Method for local area network access authentication of casual user
A temporary user, network access technology, applied in user identity/authority verification, data exchange through path configuration, nan, etc., can solve the problems of fast personnel flow, poor security, and complicated user management process in public network access areas. , to achieve the effect of simple and standardized management process, improved safety and high safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] In order to clearly illustrate the technical features of this solution, the present invention will be described in detail below through specific implementation modes and in conjunction with the accompanying drawings.
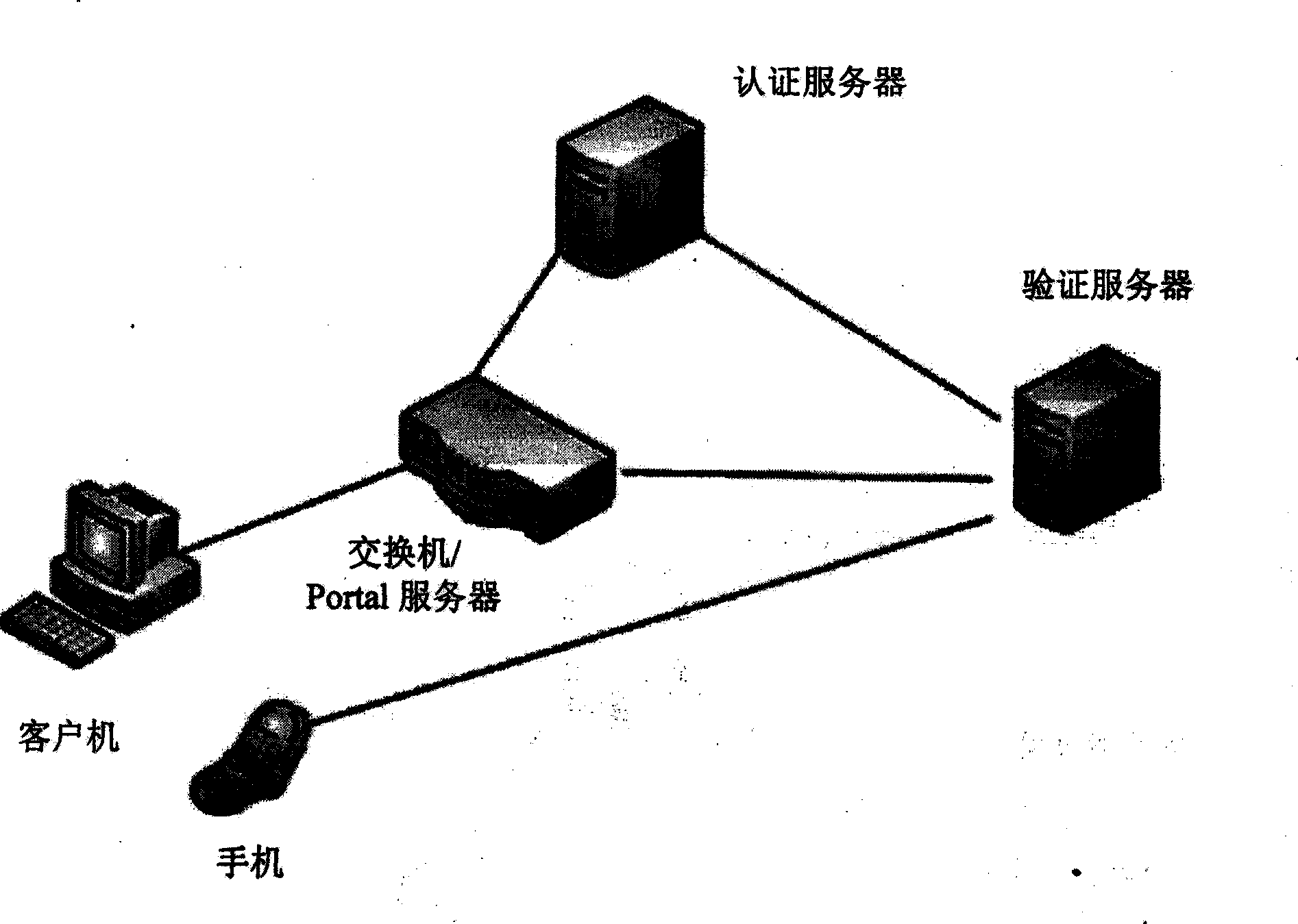
[0016] As shown in FIG. 1 , it is a schematic diagram of the system structure connection of the authentication method of the present invention. The client's computer is connected to the switch with the built-in Portal server, the switch is connected to the authentication server and the authentication server respectively, the authentication server is connected to the authentication server, and the information sending unit in the authentication server communicates with the mobile phone of the internal user through the communication network. The authentication server is a Radius server, or any authentication server. The Portal server built in the switch can also be a WEB server.
