Macro network security status assessment method based on exception measurement
A network security and status assessment technology, applied in the field of information security, can solve problems that are difficult to evaluate the daily operation status of the macro network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
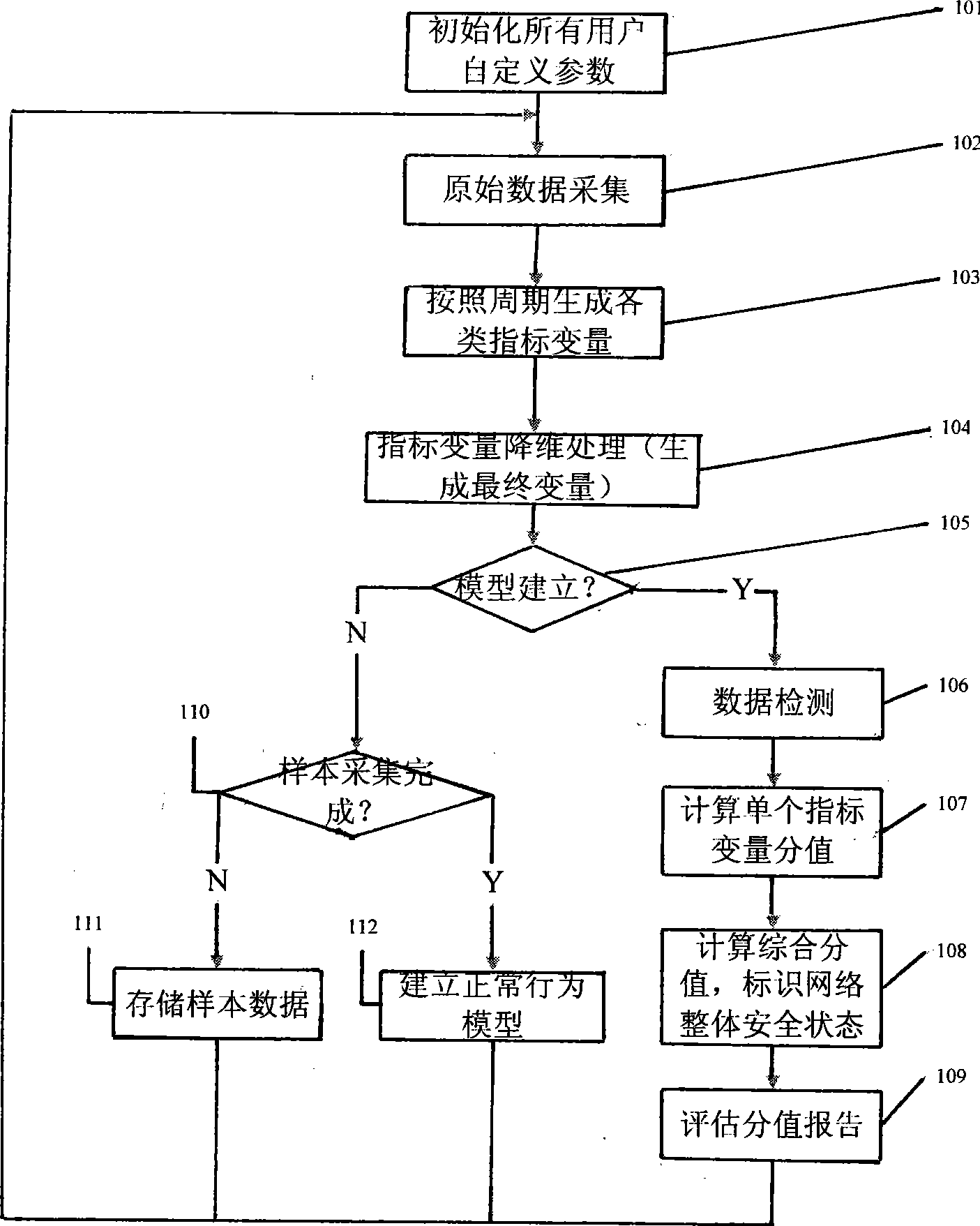
[0046] The security status evaluation method proposed by the present invention is mainly applied in the macroscopic network environment. The specific process of the evaluation process is as follows: figure 1 shown.
