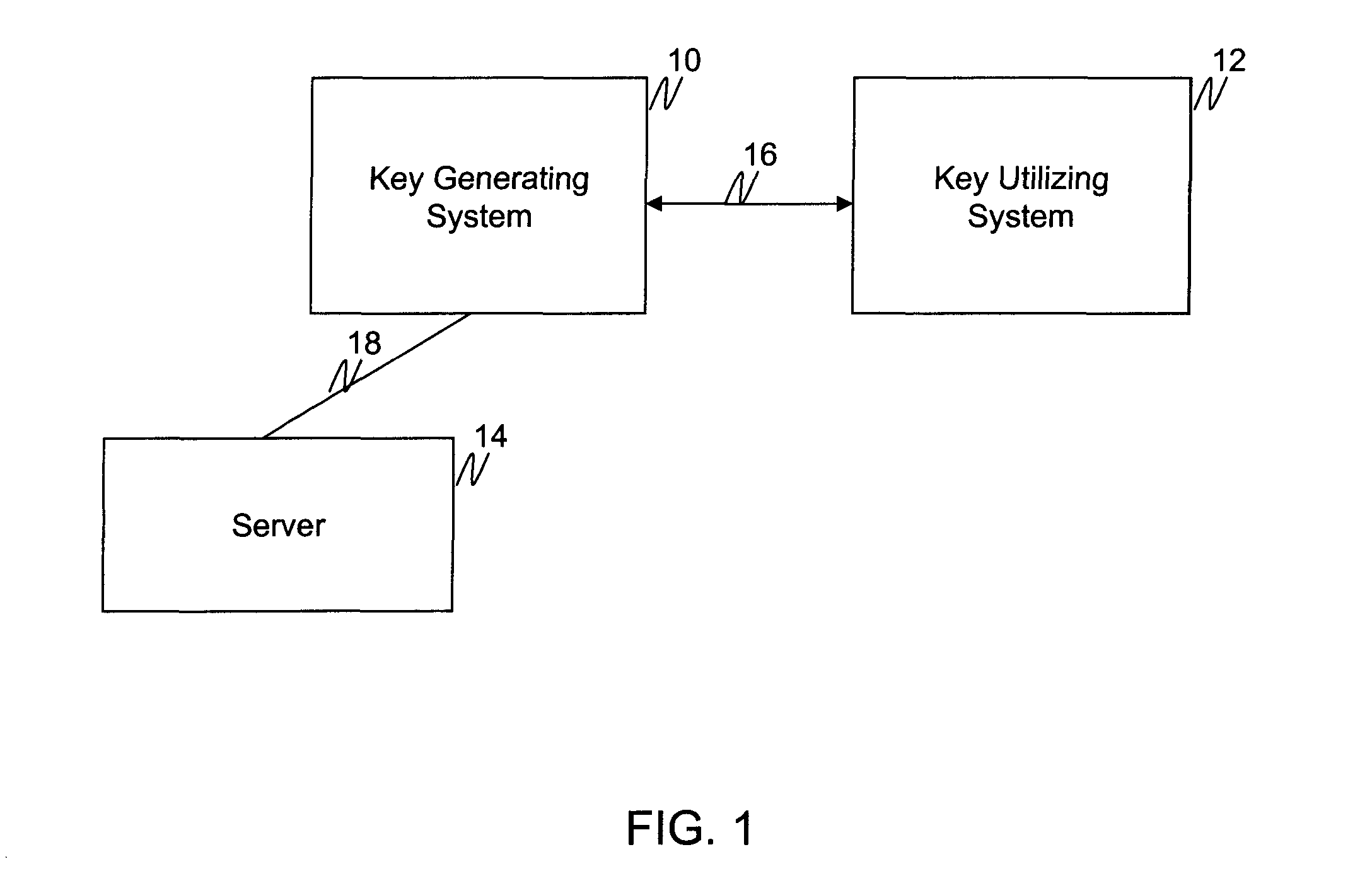
Method and device for cost-function based handoff determination using wavelet prediction in vertical networks
InactiveUS20070160007A1Determine feasibilityMore concise, accurate, and overall qualitativeAssess restrictionTelephonic communicationNetwork communicationDistributed computing
A method for performing a network handoff between different network communication providers for a wireless endpoint includes: calculating a first cost value for a first network detected by the wireless endpoint according to a first cost function calculation, calculating a second cost value for a second network detected by the wireless endpoint according to a second cost function calculation, utilizing a cost function based wavelet predictor to determine a network handoff time according to at least one of the first and second cost functions, and executing the network handoff between the first network and the second network at the network handoff time, wherein the cost function based wavelet predictor is for predicting future trends of various network characteristics.
Owner:ZYXEL
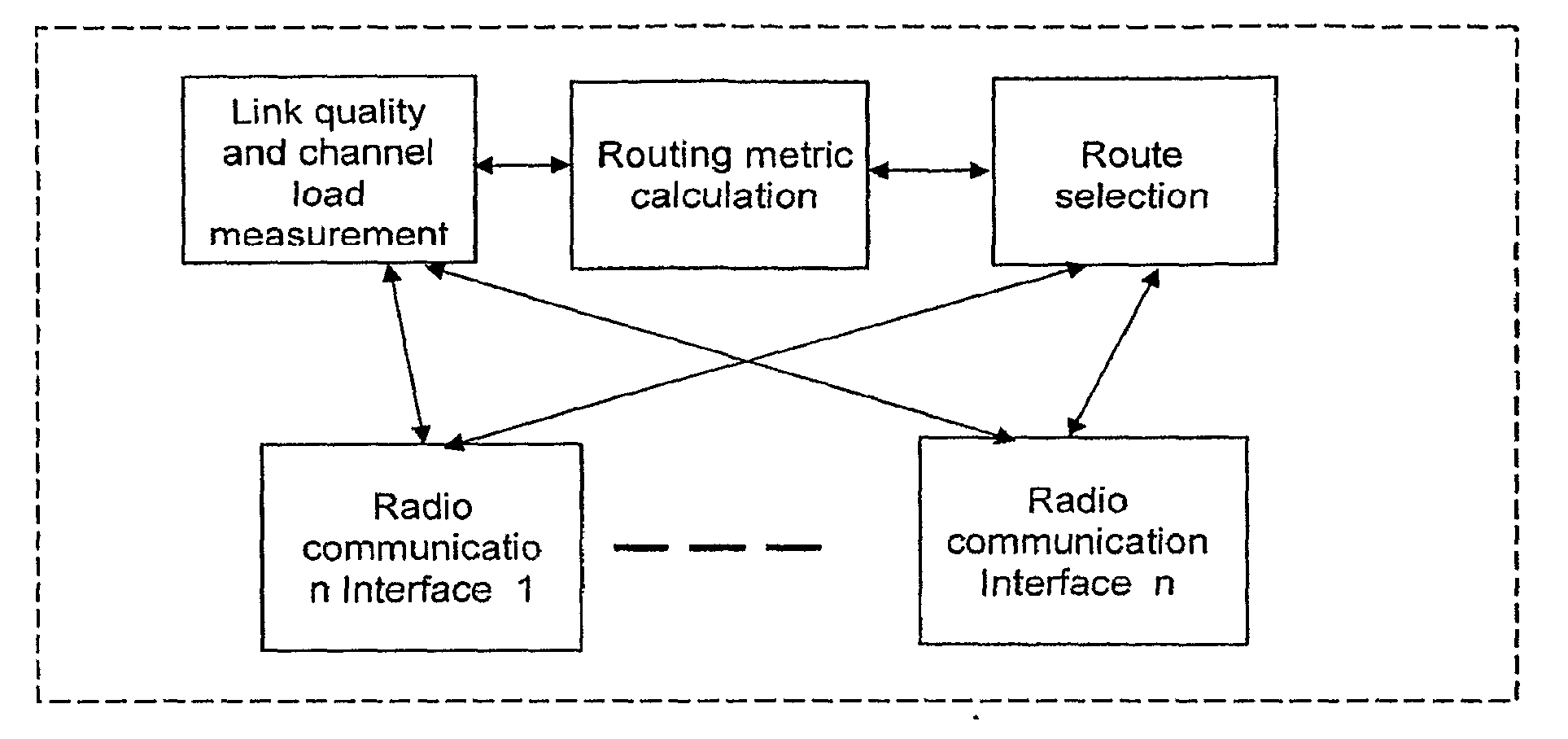
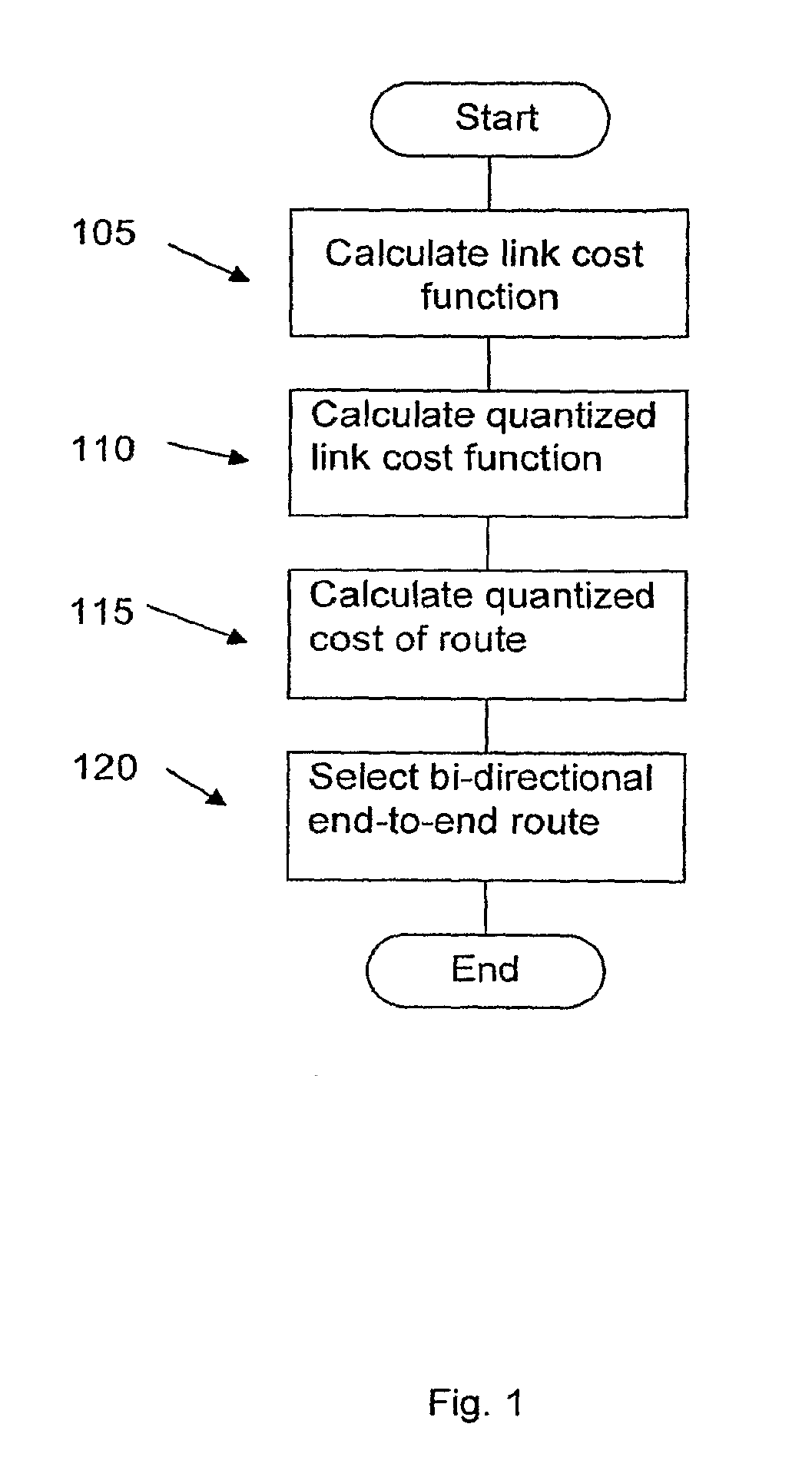
Radio and bandwidth aware routing metric for multi-radio multi-channel mutli-hop wireless networks
ActiveUS20100074194A1Improve routing performanceRapid responseError preventionTransmission systemsDistributed computingWireless network
A method and system are described for establishing an end-to-end route for data to traverse a wireless network, including calculating a link cost function, calculating a quantized link cost function using the calculated link cost, function, calculating a quantized cost of each of a plurality, of end-to-end routes for data to traverse the wireless network, wherein the plurality of end-to-end routes include routes between a same set of nodes in the wireless network, wherein, the quantized cost of each of the plurality of end-to-end routes for data to traverse the wireless network is performed using the quantized link cost function and selecting one of the plurality of end-to-end routes, for data to traverse the wireless network based on the quantized cost of each of the plurality of end-to-end routes. Also described is a node in a wireless network configured to participate in the establishment of a bi-directional end-to-end route for data to traverse the wireless network.
Owner:THOMSON LICENSING SA
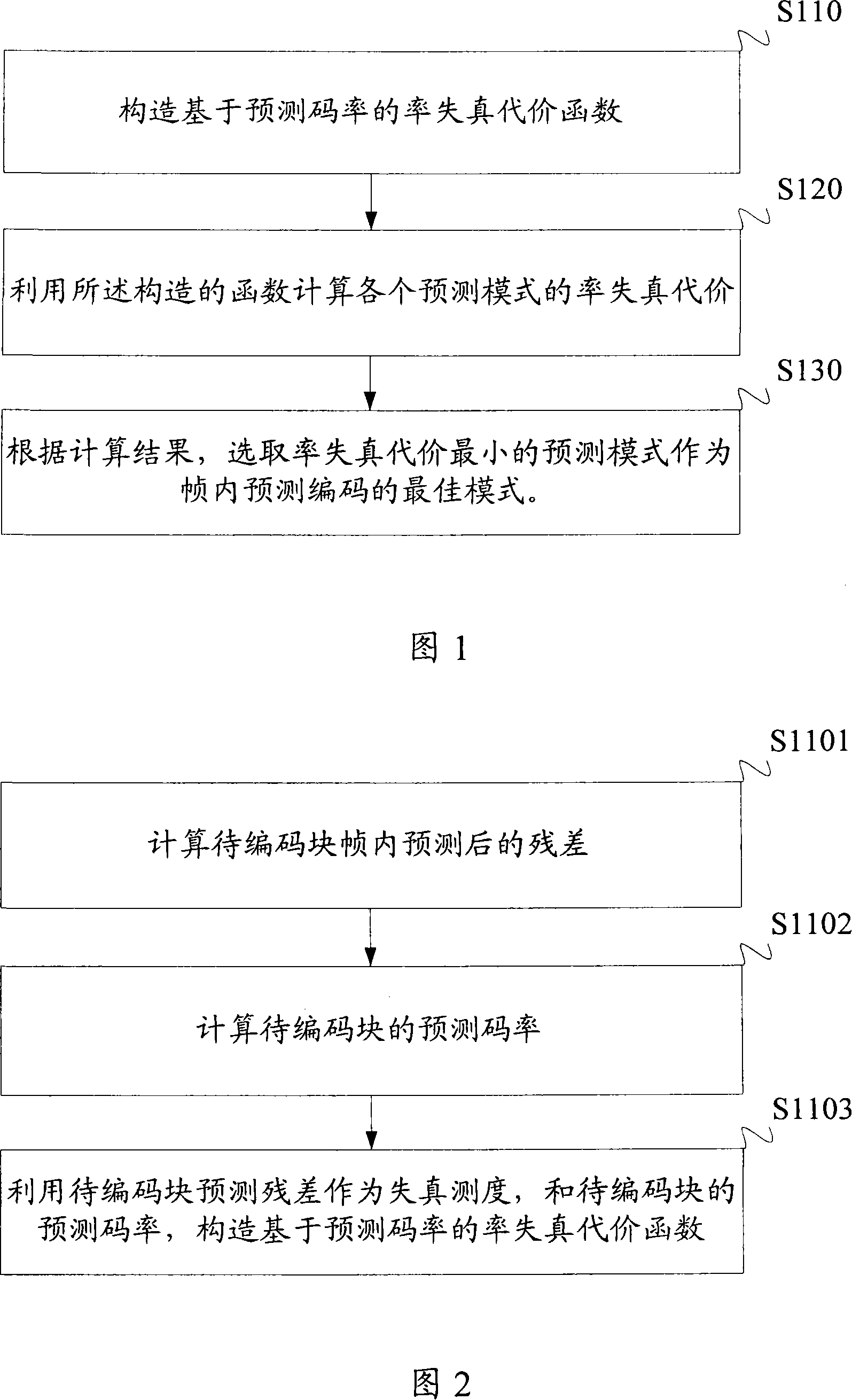
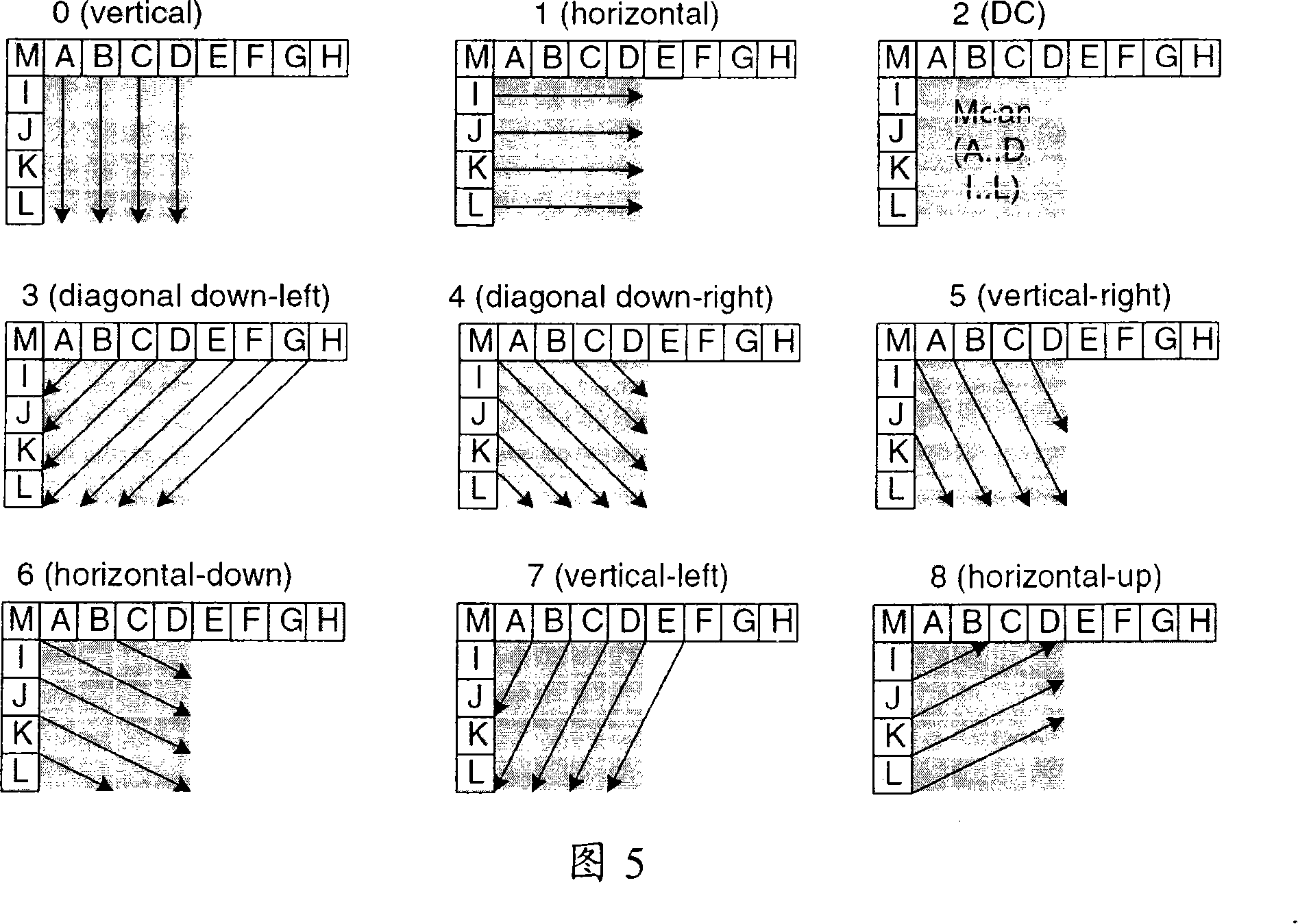
Intraframe prediction coding optimum mode selecting method and apparatus for video coding
InactiveCN101141649ASignificant changeSimple calculationPulse modulation television signal transmissionDigital video signal modificationComputer architectureModel selection
The present invention relates to a selecting method for the optimal mode of the intra prediction coding used for video frequency coding, which belongs to the video frequency coding and decoding field. The steps of the method are that a rate-distortion cost function is constructed on the basis of a prediction code rate; the rate-distortion cost of each prediction mode is calculated by the structured function, and the prediction mode with minimum rate-distortion cost is selected as the optimal mode of the intra prediction coding according to the calculating result. Proportionally, the present invention also provides a device for the selecting of intra prediction coding optimal mode of the video frequency coding. The present invention effectively avoids actually coding every blocks during the rate-distortion optimizing process on the basis that the selected mode is closer to the optimal mode of the original rate-distortion optimization model selecting, and greatly improves the coding efficiency on the precondition of ensuring little change on the code rate and the PSNR of the coding and the full searching method.