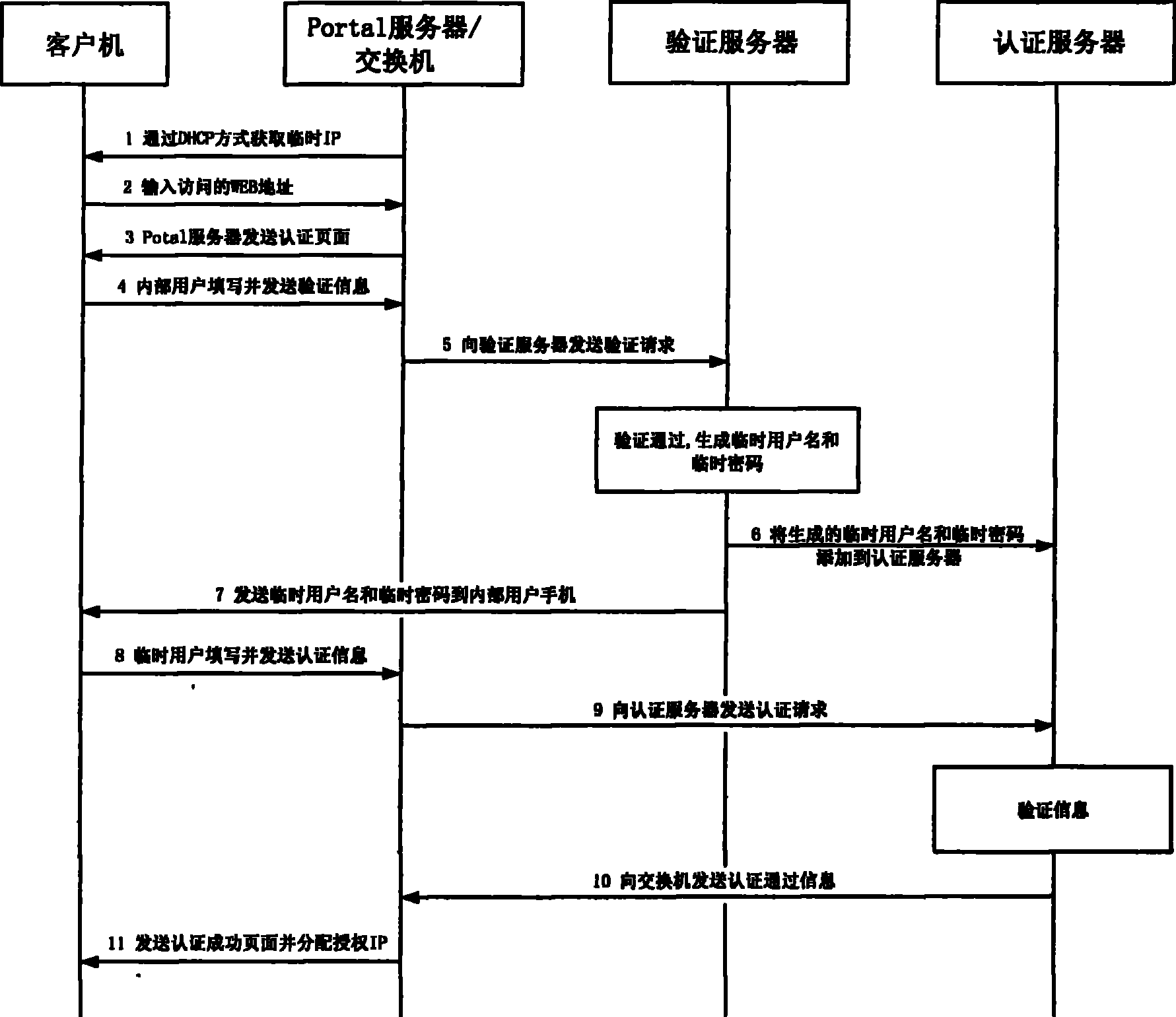
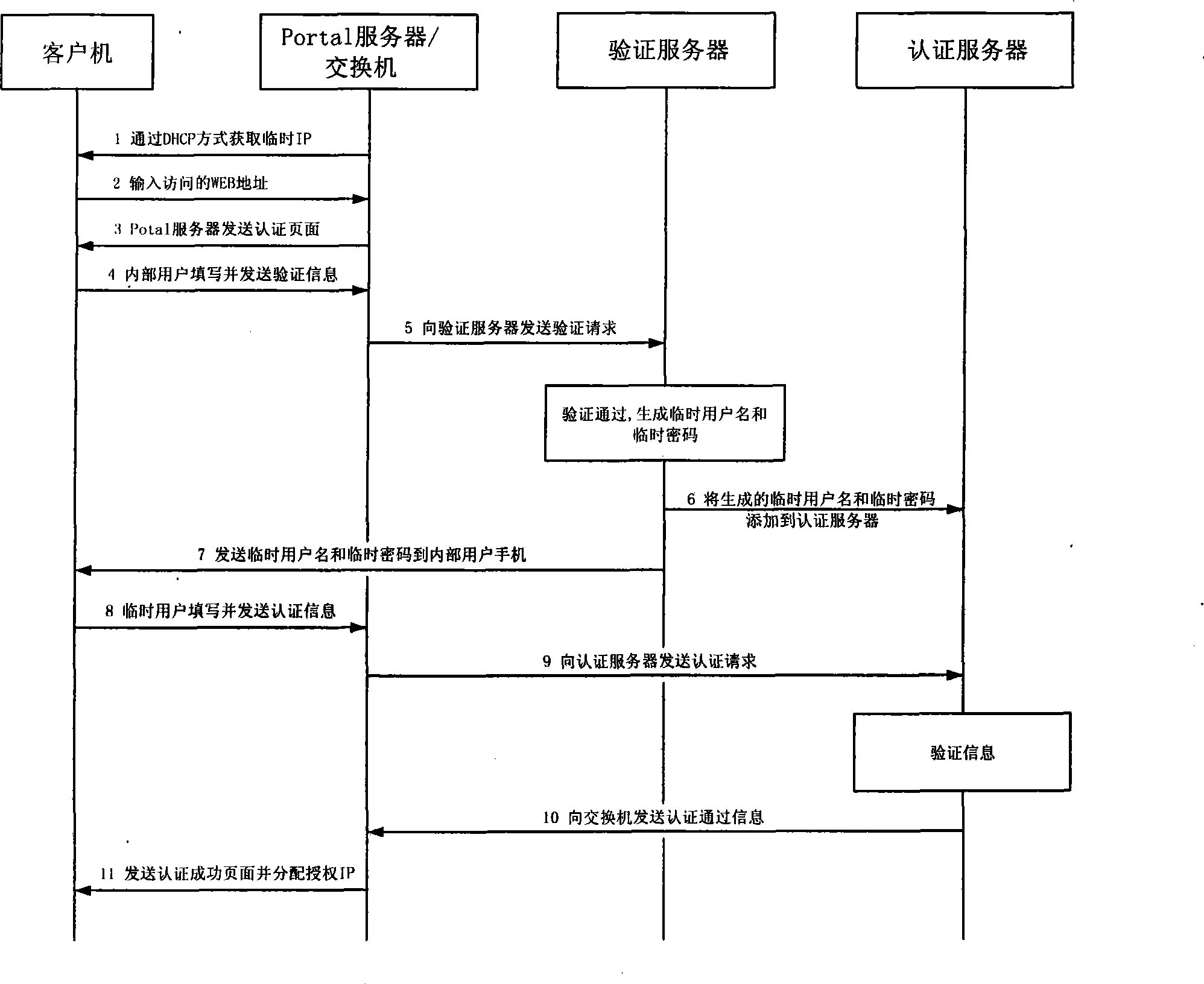
[0017] In the signaling flowchart shown in Fig. 2, an implementation scheme o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com