Collision-resistance method for mapping public-private key pairs by utilizing uniform user identification
A technology of user identification and public-private key pairs, applied in the field of communication network cryptography, can solve problems affecting public-private key pairs, collisions, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
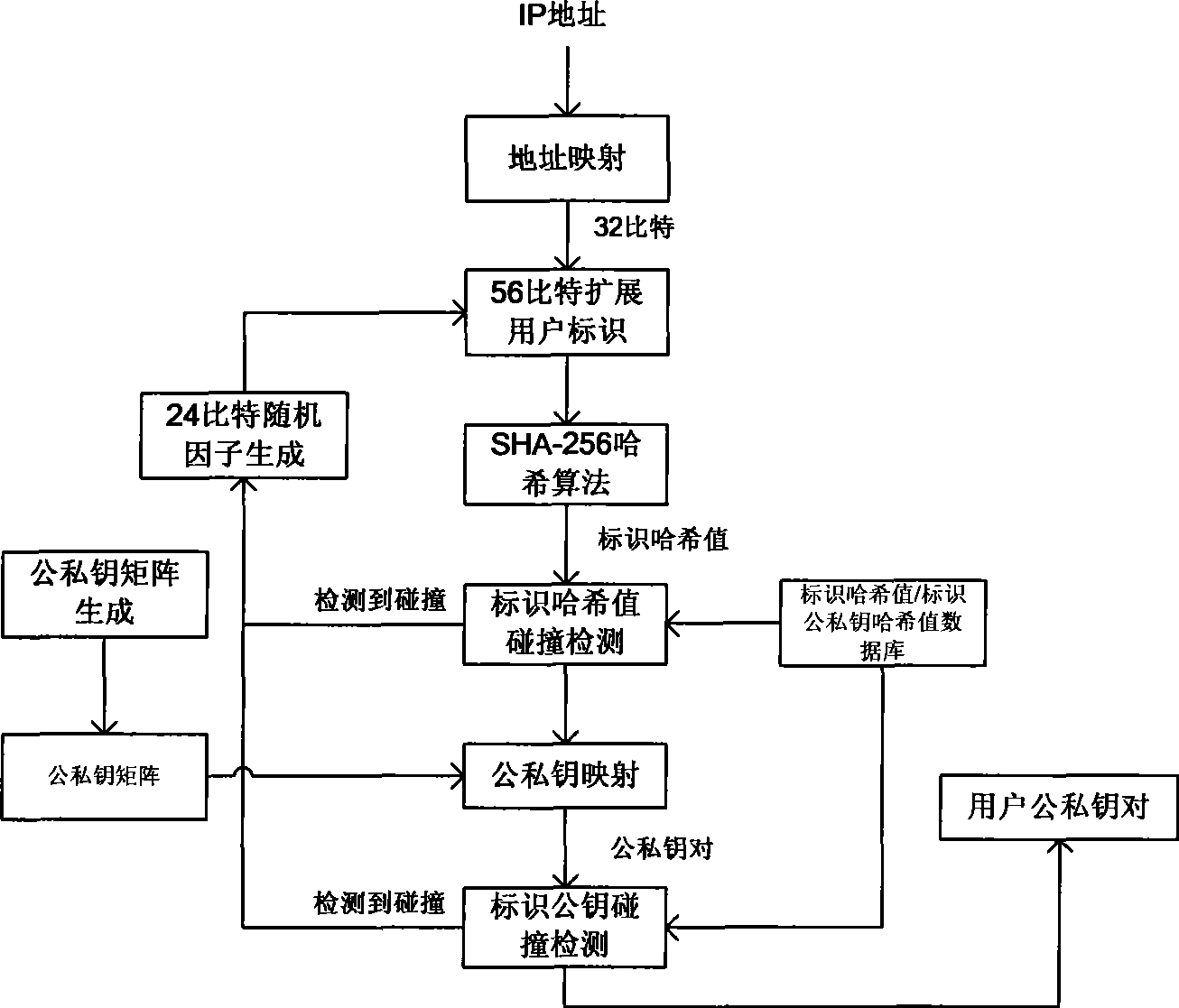
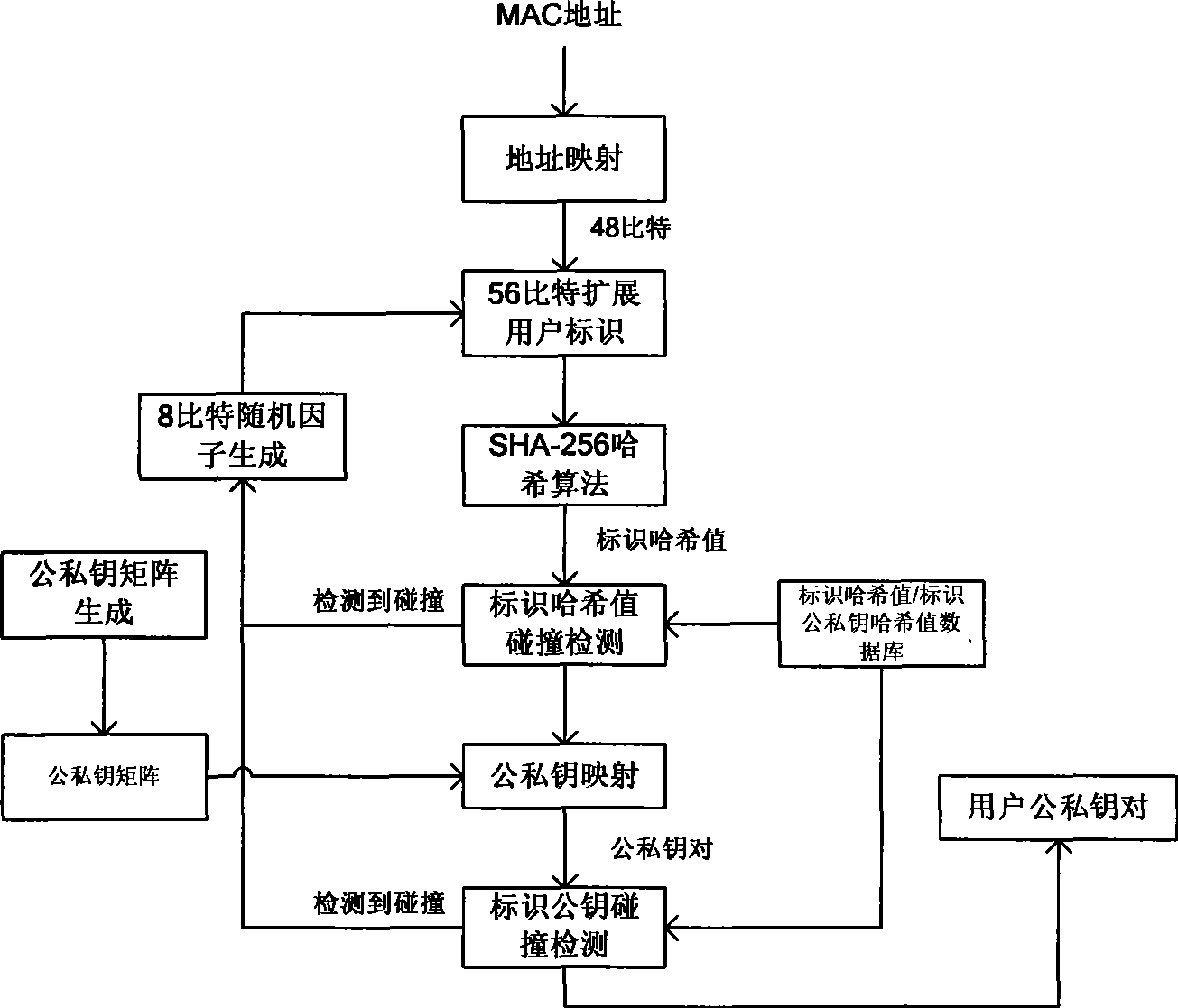
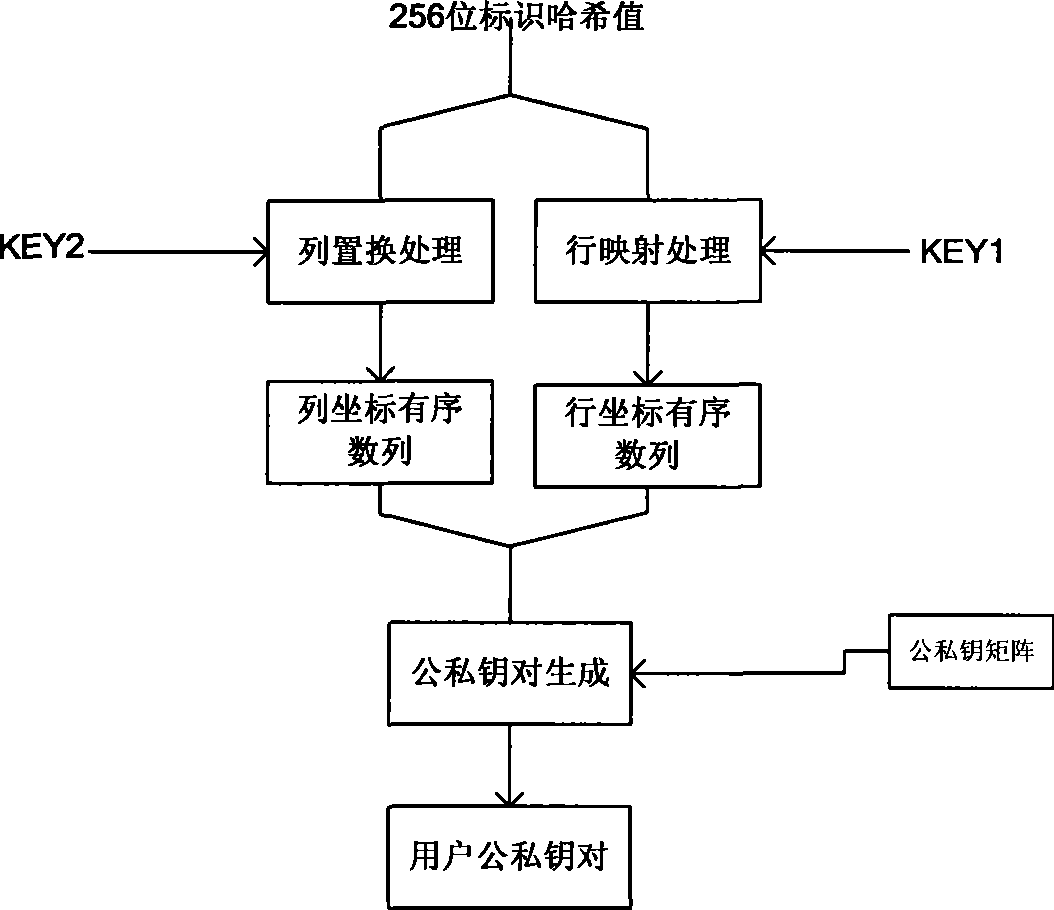
[0021] refer to Figure 1 to Figure 3 . figure 1 It is a principle working program diagram of an embodiment of IP address identification public-private key mapping in the present invention, figure 2 It is a principle working program diagram of an embodiment of MAC address identifier public-private key mapping in the present invention. In the present invention, the whole process of mapping from address to extended user ID, implementation of random factor mechanism, cyclic hash collision detection, public-private key mapping, identification public-private key collision detection, and final user public-private key pair generation is as follows: figure 1 , figure 2 shown. The present invention comprises steps:
[0022] ① Select the scale of the public-private key matrix according to the user scale, and the selection condition is that the matrix of m rows × h columns satisfies m h The public and private key generation requirements of each user; according to the scale of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com