Method, system and relative device for protecting proxy neighbor discovery
A technology of neighbor discovery and protection agent, applied in the field of communication, to solve security problems and avoid attacks of forged IP addresses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention more clear, the embodiments of the present invention will be further described in detail below with reference to the accompanying drawings.
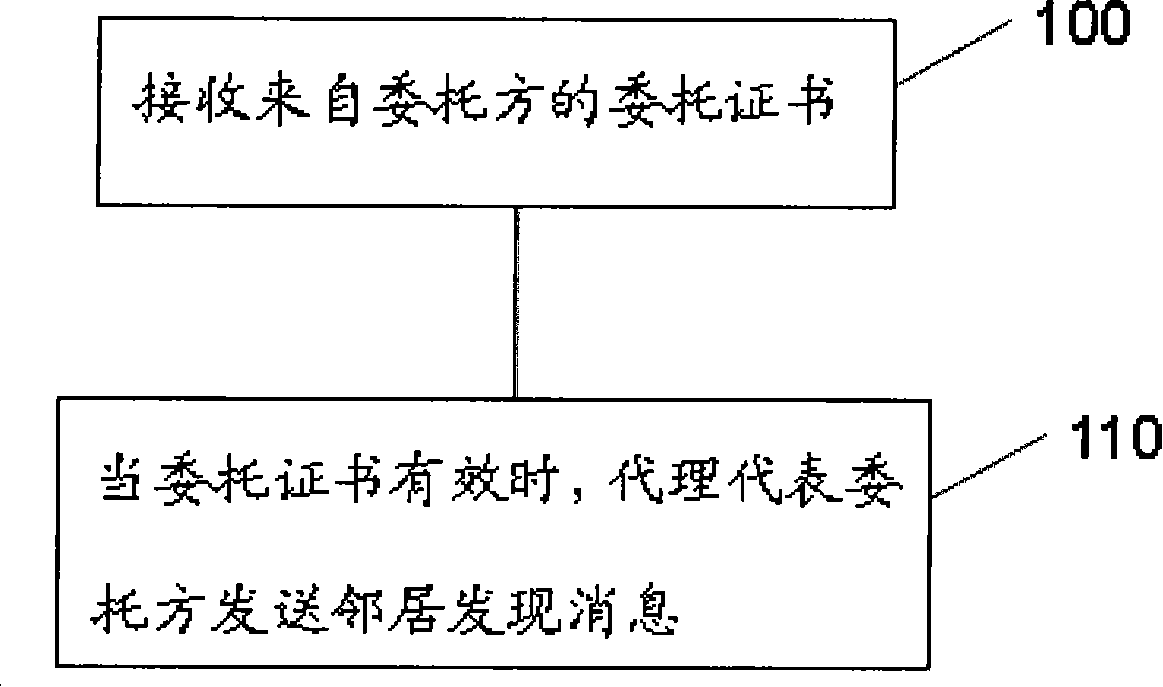
[0059] like figure 1 As shown, Embodiment 1 of the present invention provides a method for protection agent neighbor discovery, the method includes:
[0060] 100. The agent receives the entrustment certificate from the entrusting party;
[0061] In this embodiment, the simplest first-level agent is taken as an example for illustration, and the entrusting party is a mobile node MN that leaves the home network and is in a roaming state.
[0062] The content of the entrusted certificate includes: verification information, and the digital signature of the entrusting party (hereinafter referred to as the first digital signature). Wherein, the verification information includes: a cryptographically generated address CGA and CGA ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com