Protection processing method and apparatus of software operation
A technology for protection processing and software, applied in the field of protection processing methods and devices for software operation, can solve the problems of inability to provide software protection processing methods and inconvenience in use, and achieve the effects of safe and convenient use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The technical solutions of the present invention will be further elaborated below in conjunction with the accompanying drawings and specific embodiments.
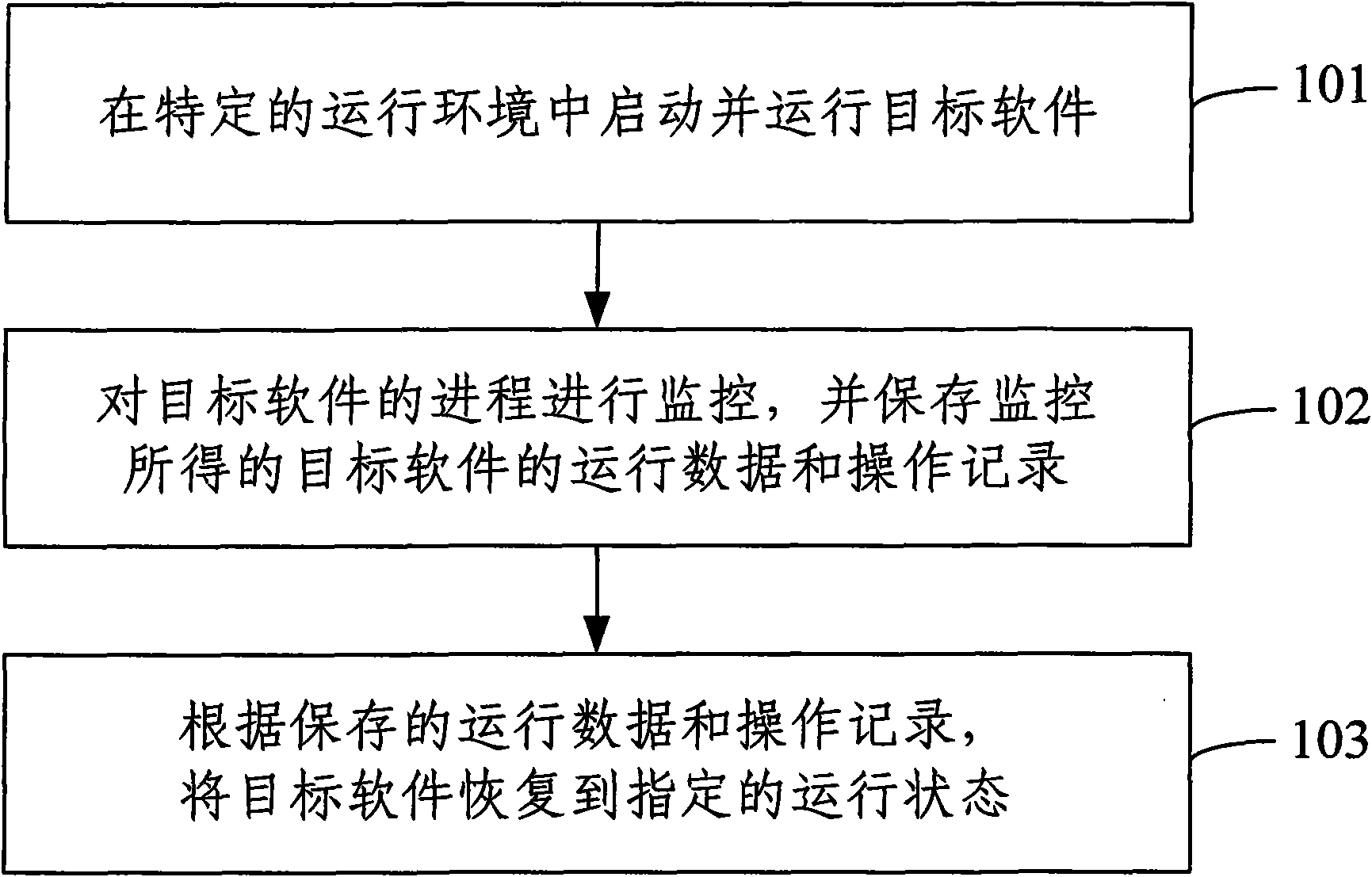
[0033] In order to prevent viruses and Trojan horses in software running from causing direct harm to the operating system, and to realize recordable, replayable, and controllable software during use, a method for protecting software running provided by the present invention is as follows: figure 1 As shown, it mainly includes the following steps:
[0034] Step 101, start and run the target software in a specific running environment.
[0035] The target software referred to in the present invention may be any software and application program that can run in the operating system. Before starting and running the target software, it is necessary to configure a specific operating environment for the target software. The present invention can fully encapsulate the application program interface (API, Application Programmin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com