Owner:PEKING UNIV +1
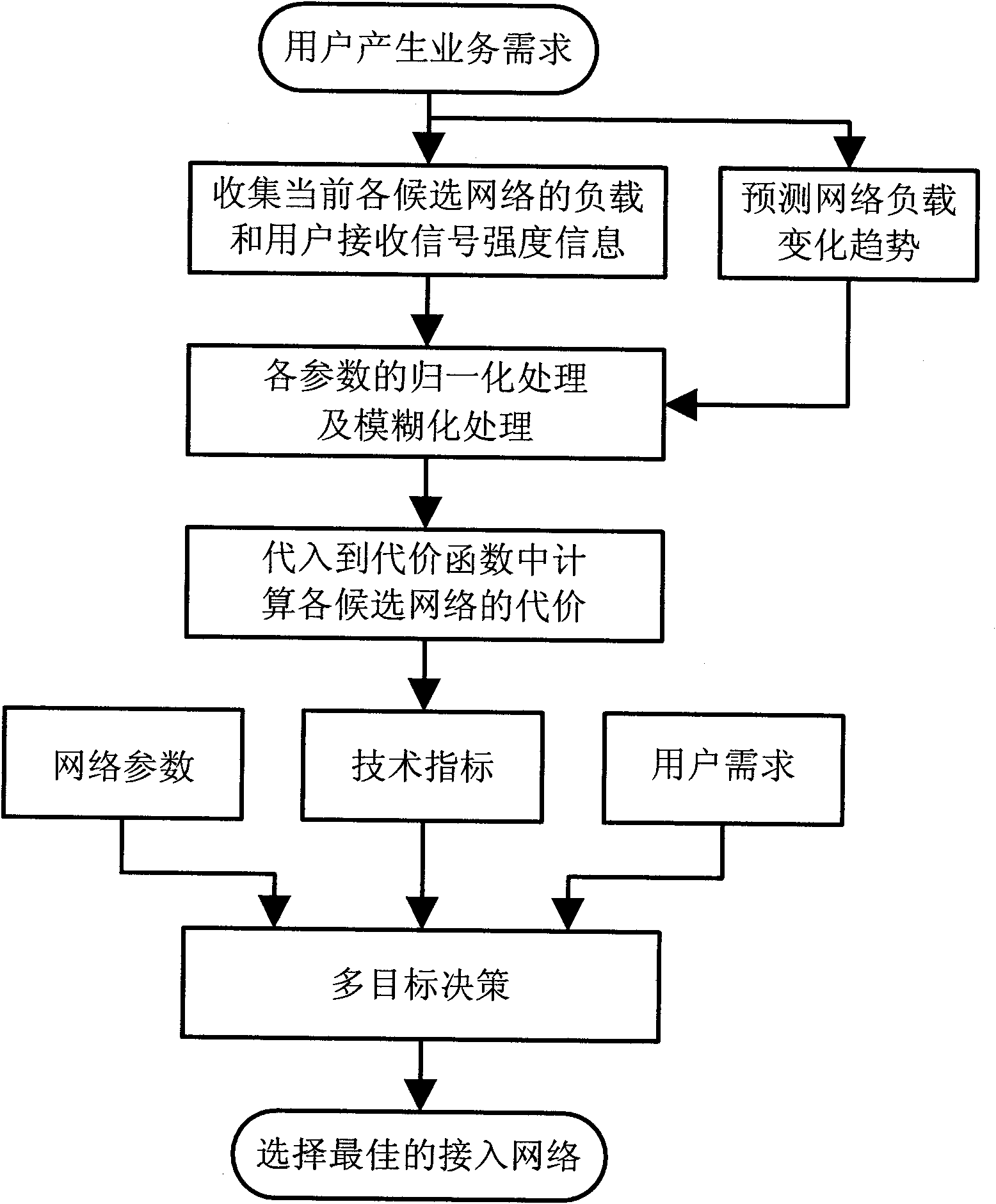
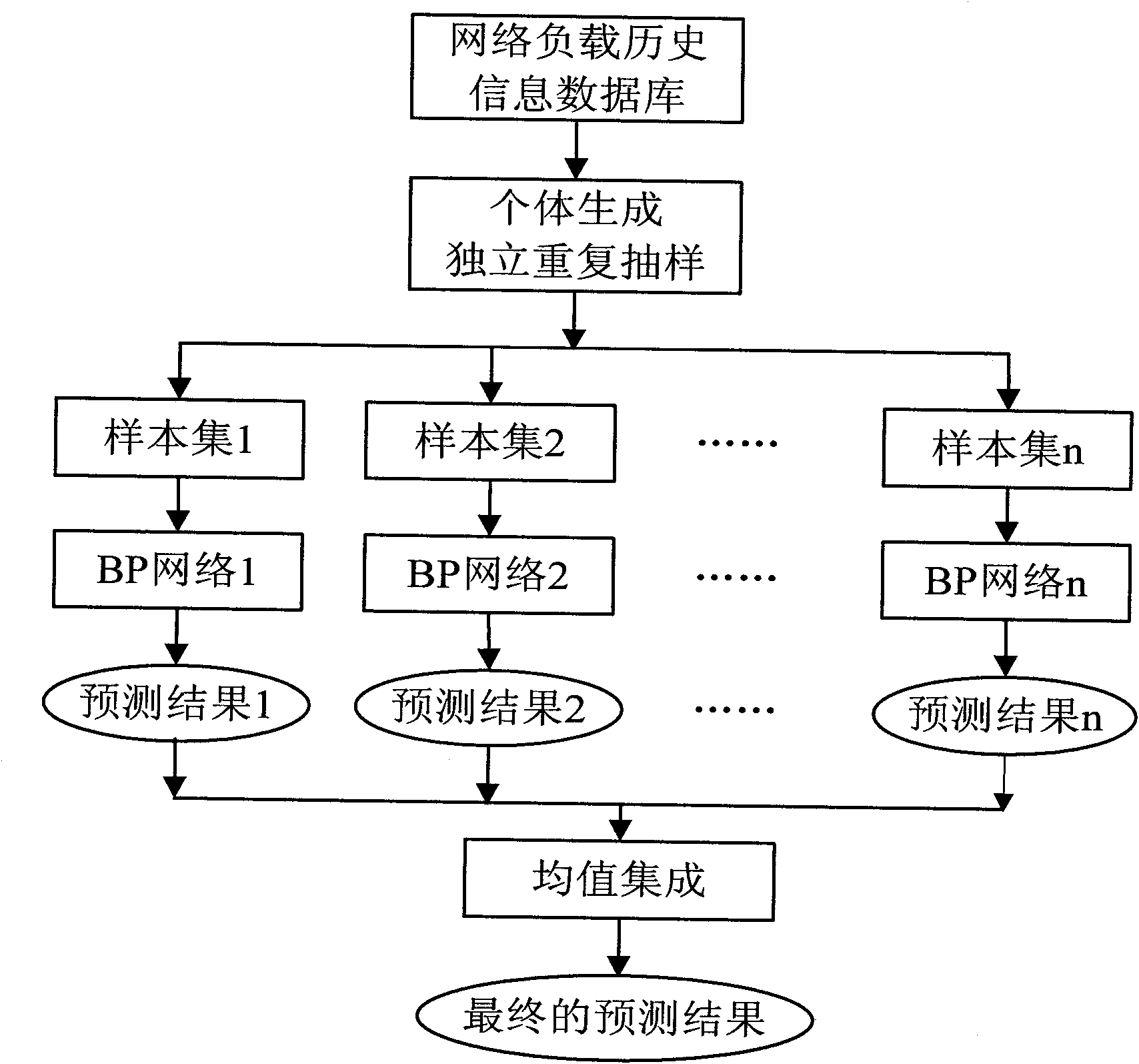
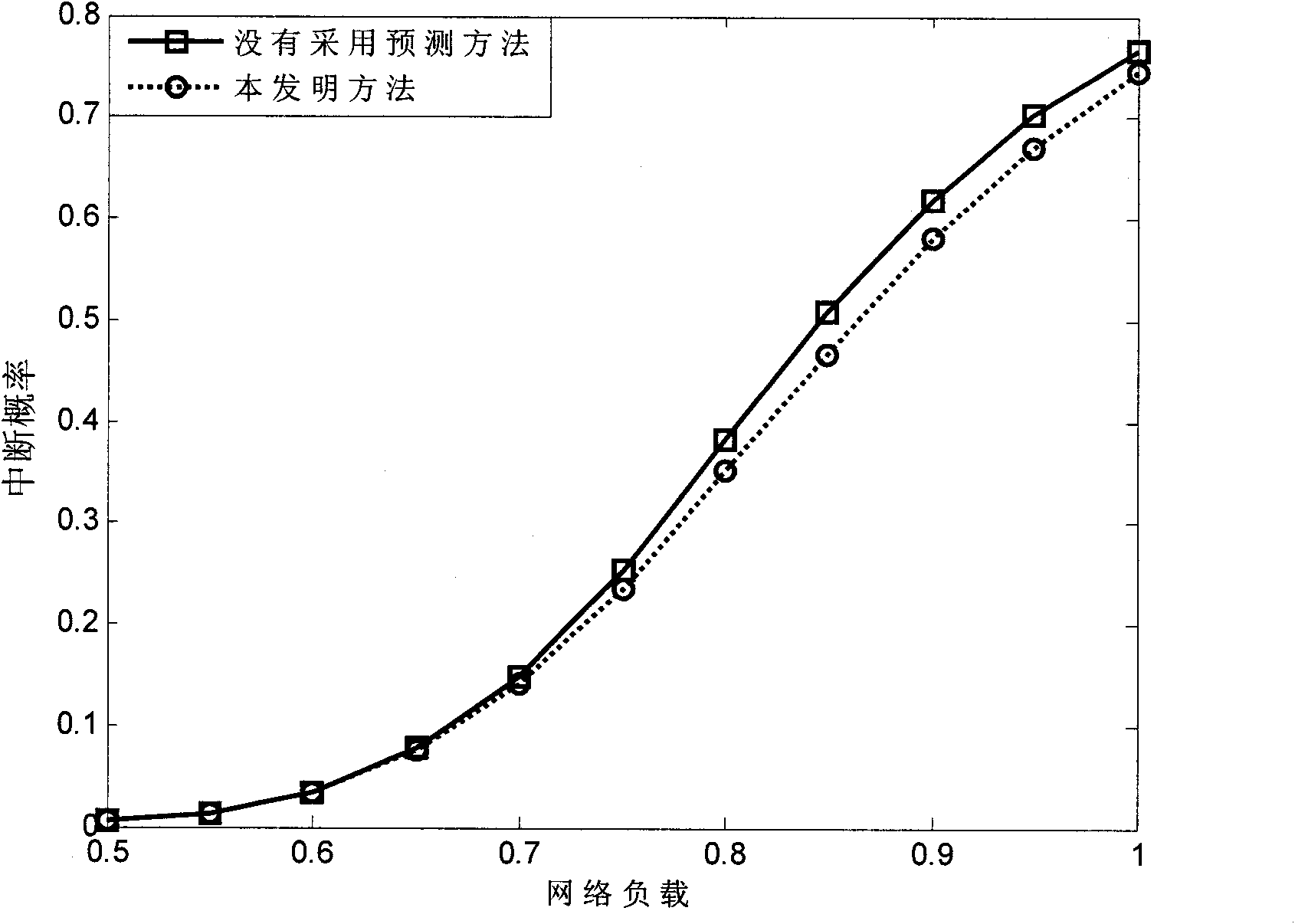
Access network selection method based on neural network and fuzzy logic
InactiveCN101860885AReduced probability of outageReduce blocking rateAssess restrictionUser needsCurrent load
The invention discloses an access network selection method based on a neural network and a fuzzy logic, which mainly solves the problem that the future load change and the parameter uncertainty of a candidate network in the network selection process influence user performance. The method comprises the following implementation processes of: collecting the current load information of a located network and user received signal intensity information by the base station of each candidate network; forecasting the change tendency of the future load of each candidate network by utilizing an integrated BP (Back-Propagation ) neural network; processing the network load and the user received signal intensity information by utilizing the normalization fuzzy logic; calculating the technical indexes of the candidate network by utilizing cost functions; comprehensively balancing the technical indexes, the network parameters and the user requirements of the network by utilizing a multi-objective decision to obtain the proper access degree of each candidate network; sending the proper access degree of the network in which the base station is to the user through a wireless enabler by each base station; and after the user compares, selecting the candidate network with the maximum proper access degree as an objective network. The invention can effectively reduce the blocking probability when the user accesses to the network and the interrupting probability in the serving process to realize a function for the user to select the best access network.
Owner:XIDIAN UNIV
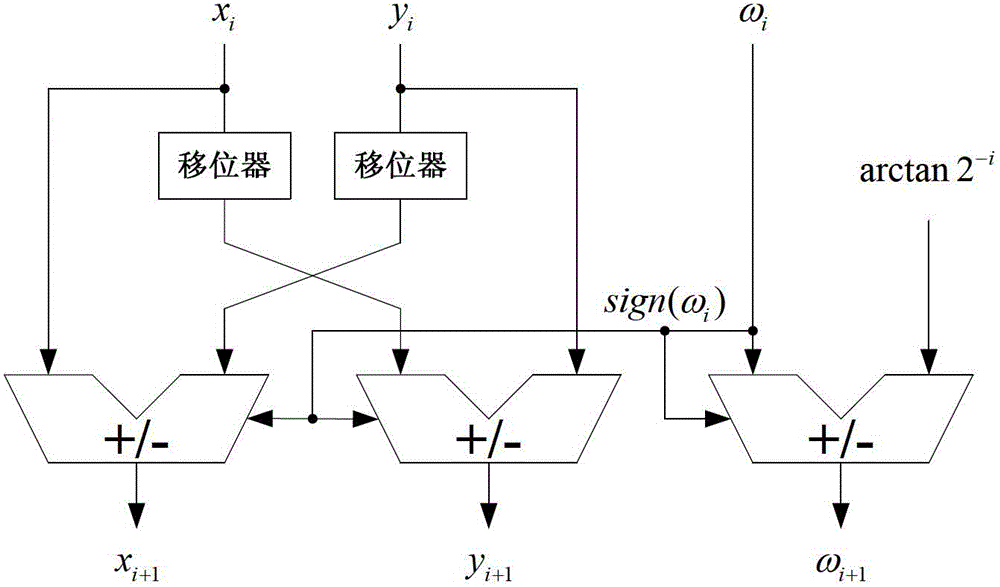
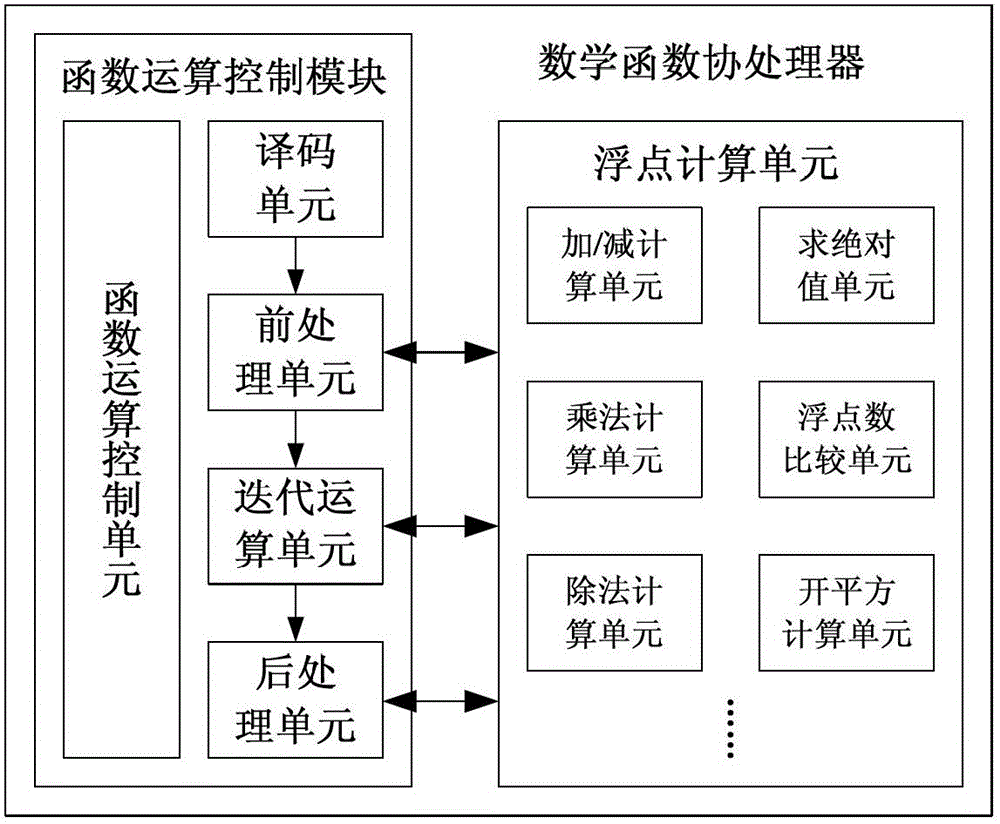
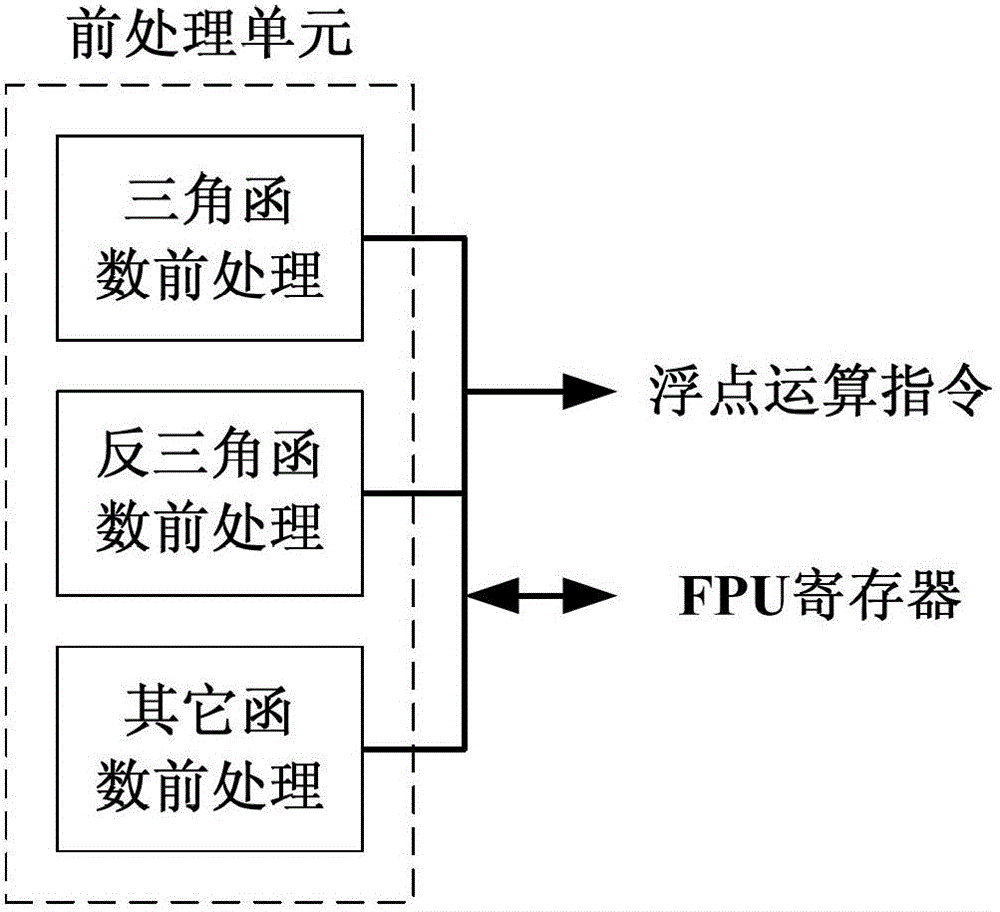
Elementary transcendental function operation method based on floating point arithmetic unit and coprocessor for method
InactiveCN102722469AThe calculation method is simple and flexibleSimple structureDigital data processing detailsComplex mathematical operationsCoprocessorSimulation
The invention provides an elementary transcendental function operation method based on a floating point arithmetic unit and a coprocessor for the method. According to the method, a coordinate rotation digital computer (CORDIC) algorithm is decomposed into a function operation control part and a floating point calculation part; the function operation control part is used for finishing an operation control function of the CORDIC algorithm; and the floating point calculation supports absolute value solution, addition / subtraction, multiplication, division, evolution and comparison operation of floating point number, and a general register used in the floating point calculation can be read and written by a function operation control module. A special mathematical function calculation component is redesigned as required in the conventional method, so the conventional method is complex in control and structure and high in consumption of hardware resources. By adding the function operation control module with a simple structure, transcendental function operation is realized by using the existing floating point operation instruction based on the existing floating point arithmetic unit; and the function operation control module is simple in structure and easy to implement and apply, and can support calculation of trigonometric and anti-trigonometric functions, hyperbolic function, exponential function and logarithmic function.
Owner:XI AN JIAOTONG UNIV
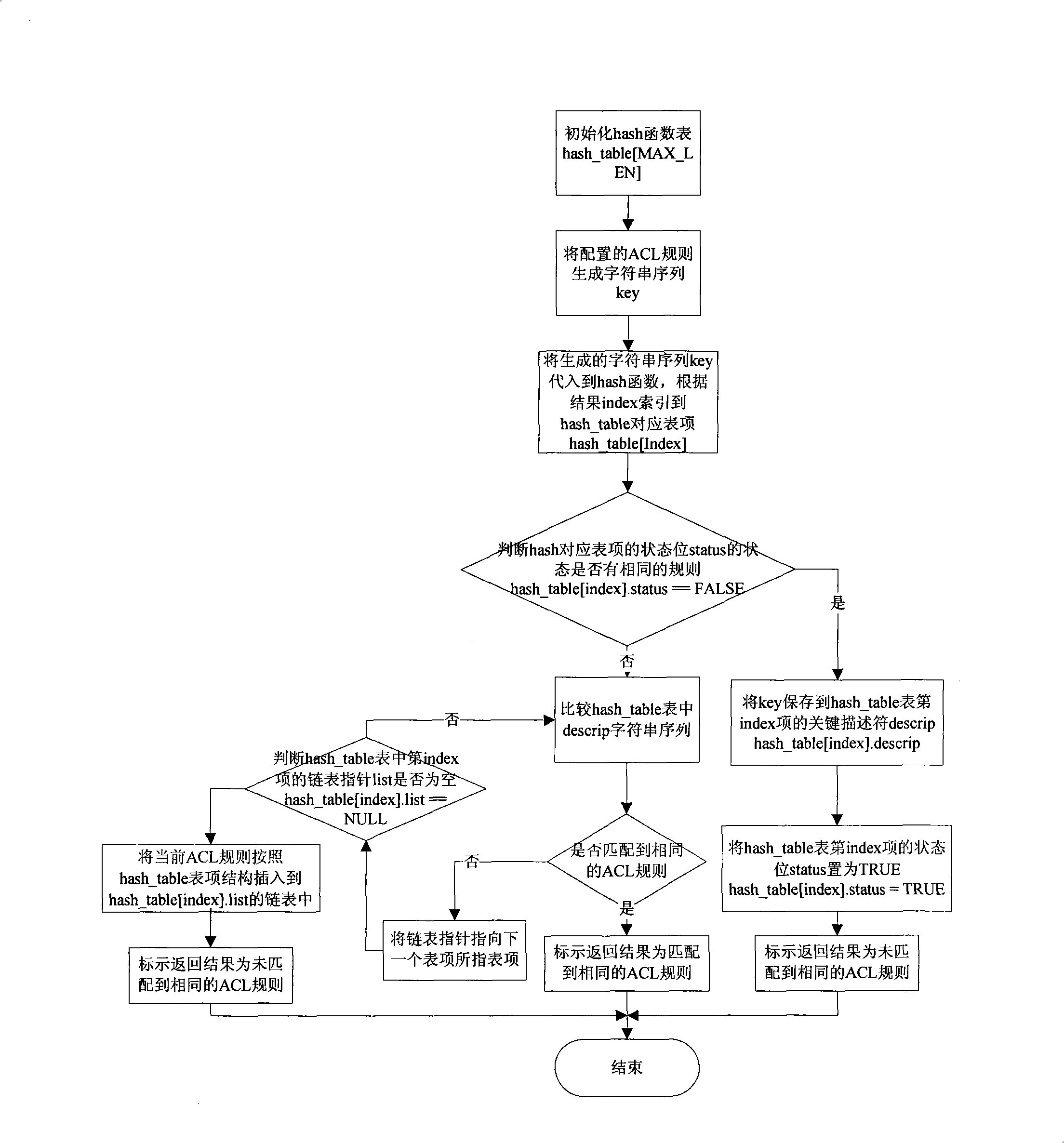
Method for fast searching, positioning and matching access control list
InactiveCN101345694AEasy to implementImprove efficiencyData switching networksSpecial data processing applicationsTheoretical computer scienceHash table
The invention provides a method of fast finding fixing and matching an access control list, comprising: serializing information character strings in all matching fields of ACL rule to be arranged, initializing hash table [MAX LEN] table; using the ACL rule character string sequence as a Key of a hash function, carrying corresponding character string Key and hash basket size prime into the function for computation, obtaining has function hashed value (index); indexing corresponding items of the ACL rule in the hash_table according to the computing result. According to the invention, hash algorithm is simple, efficiency is high, hash distributing performance is excellent. In addition, a chain table is maintained for HASH table, a method of storing all conflicting list items can better solve the problem of balancing space and time in practical application, thereby excellently advancing system efficiency without wasting huge space.
