Log correlation analysis system and method
A technology of correlation analysis and analysis method, which is applied in the field of network security management system, can solve the problems of no protocol rules, large amount of log data information, and lack of practical significance, etc., and achieve the goals of increasing calculation speed, high practical guidance, and improving objectivity Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
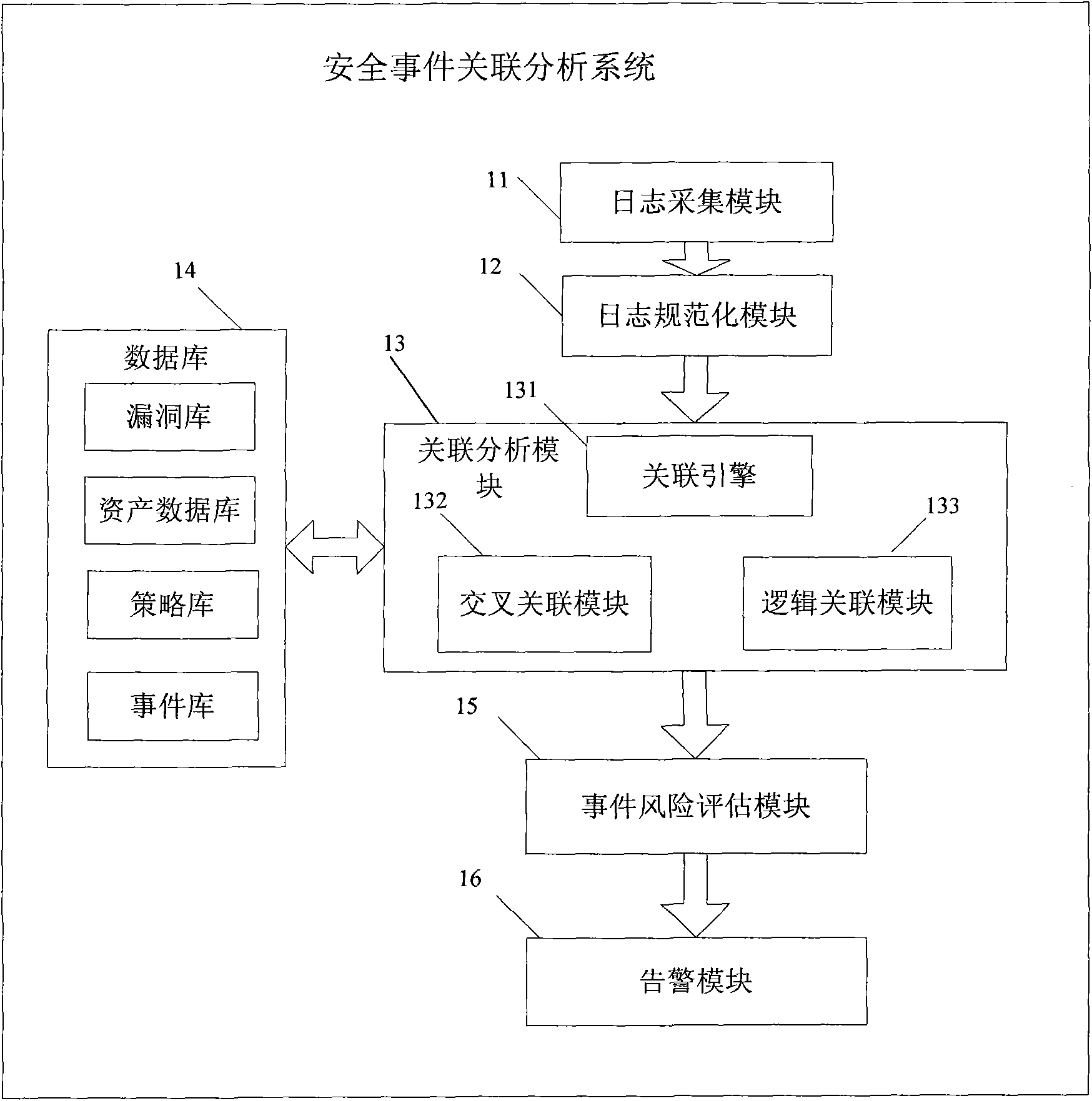
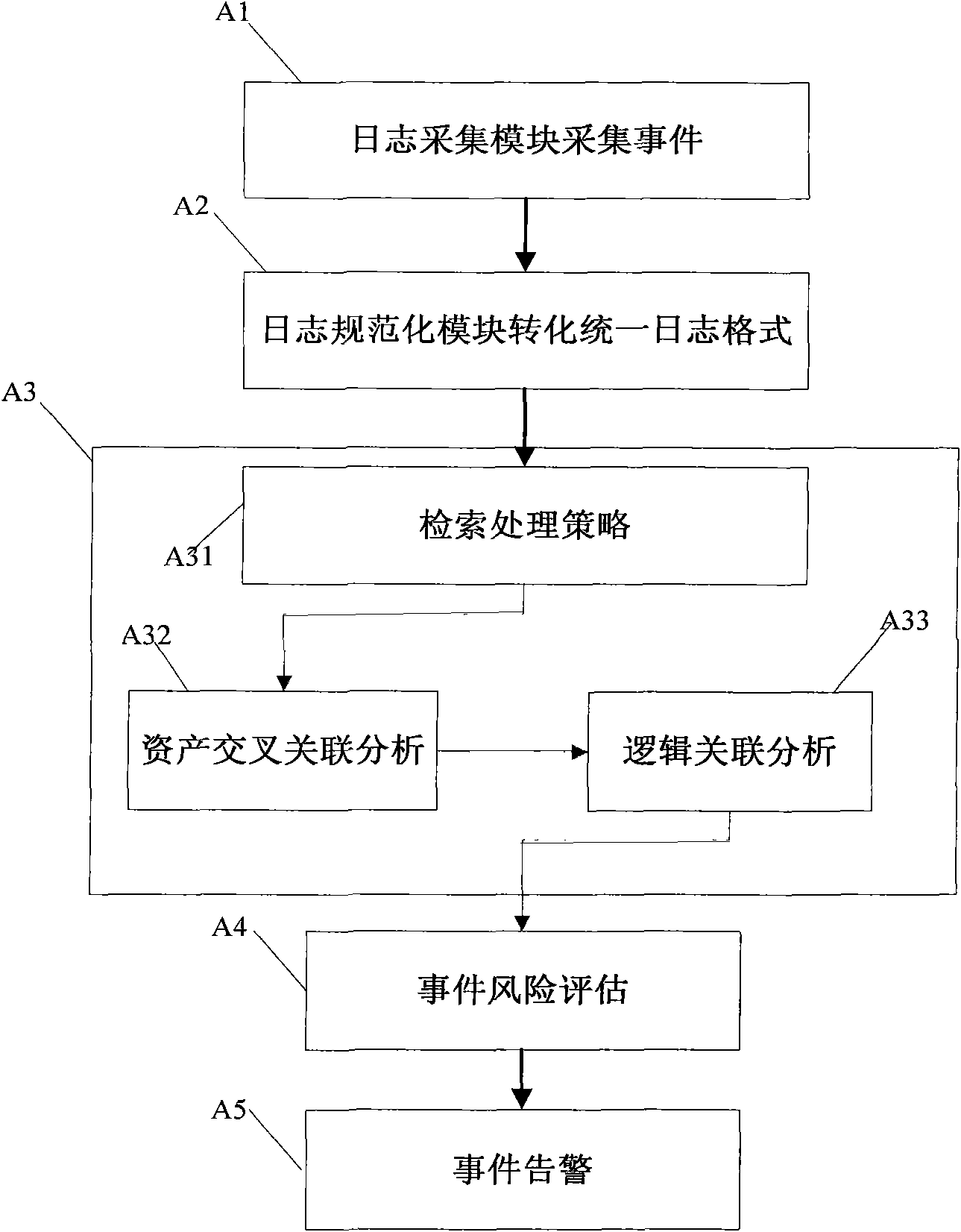
