Net locking method and system
A network-locking, one-pair technology, applied in network data management, electrical components, security devices, etc., can solve the problem of inability to dynamically modify locking parameters, and achieve the effect of reducing operating costs and enhancing security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
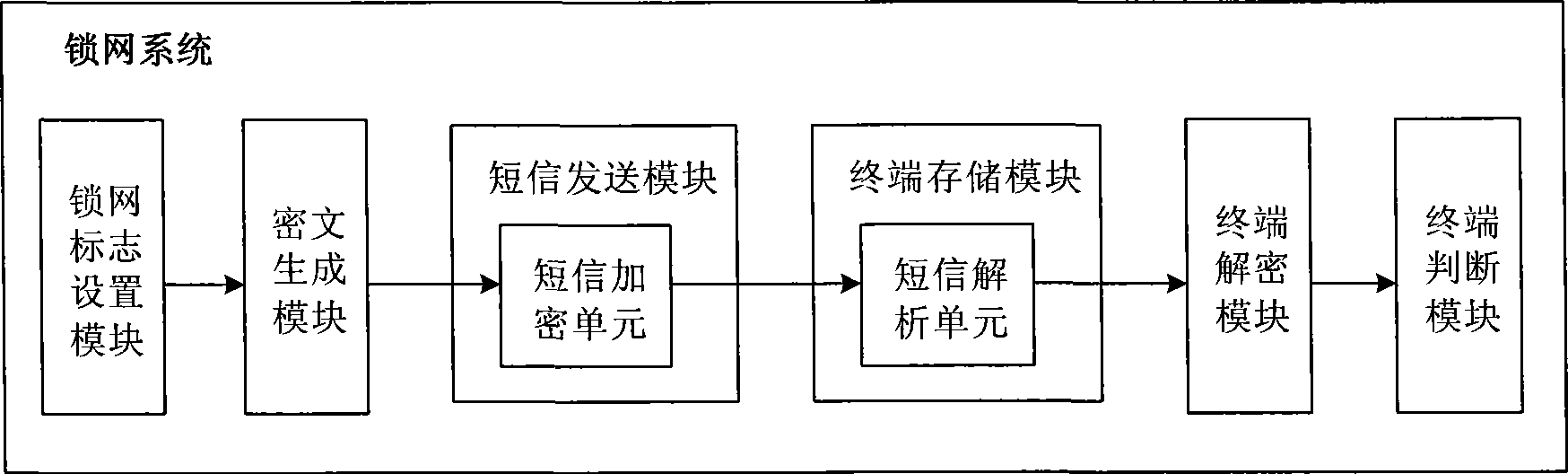
Image
Examples
Embodiment Construction
[0030] The following describes in detail the technical solutions of the network locking method and system of the present invention in conjunction with the accompanying drawings and specific embodiments:
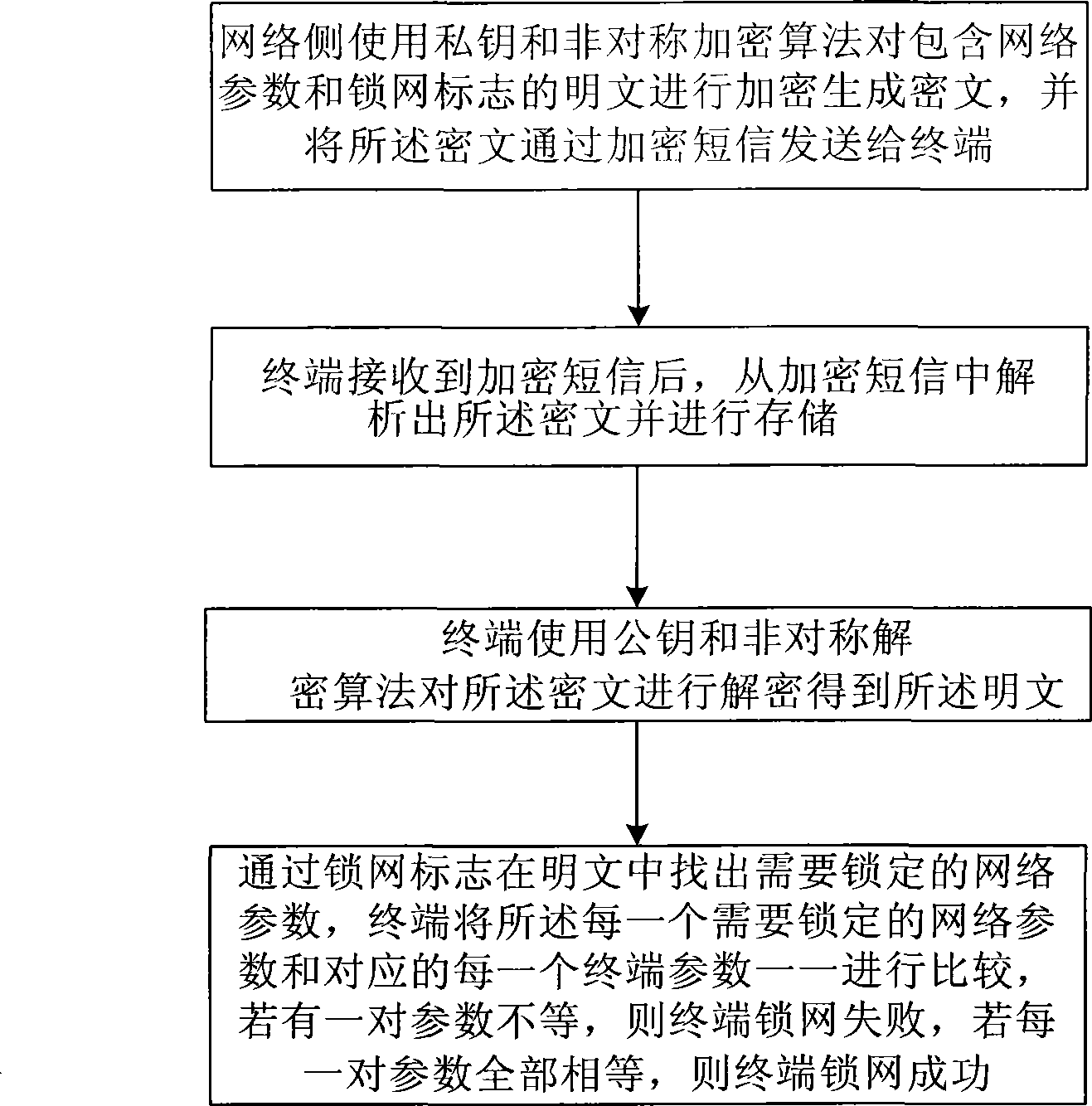
[0031] figure 1 It is a flow chart of the network locking method of the present invention, and the following are the concrete steps of locking the network:
[0032] Step 1: The network side uses a private key and an asymmetric encryption algorithm to encrypt the plaintext containing the network parameters and the network lock flag to generate a ciphertext, and sends the ciphertext to the terminal through an encrypted message;
[0033] The plaintext M includes: a network parameter P and a network lock flag F,
[0034] The network parameter P is a collection of some network parameters, which includes P1, P2, P3, ... PN, and common network parameters are MCC (Mobile Country Code), MNC (Mobile Network Code), and MIN2 (Mobile Station Identification);
[0035] The network lock fl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com