[0047] In order to make those skilled in the art understand the present invention better, below in conjunction with figure 1 The flow chart shown is a further detailed description of the present invention. Include the following steps:
[0048] Step 101: Initialize all user-defined parameters, specifically including:
[0049] Configurable information used by the data modeling process:
[0050] Number of sample lines: the number of continuous samples taken from the sampling point;
[0051] Number of sample columns: the dimensionality of the sample vector data itself;
[0052] Normal data fluctuation range: one of the basis for extracting normal principal components;
[0053] Contribution rate: the second basis for extracting normal principal components;
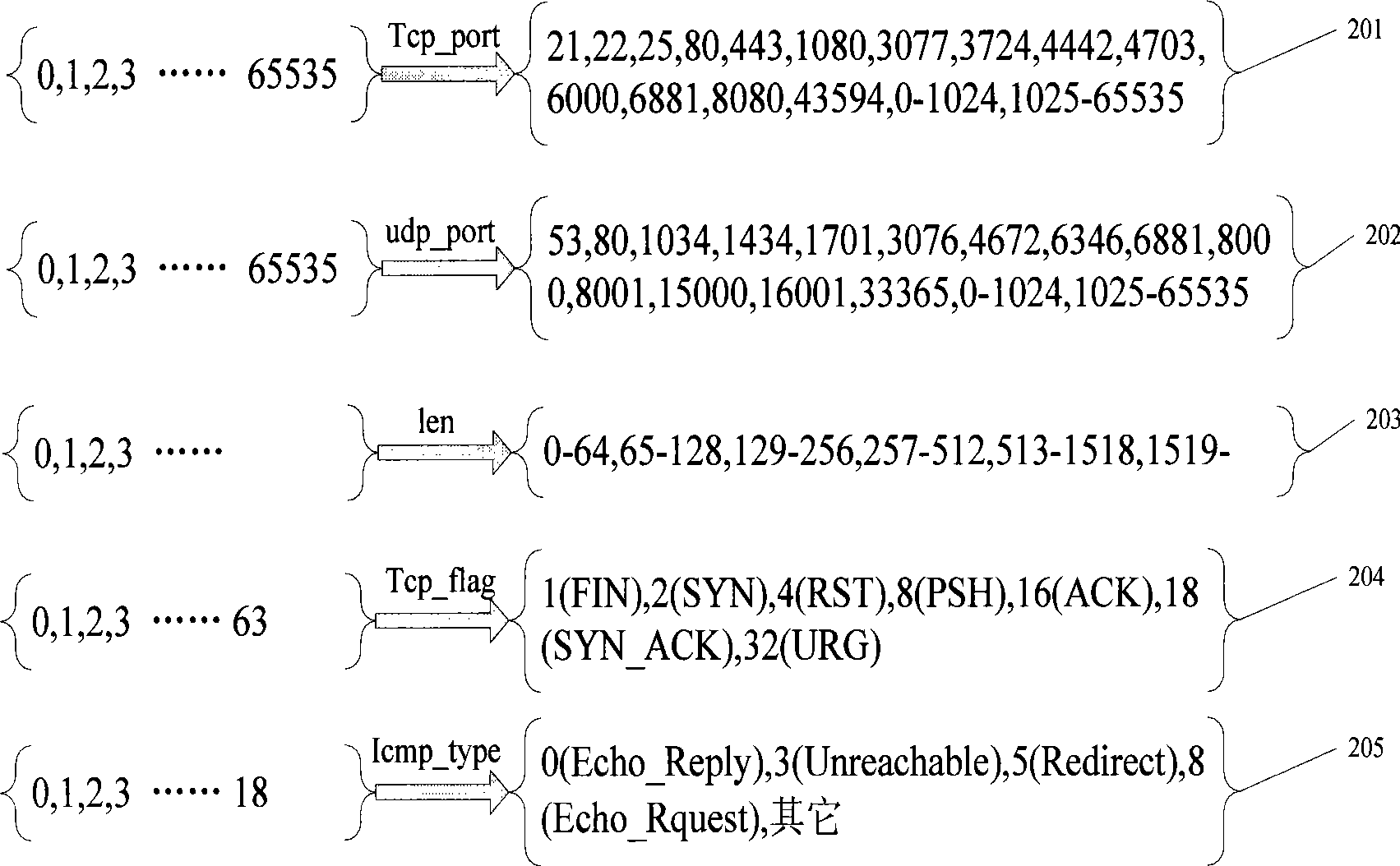
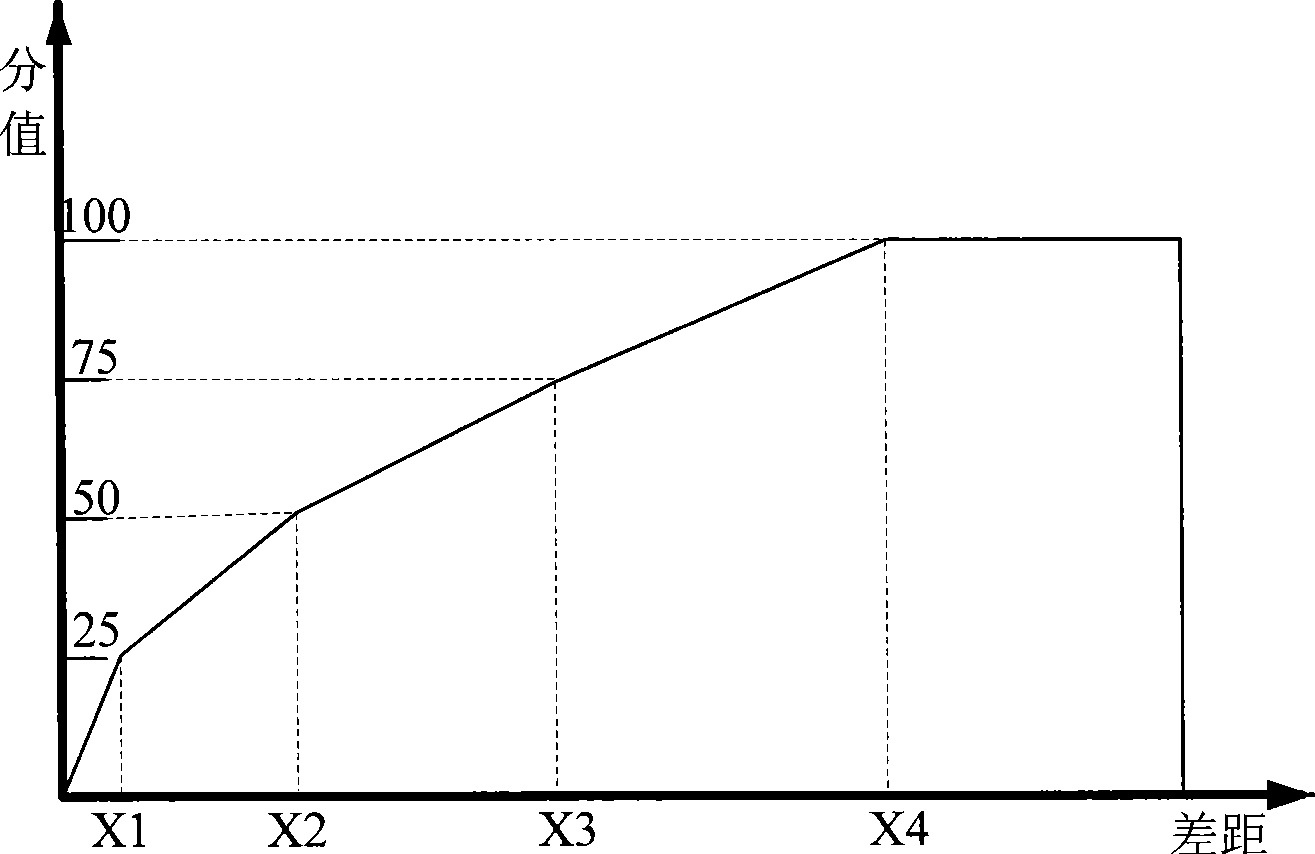
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com