Owner:SHANGHAI BROADBAND TECH
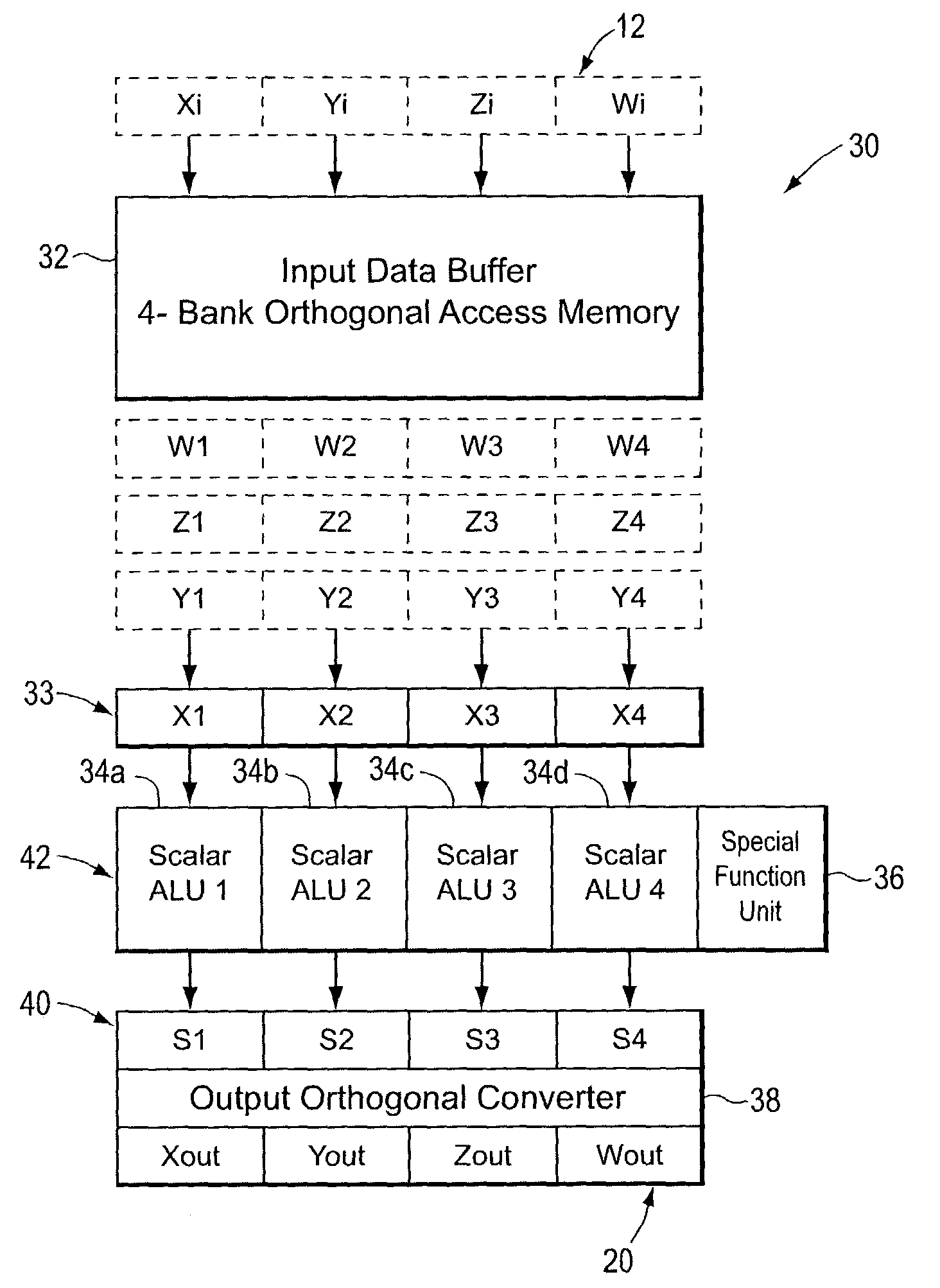
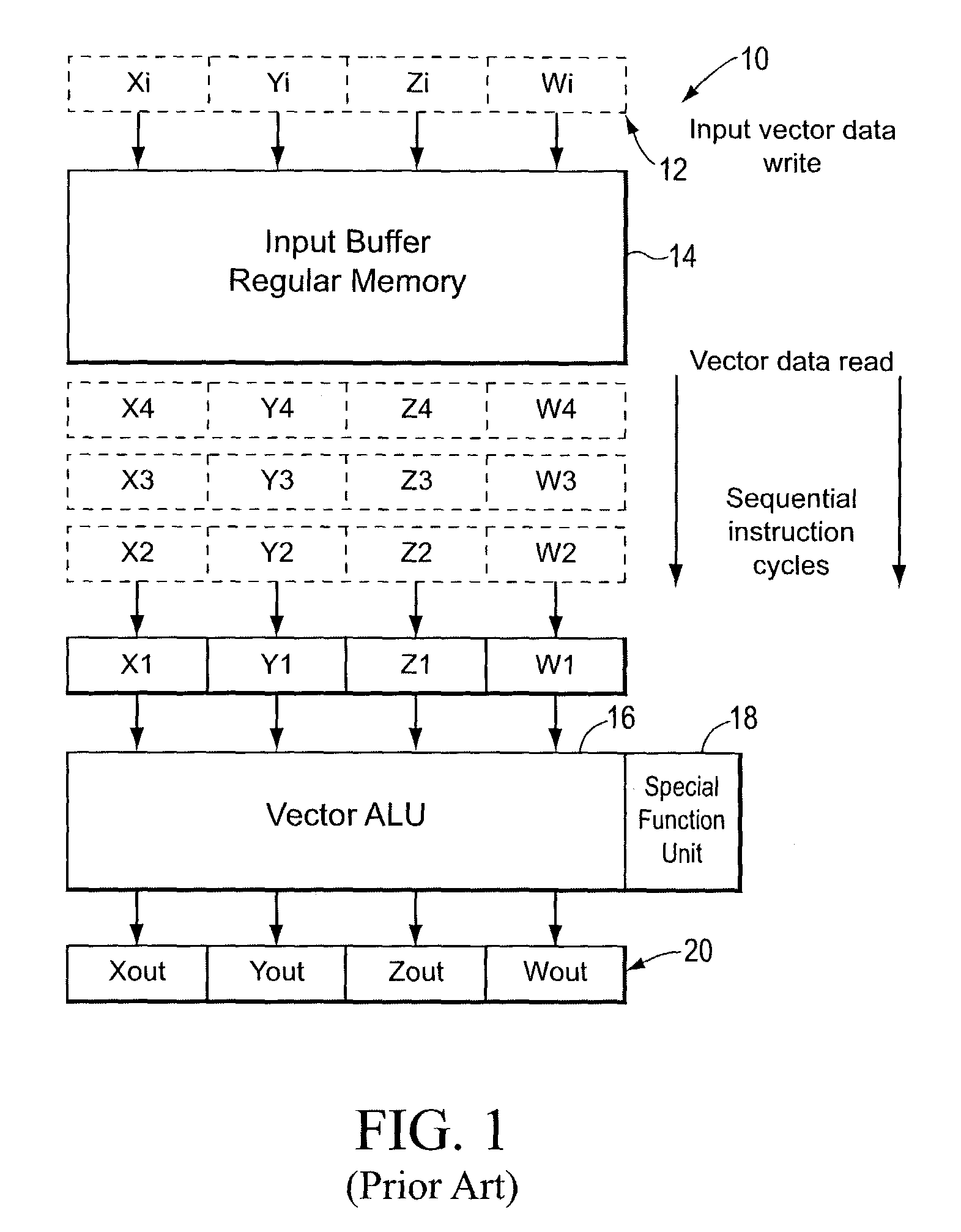
SIMD processor with scalar arithmetic logic units
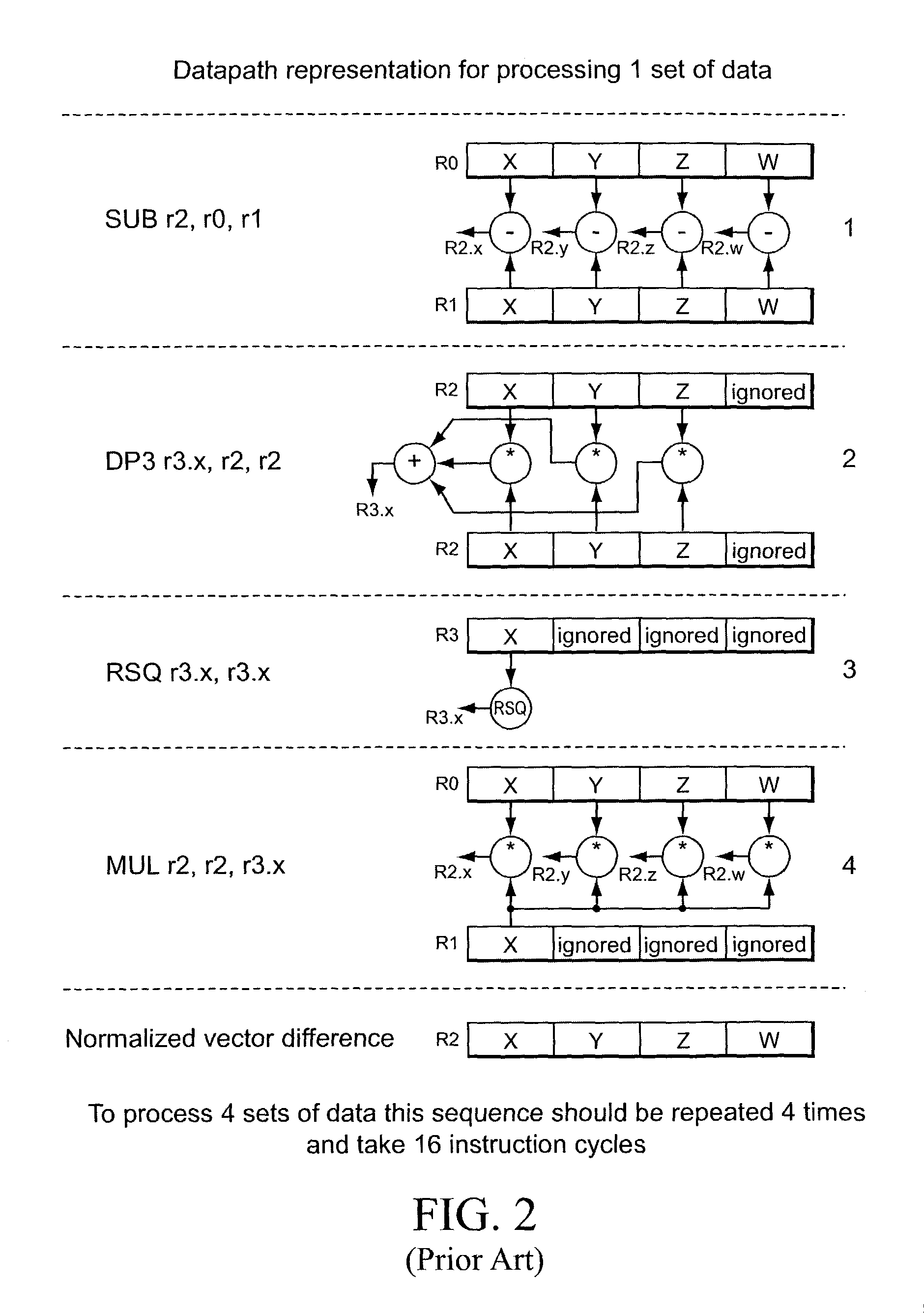
ActiveUS7146486B1Shorten the timeAvoid confictConcurrent instruction executionArchitecture with single central processing unitArithmetic logic unitScalar processor
A scalar processor that includes a plurality of scalar arithmetic logic units and a special function unit. Each scalar unit performs, in a different time interval, the same operation on a different data item, where each different time interval is one of a plurality of successive, adjacent time intervals. Each unit provides an output data item in the time interval in which the unit performs the operation and provides a processed data item in the last of the successive, adjacent time intervals. The special function unit provides a special function computation for the output data item of a selected one of the scalar units, in the time interval in which the selected scalar unit performs the operation, so as to avoid a conflict in use among the scalar units. A vector processing unit includes an input data buffer, the scalar processor, and an output orthogonal converter.
Owner:S3 GRAPHICS
Dynamic cluster based multi-objective programming wireless sensing network routing algorithm
InactiveCN101119303AReduce lossMeet Qos service requirementsEnergy efficient ICTNetwork topologiesNetworked Transport of RTCM via Internet ProtocolRouting algorithm
The present inventionprovides a multi-objective programming radio sensing network routing arithmetic based on the dynamic cluster, essentially comprising the following steps: 1) inputting the basic information of the sensor network, calling the first energy-consumption pattern and accounting the energy consumed by the whole network for once data transmission, the best cluster-head data kopt; 2) calling the dynamic cluster pattern, setting the variables and class number of the dynamic cluster pattern, the variable of the cluster is the coordinate of the node, and the class number is the best cluster-head data kopt, defining the indicator function of the comprehensive evaluation: C(P)=w1f(P)-w2W(P)+w3D(P), according to the indicator function, accounting the costs of the routes from the source node to the destination node, after that, selecting the link with the smallest cost as the route from the source node S to the destination node D. The present invention provides a multi-objective programming radio sensing network routing arithmetic based on the dynamic cluster which has quick accounting speed and comparatively small energy consumption and reduces the complexity, effectively satisfying the requirements to the network OoS service.
Owner:ZHEJIANG UNIV OF TECH
Short message verification system and method
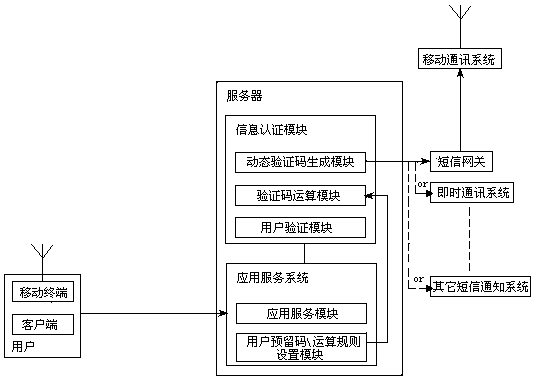
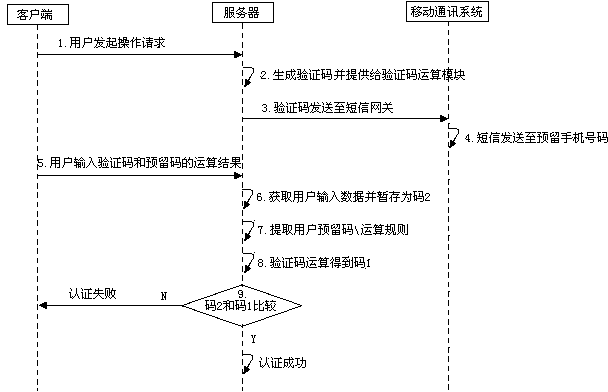
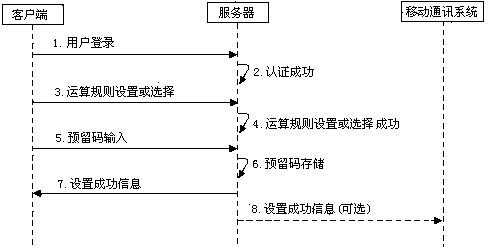
InactiveCN104320767ADoes not compromise securityEasy to rememberMessaging/mailboxes/announcementsSecurity arrangementUser verificationComputer hardware
The invention relates to the field of information security, in particular to a short message verification system and method. The short message verification system comprises a server and a client side, the server at least comprises a message verification module and an application service system, and the message verification module comprises a dynamic verification code generating module and a user verification module. The short message verification system is characterized in that the message verification module further comprises a verification code operation module, and the application service system further comprises a user reserved code and operation rule setting module. The short message verification system has the advantage that even if short message verification codes are illegally obtained, safety of users is not affected. When manual computation is adopted by a client side user, memory is easy, operation speed is high, and breaking difficulty is high; operation rules can be set by the user at a server end; when function computation is adopted, the purpose can be achieved through client side software programs; a universal client side computation hardware device can be manufactured; encryption computation service can be provided by a third part service mechanism.
Owner:吴东辉
Method and device for determining optimal path
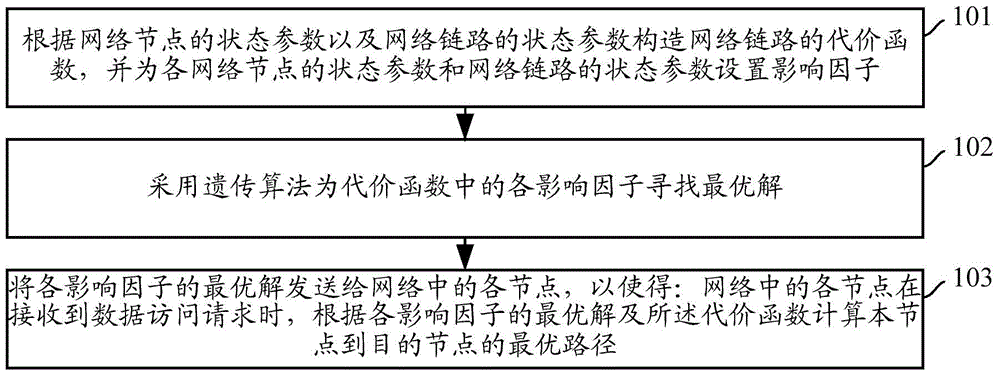
ActiveCN104994021AImprove the efficiency of determining the true optimal pathData switching networksState parameterNetwork link
The application provides a method and device for determining an optimal path. The method comprises the following steps: constructing the cost function of a network link according to the state parameters of network nodes and the state parameter of the network link, and setting influence factors for the state parameter of each network node and the state parameter of the network link; finding an optimal solution for each influence factor in the cost function with a genetic algorithm; and transmitting the optimal solution of each influence factor to each node in the network in order that an optimal path from each node in a network to a destination node is calculated according to the optimal solution of each influence factor and the cost function when each node in the network receives a data access request. Through the application, the efficiency in determination of a real optimal path is increased.
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
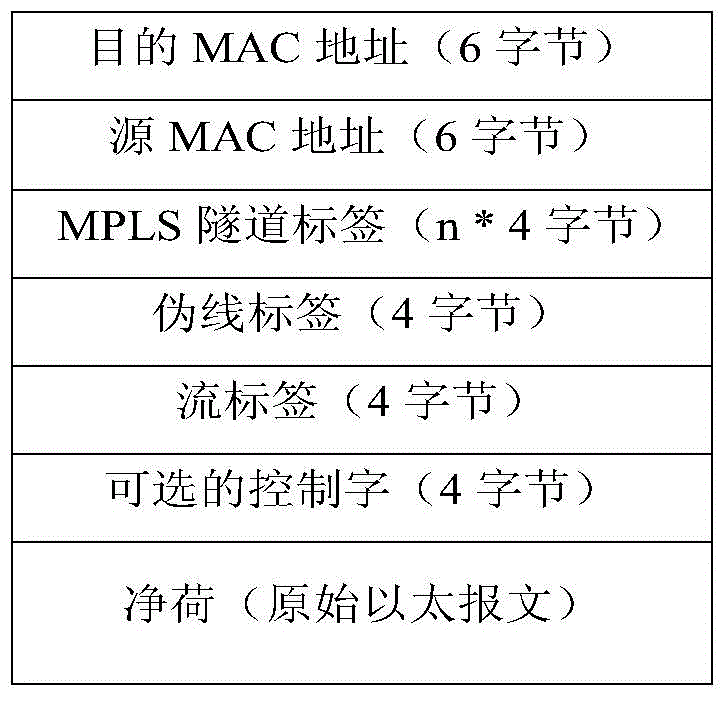
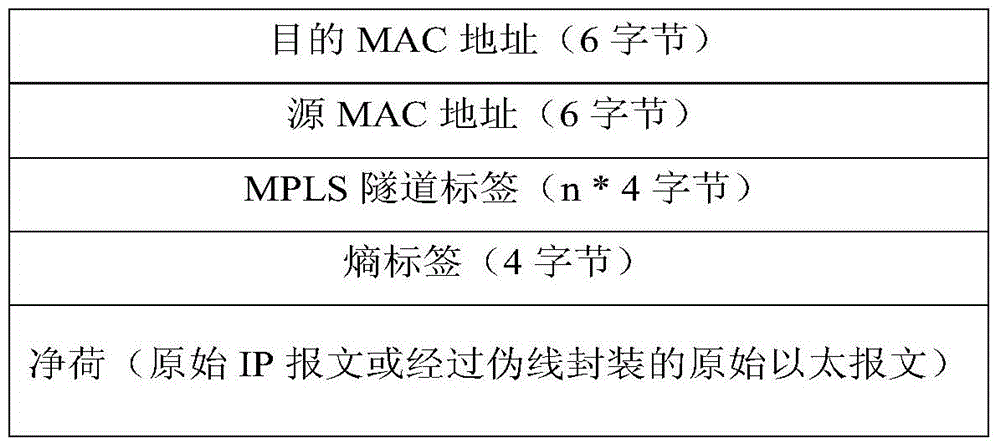
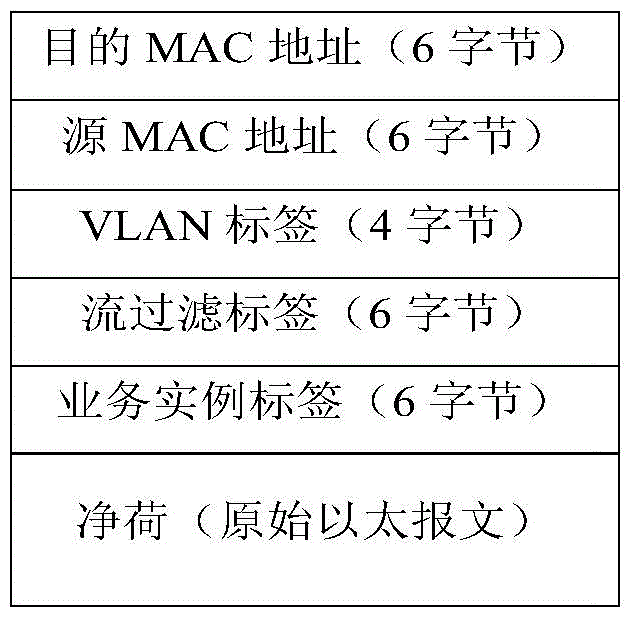
Flow label encapsulating method and system
InactiveCN104639470ASolve the problem that the flow identification encapsulation cannot be realizedData switching networksOpenFlowDistributed computing
Disclosed are an encapsulation method and system for a flow identifier. The encapsulation method for a flow identifier comprises: in the case where flow table matching is successfully conducted on a packet, adding, by an openFlow switch, a flow identifier to the packet; and invoking, by the openFlow switch, a pre-saved function calculation function to assign the flow identifier, so as to complete the encapsulation of the flow identifier. The present invention achieves the effect of enabling an openFlow network node to take a Hash calculation result of some fields of an original packet before encapsulation as the assignment of a new encapsulated flow identifier, which is required by the encapsulation of the flow identifier.
Owner:ZTE CORP
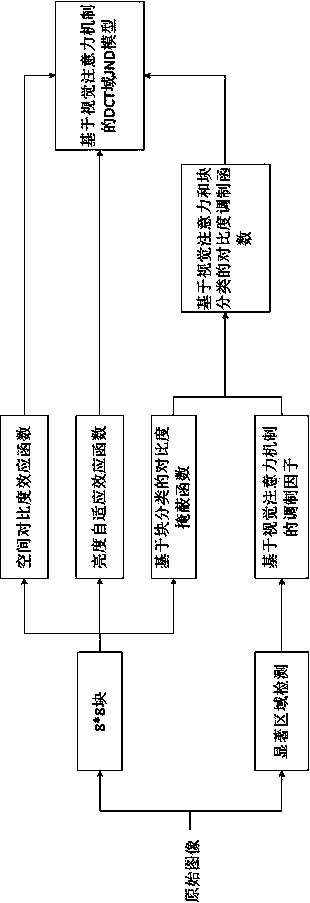
Image JND threshold value computing method in DCT domain and based on visual attention mechanism
InactiveCN103475881AFine and accurate classificationMuch noiseTelevision systemsPattern recognitionVision based
The invention provides an image JND threshold value computing method in a DCT domain and based on a visual attention mechanism. The image JND threshold value computing method comprises two schemes combining significance and block classification, wherein one scheme includes that a visual attention masking factor of a single point is combined with block classification masking factors according to a point-to-point mode; the other scheme includes that the average significance of all blocks represents significance of the whole block classification, and then a visual attention masking factor of each block is combined with block classification masking factors according to a block-to-block mode. A value obtained through calculation by a comprehensive contrast masking function is utilized to modulate a traditional JND threshold value, and finally a more accurate JND threshold value is obtained. The two schemes of the method can both effectively improve accuracy of the JND threshold value, and therefore the JND threshold value is matched with a human eye vision system. A model achieved by the image JND threshold value computing method can contain more noise, and in the aspect of the PSNR, the model can be improved by 0.54DB on average.
