Data security protection method and device
A technology of data security and protection device, applied in the field of storage security, can solve problems such as the inability to judge whether the storage device is in a legal use state, the storage device not providing the self-destruction function, and the brute force cracking.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
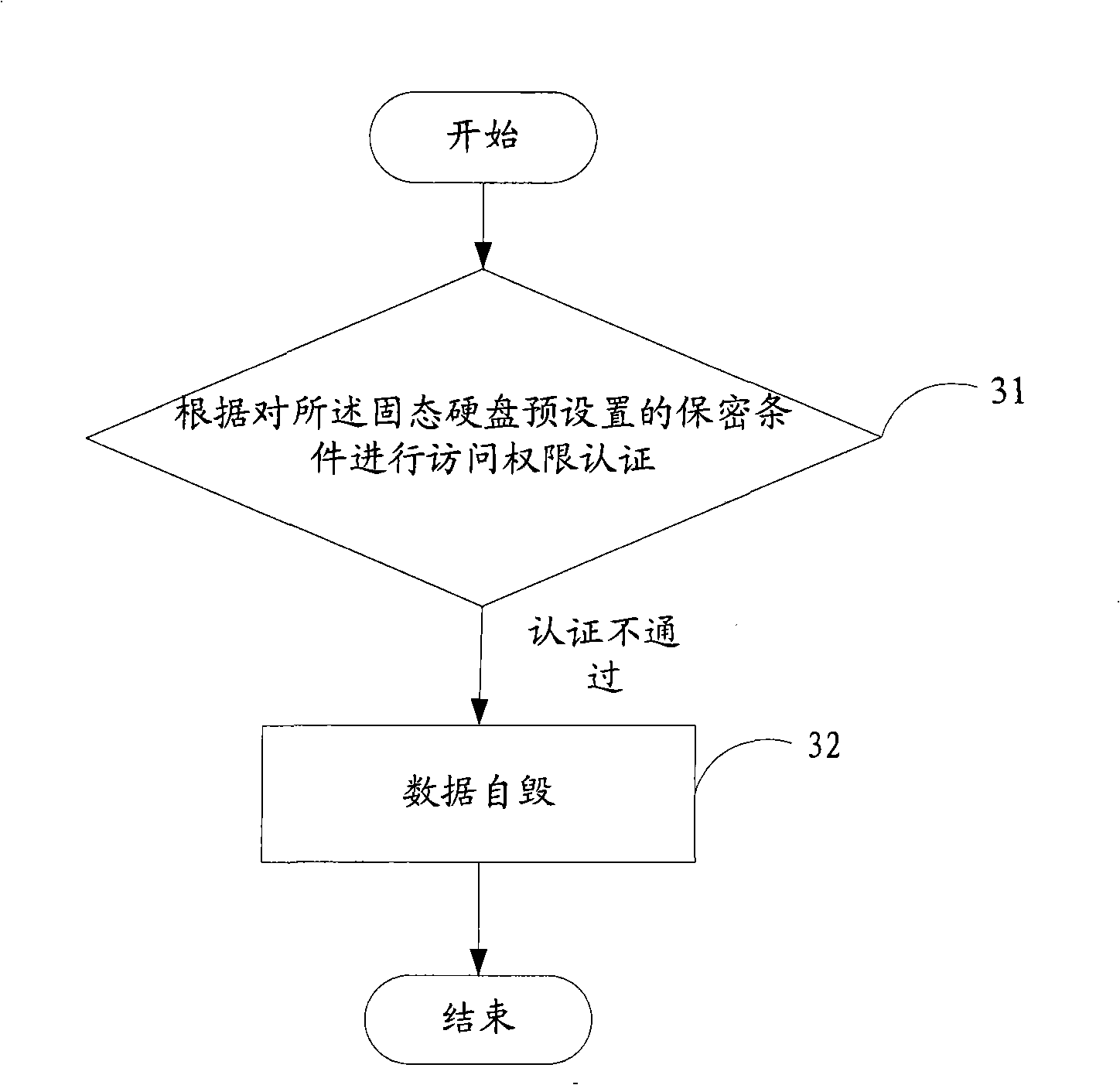
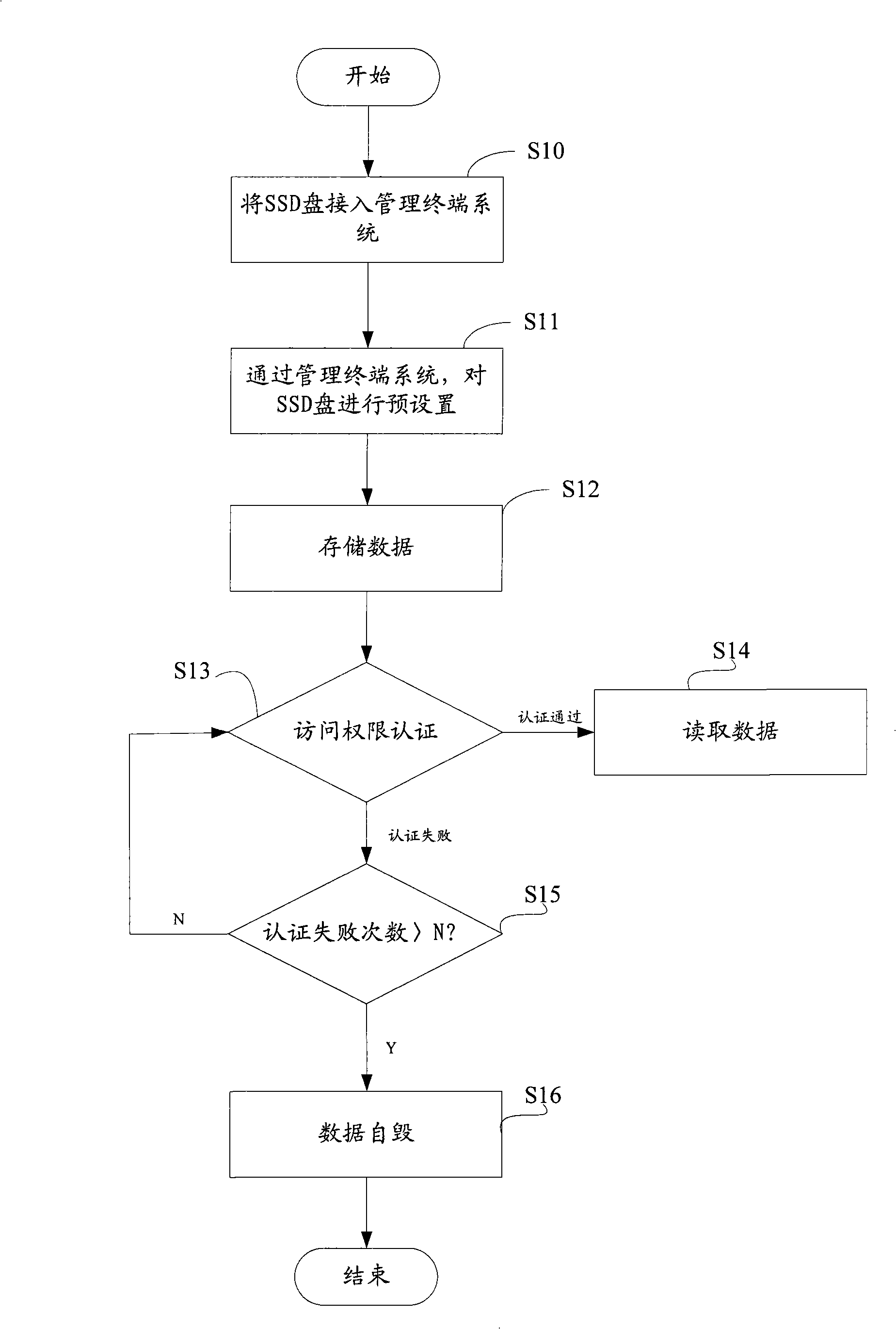
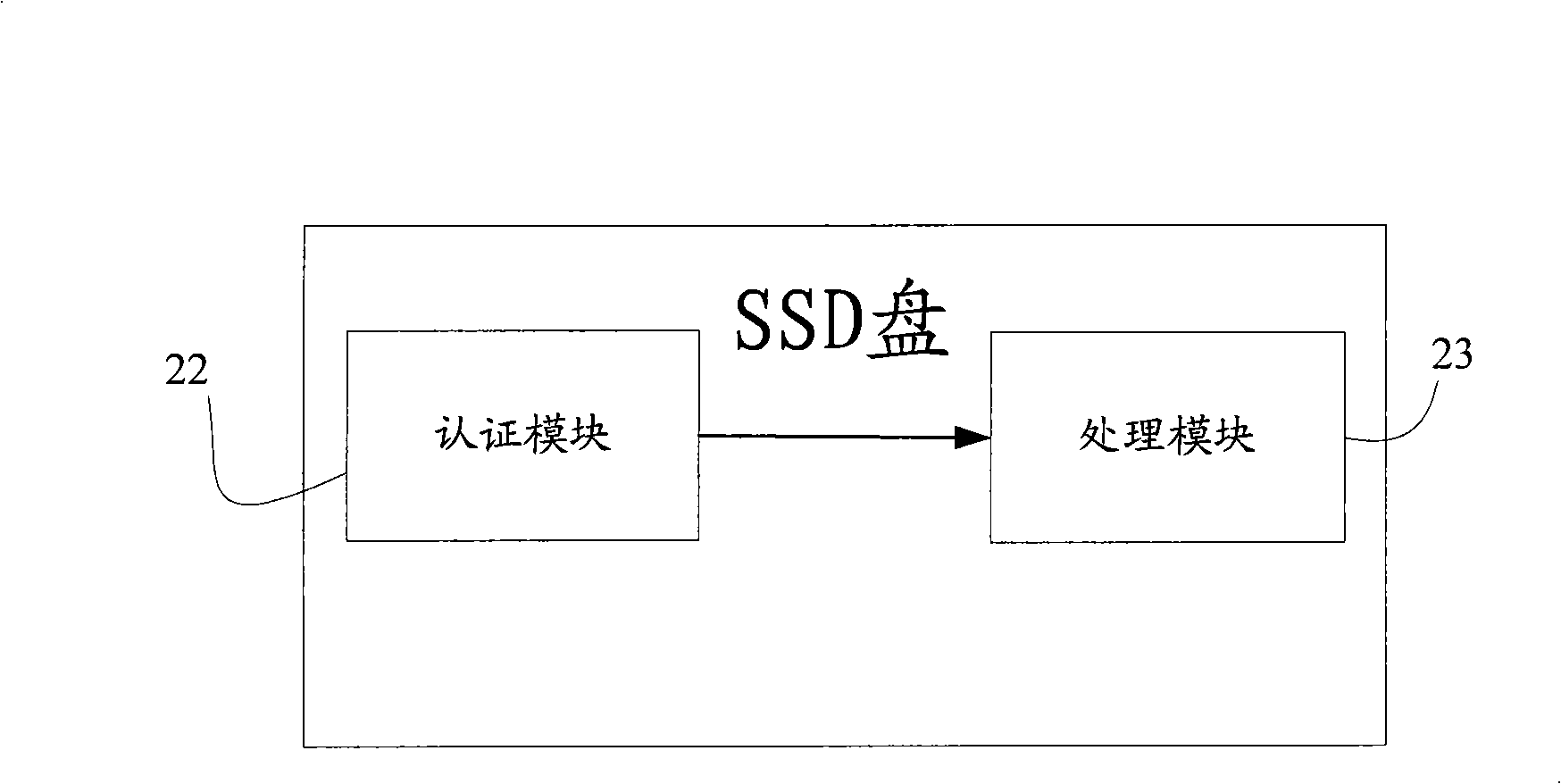
[0031] One is that the authentication can be performed by the IP address segment or MAC address segment of the computer that is allowed to access the SSD preset in step S11, and the application system will request the IP address segment or MAC address segment of the computer that uses the SSD to establish with step S11 If the IP address or MAC address of the computer is in the address database, it means that the SSD is allowed to be used by the computer, and the authentication is successful, and then proceed to step S14, otherwise it means that the SSD is not allowed to be used by the computer , the authentication was unsuccessful.
[0032] The other is to ask the computer user who requests to use the SSD to input the user name and password. If the user name and password match, the authentication is successful and step S14 is performed, otherwise the authentication is unsuccessful.
[0033] The other is to compare and search the fingerprint information of the computer user req...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com