Concurrent access control method and device
An access control and access lock technology, applied in the network field, to achieve the effect of improving time, reducing load, and reducing invalid operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
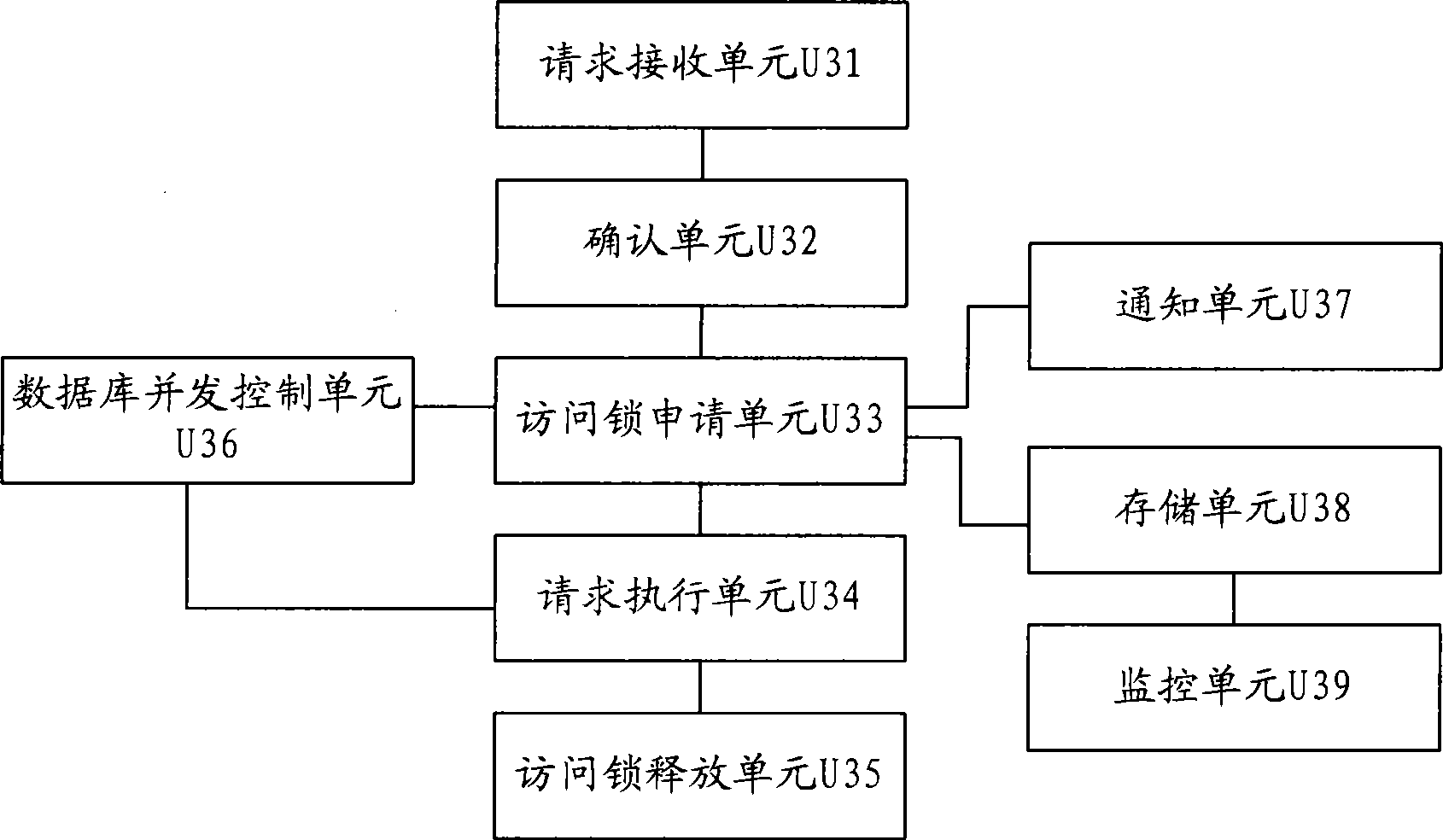
Image
Examples
Embodiment 1
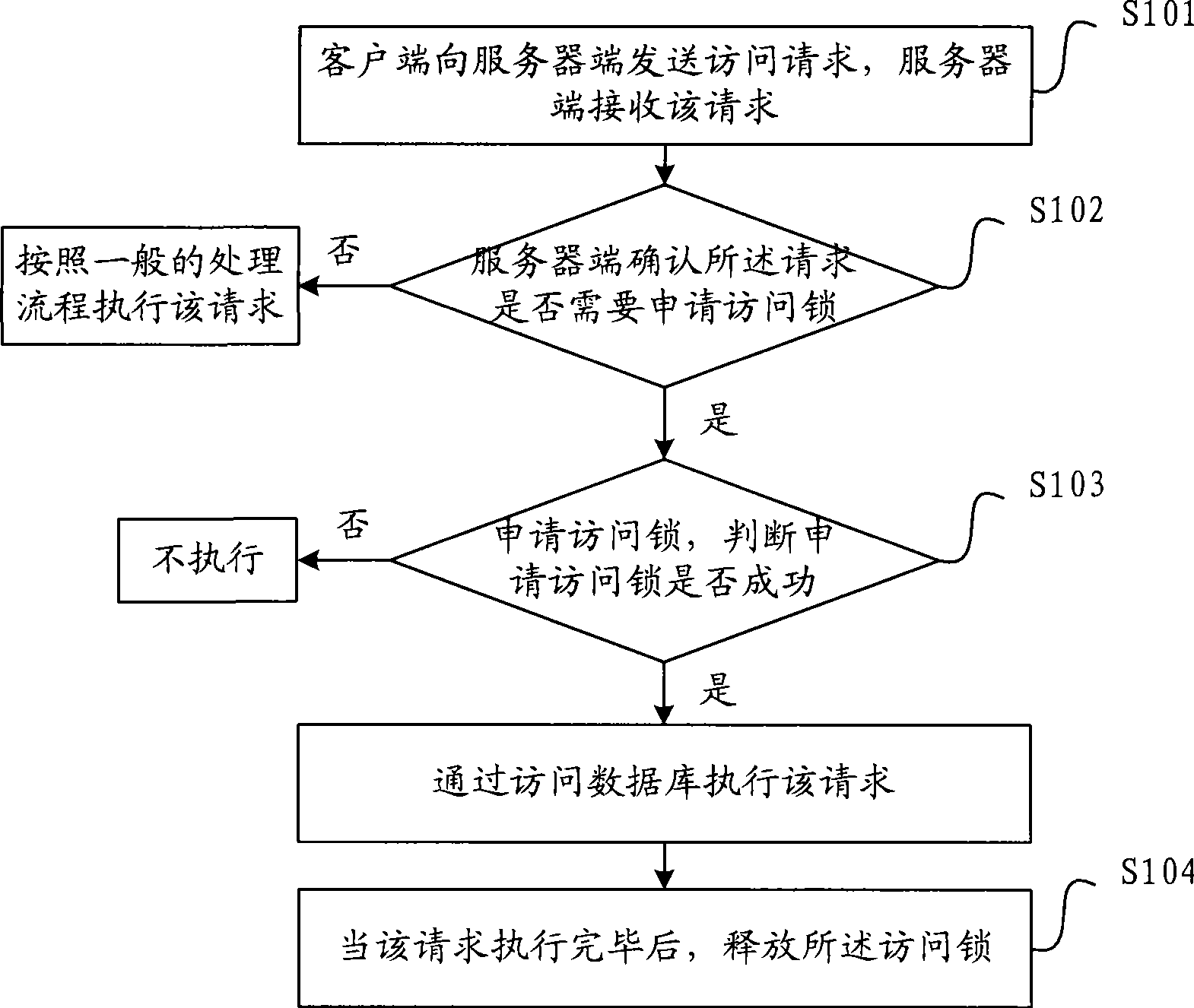
[0039] refer to figure 1 , is a flowchart of a concurrent access control method described in the embodiment. Wherein, the server side in the following process refers to the application server side.
[0040] S101, the client sends an access request to the server, and the server receives the request;
[0041] S102, the server side confirms whether the request needs to apply for an access lock, if yes, proceed to S103 to apply for an access lock; if not, execute the request according to the general processing flow;
[0042] The confirmation process refers to confirming whether the data currently requested to be accessed is data that needs to be prevented from concurrent access, or whether the function currently requested to be executed is a function that needs to be prevented from concurrent access (this function may need to access a batch of data). During the process of the server processing business, some data or functions can be accessed or executed concurrently, while some...