Owner:TONGJI UNIV
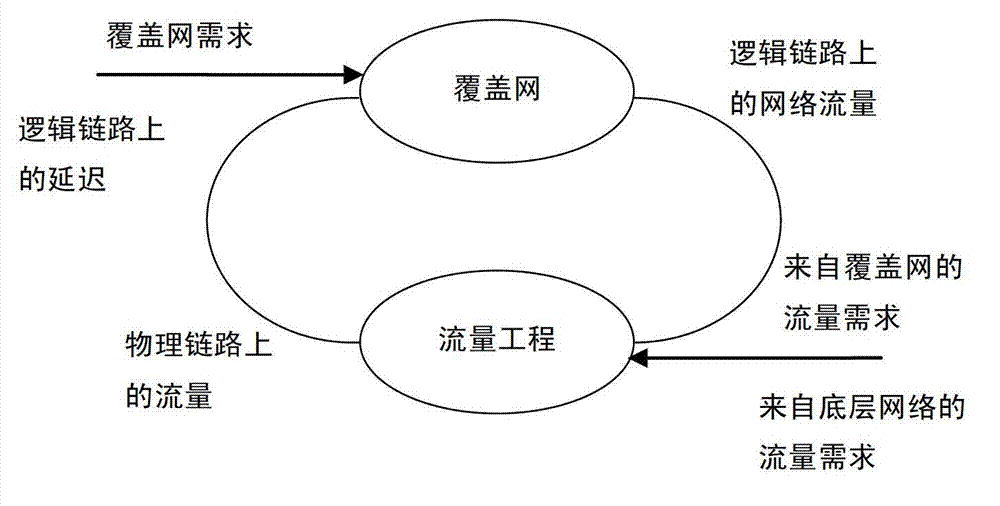
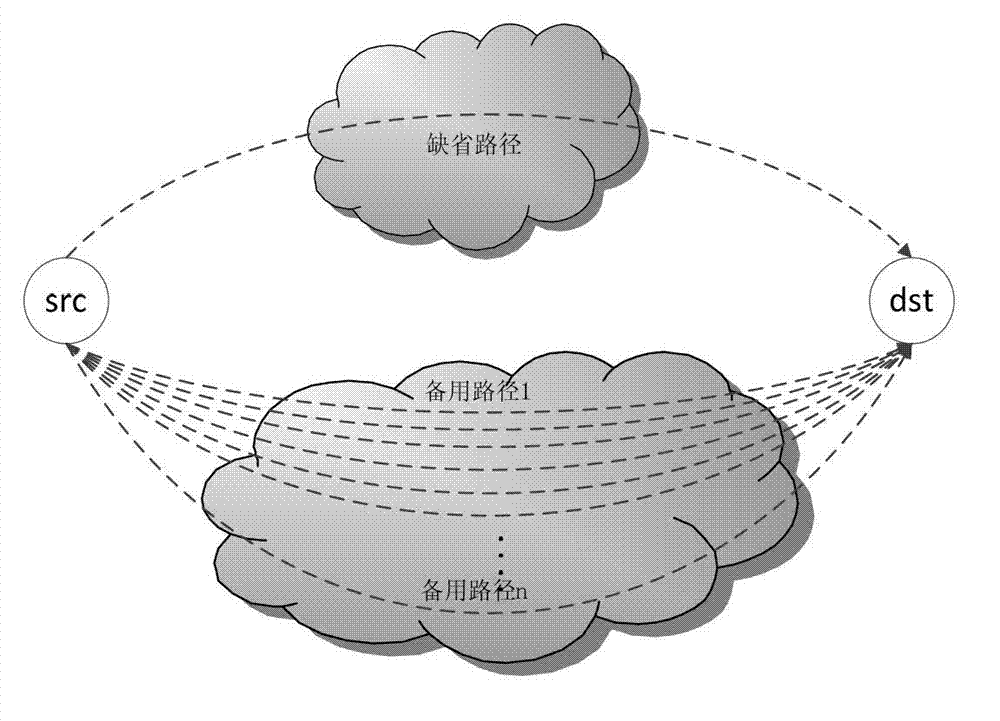
Delay scheduling-based network traffic conflict prevention method and delay scheduling-based network traffic conflict prevention system
ActiveCN103051546ANo backflowDoes not cause routing jitterData switching networksTraffic capacityCarrying capacity
The invention provides a delay scheduling-based network traffic conflict prevention method and a delay scheduling-based network traffic conflict prevention system. The method includes: step 1: path performance detection is carried out on a default path within a probing cycle, and if the default path of an overlay network can meet the requirement of network transmission performance, step 2 is executed, or else step 3 is executed; step 2: traffic is transmitted via the default path; step 3: a transfer traffic calculation function is utilized to calculate transfer traffic to be transferred on the default path, and the transfer traffic is part of the traffic transmitted on the default path; step 4: path performance detection is carried out on alternate paths, the transfer traffic is allocated onto the alternate paths for transmission according to the carrying capacity of the alternate paths, and the steps are repeated in the next probing cycle. The invention solves the problem of vertical conflict in the prior art, prevents the phenomenon of frequent jitter caused by the optimization conflict problem of the conventional overlay network system, and guarantees the normal service performance of the overlay network.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method and system for timing code execution in a korn shell script
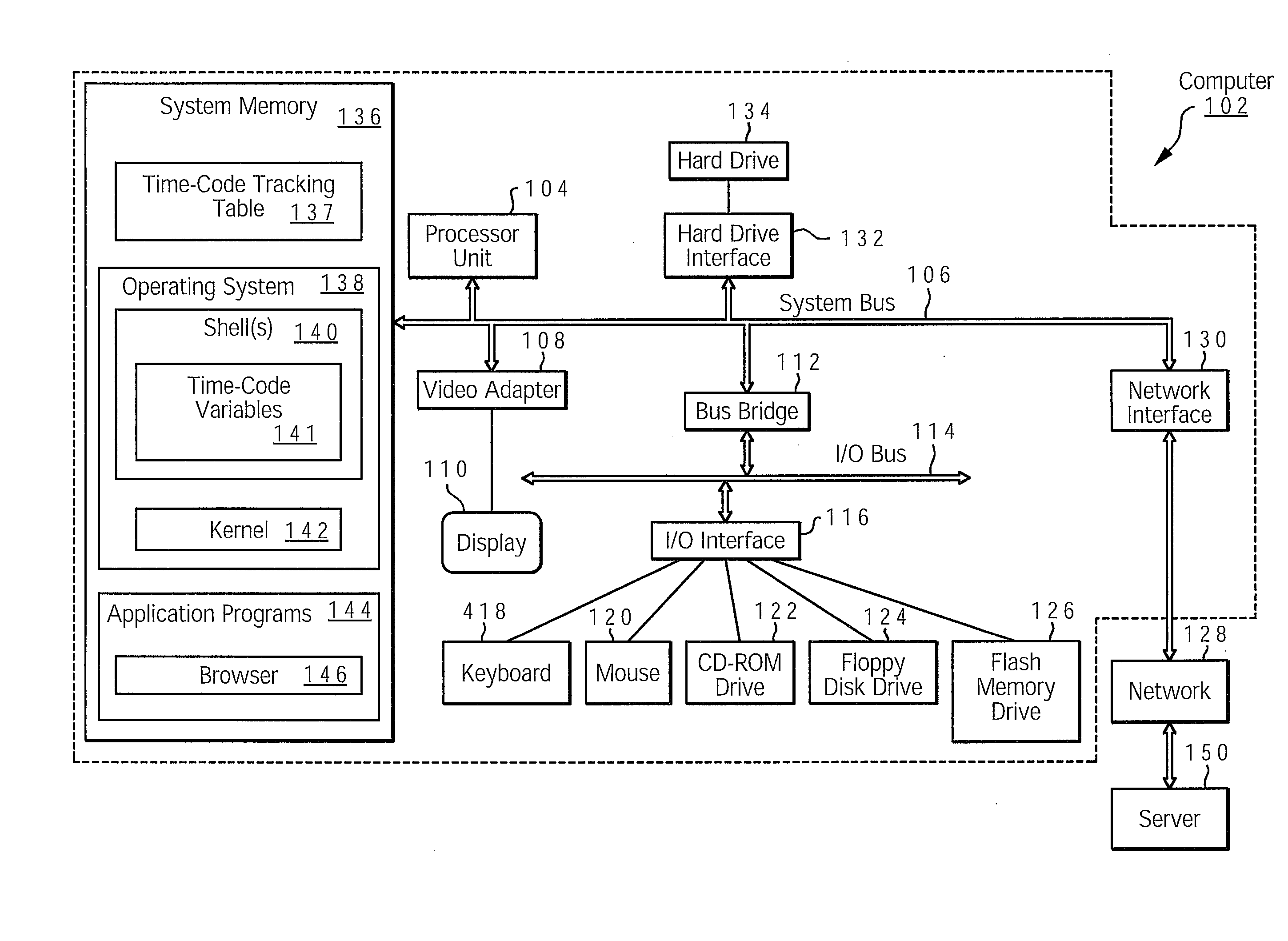
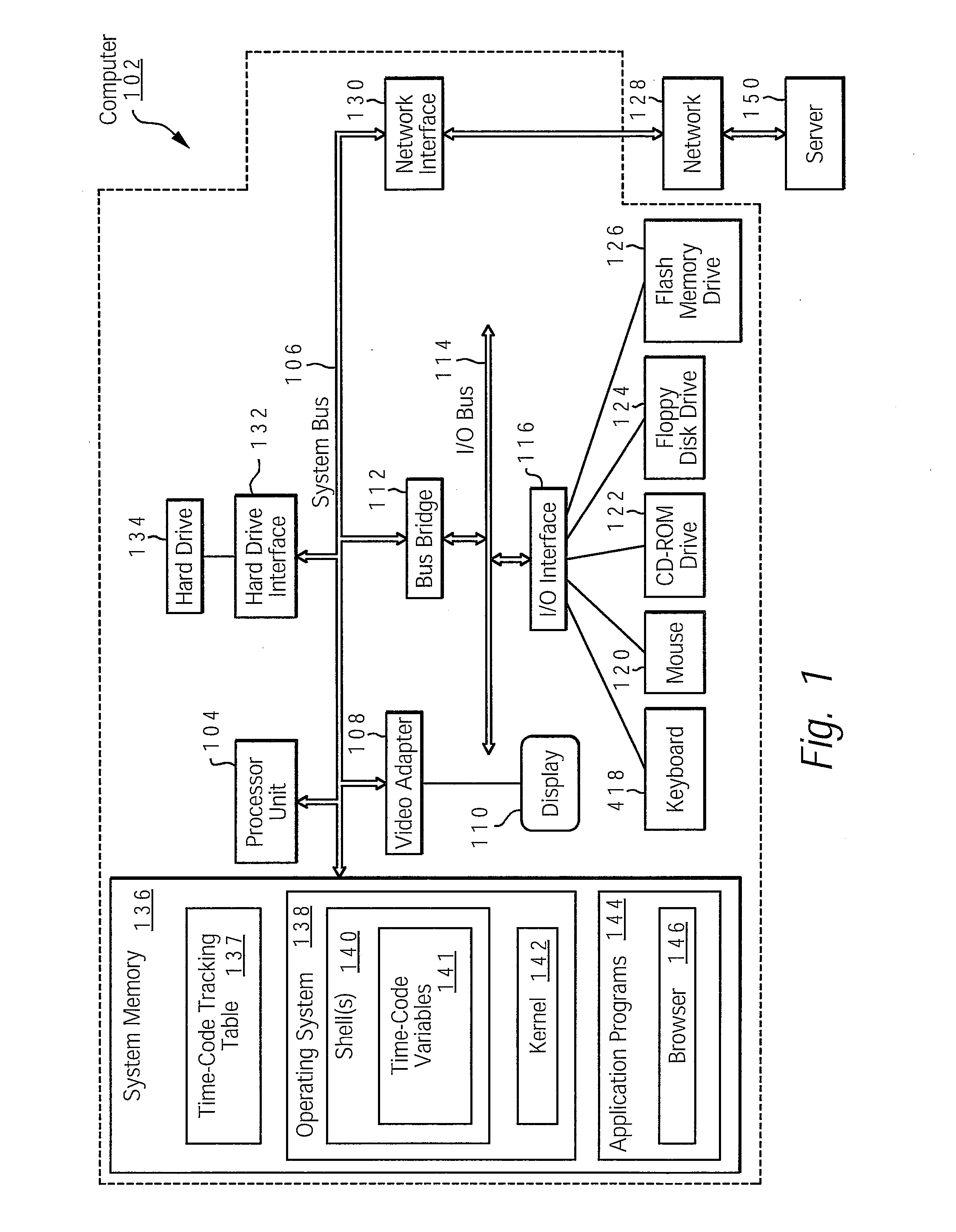
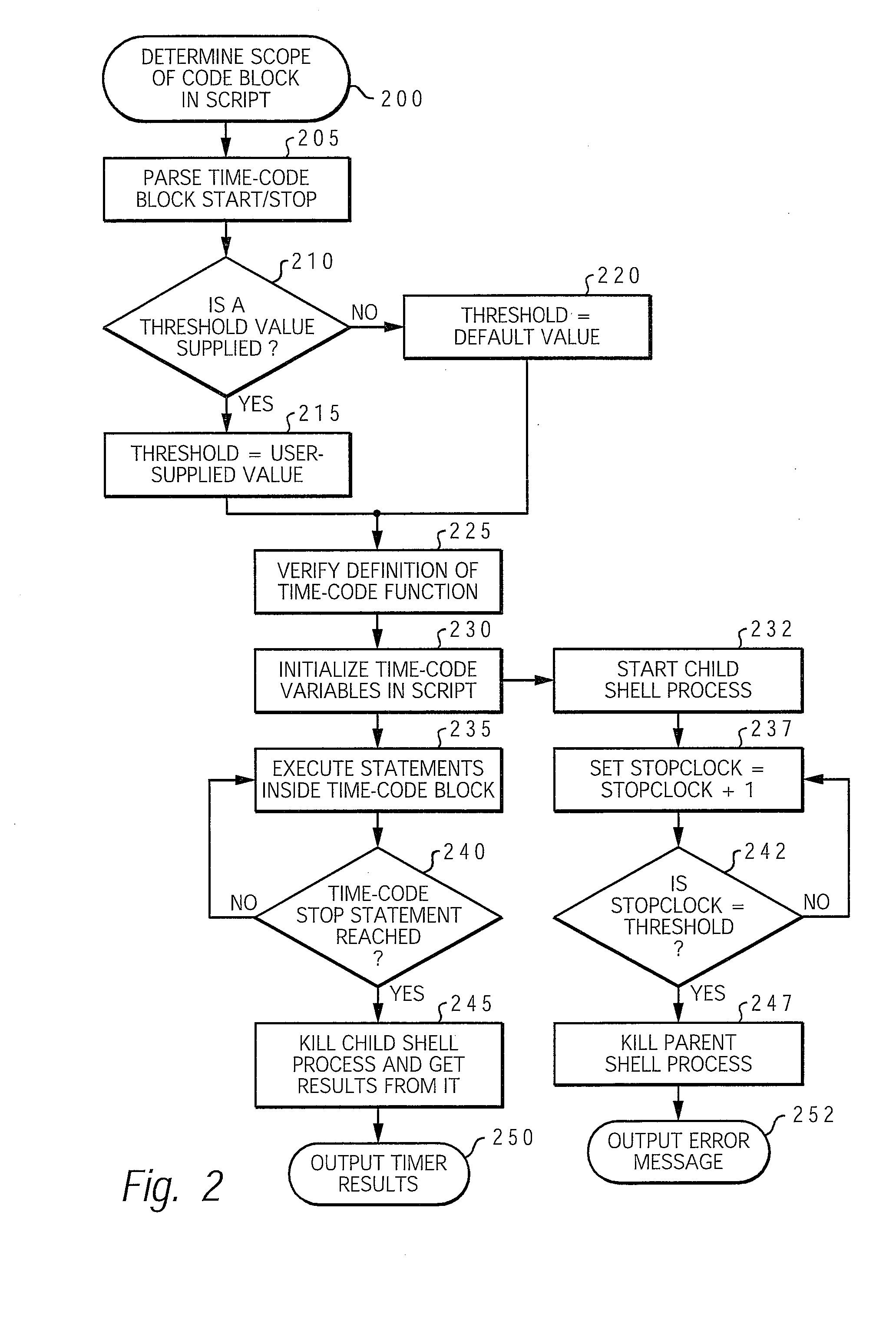
InactiveUS20080127067A1Easy to debugSpecific program execution arrangementsMemory systemsEngineeringUser defined
A method, system, and computer program product for timing the execution of code to facilitate the debugging of a Korn shell script. A user specifies the starting point and stopping point of a block of code by placing a time-code function at the beginning and end of the block of code. Furthermore, the user specifies a threshold value within the time-code function that corresponds to a maximum amount of time allotted for execution. The user defines a label variable to identify the output. When the block of code is executed, the time-code function calculates the time of execution and outputs the results. If the code contains an error that causes the execution time to exceed the threshold value, the time-code function halts the execution of the block of code and an error message is displayed. The error message then assists the user in debugging the block of code.
Owner:IBM CORP
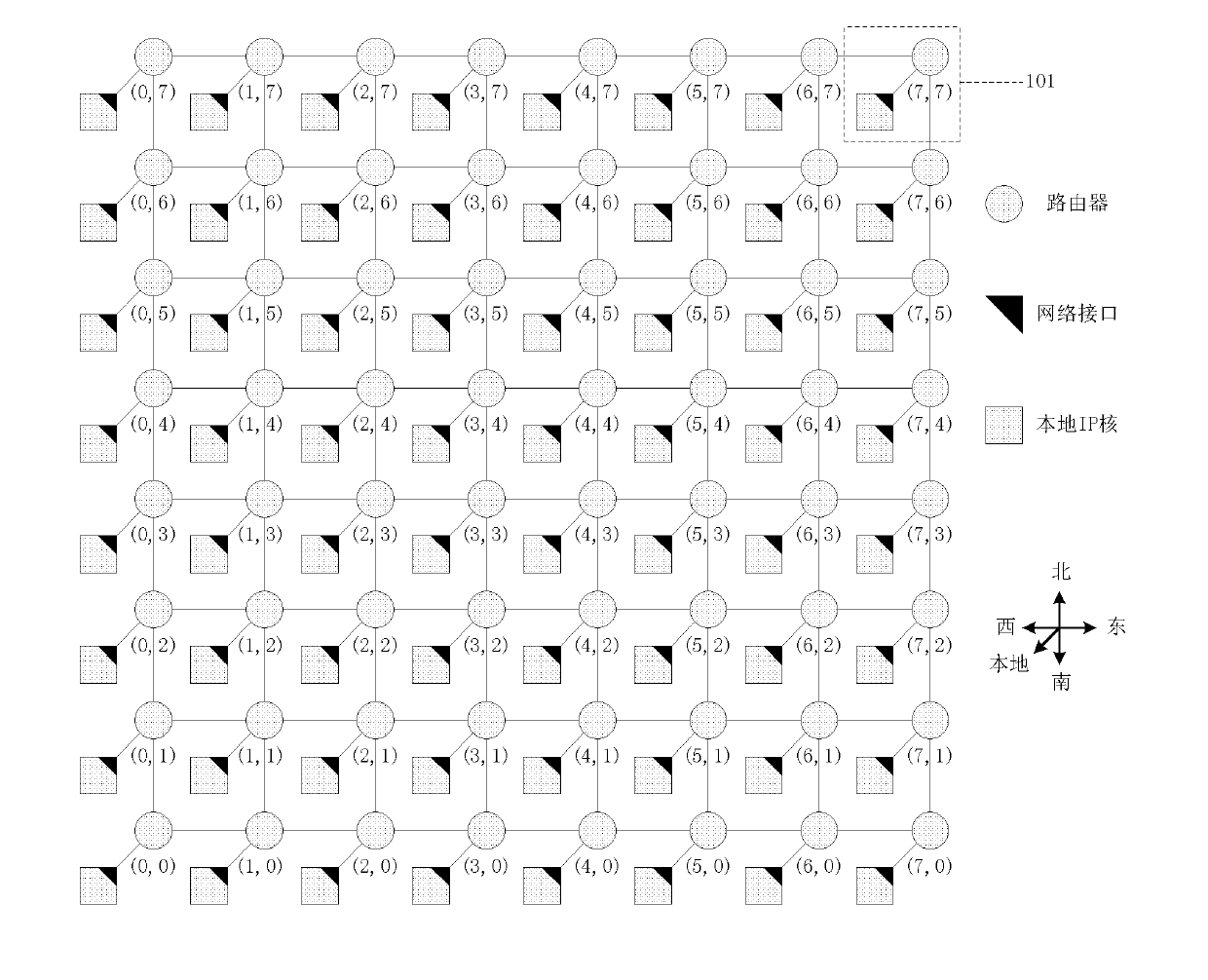
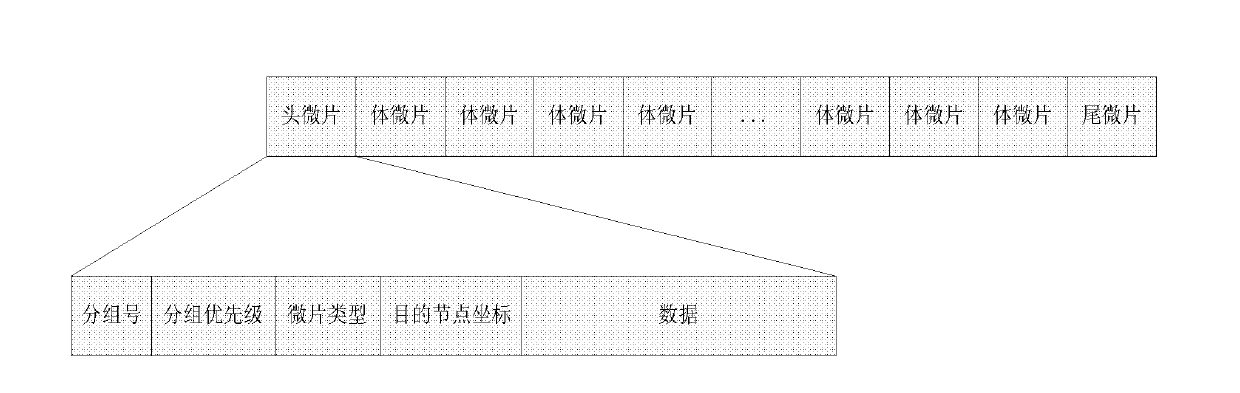
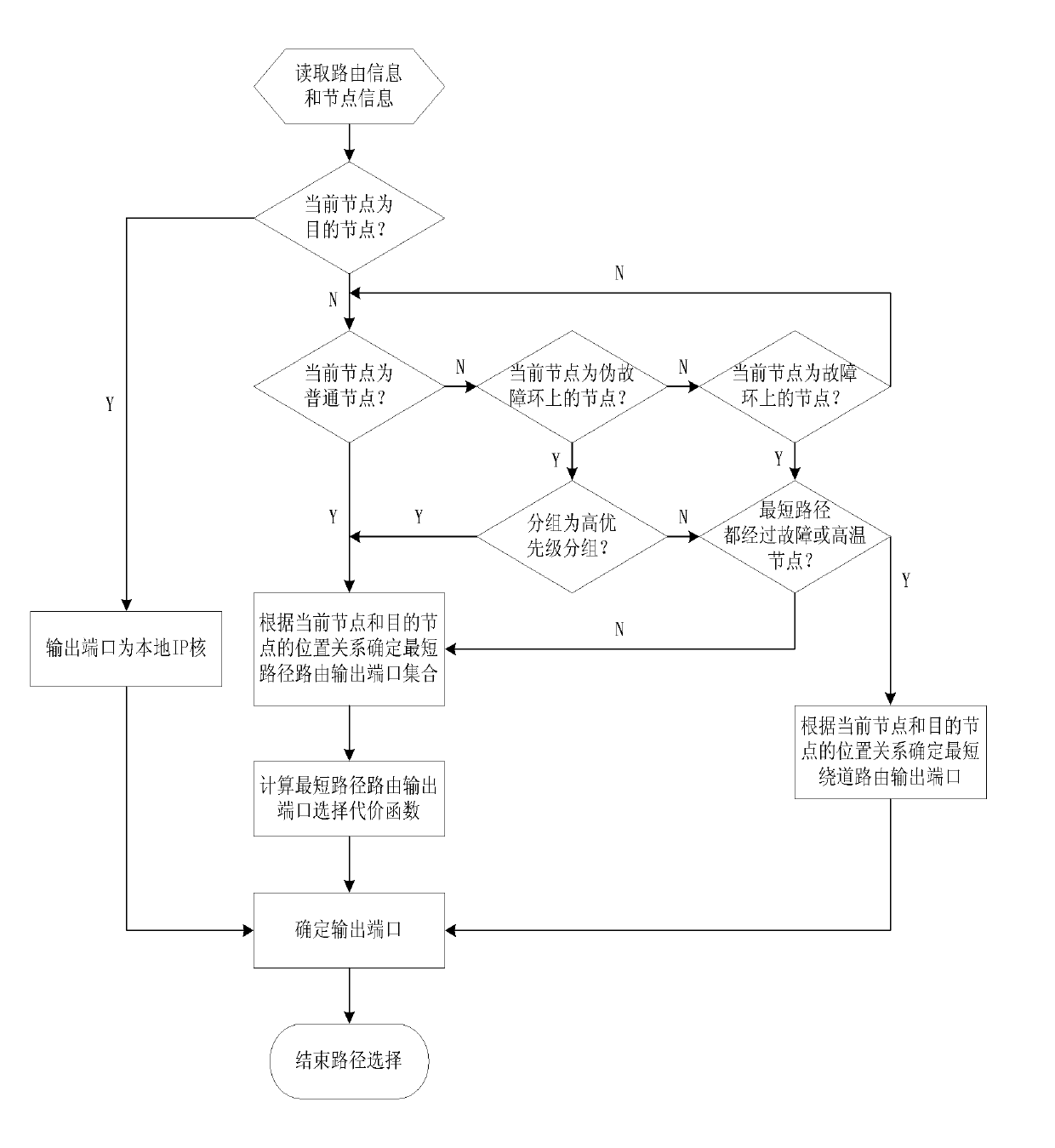
Network path selection method for heat balance sheet with fault tolerance function
The invention discloses a network path selection method for heat balance sheet with fault tolerance function, which mainly solves the problem that the prior art does not have fault tolerance function and can not guarantee the packet delay property relying on the routing table. The execution steps are as follows: (1) reading the current ode address information and judging the current node type; (2) reading the packet target node address information and judging the packet priority; (3) determining the routing output port set of the shortest path according to the node address information, the node type and the packet priority; (4) defining the selection cost function of output port: i=1, 2, reading the calculation parameter of cost function and calculating the selection cost of output port; and (5) determining the output port. The invention has the advantages of improving the network-on-chip heat balance, reliability and service life and effectively satisfying the requirement of network-on-chip property to the practical application.
