Methods and systems for securing a computer network
A network and proprietary network technology, applied in the field of computer networks, can solve the problem of uncertainty in the reliability of user authentication wirelessly connected to the network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
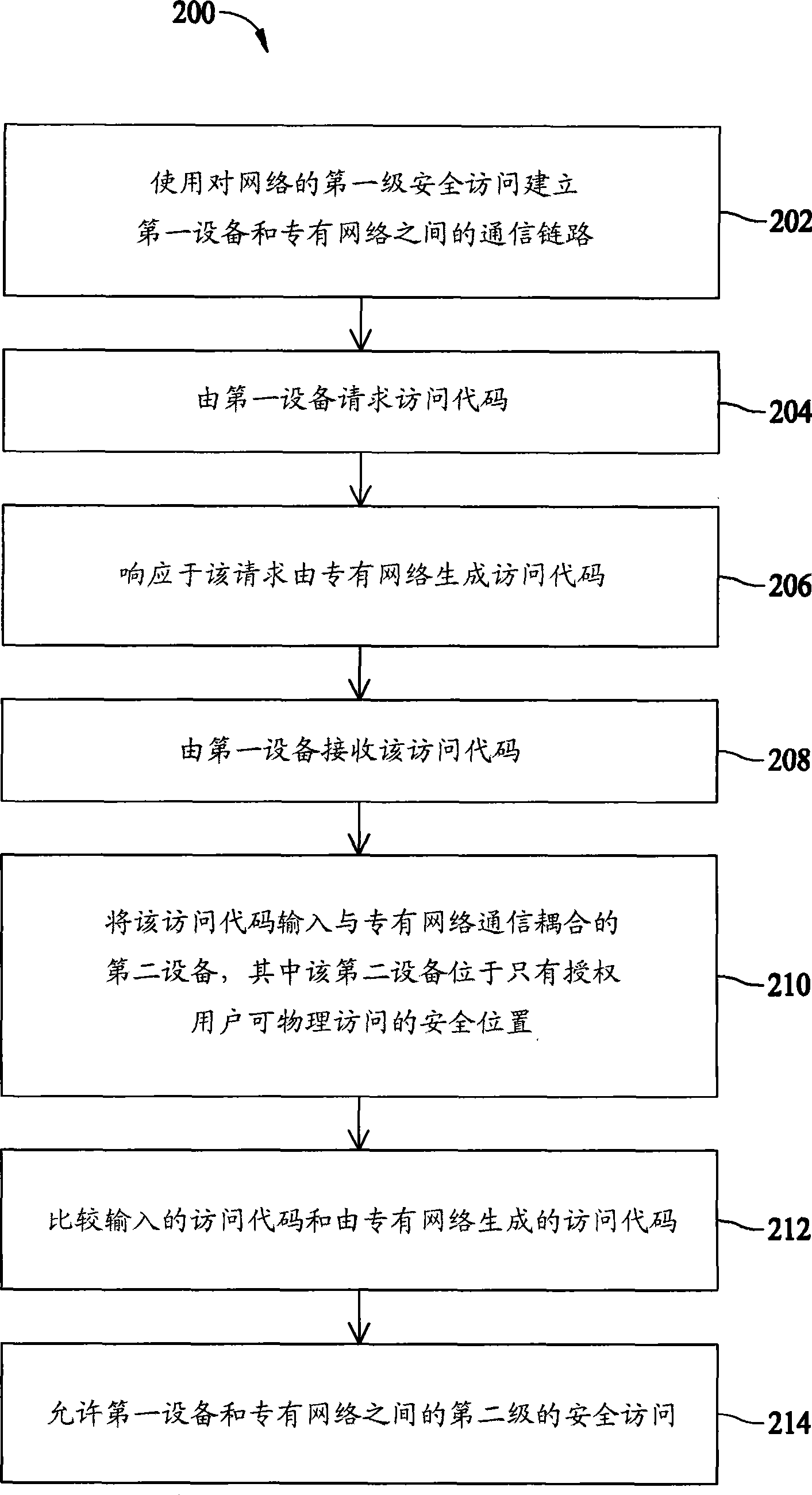
Method used
Image
Examples
Embodiment Construction
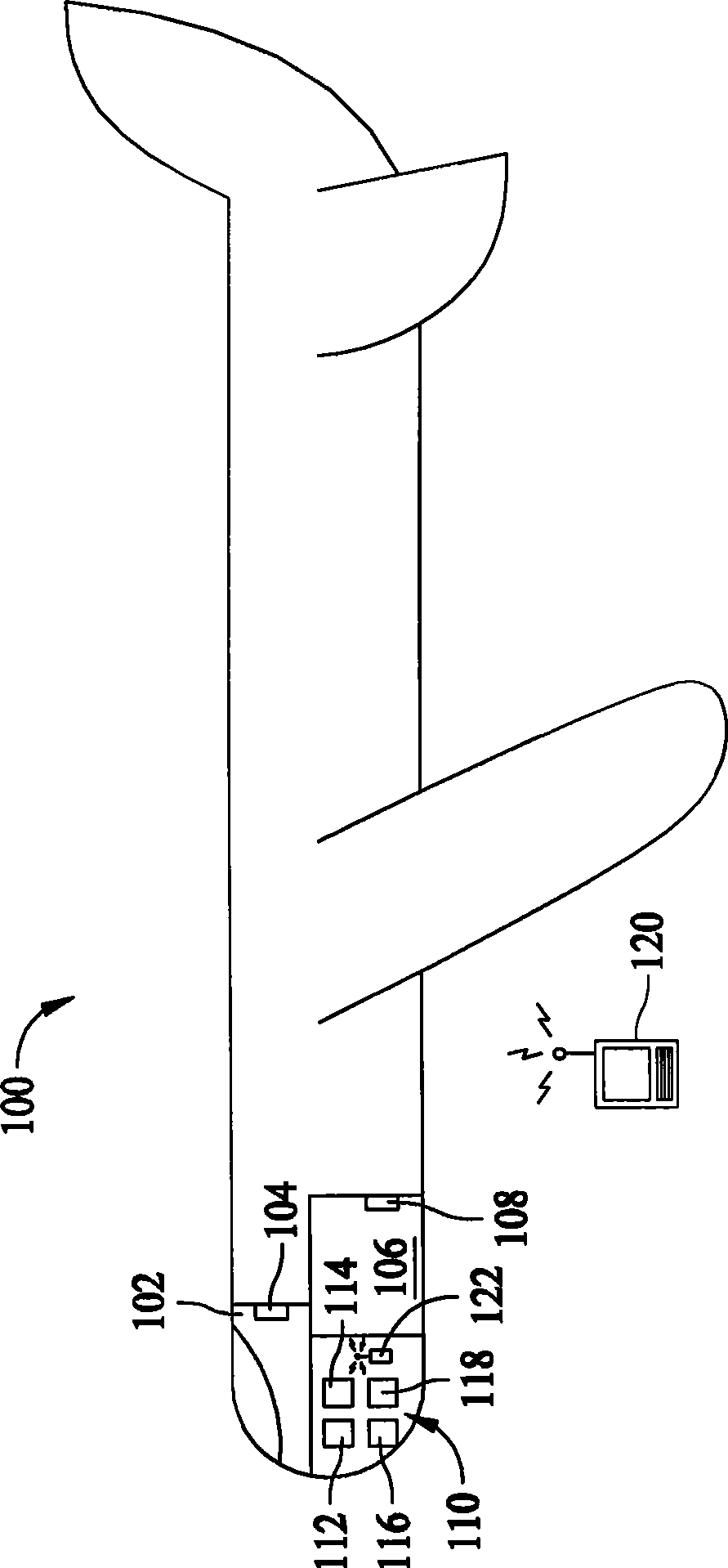
[0008] figure 1 is a side cross-sectional view of an aircraft 100 according to an embodiment of the invention. Aircraft 100 includes a cockpit 102 from which aircraft 100 is operated and controlled. Cockpit 102 is a secure access area onboard aircraft 100 . For example, an access procedure is required before access to the cockpit 102 is permitted. The cockpit 102 includes an input device 104 . Aircraft 100 also includes an electronics bay 106 onboard aircraft 100 , which is a secure access area onboard aircraft 100 . The electronic pod 106 also includes an input device 108 .
[0009] Aircraft 100 includes a computer network, such as aircraft data network (ADN) 100 . In an exemplary embodiment, AND 110 includes four domains with different levels of security access requests. AND 110 includes aircraft control domain 112 , airline information services domain 114 , passenger information and entertainment services domain 116 , and passenger-owned equipment domain 118 . Aircra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com