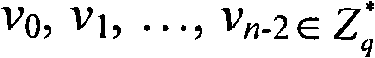Multicast cryptographic key distribution method and updating method based on unicast conversation cryptographic key
A session key and multicast key technology, which is applied in the branch office to provide special service devices, data exchange details, security devices, etc., can solve the problem of low efficiency of multicast key distribution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
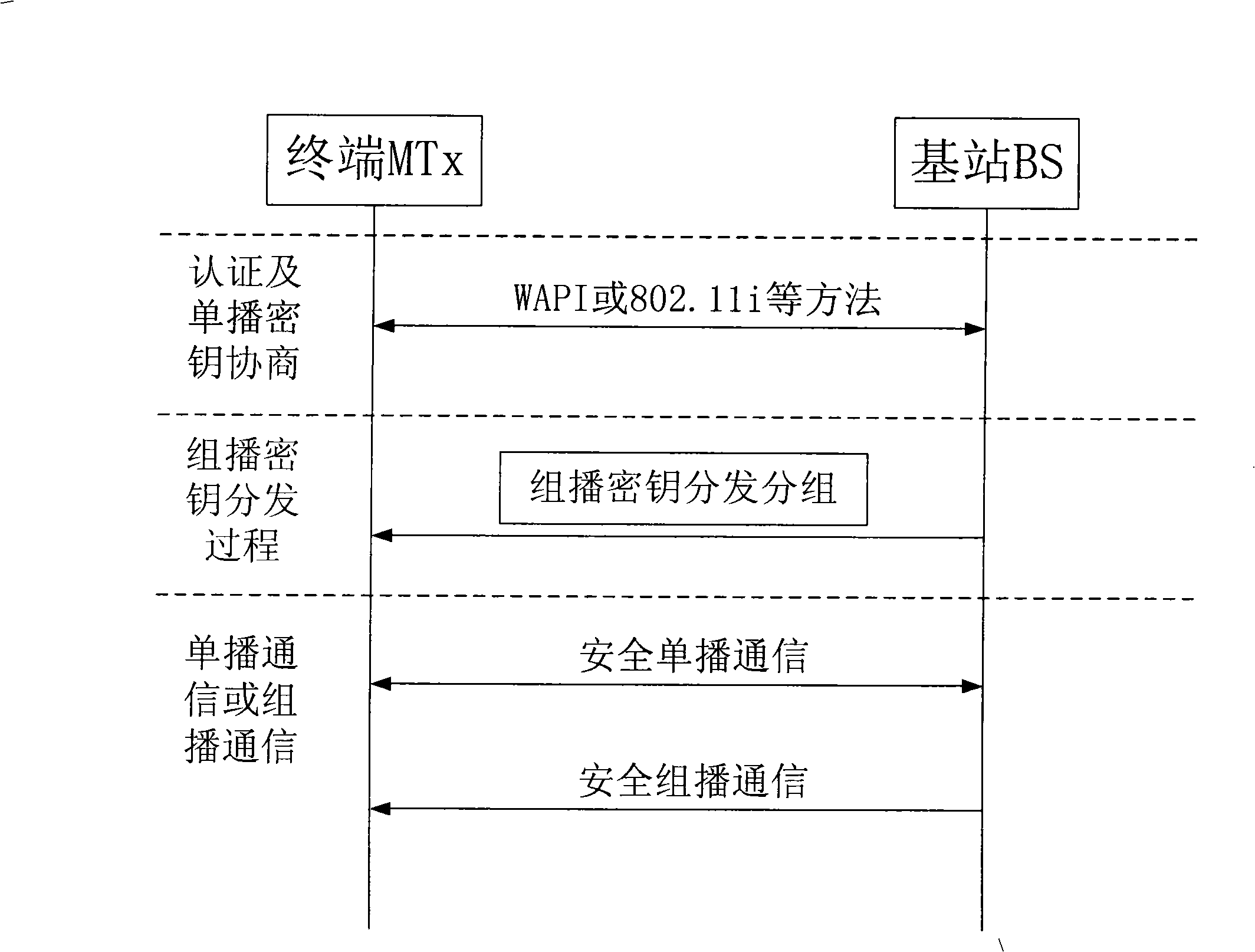
[0076] see figure 1 , the present invention is based on the multicast key distribution method of unicast session key and specifically comprises the following steps:
[0077] 1) Establish system parameters, the system parameters are: set (G 1 , +) and (G 2 , ·) is a cyclic group with both orders p, p is a prime number, and satisfies G 1 The Diffie-Hellman calculation problem in is a difficult problem; let P be G 1 Generator of ; let e be G 1 and G 2 The bilinear transformation on , that is, e: G 1 ×G 1 →G 2 ;Let h( ) be a one-way hash function;
[0078] This step is only to establish the system parameters during the first application, after the establishment, this step is not required in the subsequent repeated application;
[0079] 2) The base station performs security authentication and unicast session key USK negotiation with each terminal, and each terminal i shares a unicast session key USK with the base station i , the unicast session integrity verification key ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com