Owner:陕西光电子先导院科技有限公司
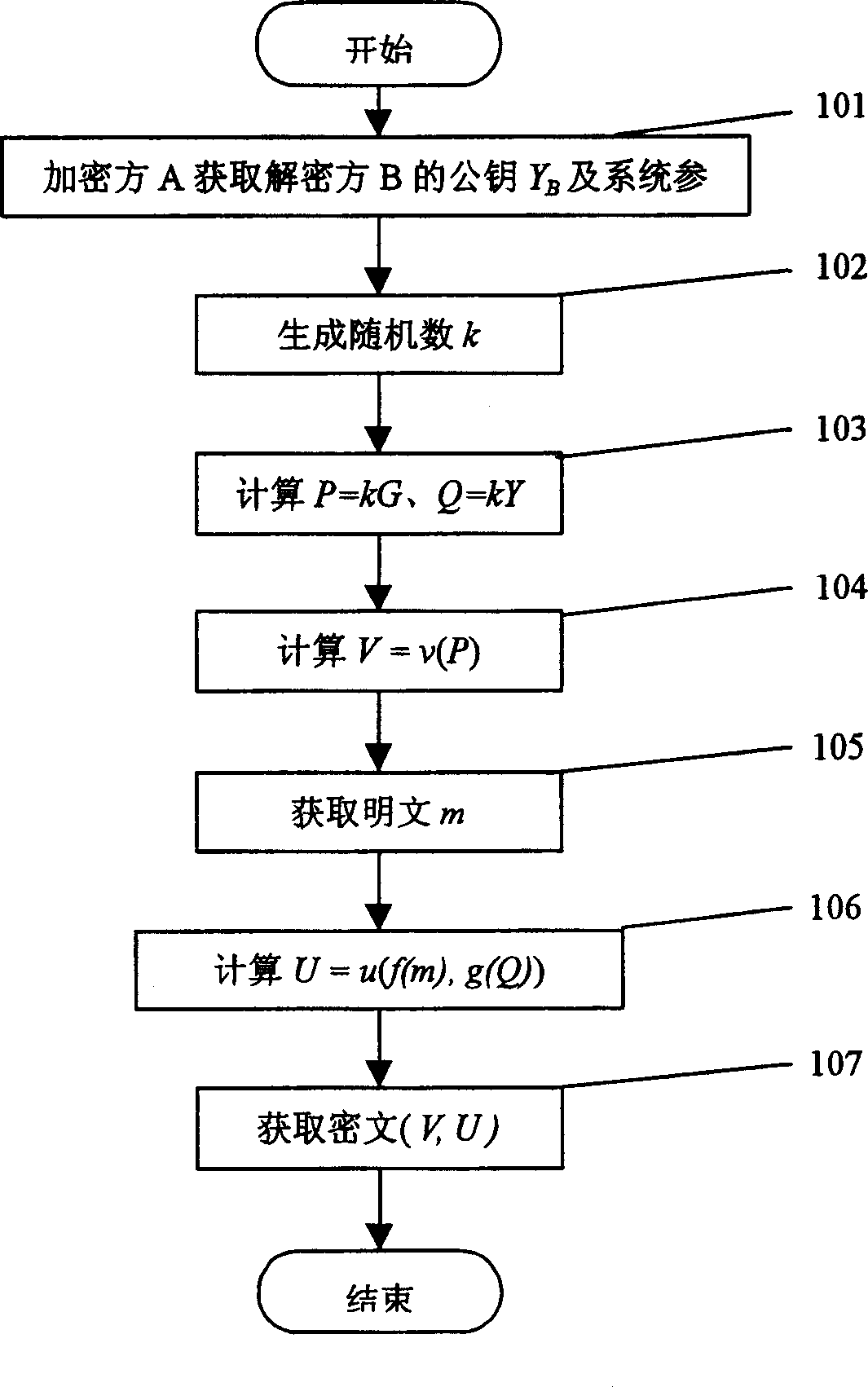
Elliptic curve encryption and decryption method and apparatus
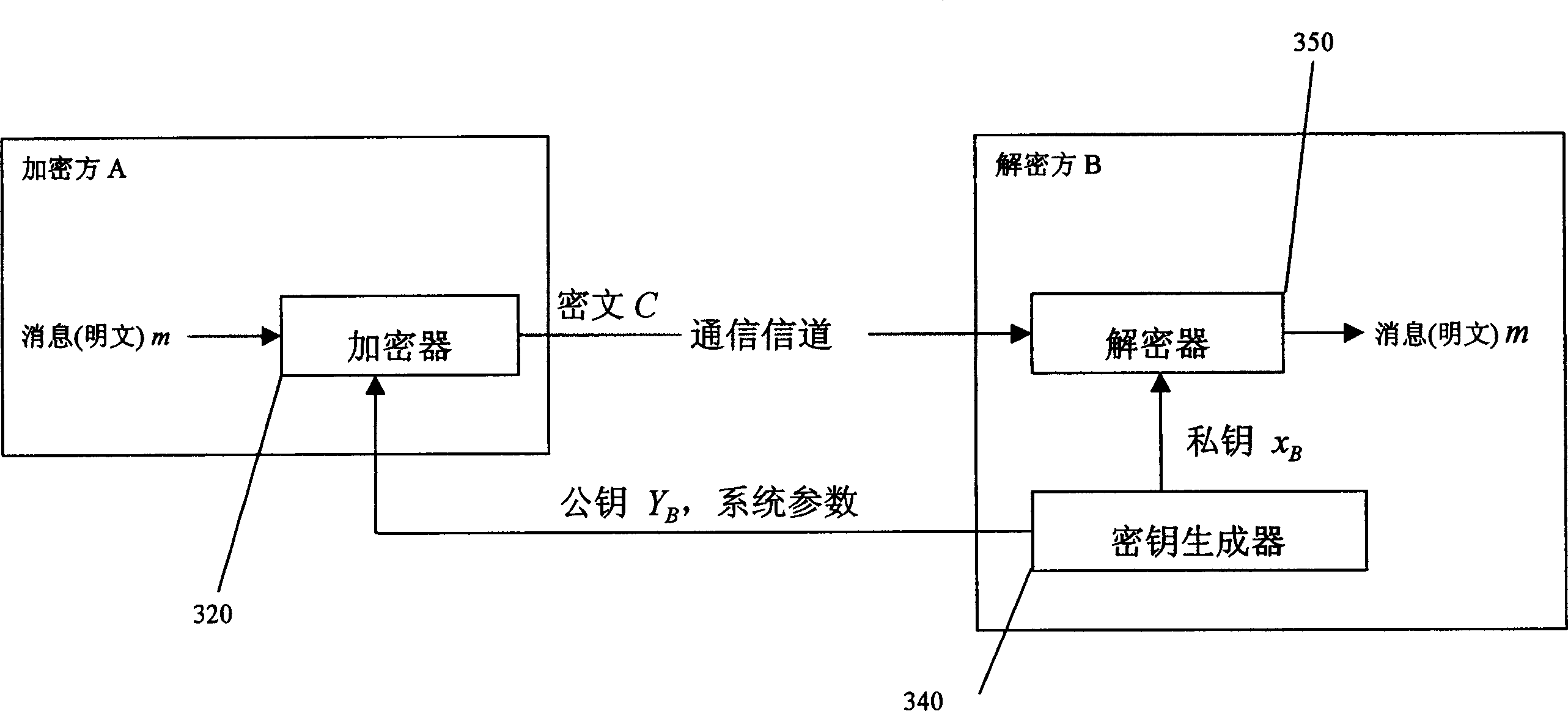
InactiveCN1505306ATroubleshoot embedding issuesIncrease flexibilitySecret communicationSecuring communicationPlaintextCiphertext
Owner:BEIJING HUADA INFOSEC TECH
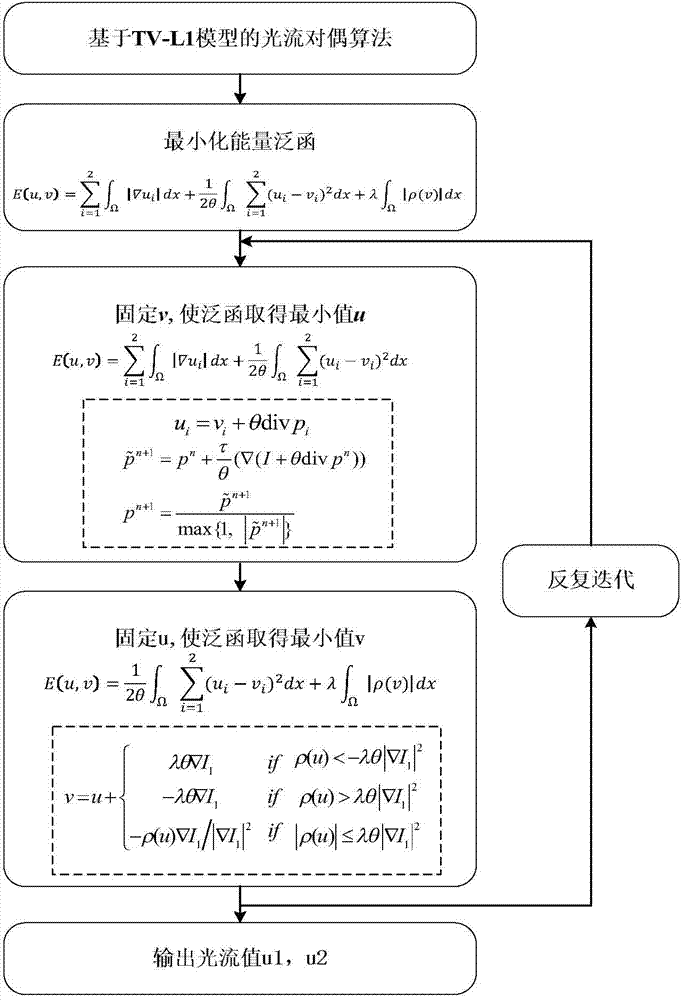
Robust optical flow field estimating method based on TV-L1 variation model
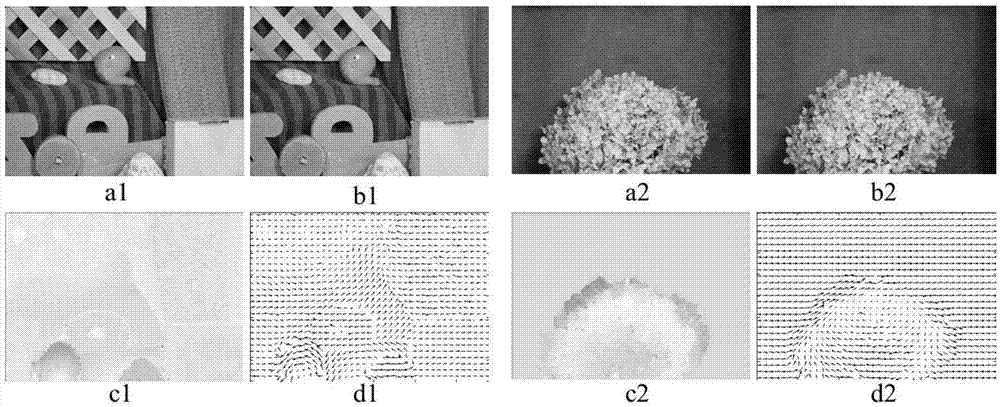
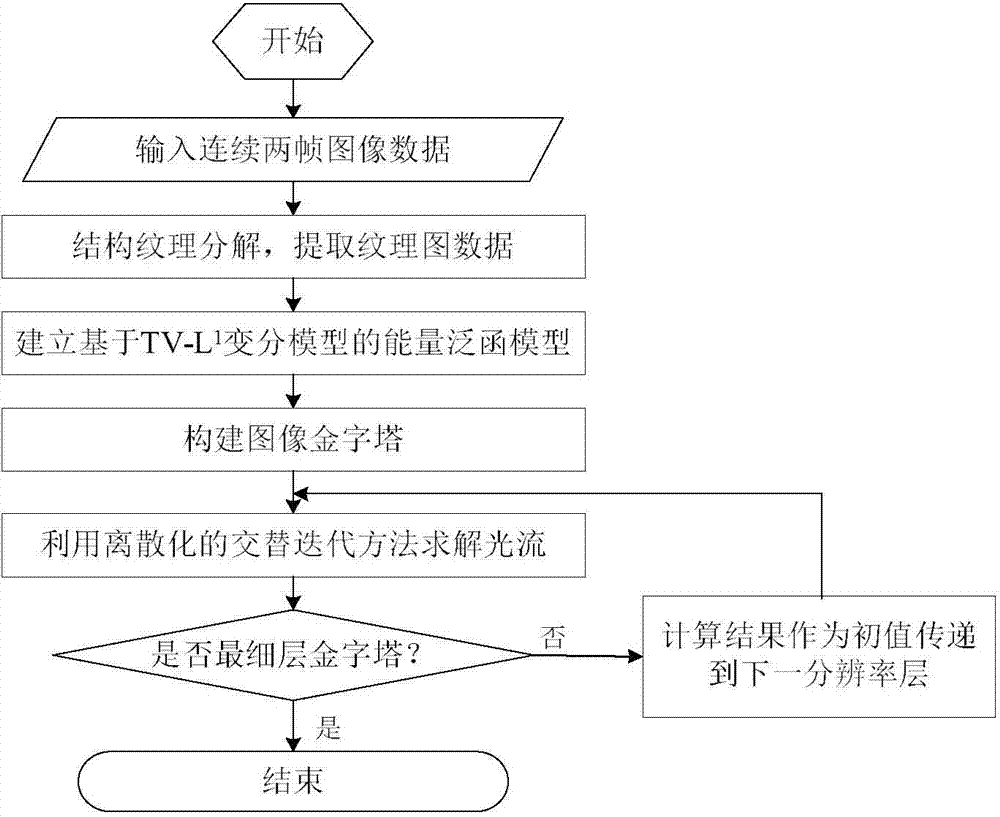
InactiveCN103700117AKeep segment smoothCalculation speedImage analysisImage resolutionGraphics processing unit
The invention discloses a robust optical flow field estimating method based on a TV-L1 variation model. The robust optical flow field estimating method comprises the following steps: firstly, performing structural texture resolution on an input image, and establishing an optical flow calculating model based on the TV-L1; secondly, establishing an image pyramid, calculating optical flow on the lowest image resolution layer by a discretized alternating iteration method, further calculating with a calculated value as an initial value of a next higher resolution layer till the highest resolution layer, namely the original image resolution, and accelerating the algorithm by using a GPU (graphic processing unit) so as to improve the instantaneity of the algorithm; finally, calculating the error of the algorithm by using an optical flow error evaluating function. In the robust optical flow field estimating method, the input image is processed by a structural texture resolving method and a texture image is applied to optical flow calculation, so that influence of an image shadow caused by illumination variation on the calculation is avoided; by the robust optical flow field estimating method based on the TV-L1 variation model, segmenting smoothness of the image is kept and the optical flow calculating precision and optical flow calculating speed are improved.
Owner:BEIJING UNIV OF TECH
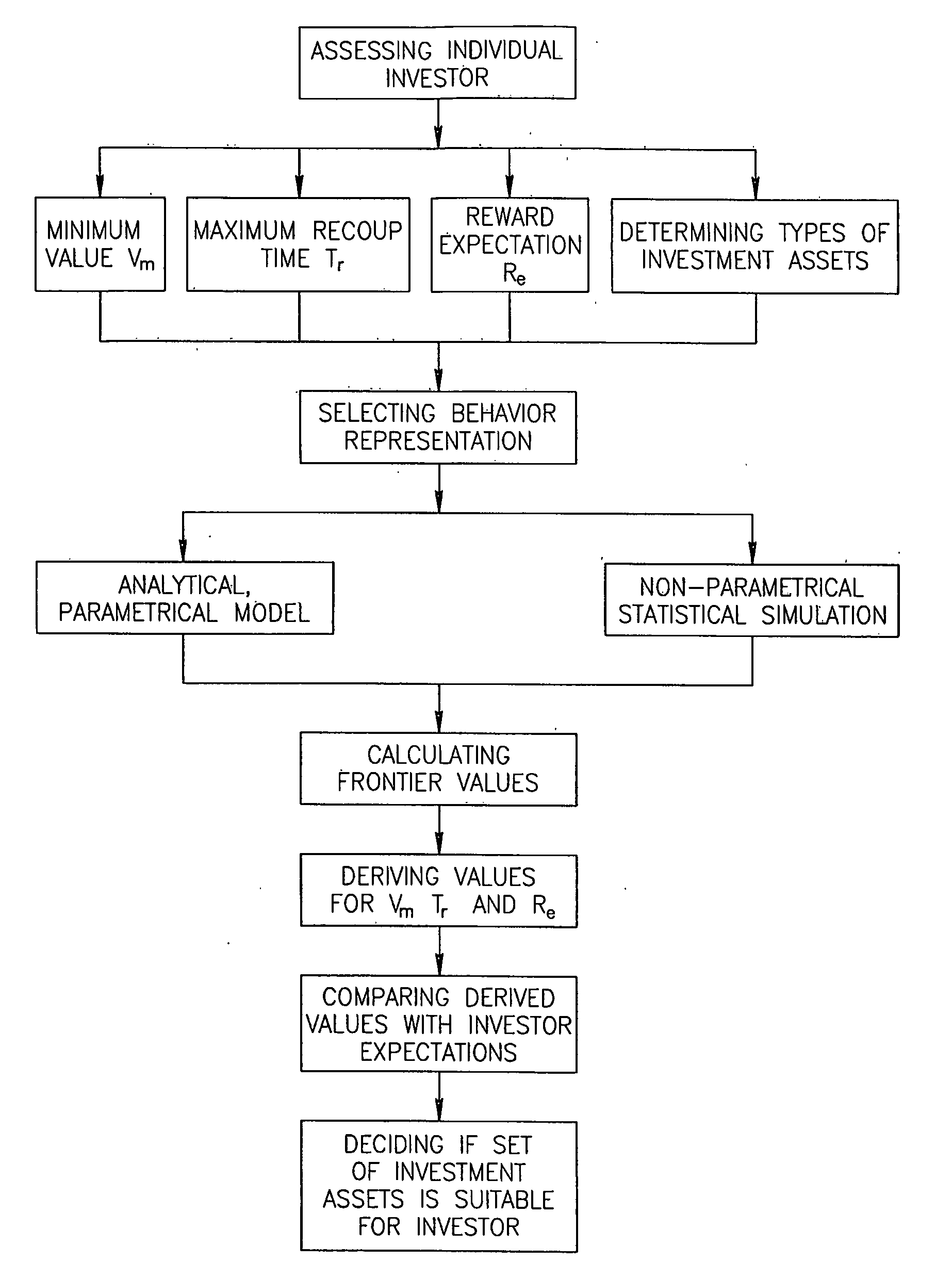
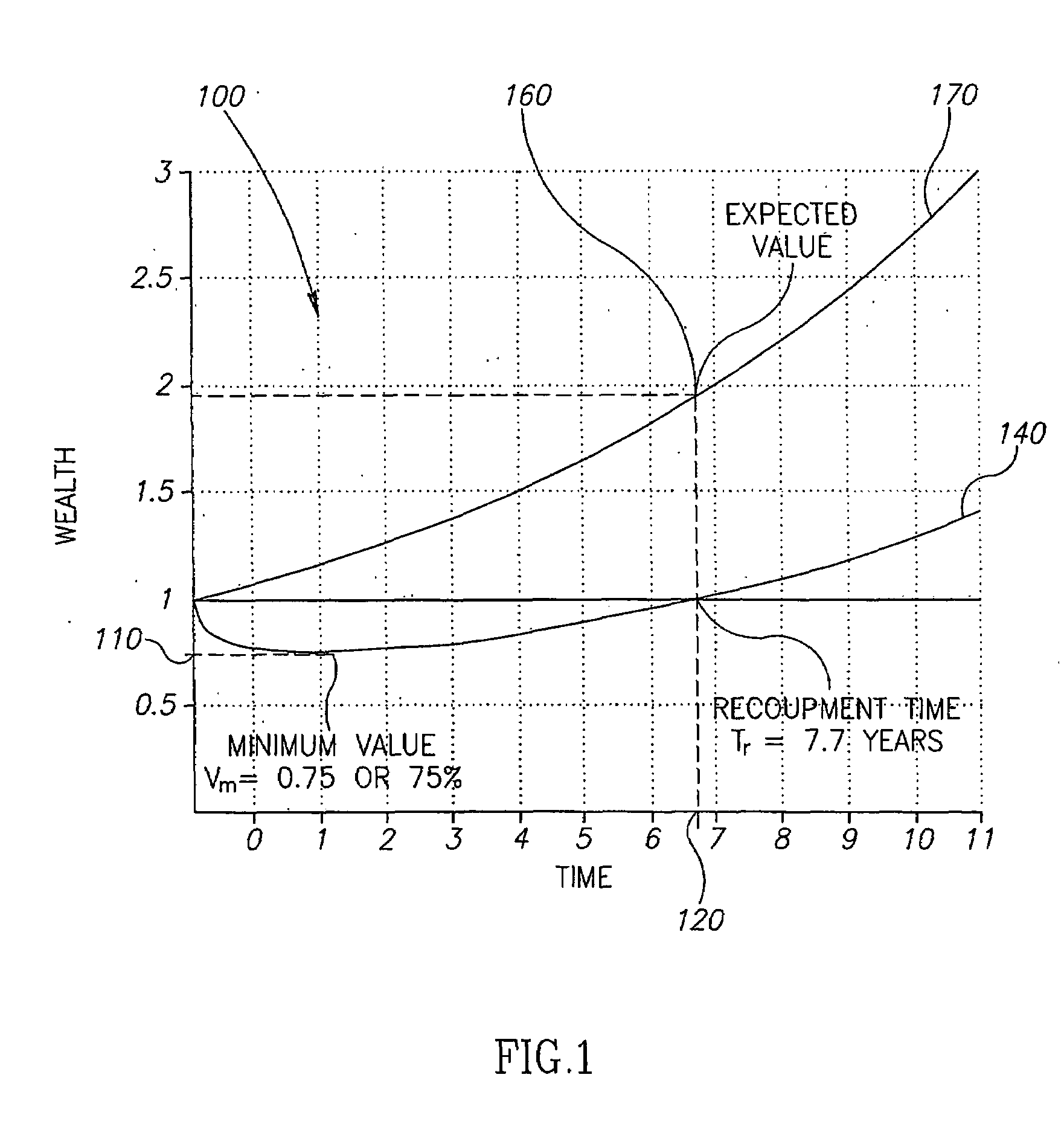
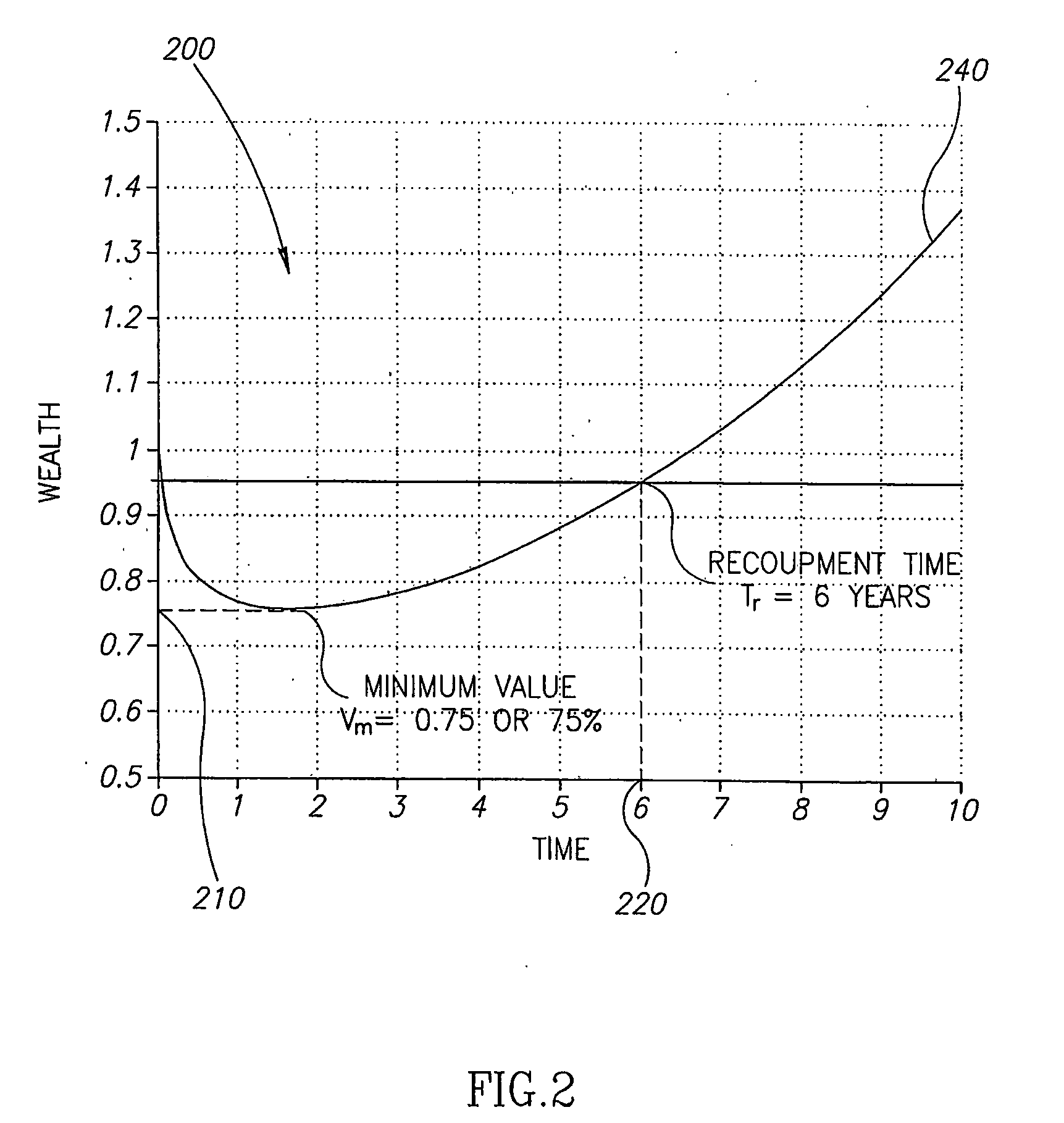
Portfolio Optimization
A method for comparing, creating and optimizing investment portfolios is provided. The utility function for an investment is characterized, and the optimization problem for the utility function is stated based on investor preferences and risk tolerance. According to one embodiment, the measure of relative performance of investment portfolios is calculated based on the investor utility function. According to another embodiment, guidelines for generating an optimized portfolio for the investor from the plurality of asset classes available, are mapped out.
Owner:GORBATOVSKY DMITRY
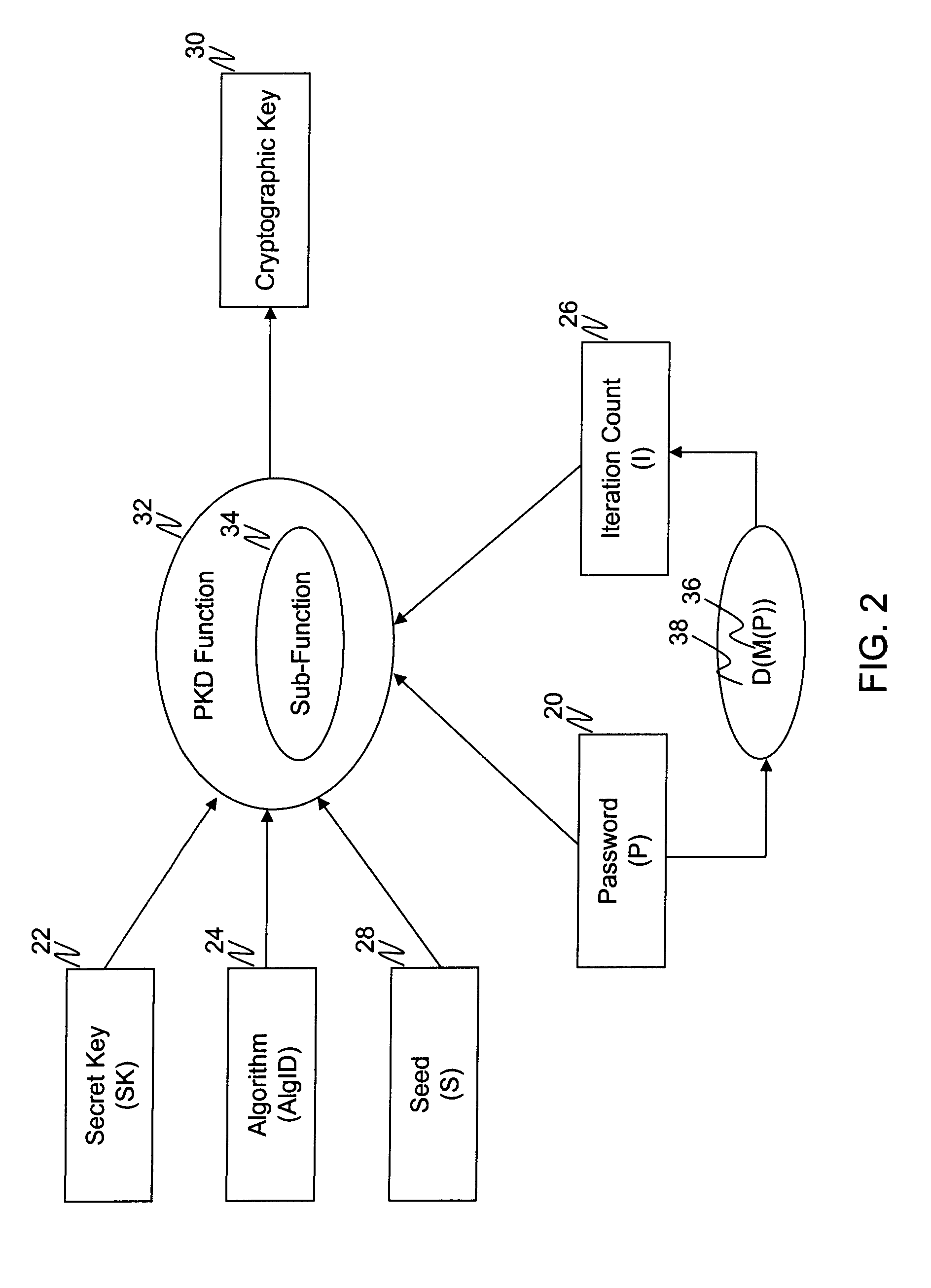
Password key derivation system and method
ActiveUS8238552B2Increase the number of iterationsReduce calculationMemory loss protectionError detection/correctionPasswordKey derivation function
A password-based key derivation function includes a sub-function that gets executed multiple times based on an iteration count. A key derivation module computes the iteration count dynamically with each entered password. The iteration count is computed as a function of the password strength. Specifically, the weaker the password, the higher the iteration count; but the stronger the password, the smaller the interaction count. This helps strengthen weaker passwords without penalizing stronger passwords.