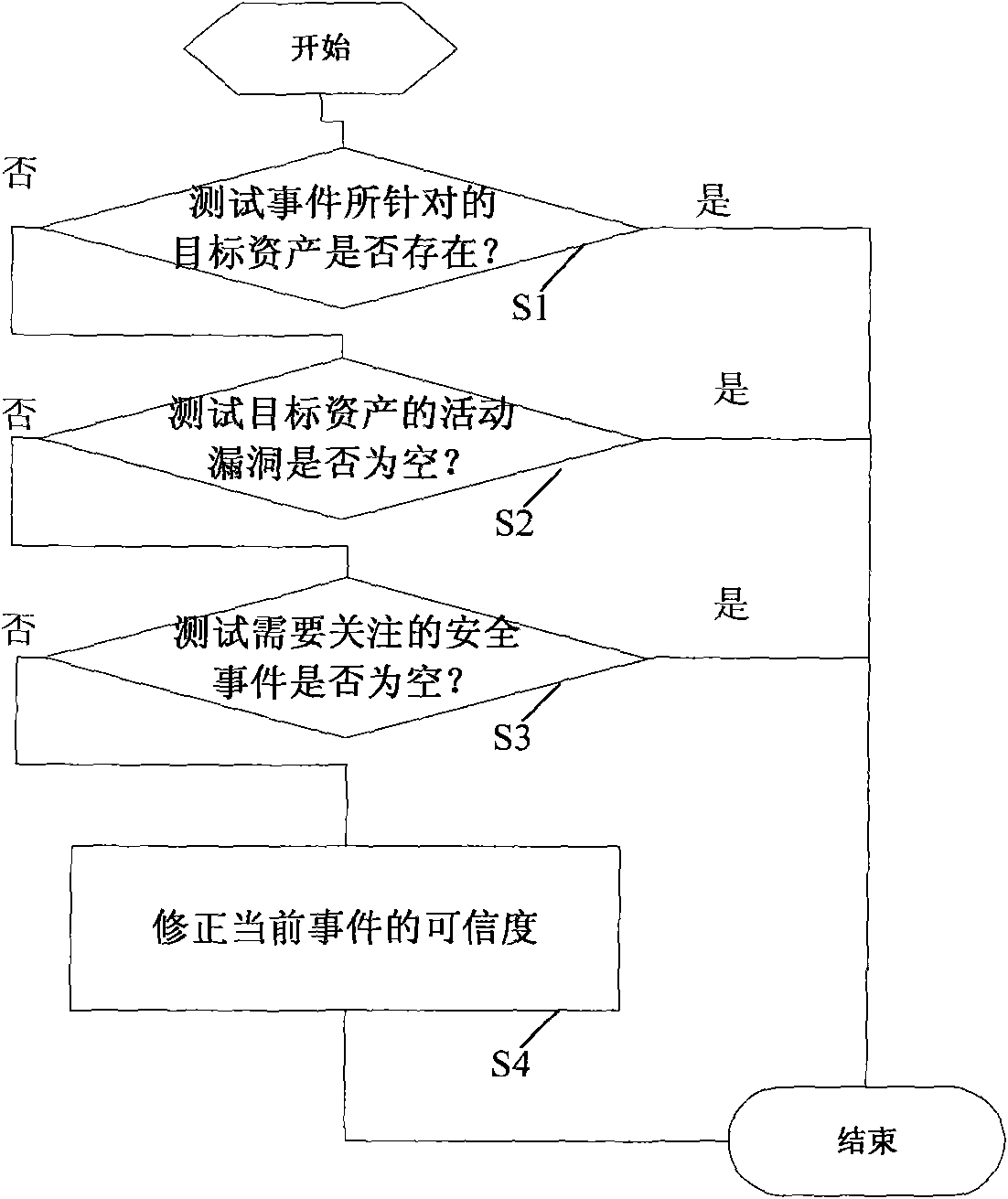
[0048] The core idea is: construct a log event correlation analysis system, which uses different detection tools to collect device health data and log data, detect security weaknesses, and submit standard log data; extract data based on preset regular expressions The feature data in the log data is composed of marked log events, and the log events are analyzed for event-vulnerability association, event-asset association, and event chain association analysis to reduce false alarms and discover new events; and then analyze the events based on the event Credibility, priority, and the value of the source assets and target assets involved in the event. After calculating the threat value and risk level of the event for the source asset and the attack threat value and risk level of the target asset, the threat value is greater than the threshold 1 event, and respond according to the event type identifier of the event.
[0049] Such as figure 1 As shown, it is a functional module sch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com