Cipher key negotiating method, enciphering/deciphering method and signature/verification method
A key agreement and key technology, applied in user identity/authority verification, public key for secure communication, and key distribution, which can solve the problems of undisclosed facts and increased possibility of being deciphered, and achieve strong anti-attack capability , scale and complexity enhancement, solving the effect of small algorithm space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
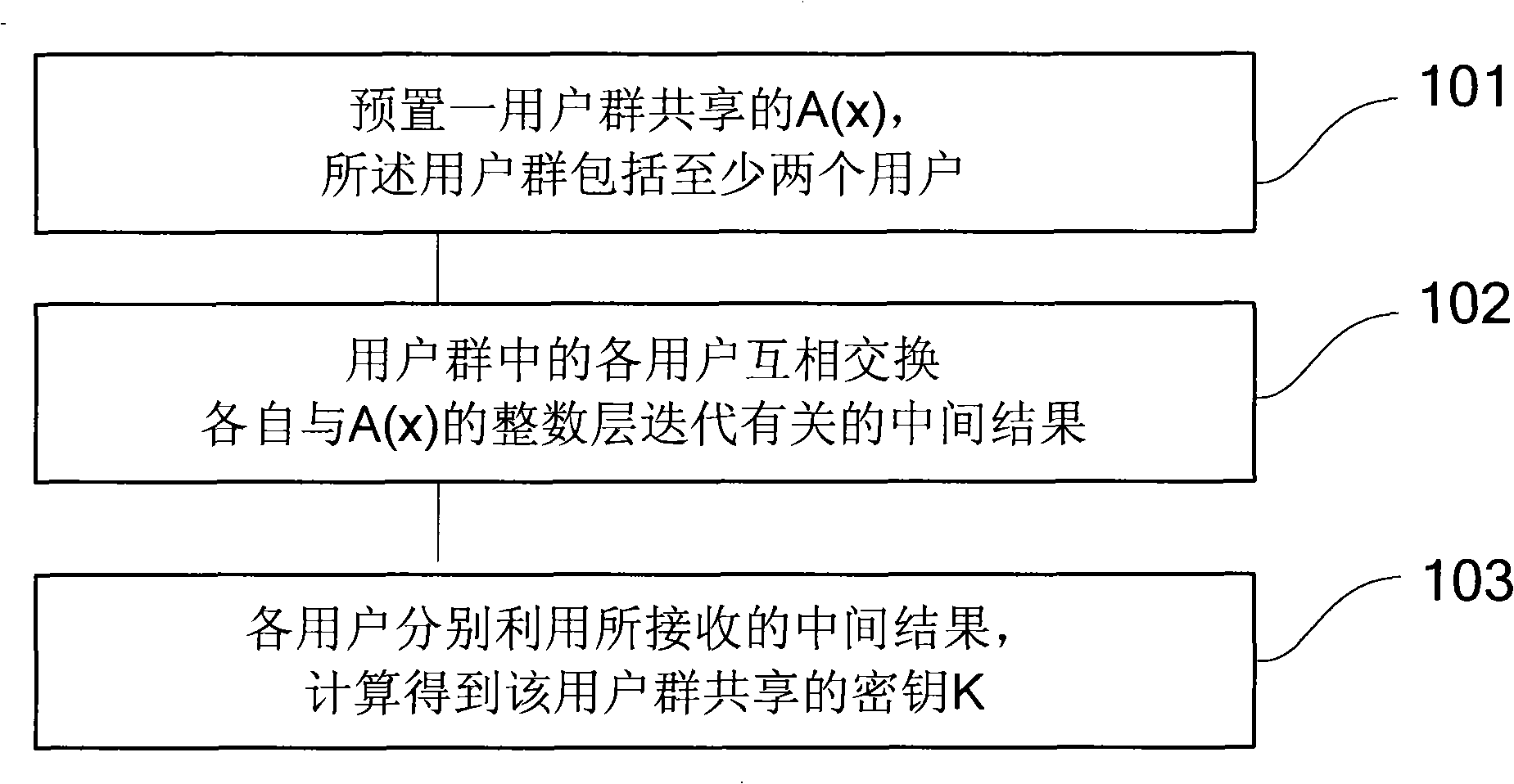
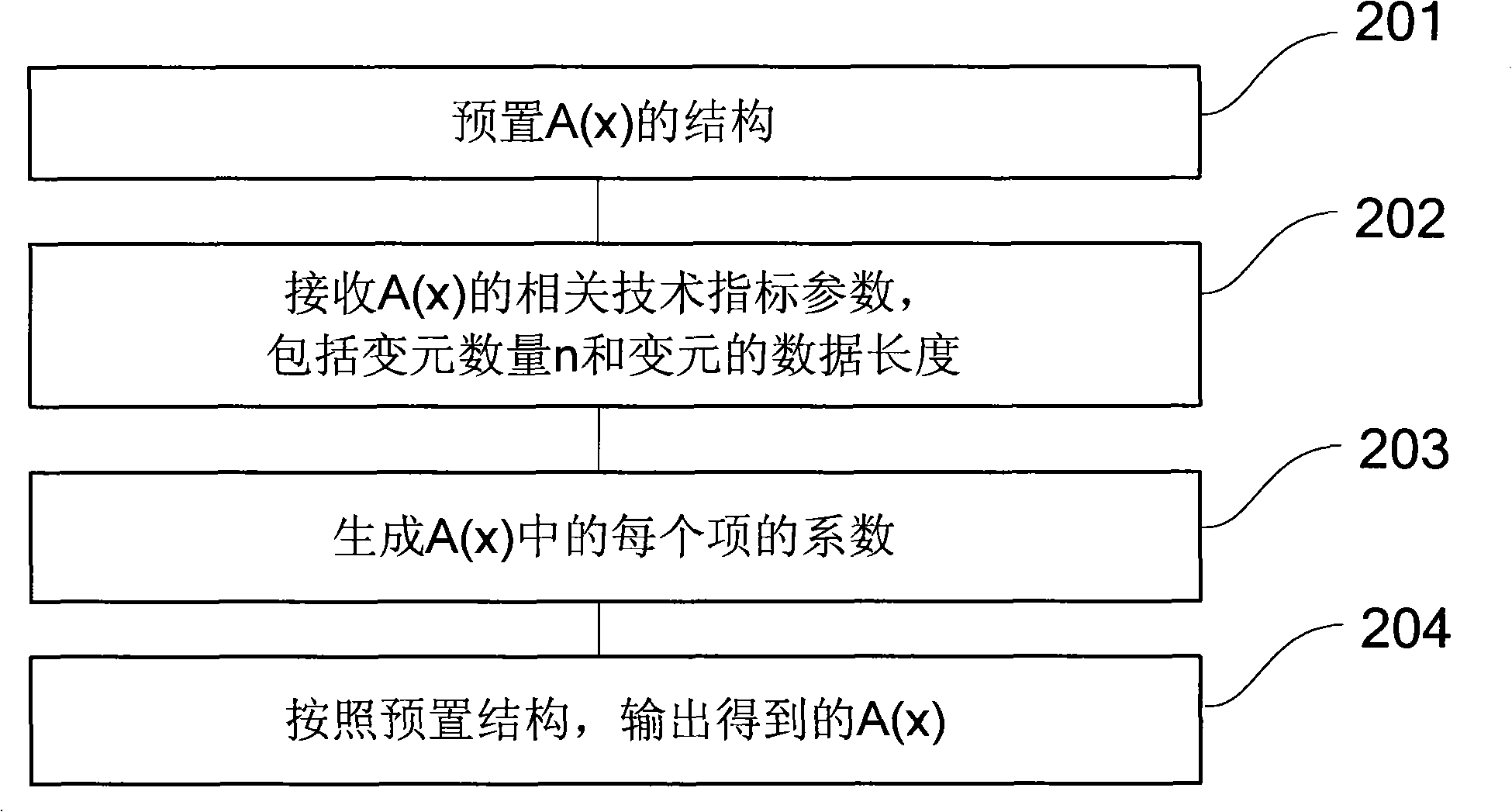
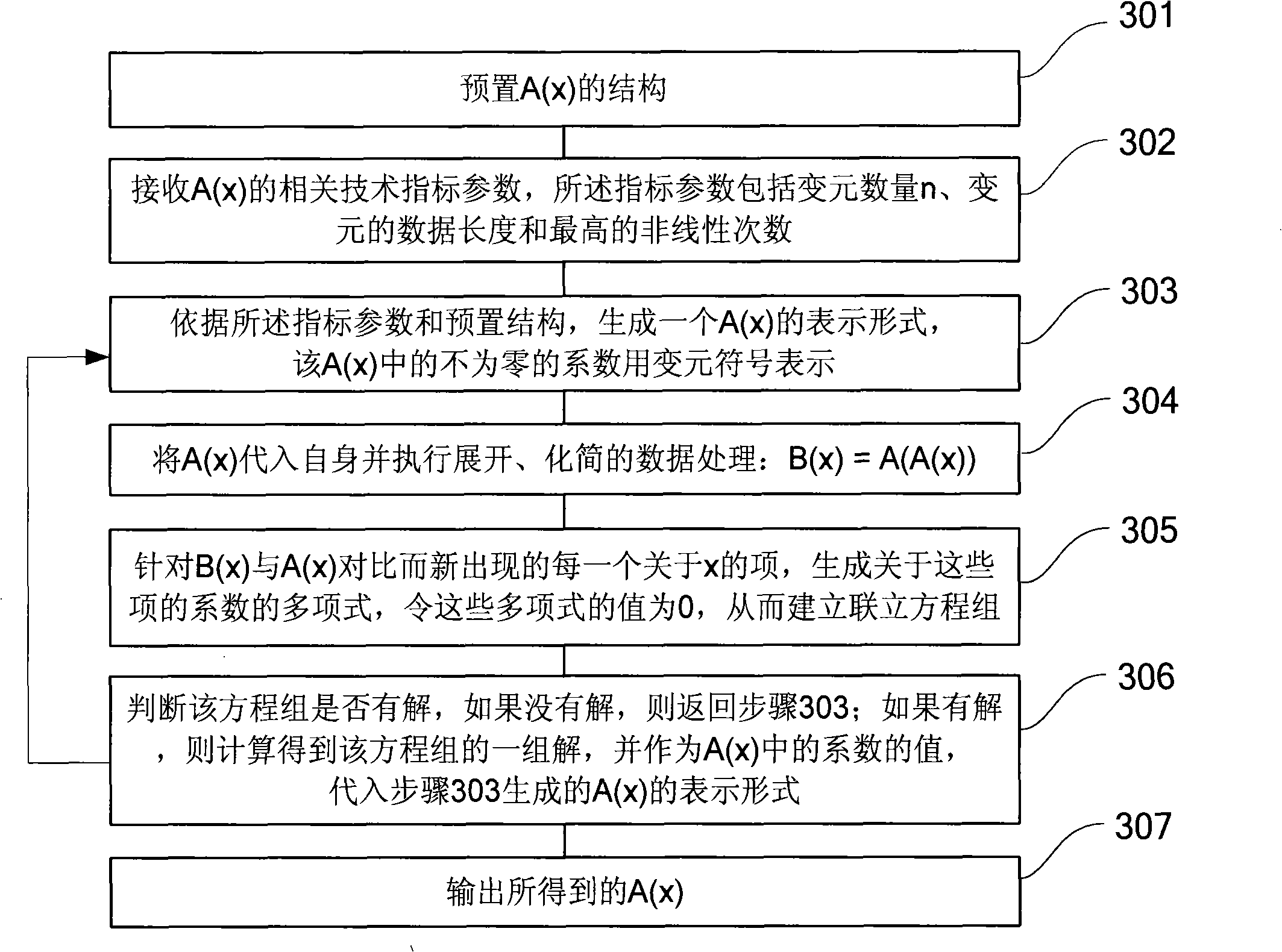
[0074] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0075] The present invention belongs to the category of information security products, and is mainly used in network trust systems, such as certificates, banks, mobile phones, Internet, e-commerce, e-government, logistics, network monitoring, power control, fund transfer, transactions, data encryption and other links.
[0076] The hardware environment required for applying the present invention belongs to the knowledge well known to those skilled in the art. For example: computers, network devices, handheld or portable devices, programmable consumer electronics devices, smart cards, microcontrollers, dedicated digital signal processing chips, multiprocessor systems, distributed computing environments including any of the above syst...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com