Owner:OPEN TEXT HLDG INC
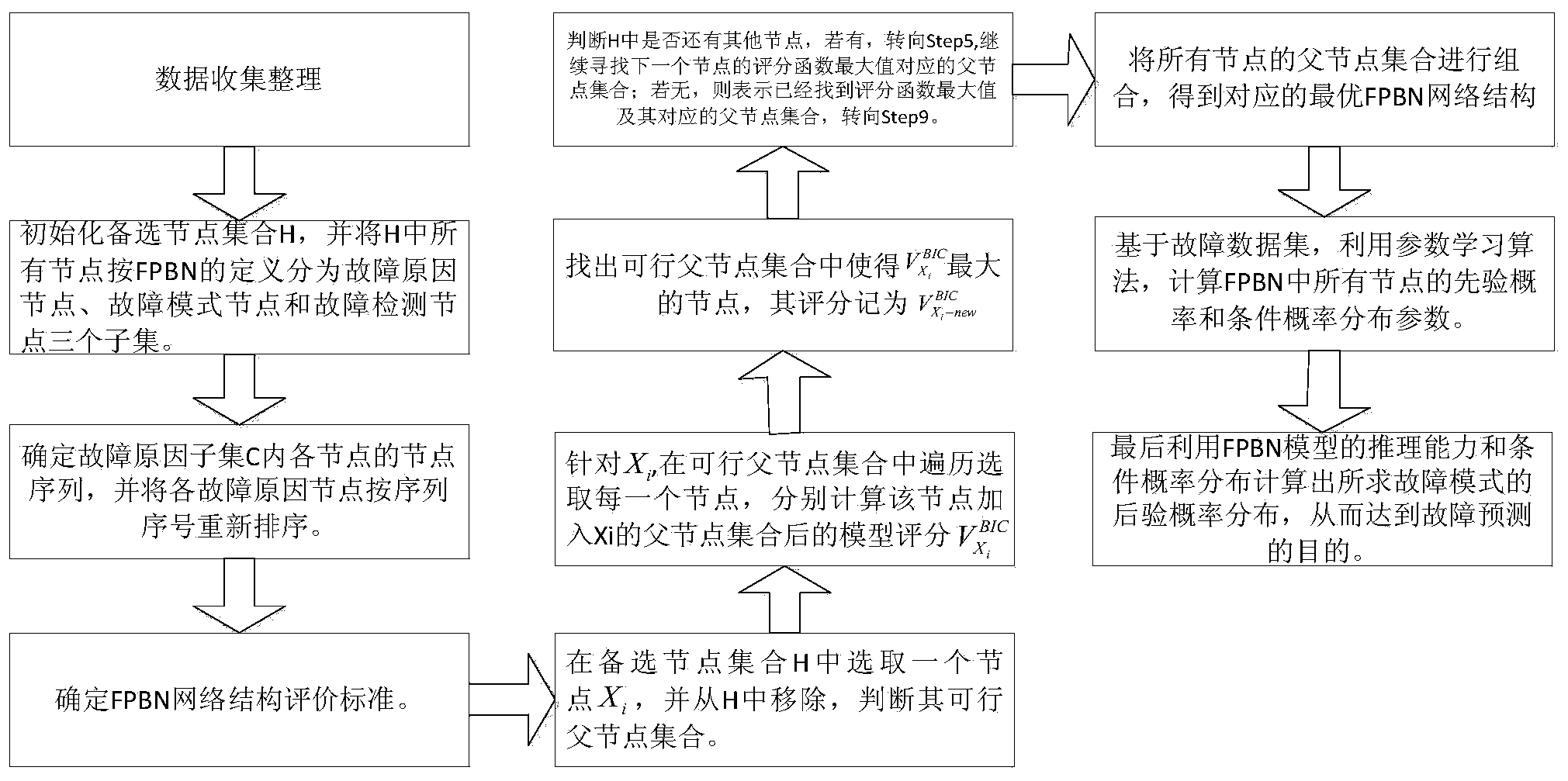
Equipment failure Bayesian network prediction method based on K2 algorithm
ActiveCN104217251AImprove search efficiencyReduce the number of calculationsForecastingData setDeterministic algorithm
The invention discloses an equipment failure Bayesian network prediction method based on a K2 algorithm, and is used for solving the technical problem of low searching efficiency of a conventional equipment failure Bayesian network prediction method. The equipment failure Bayesian network prediction method has the technical scheme that an FPBN (Failure Prediction Bayesian Network) structure learning algorithm based on a K2 searching algorithm is adopted for building an FPBN structure capable of really reflecting each variable incidence relation in a failure data set, so that an FPBN model is built. Finally, the actual operation state of equipment is predicted by uitlizing a parameter learning algorithm on the basis of a built failure prediction model. The method uses the K2 searching algorithm as the basis; the failure knowledge, the expertise and the failure data are effectively fused; and the problem of modeling difficulty in system to FPBN conversion in the equipment prediction process is solved. In addition, the FPBN-K2 algorithm calculation process totally adopts deterministic searching algorithms, and repeated searching for many times is not needed; the searching space is reduced; the number of scoring function calculation times is reduced; and the searching efficiency of the FPBN structure learning algorithm is improved.
Owner:DONGGUAN PANRUI ELECTROMECHANICAL TECH CO LTD
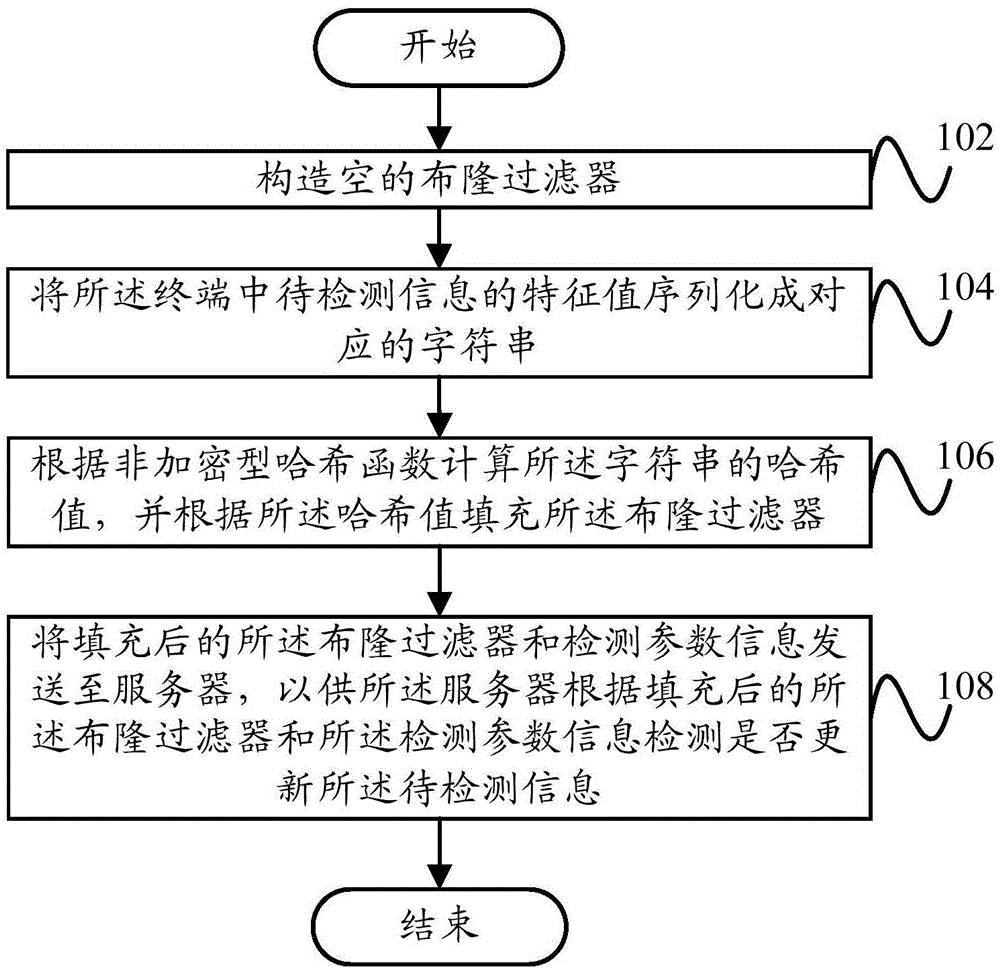
Information updating method, information updating device, terminal and server
The invention provides an information updating method, an information updating device, a terminal and a server. The information updating method comprises the following steps of constructing an empty Bloom filter; serializing a characteristic value sequence of to-be-detected information in the terminal to a corresponding character string; computing a hash value of the character string according to an unencrypted hash function and filling the Bloom filter according to the hash value; and sending the filled Bloom filter and detection parameter information to the server to make the server detect whether the to-be-detected information is updated according to the filled Bloom filter and the detection parameter information. Through the technical scheme of the invention, minimization of mobile network traffic can be realized, the technical scheme can be realized through serializing the characteristic value of the to-be-detected information and computing the hash value, and the algorithm is simple and efficient.
Owner:CHANJET INFORMATION TECH CO LTD
Privacy protection system and method for Internet of Vehicles
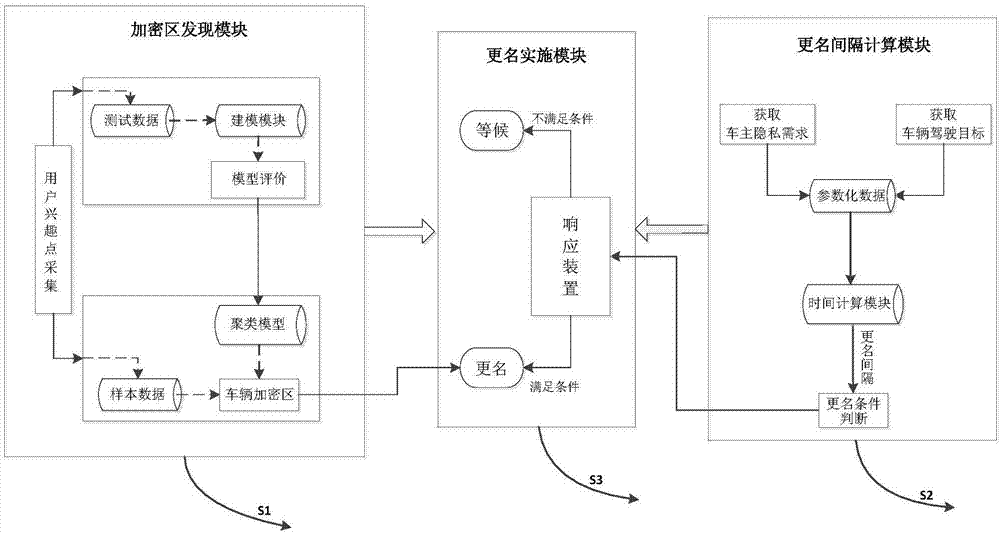
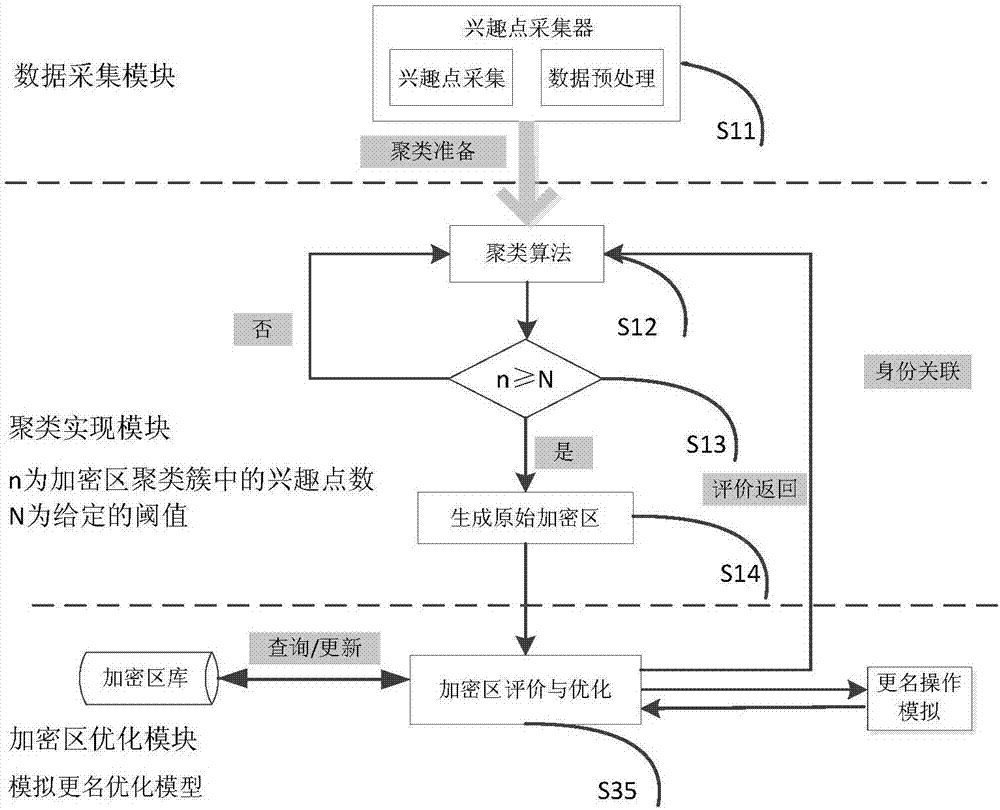
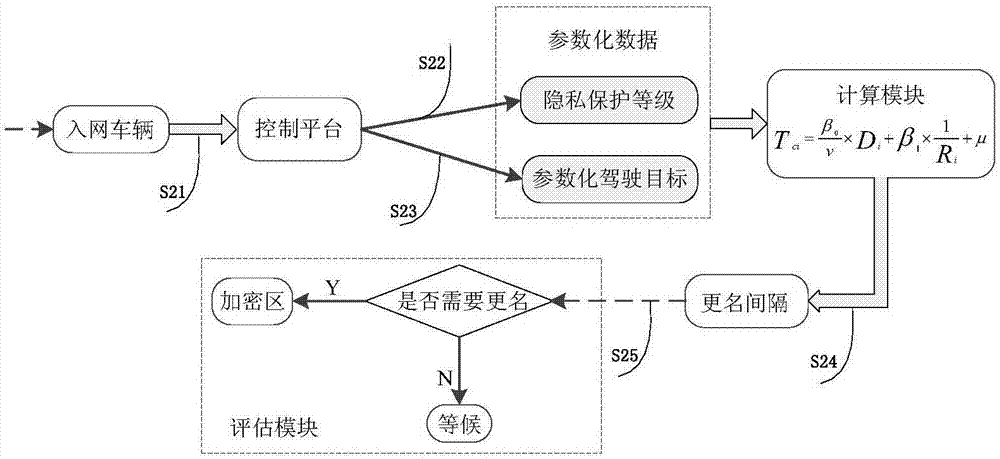
ActiveCN106911670APersonalized privacy protection serviceReduce replacement frequencyRelational databasesTransmissionPersonalizationThe Internet
The present invention provides a privacy protection system and method for the Internet of Vehicles. Implementation of the method requires the following modules: an encryption region discovery module, a renaming interval calculation module, and a pseudonym changing implementation module. The method comprises: firstly, defining user interest points on a road network, discovering a place where interest points are dense by performing clustering analysis on the interest points on the road network by means of a machine learning cluster according to a current road network condition in conjunction with data mining knowledge, and using the region as an encryption region of vehicle renaming; collecting and parameterizing location privacy protection needs of an owner of a vehicle and a driving destination of the vehicle, calculating a renaming interval that meets user needs by means of a statistical function, and using the interval as a criterion for determining whether to assign a pseudonym to the vehicle; and finally, assigning the pseudonym to the vehicle meeting the renaming criterion in the encryption region to achieve location privacy protection of the vehicle. The method of the present invention provides personalized privacy protection for vehicle owners, and reduces the probability of success of an attacker in stealing privacy of the vehicle owners.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
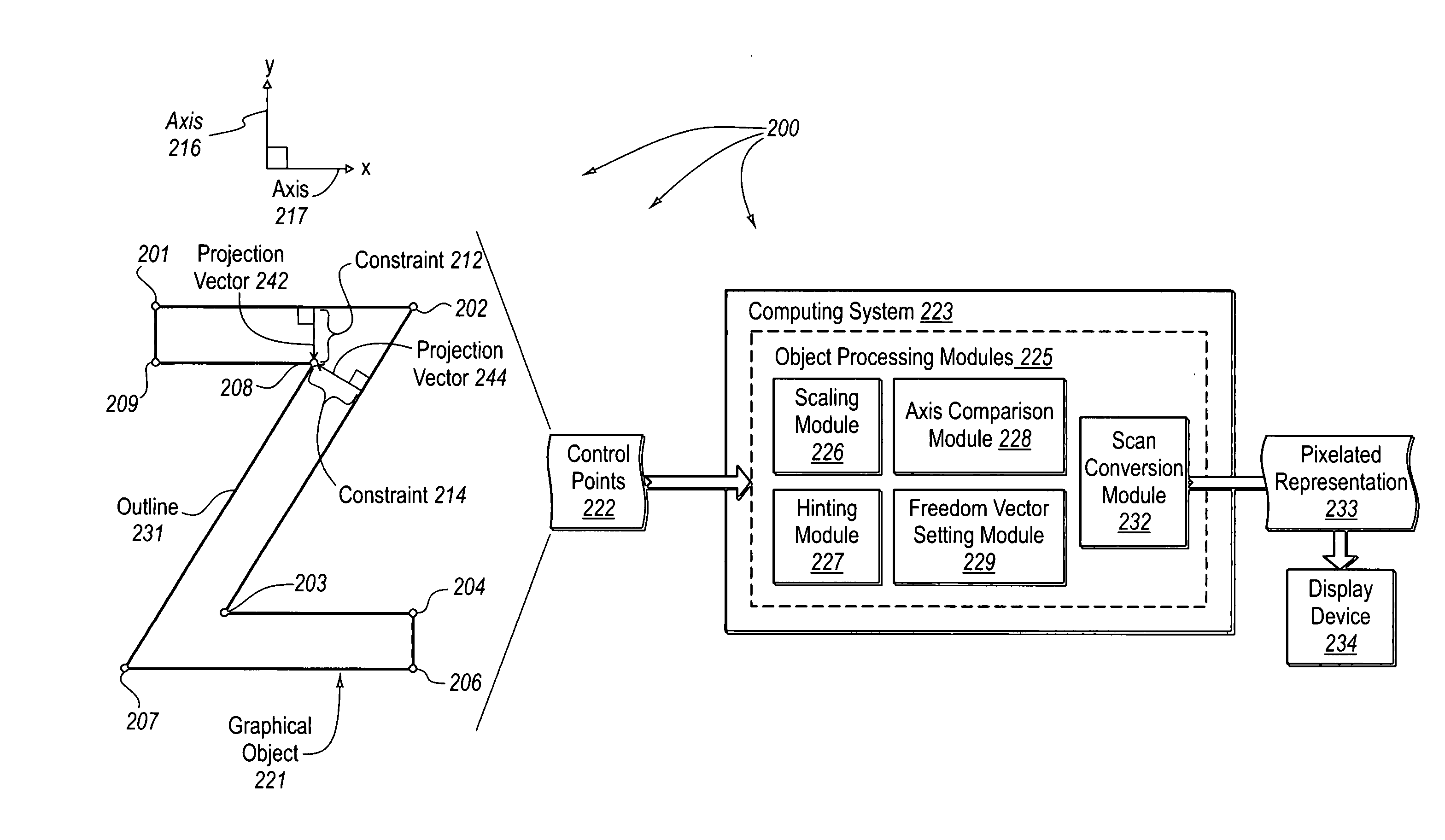
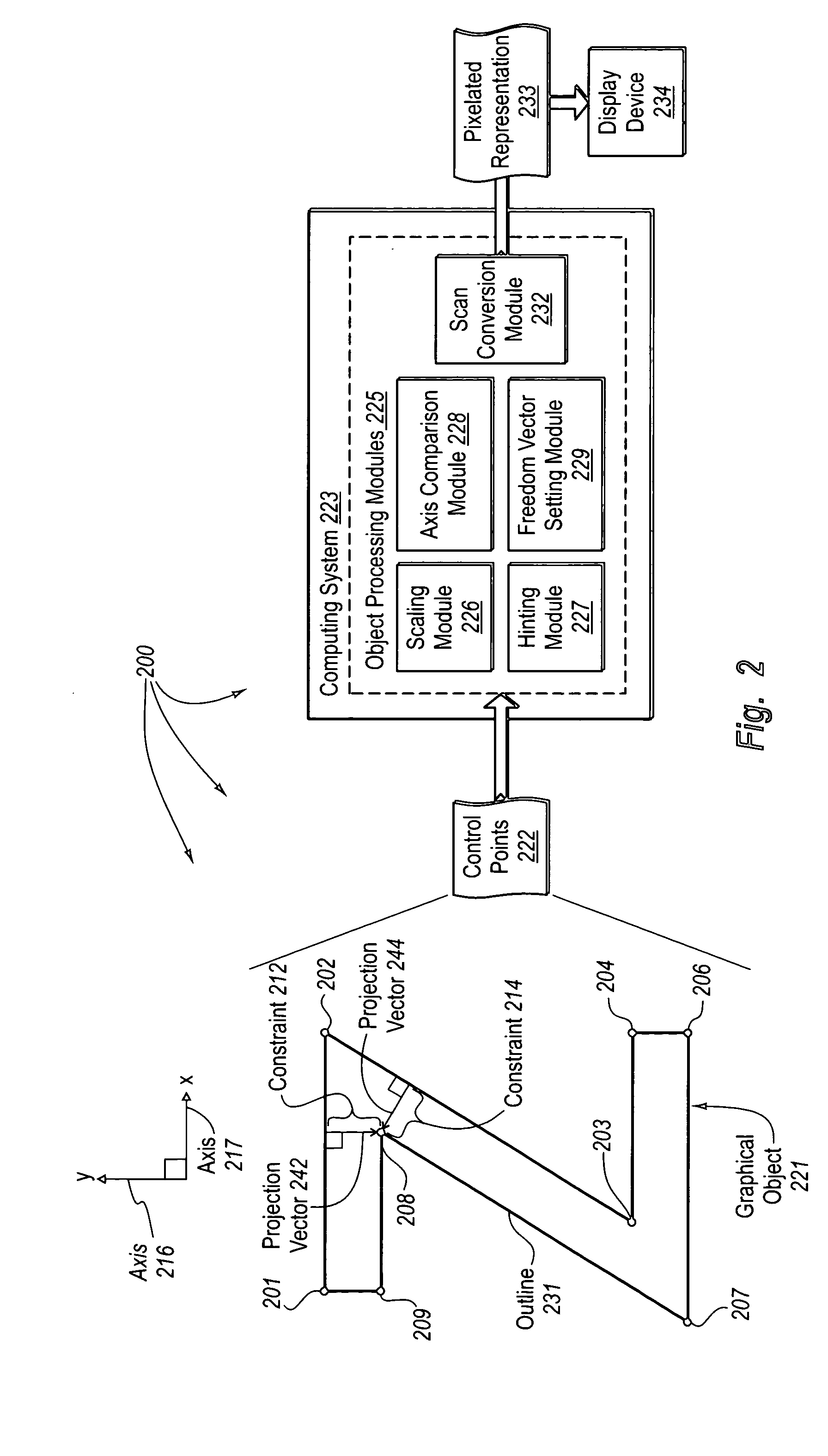
Dynamically determining directions of freedom for control points used to represent graphical objects
The principles of the present invention relate to dynamically determining directions of freedom for control points used to represent graphical objects such as text. A computing system identifies a first function that represents a first constraint, solutions to the first function indicating compliance with the first constraint. The computing system calculates, based on the location of a control point and the identified first function, that the control point does not comply with the first constraint. The computing system automatically determines a first direction of freedom in which the control point can be moved to comply with the first constraint such that movement of the control point in the first direction of freedom has a reduced likelihood of causing non-compliance with other constraints.
