Method for secretly writing and extracting secret information of compressed digital audio
A technology for secret information and digital audio, which is applied in the field of steganography and extraction of secret information, and can solve problems such as the inability to effectively guarantee the security of digital steganography, changes, and capacity limitations of steganography.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
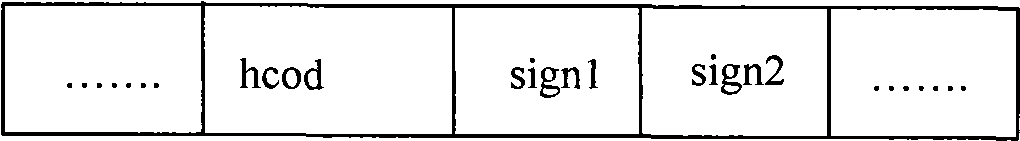
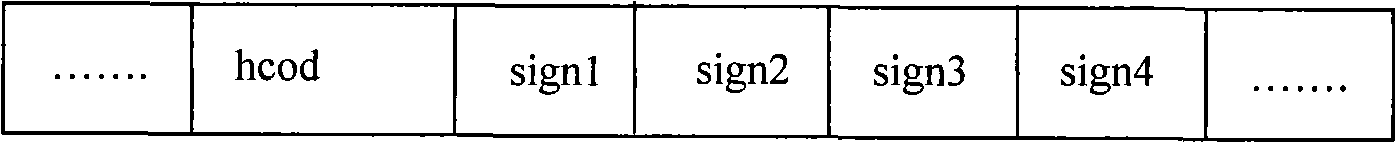
[0030]Embodiment one: a kind of steganographic method for compressing secret information in digital audio, the object that this steganographic method handles is the audio code stream of a compressed digital audio, and this audio code stream mainly adopts MPEG standard to compress, but this Steganographic methods are not limited to audio streams, nor are they limited to a particular compression standard. The MPEG encoder adopts Huffman coding, so the audio code stream is expressed as a Huffman codeword, also known as a variable length codeword VLC (VariableLength Coding). The MPEG encoder provides 34 available Huffman code tables with a total of 4995 codewords.
[0031] Because the variable-length code word in the Huffman code table is divided into a large value area, a small value area and a zero area according to the MDCT (Modified Discrete Cosine Transform, modified discrete cosine transform) coefficient after quantization, wherein for the large value area , every two MDCT ...
Embodiment 2
[0053] Embodiment 2: A method for extracting the secret information in the above-mentioned compressed digital audio, the object processed by this extraction method is a digital audio containing secret information, and the object processed in this specific embodiment is the embodiment Encrypted digital audio obtained in one. This extraction method comprises the following steps:
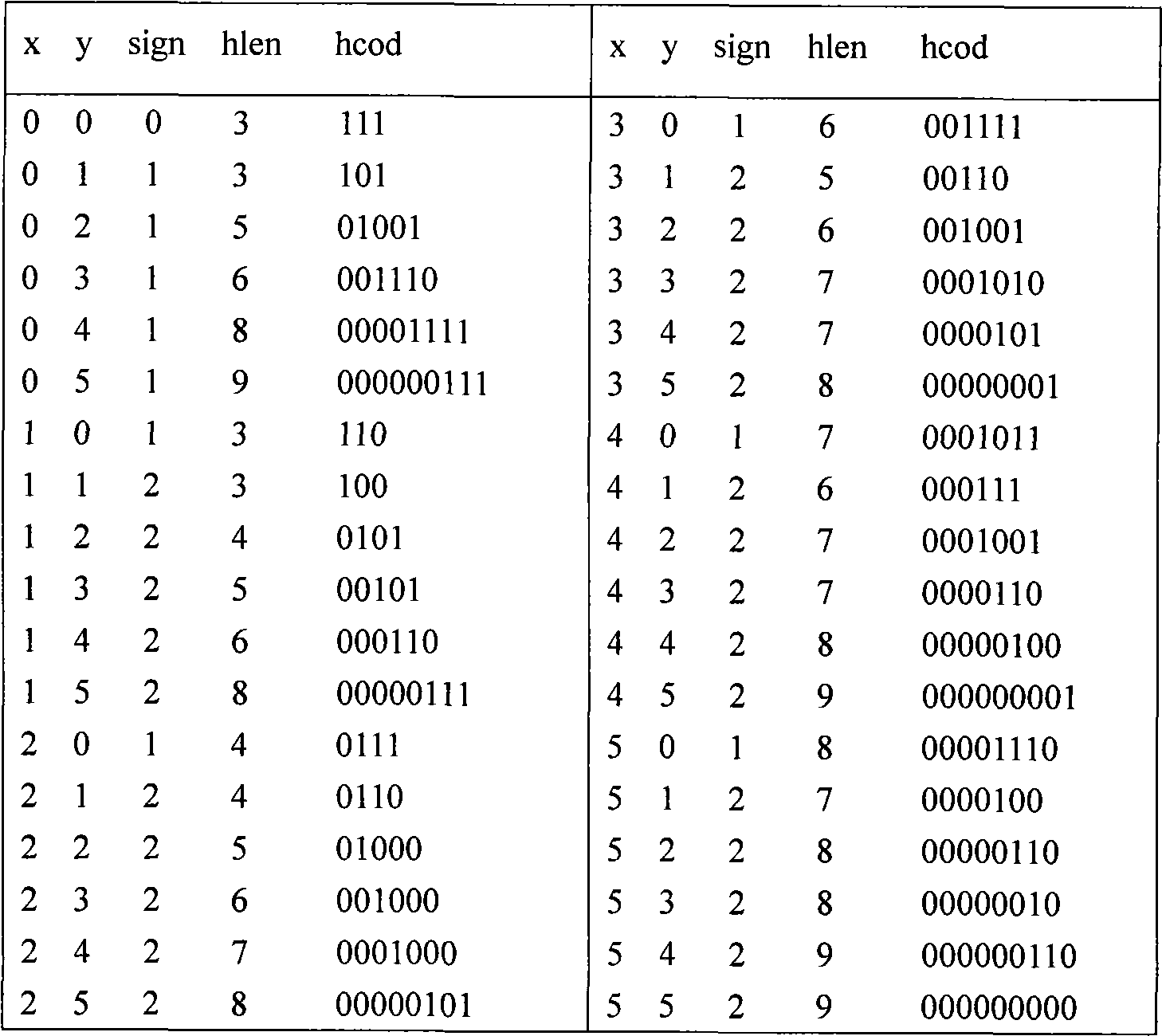
[0054] 1), before the secret information is steganographically written, it is necessary to classify all the codewords in the 34 available Huffman code tables given by the MPEG encoder, first divide each Huffman code table into an invalid codeword set and The effective codeword set, and then divide the effective codeword set into multiple subsets according to the codeword length and sign bit of each effective codeword in the effective codeword set, and the codeword length and sign bit of all valid codewords in each subset are the same , and then determine the basis of all effective codewords in the cor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com