Embodiment 2
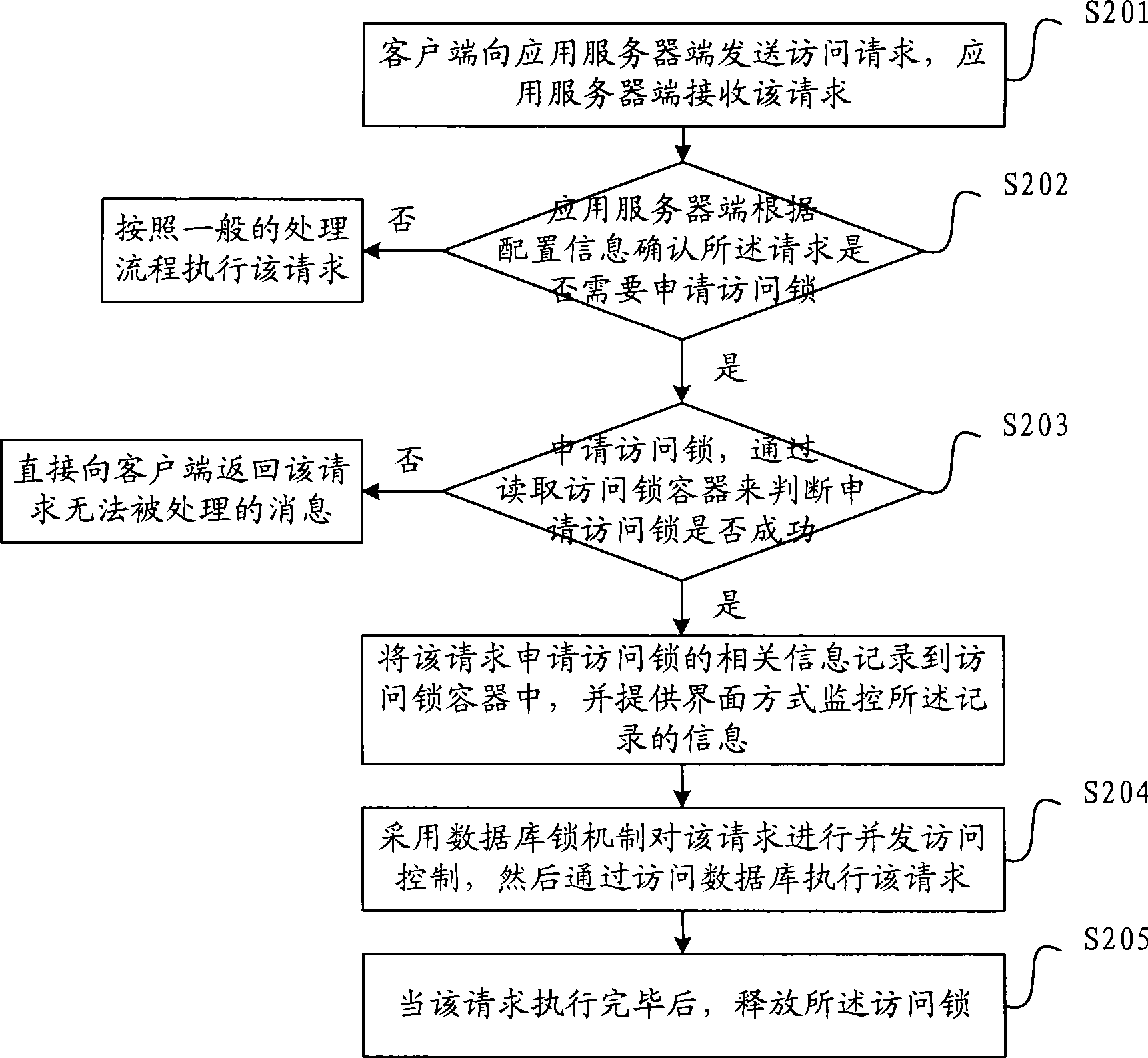
[0051] refer to figure 2 , is a flowchart of a concurrent access control method described in Embodiment 2.
[0052] S201, the client sends an access request to the application server, and the application server receives the request;
[0053] S202, the application server confirms whether the request needs to apply for an access lock according to the configuration information, if yes, proceed to S203 to apply for an access lock; if not, execute the request according to the general processing flow;
[0054] This embodiment provides a configurable way to perform concurrency control. Through business analysis, for each data or function that needs to be prevented from concurrent access, it is pre-registered in the configuration information of the application server, thereby determining the concurrent objects that need to be locked. Every time there is concurrent access, first check whether there is an object currently requested to be accessed in the configuration information, if ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com