Owner:MICROSOFT TECH LICENSING LLC
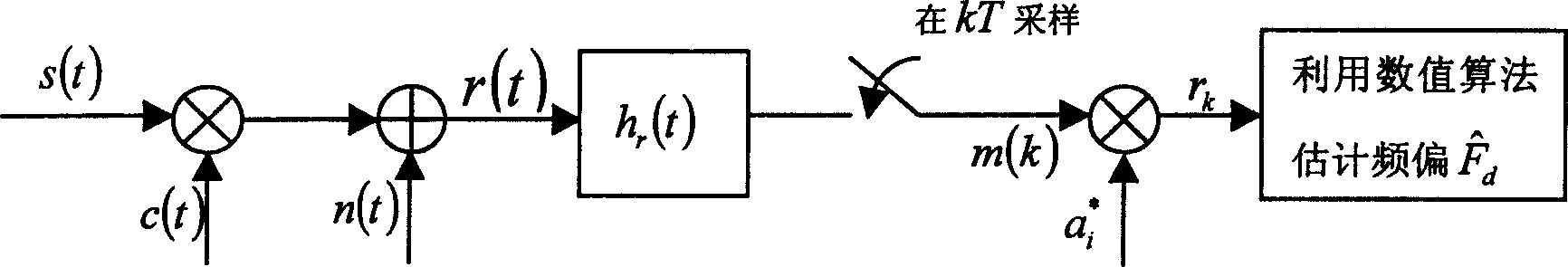
Automatic frequency control method
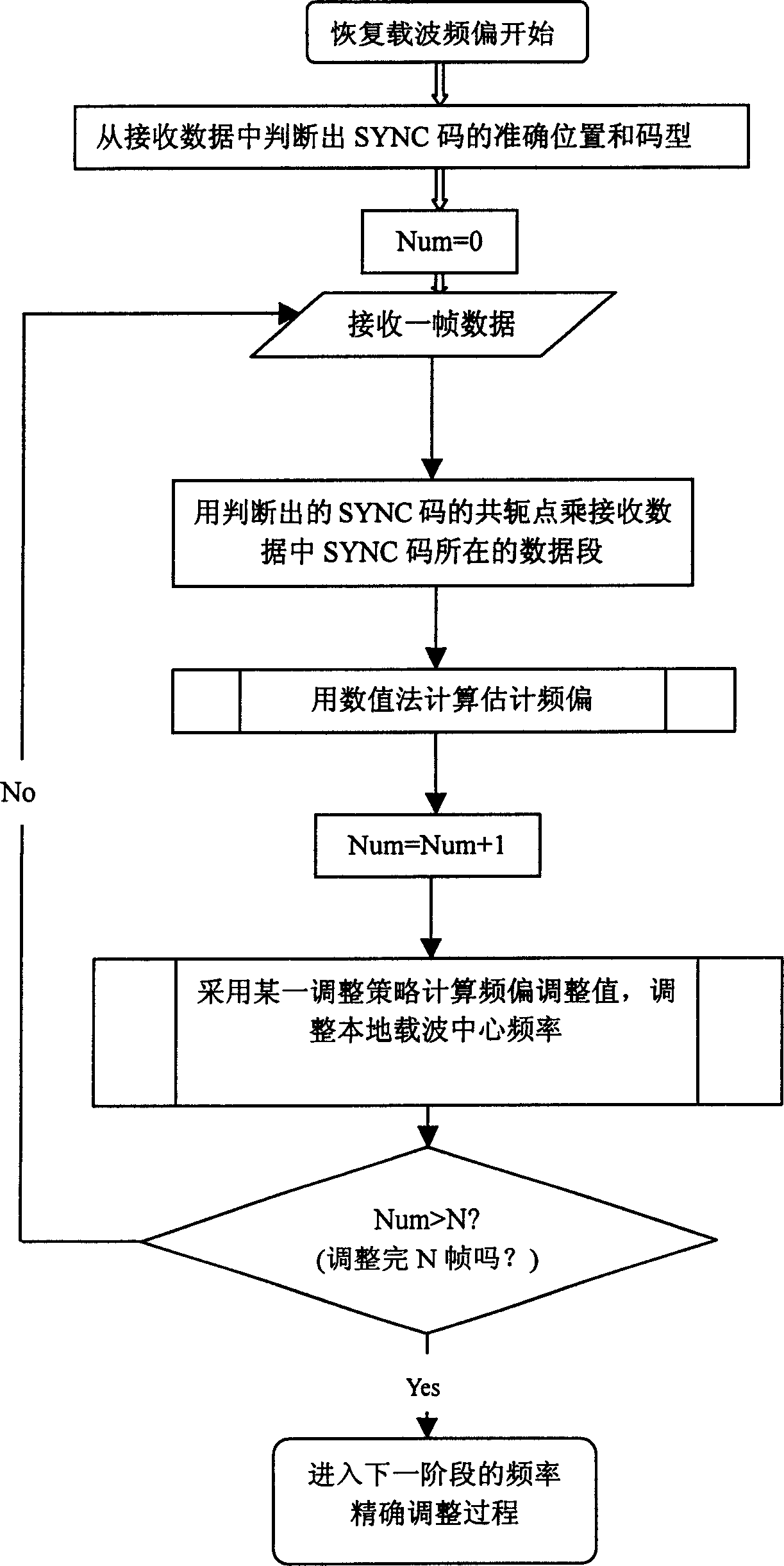
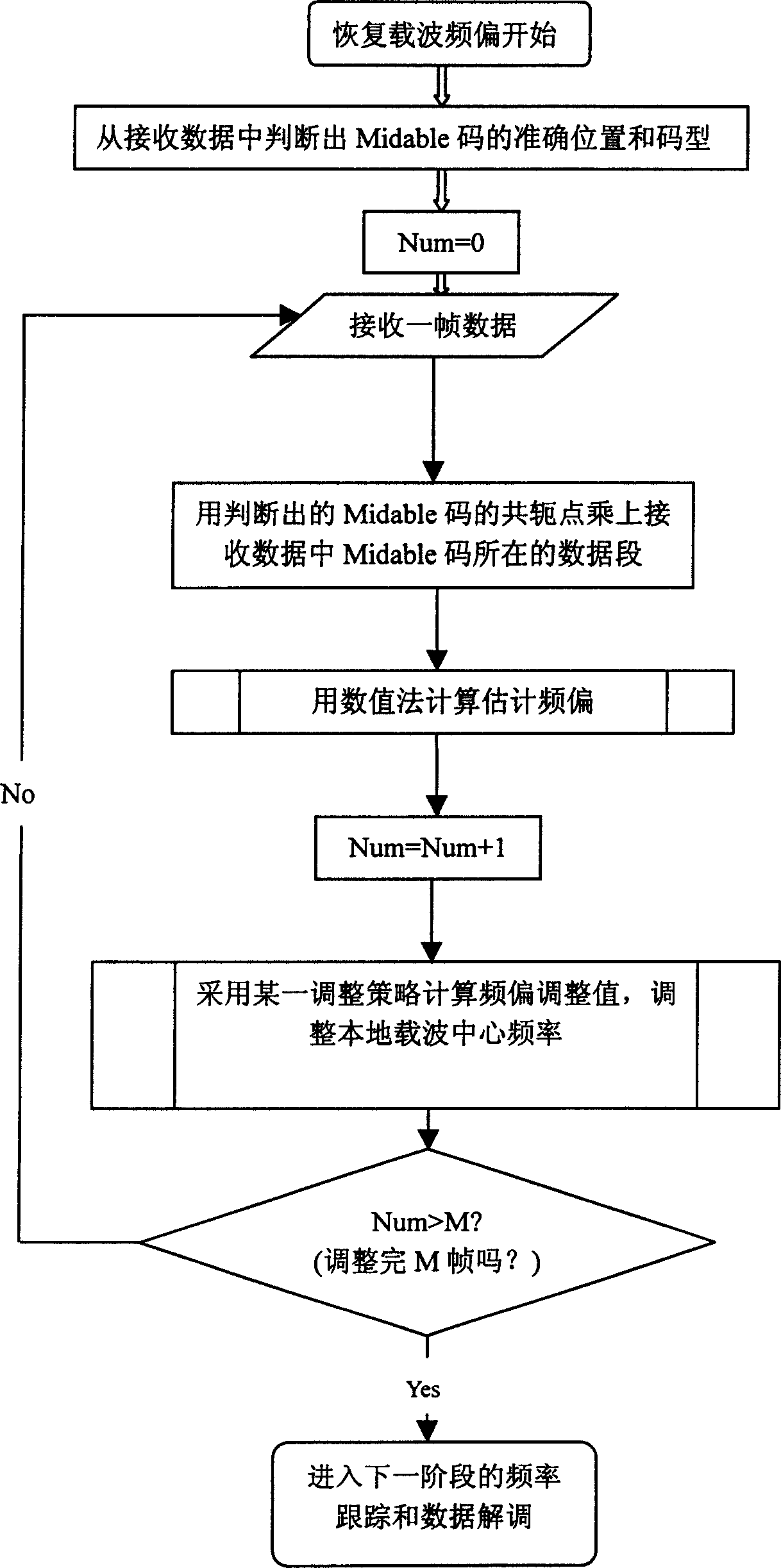
ActiveCN1612619ATake up less resourcesTransmission control/equalisingRadio/inductive link selection arrangementsData segmentCarrier signal
The method includes following steps: determining accurate position and code pattern of sequence of pilot frequency from data received; multiplying conjugate point of sequence of pilot frequency in this sub zone by data segment in the sequence of pilot frequency in data frame received so as to obtain actual data; calculating estimated frequency deviation by using numeric algorithm for automatic frequency adjustment; calculating adjusted value of frequency deviation by using adjustment strategy so as to complete one time of adjustment for center frequency of local carrier wave; after completing N time of adjustment, frequency adjustment for one phase is ended. Under same method, accurate frequency adjustment and tracking procedure for next phase is carried out. Through numeric algorithm, the invention calculates maximum likelihood estimation value of frequency deviation value. Advantages are: quick recovering frequency of carrier wave, quick speed and high efficiency etc.
Owner:RDA CHONGQING MICROELECTRONICS TECH CO LTD +1
Prediction-based network traffic load balancing method
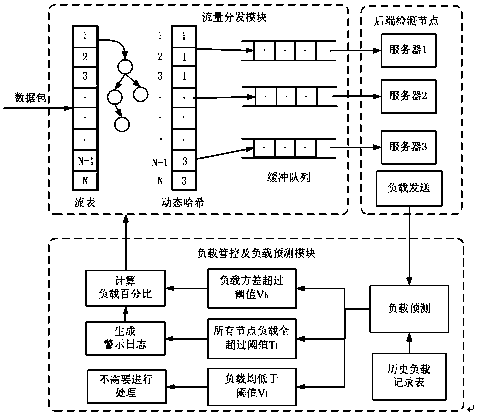
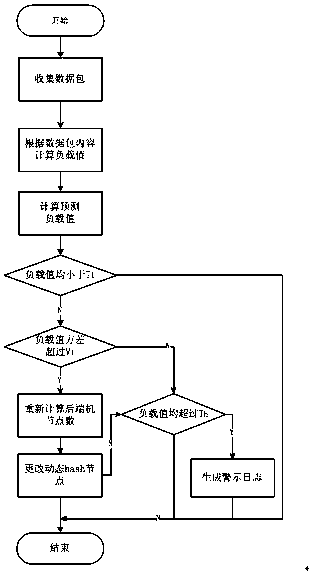
InactiveCN108632159ATo achieve the effect of dynamic adjustmentEvenly distributedData switching networksTraffic capacityHash function
The invention provides a prediction-based network traffic load balancing method which comprises the steps of (S1) calculating a hash value by using a hash function according to quaternion informationand searching a flow table according to the calculated hash value, (S2) directly going to step S4 if a flow table node is found, (S3) entering into a dynamic hash distribution module if the flow tablenode is not found, finding a destination host according to a dynamic hash distribution result and creating a flow table node, (S4) constructing a data packet according to back end processing node information in the flow table and placing the data packet into a corresponding cache queue, (S5) allowing a sending thread to take data from the queue and send the data, (S6) collecting back end feedbackinformation with T as a period, (S7) calculating a predicted load value, and (S8) dynamically adjusting the proportion of virtual nodes in hash to achieve the effect of dynamic adjustment. A zero session destruction rate is achieved on the basis of ensuring load balance and a low packet loss rate.
Owner:哈尔滨英赛克信息技术有限公司
High-performance network log message distribution method for supporting target cluster dynamic detection
ActiveCN109688006AGuaranteed activityReduce the impactData switching networksDistribution methodHigh performance network
The invention provides a high-performance network log message distribution method for supporting target cluster dynamic detection. By adopting a keep-alive dynamic detection strategy of distributed detection and unified state release, consistency of receiving host status on each distribution node can be ensued, and at the same time, weighted load balancing is used in the log message distribution process to avoid a large amount of memory access. By adopting methods such as distributed dynamic detection and unified state distribution, the activity of the receiving host is ensured. The weighted load balancing algorithm is used to distribute the network log messages more evenly to the receiving host in the cluster environment. At the same time, the method of determining the ports of the receiving host packet by packet by hash values of the quintuple (source address, destination address, source port, destination port, and protocol) included in the session packet calculated by using the hashfunction effectively reduces the impact of the failure of the receiving host.
Owner:BEIJING TIANYUAN TETONG SCI & TECH CO LTD
Processor implementation device including transcendental function calculation
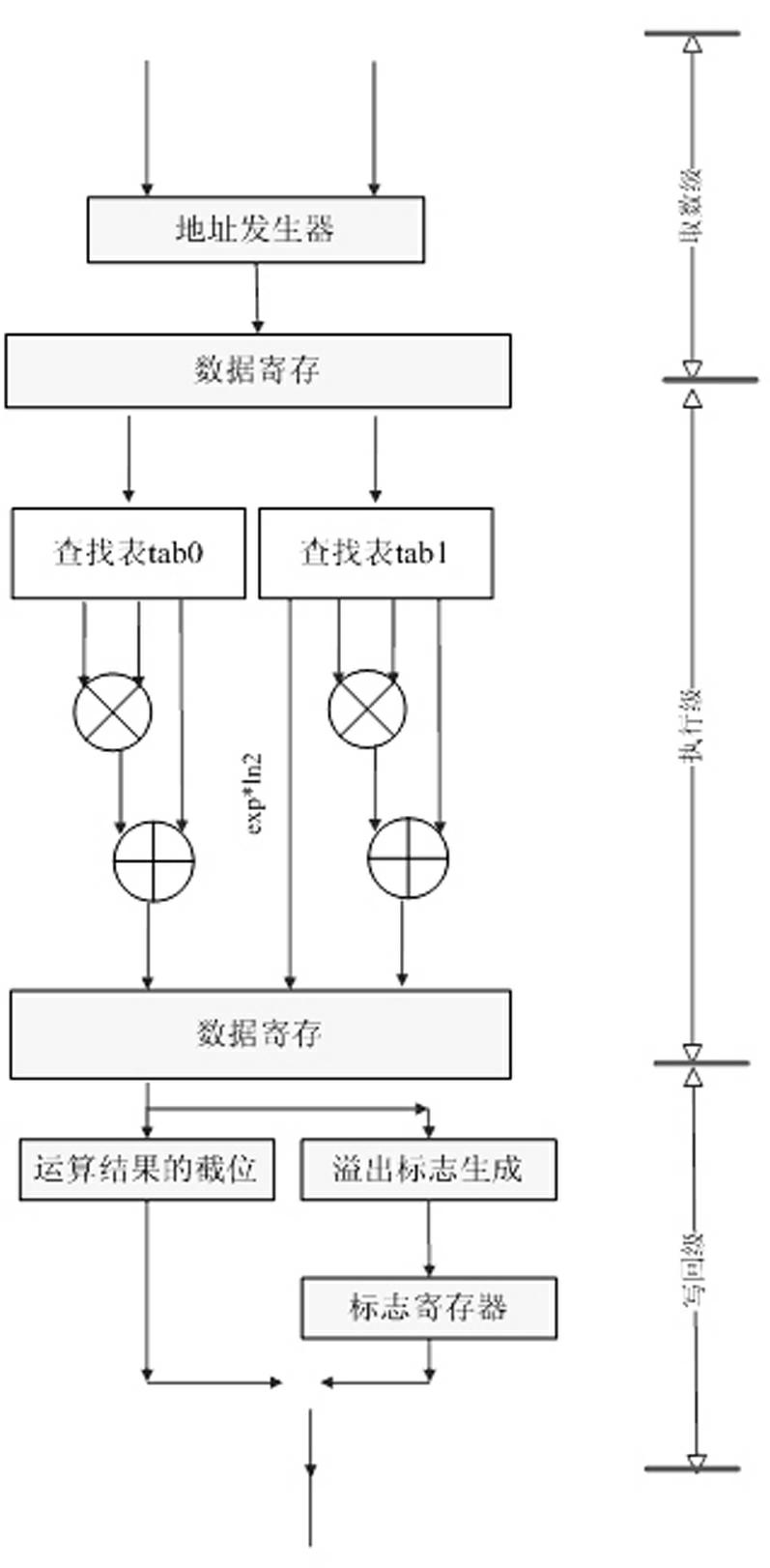
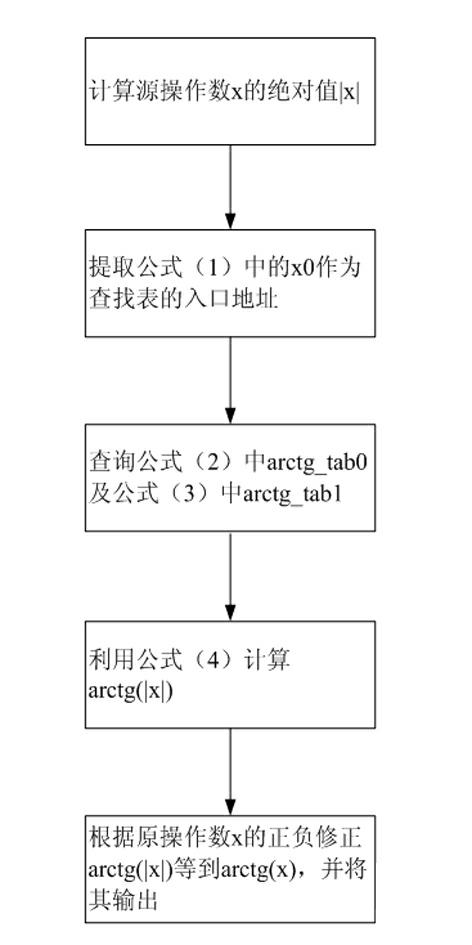
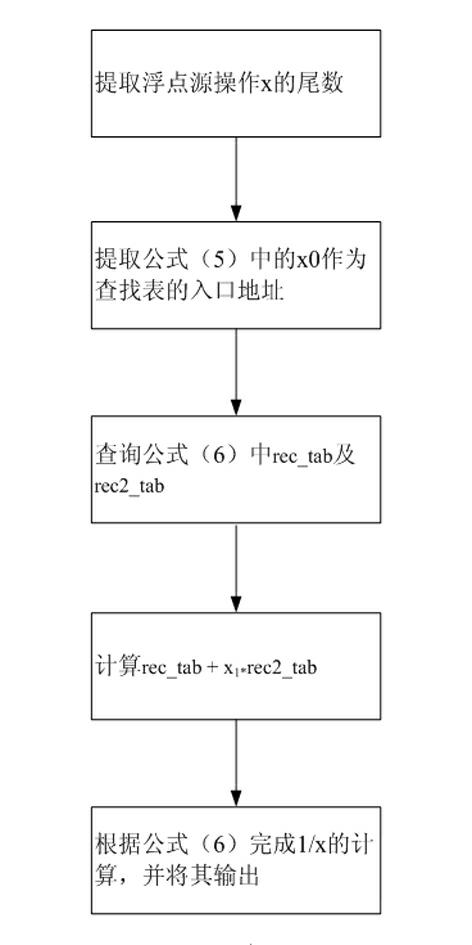
A processor implementation device including transcendental function calculation belongs to the technical field of digital signal processor, and aims to provide hardware capable of quickly achieving calculation of fixed-point arc tangent value, floating-point reciprocal, floating-point natural logarithm and floating-point evolution. The hardware circuit is a three-stage pipeline architecture sequentially consisting of a fetching stage including an address generator and a first data register, an execution stage including tab0, tab1, two multiplication-addition modules and a second data register, and a write back stage including a truncation module and a mark generation module, wherein the fetching stage is used for generating addresses for looking up tables, and registering and transmitting control signals desired for the execution stage and the write back stage, the transformed input data and an address signal to the execution stage for calculation; the execution stage is used for calculating the fixed-point arc tangent value, floating-point reciprocal, floating-point natural logarithm and floating-point evolution; and the write back stage is used for generating the mark, and truncating and outputting the operation result.
Owner:CHINA ELECTRONIC TECH GRP CORP NO 38 RES INST
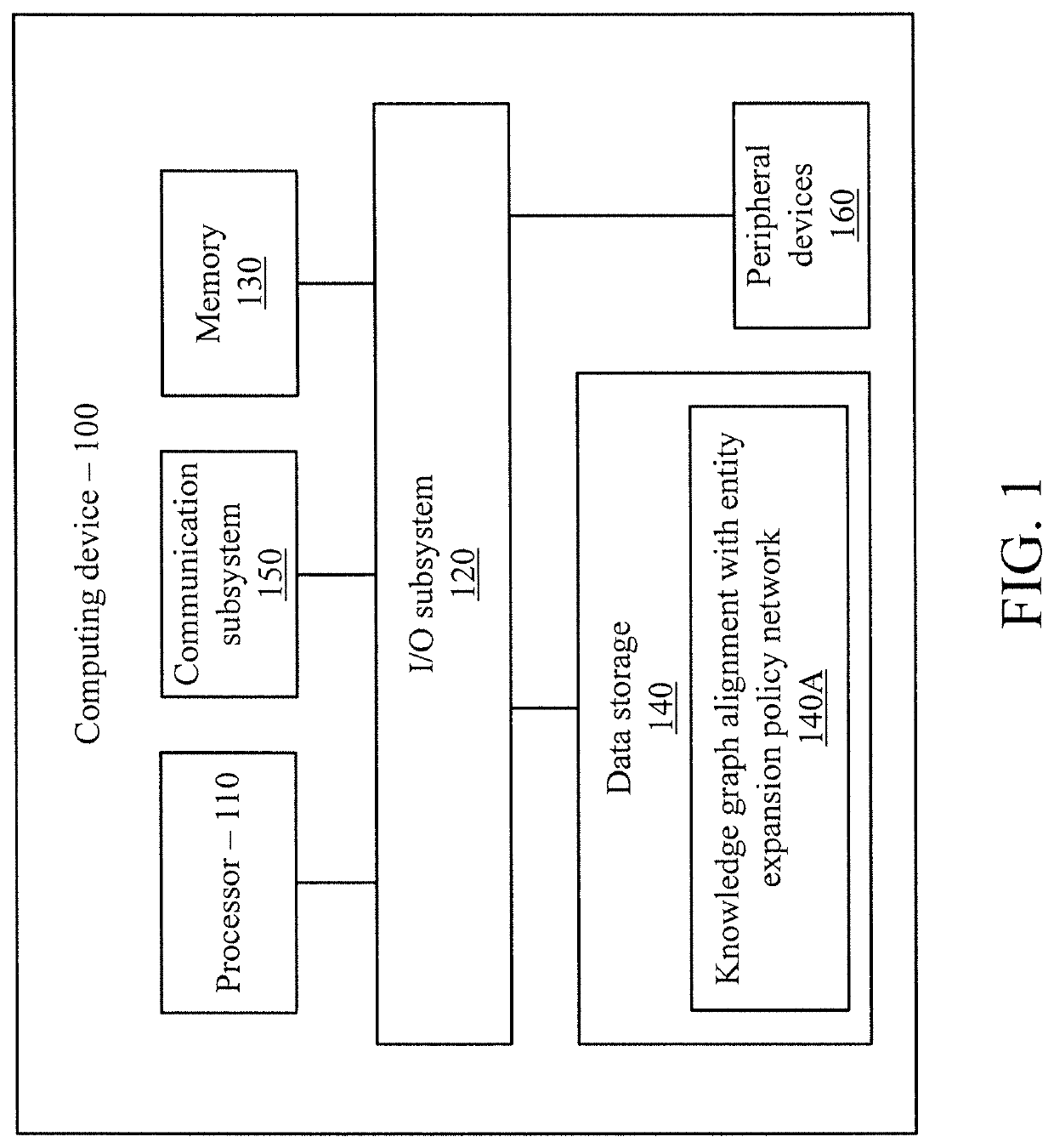
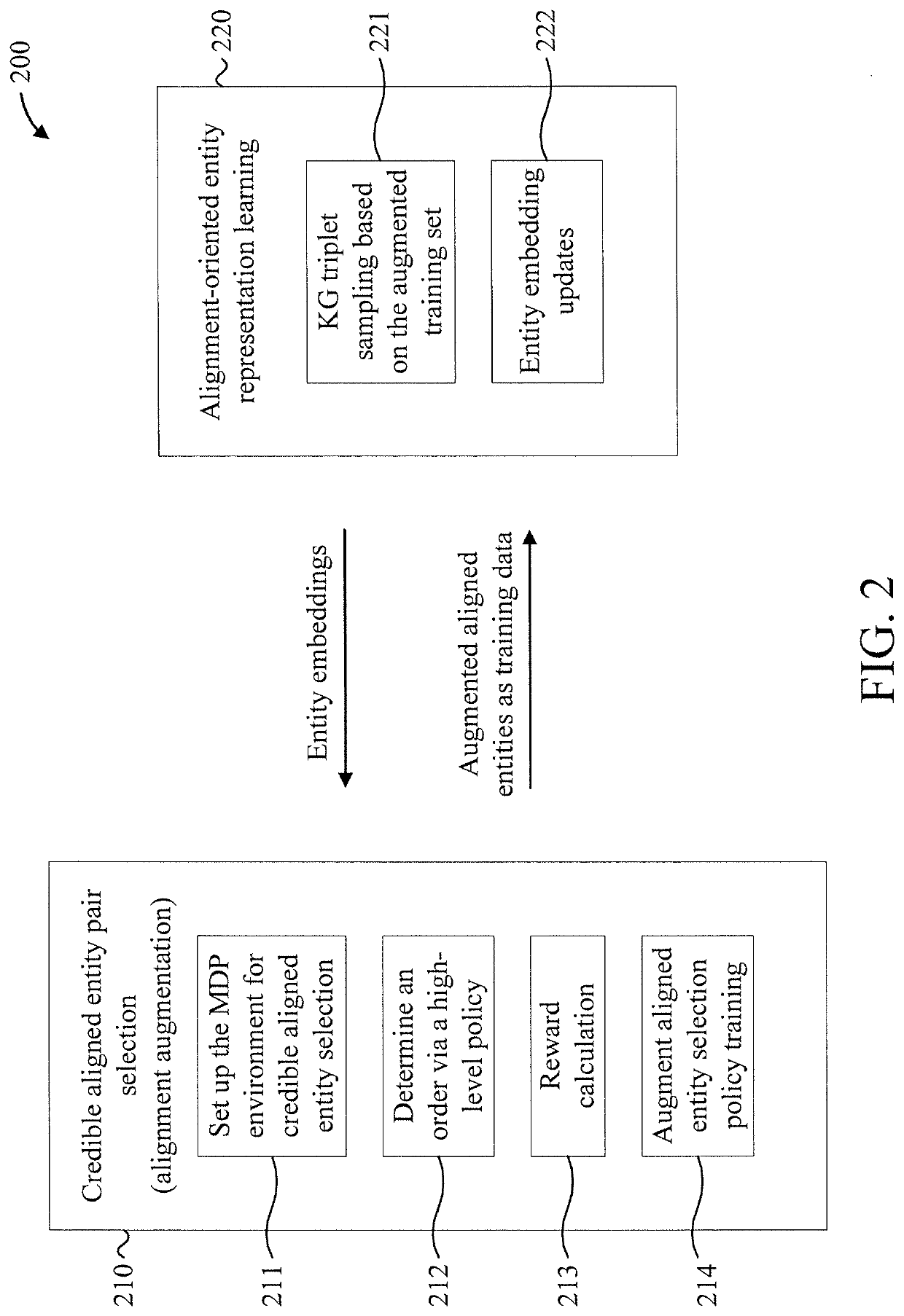
Knowledge graph alignment with entity expansion policy network
PendingUS20210216887A1Character and pattern recognitionArtificial lifeTheoretical computer scienceEngineering
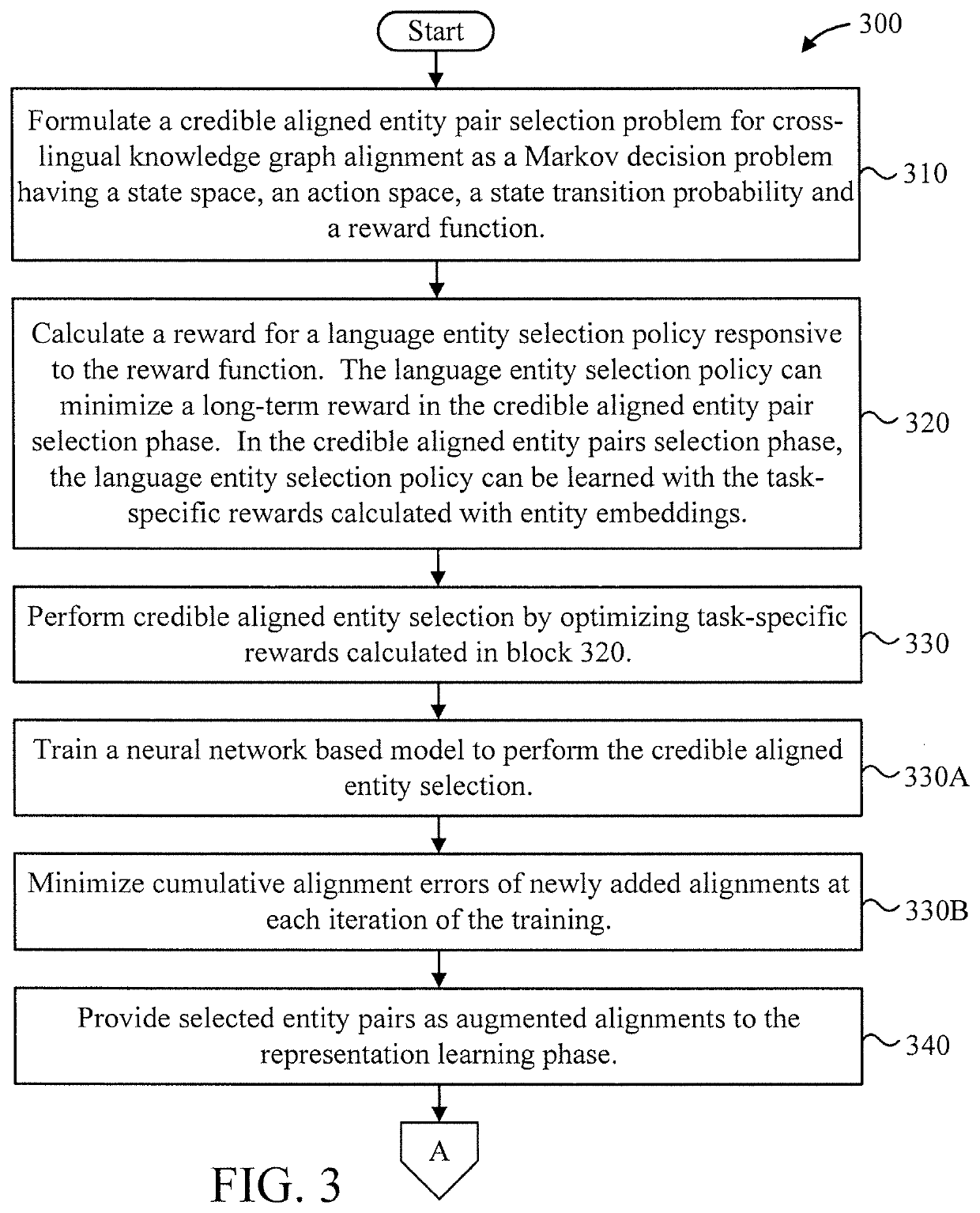
A computer-implemented method is provided for cross-lingual knowledge graph alignment. The method includes formulating a credible aligned entity pair selection problem for cross-lingual knowledge graph alignment as a Markov decision problem having a state space, an action space, a state transition probability and a reward function. The method further includes calculating a reward for a language entity selection policy responsive to the reward function. The method also includes performing credible aligned entity selection by optimizing task-specific rewards from an alignment-oriented entity representation learning phrase. The method additionally includes providing selected entity pairs as augmented alignments to the representation learning phase.
