Method and system blocking charging attack
A billing overflow and mobile terminal technology, applied in the field of communication, can solve the problems that firewalls cannot stop and billing overflow attacks cannot be solved, and achieve the effect of simple and feasible operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
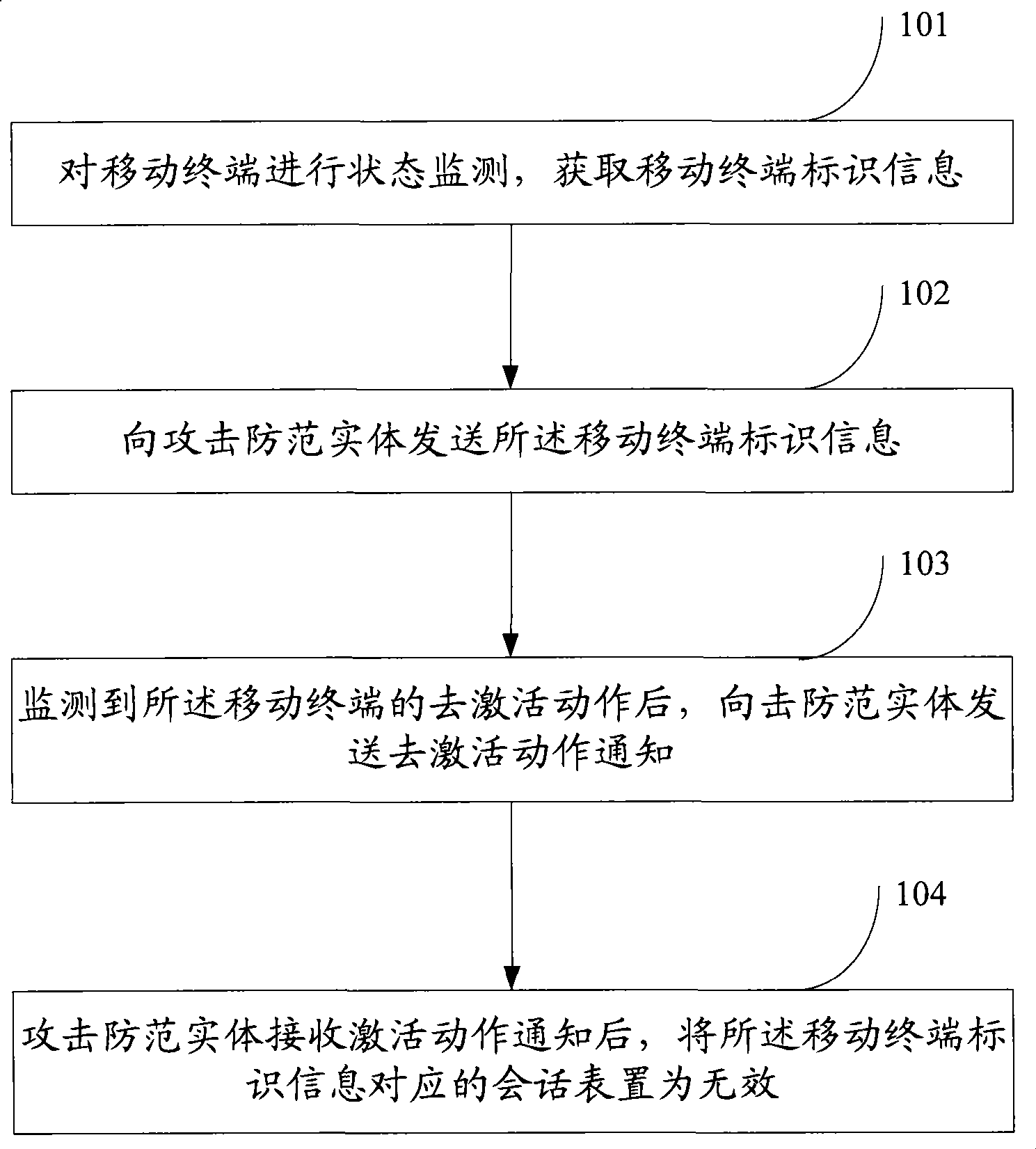
[0056] Such as figure 1 As shown, it is embodiment one of the present invention's method for preventing billing overflow attack, including:
[0057] 101. Perform status monitoring on the mobile terminal, and obtain identification information of the mobile terminal;
[0058] The status monitoring of the mobile terminal specifically refers to unpacking and checking the past GTP messages; for the messages that pass the security check, a mobile terminal status monitoring mechanism is established according to the status mechanism stipulated in the GTP protocol. In order to monitor the state of the mobile terminal; the session information of the mobile terminal is usually displayed as a GTP message, so obtaining the session information of the mobile terminal can be obtained by directly intercepting the GTP message or intercepting the GTP message sent by the GSN.
[0059] Wherein, the state monitoring of the mobile terminal is performed in the GTP protocol domain, that is, it can be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com