Method for deleting in-service virus
A technology of virus files and anti-virus software, which is applied in the direction of instruments, electronic digital data processing, and platform integrity maintenance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
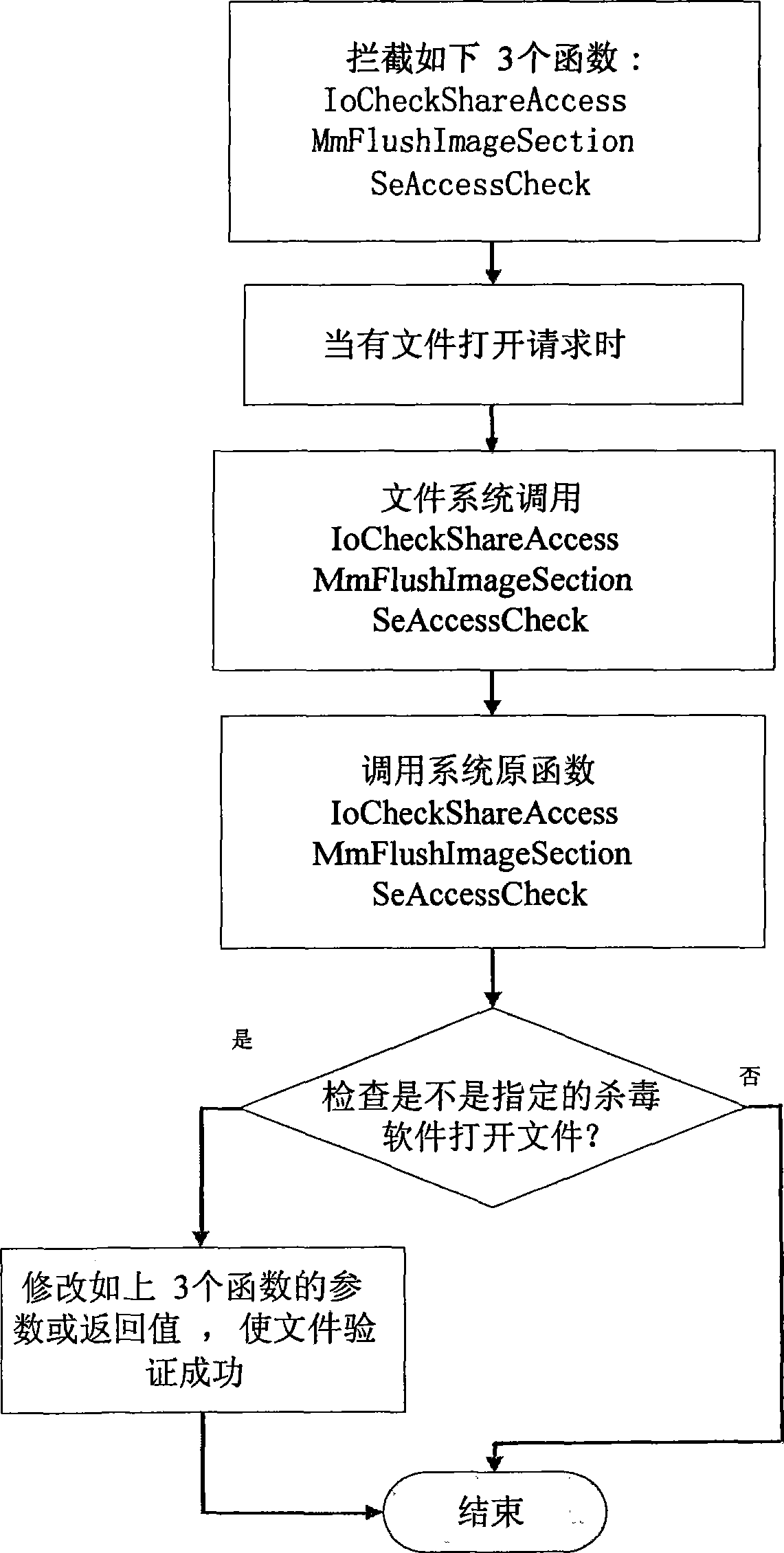
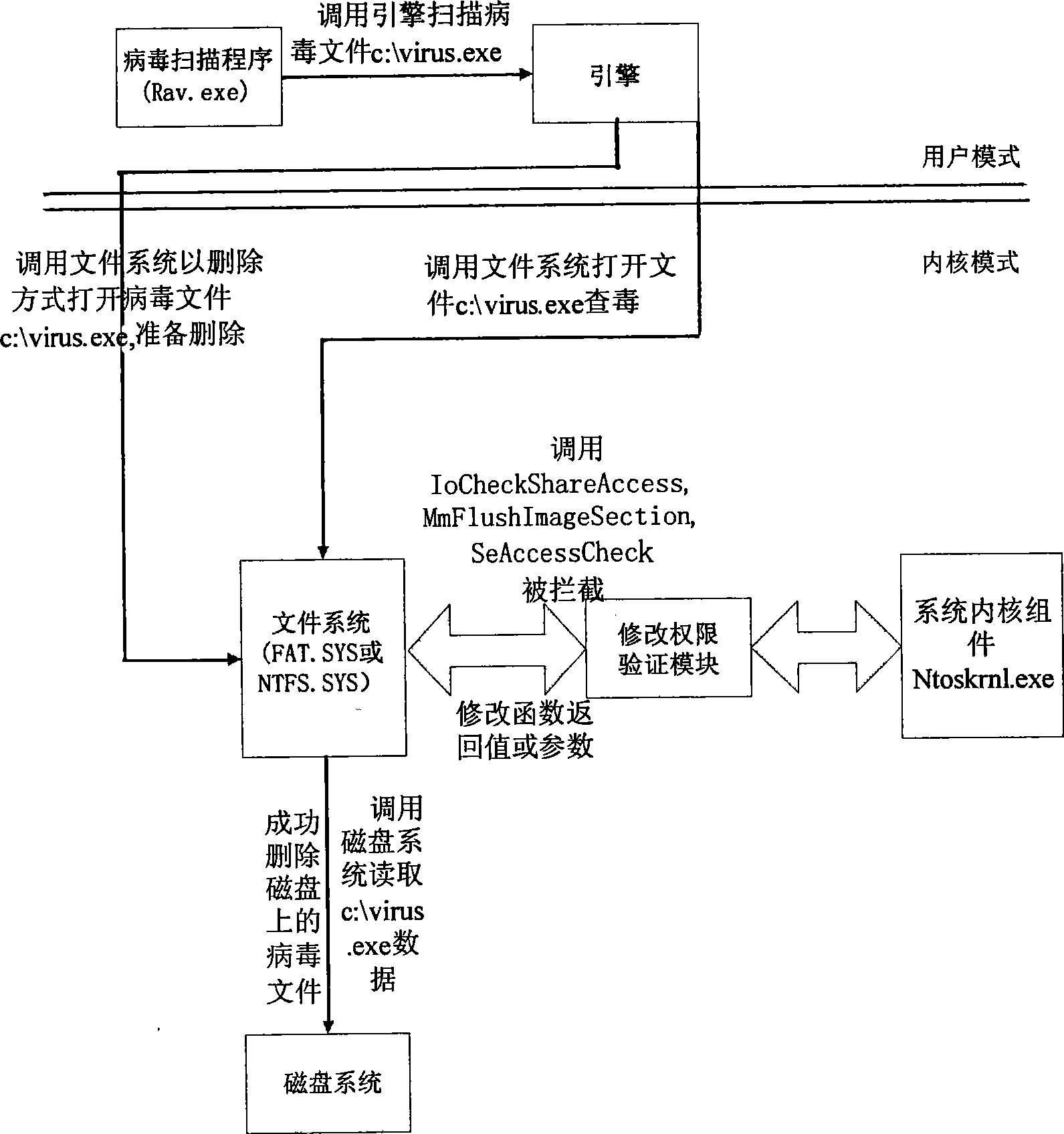
[0019] figure 1 and figure 2 A preferred embodiment of the invention is shown. Refer to the following figure 1 and figure 2 , describing the process of deleting the running virus file in this embodiment.
[0020] (1) First intercept the following three functions:
[0021] IoCheckShareAccess, MmFlushImageSection, SeAccessCheck
[0022] When the file is opened, the file system will verify the permission of the file opening request, and only those who pass the permission verification can open the file.
[0023] When a file is opened for the first time, the Windows NT system will call the two functions of IoSetShareAccess and IoUpdateShareAccess of its kernel to set the initial permissions of the file. specific description of . These two functions are mainly used to set the share permission and update permission of the file when the file is opened.
[0024] When the file is opened again, the system will call three functions, IoCheckShareAccess, MmFlushImageSection, and S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com