Owner:NEC LAB AMERICA
Function calculation cold start acceleration method and device, equipment and storage medium
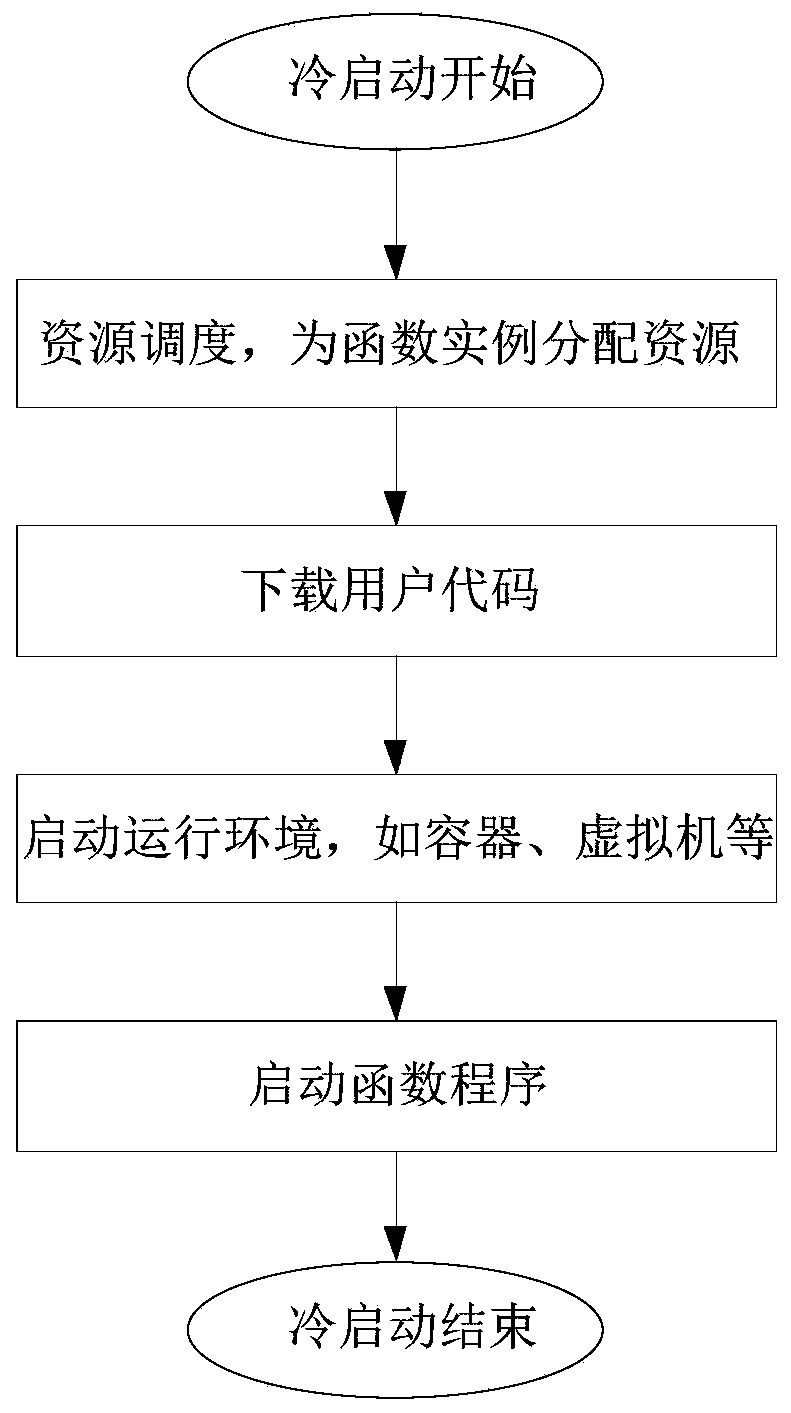
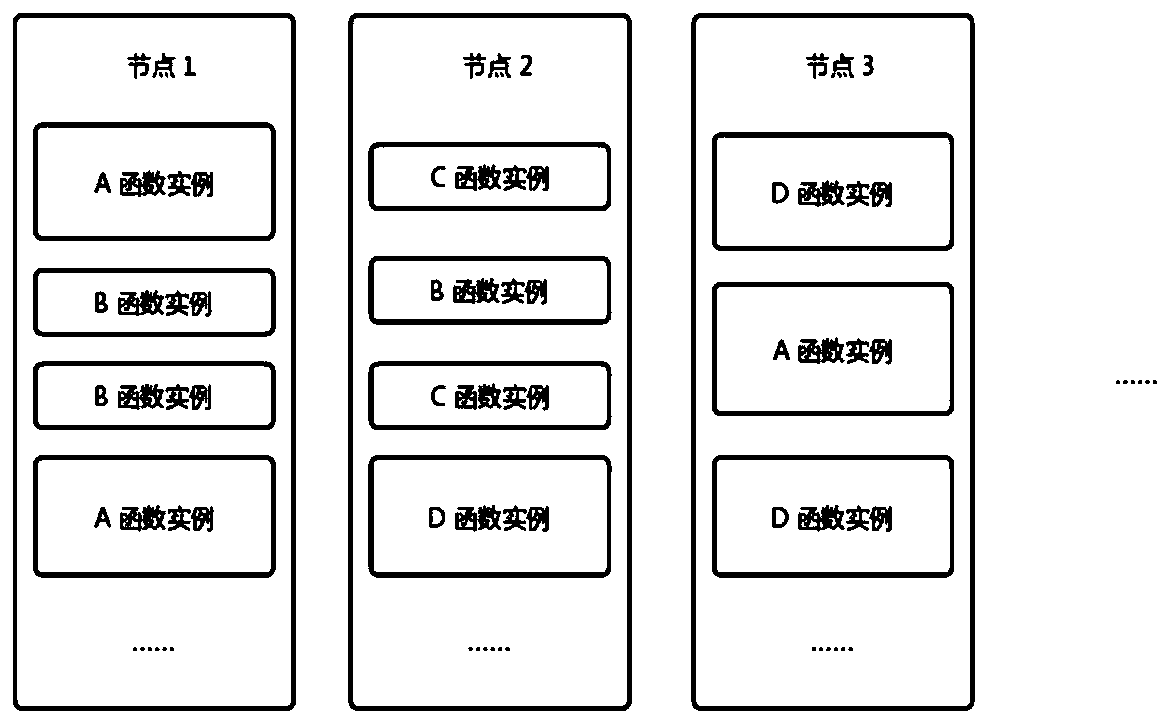
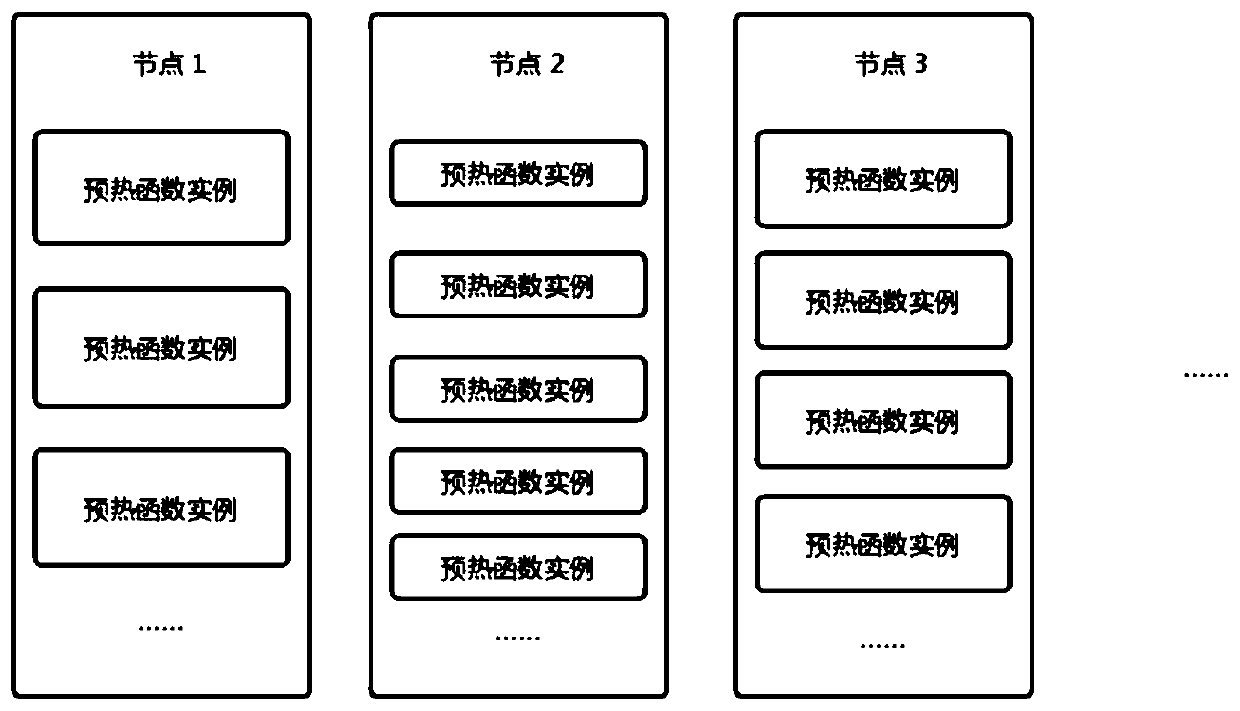
ActiveCN111475235AReduced cold start timeImprove resource utilization efficiencyProgram loading/initiatingExecution paradigmsThermodynamicsStart up time
An embodiment of the invention provides a function calculation cold start acceleration method, a function calculation cold start acceleration device, equipment and a storage medium. The function calculation cold start acceleration method comprises the steps of: in response to an instruction used for instructing cold start of a preset function, acquiring a target preheating function instance supporting operation of the preset function, wherein the target preheating function instance comprises a function program supporting dynamic function code loading; acquiring a user code corresponding to thepreset function; and loading the user code on the target preheating function instance through using the function program supporting dynamic function code loading to obtain an operation result corresponding to the user code. According to the function calculation cold start acceleration method and the function calculation cold start acceleration device of the invention, the problem that the resource utilization efficiency of a function calculation platform cannot be reduced because the function cold start time cannot be effectively shortened in the prior art can be solved.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Nonlinear parameter regulating phase-locked loop method and device
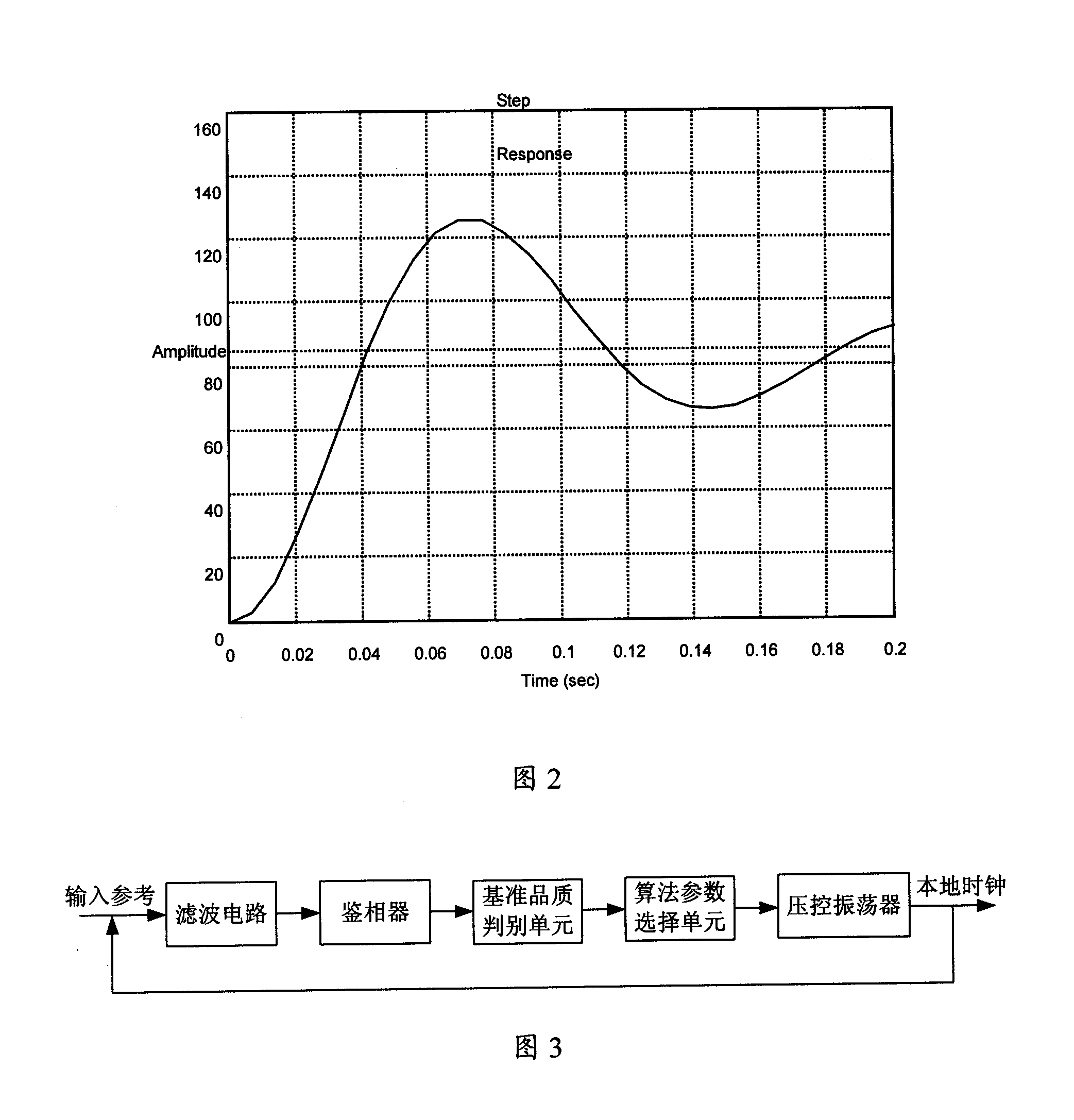
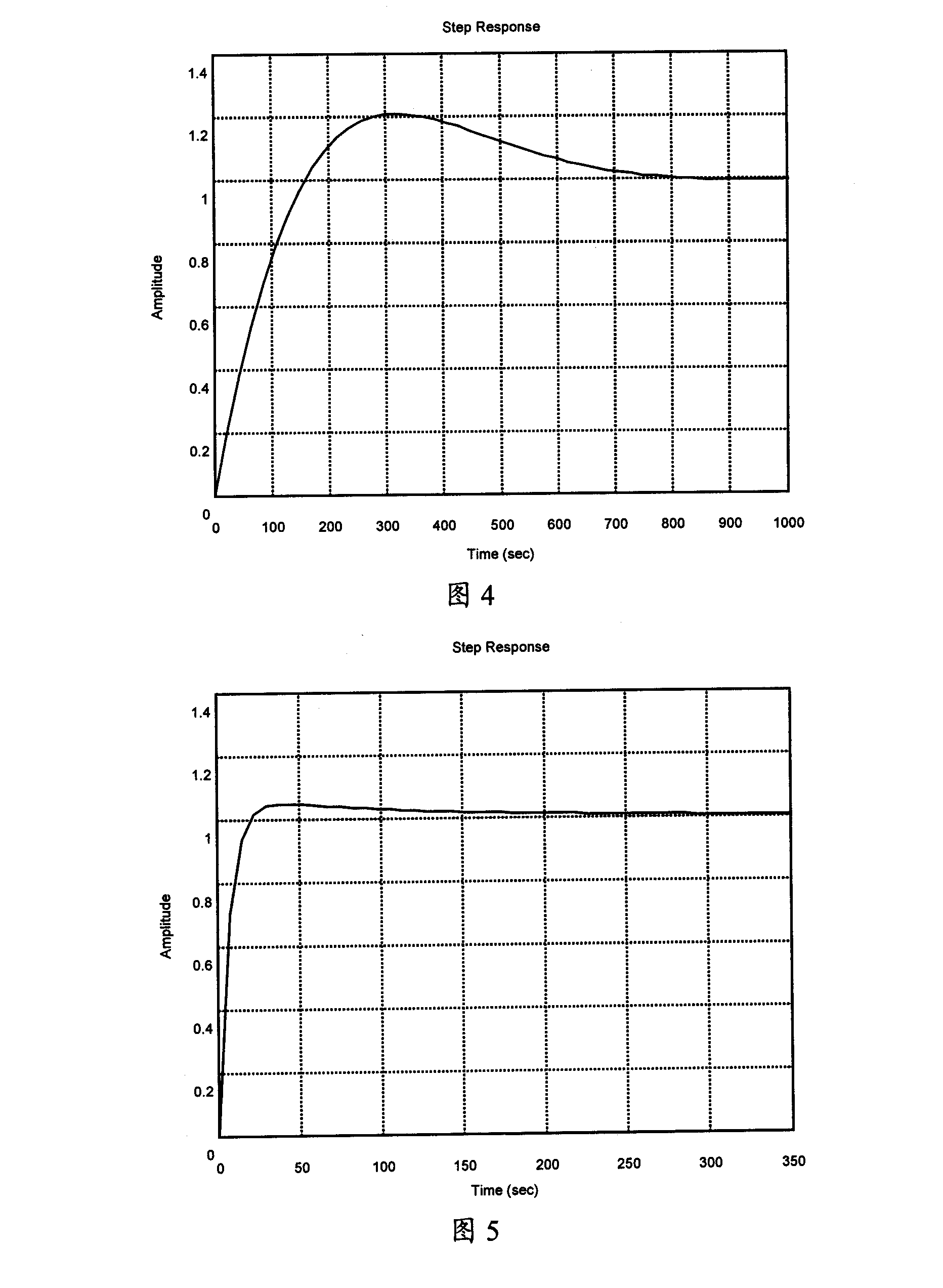
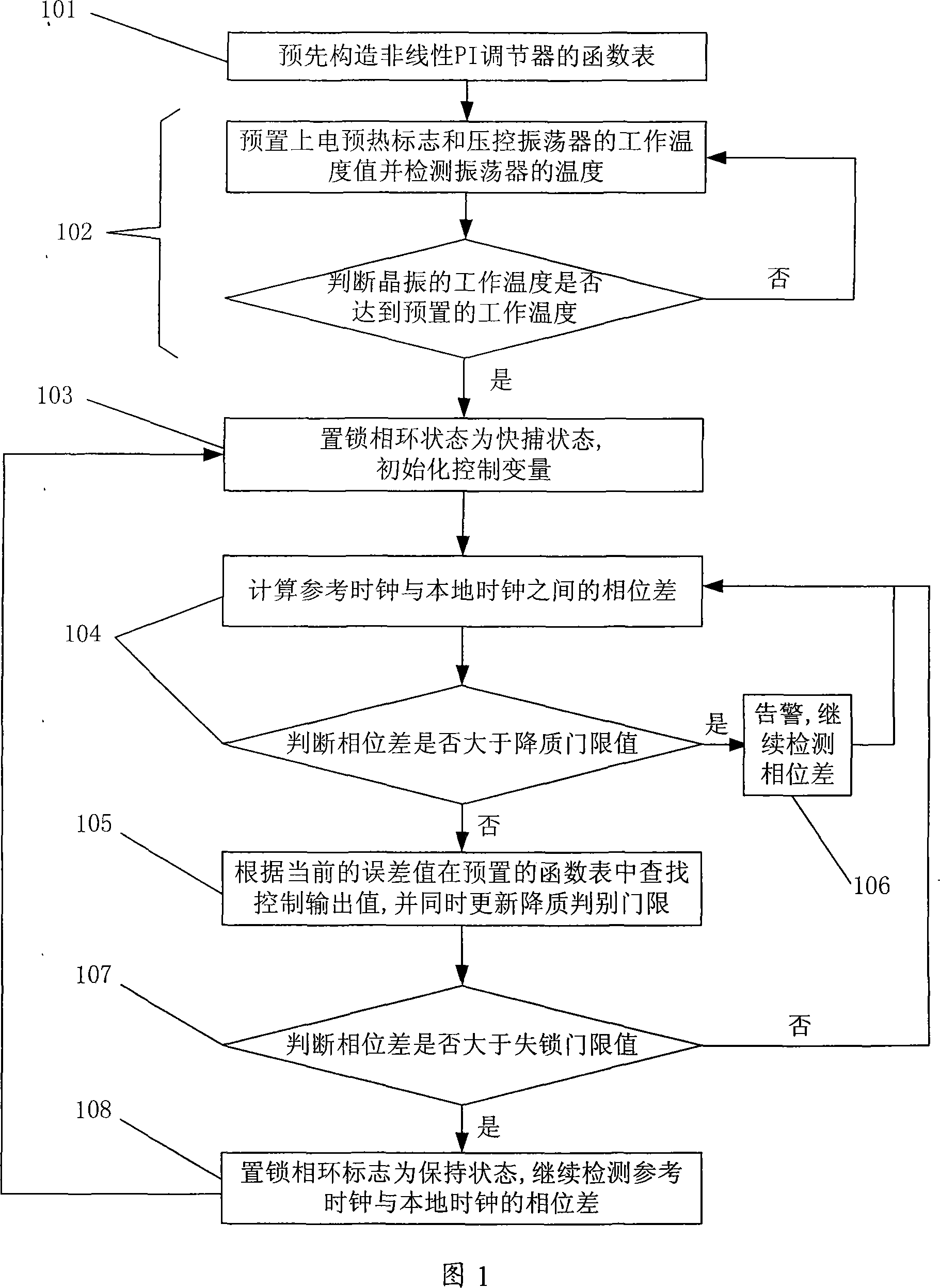
InactiveCN101174940AImprove dynamic response performanceSmooth changeSynchronising arrangementPhase differencePhase-locked loop
The present invention provides a method and a device for regulating the phase-locked loop with non-linear parameter; the present invention is used for realizing the clock synchronization between the local clock and the network clock; the method comprises that the function list of a non-linear PI regulator is prefabricated and the function calculation data list is stored in a non-volatile memory in advance; the phase difference between the reference clock and the local output clock is detected cyclically. The gain parameter of the present PI control link obtained by the data list stored in advance is consulted according to the phase difference and the parameter is substituted into the PI control link to calculate the controlling quantity. The method and the device of the present invention, by presetting the non-linear algorithm parameter list, obtains the gain parameter value of the PI control link at every phase error point; the anti-interference capability is greatly increased compared with the original one; the dynamic response capability of the phase-locked loop is promoted, the regulating time and the overshoot are further reduced; moreover, the robust property of the phase-locked loop is enhanced.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com