Compression method and compression device of alarm mask data
A technology of shielding data and compressing methods, applied in the field of optical transmission, can solve the problems of low alarm reporting efficiency, user service interruption, capacity overrun, etc., to achieve the effect of reducing reporting time, improving system efficiency, and reducing the amount of set data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
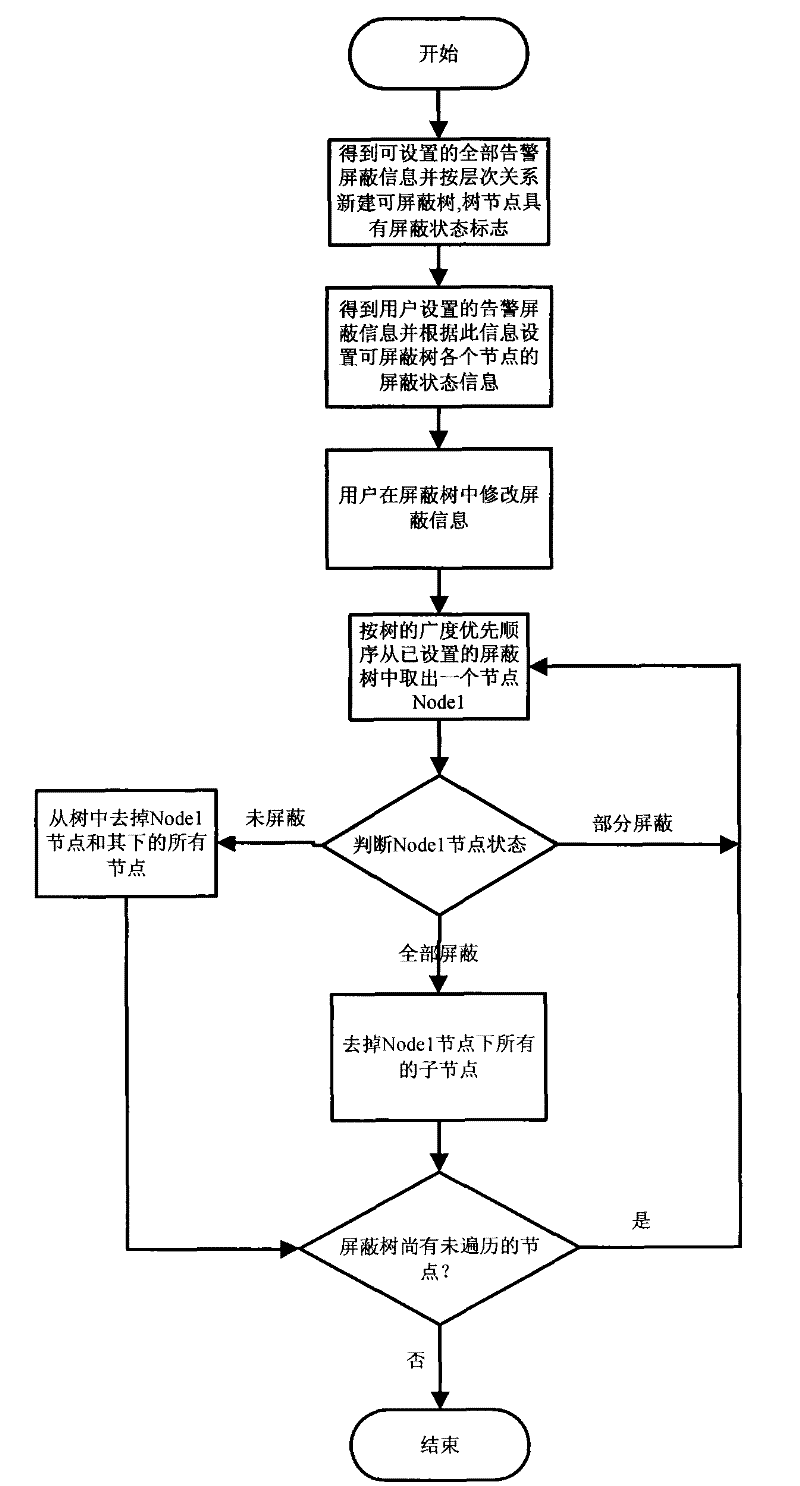
[0027] The alarm masking data compression device involved in this example is used to realize the alarm masking data compression method, including: a status flag module, which obtains the settable alarm masking data, establishes a maskable tree according to the hierarchical relationship, and sets each The node status of the node, the node status includes full shielding status, partial shielding status, and unshielding status; the status update module updates the node status of the shieldable tree; the compression module compresses the shielding tree according to the hierarchical relationship and the traversed node status, and gradually Layer pruning of all nodes below the fully shielded state node, the unshielded state node itself and all nodes below it; the remaining shieldable tree after pruning is the compressed shielding tree, and the compressed alarm shielding data is obtained.
