Method and apparatus for scanning virus program
A virus program and scanning method technology, applied in computer security devices, instruments, electronic digital data processing, etc., can solve problems such as property infringement of network users, increase in data volume, and prolonging the time for virus program detection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
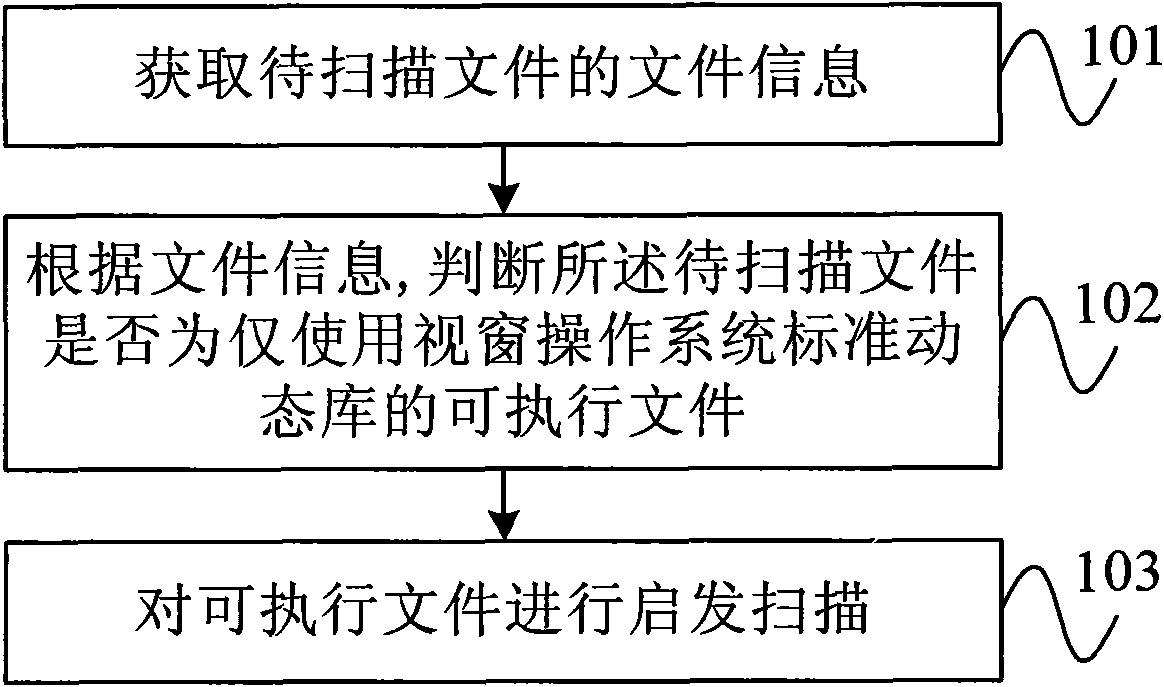
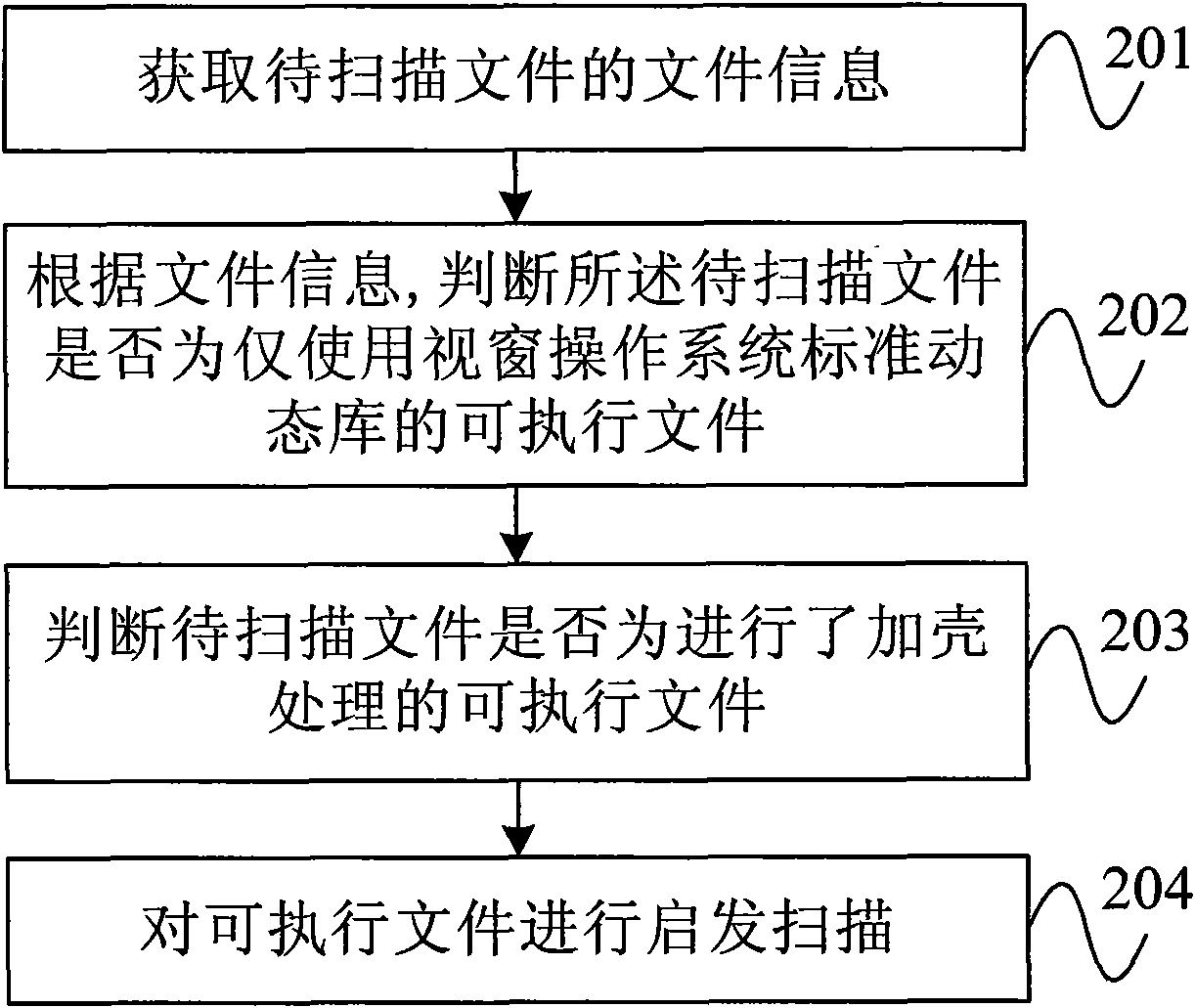
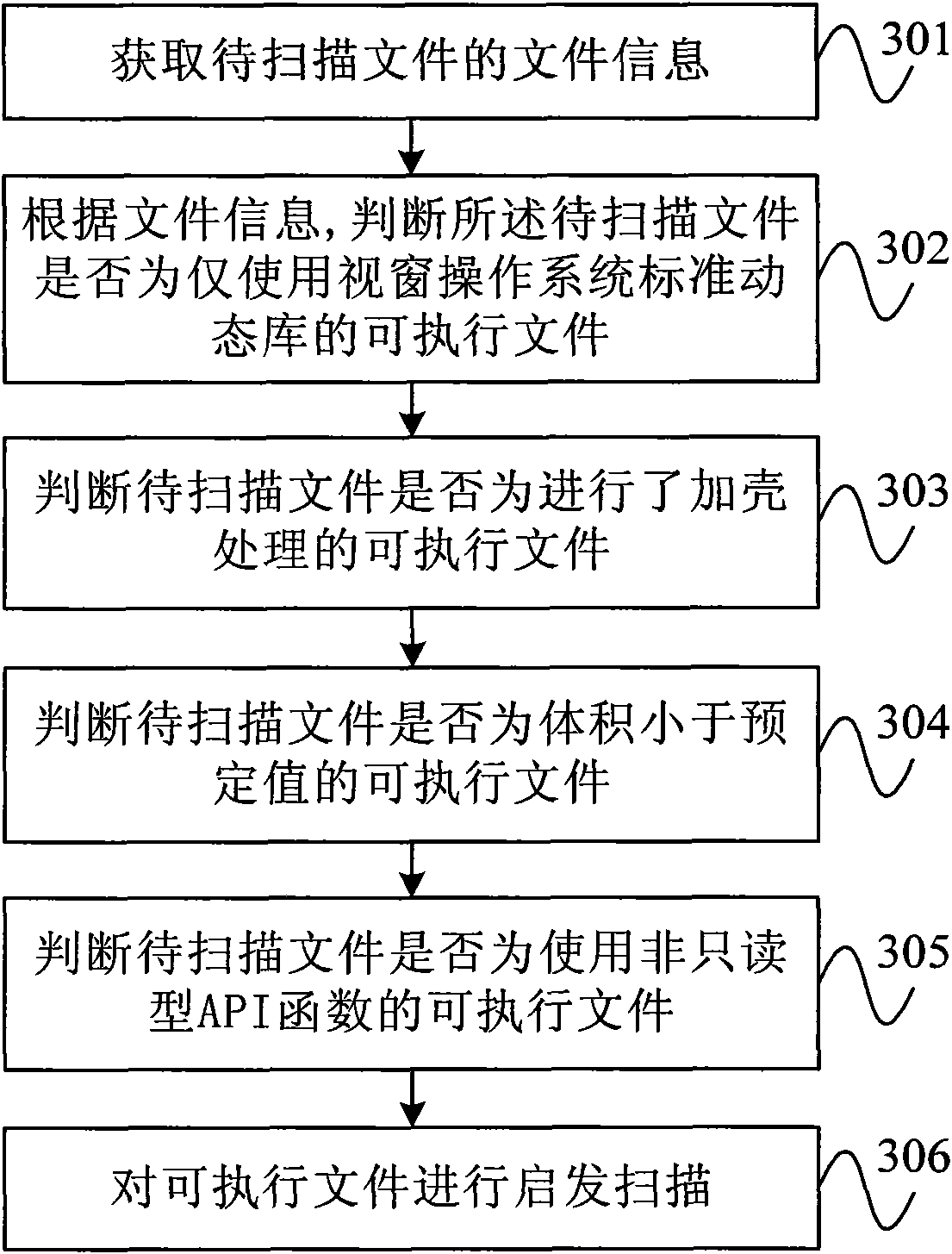
[0021] figure 1 It is a flow chart of the virus program scanning method according to an embodiment of the present invention. As shown in the figure, the method may include the following steps:
[0022] Step 101, acquiring file information of a file to be scanned.
[0023] Step 102, according to the file information, judge whether the file to be scanned is an executable file that only uses the standard dynamic library of the Windows operating system, if so, continue to execute the virus program scanning method described in this embodiment, otherwise obtain the next file to be scanned file, and re-execute the virus program scanning method described in this embodiment.
[0024] Since Microsoft's Windows (Windows TM ) The penetration rate of the operating system is very high. Therefore, in order to increase its own infection rate, most of the existing virus programs usually use the standard dynamic library of Microsoft's Windows operating system. If it is determined that an exec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com