[0028] The compression method of the alarm shielding data involved in this example, such as fi...
Embodiment 2
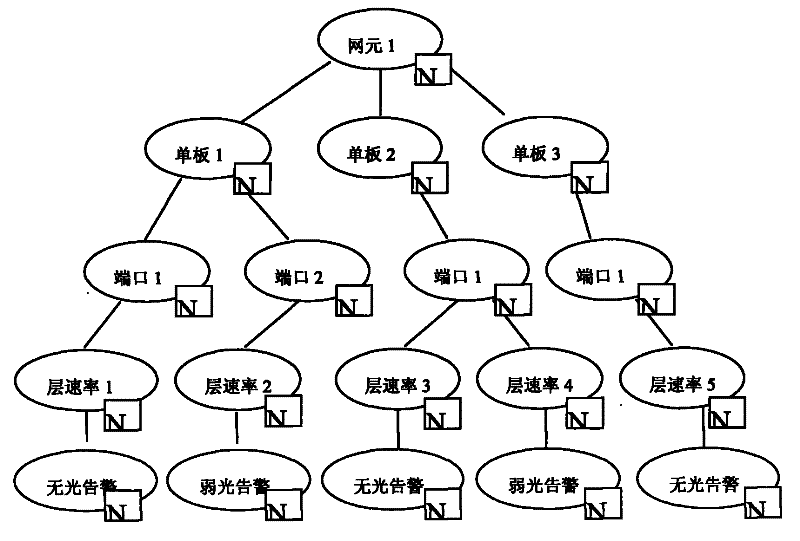
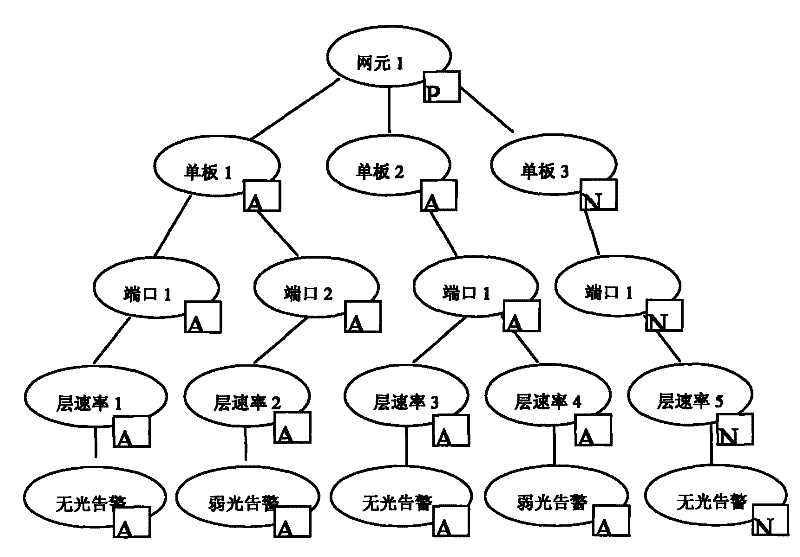
[0052] Please refer to Figure 2 to Figure 4 And Table 1 to Table 4, on the basis of the above example, this example uses a specific implementation mode under one network element to illustrate the method of compressing the alarm mask data and the method of comparing the compressed data.
[0053] Referring to Table 1, Table 1 provides the alarm shielding information that can be set under a network element.
[0054] Table 1
[0055] Alarm number
network element
port
layer rate
Alarm reason
1
veneer 1
port 1
layer rate 1
No light alarm
2
veneer 1
port 2
layer rate 2
Low light warning
3
veneer 2
port 1
layer rate 3
No light alarm
4
Network element 1
veneer 2
port 1
layer rate 4
Low light warning
5
Network element 1
veneer 3
port 1
layer rate 5
No light al...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com