Method and system for automatically analyzing malicious codes based on virtual hardware environment
A malicious code, virtual system technology, applied in software testing/debugging, instrumentation, electrical digital data processing, etc., can solve problems such as difficulty in comprehensive coverage and limiting analysis efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] Below in conjunction with accompanying drawing and specific embodiment the present invention is described in further detail:
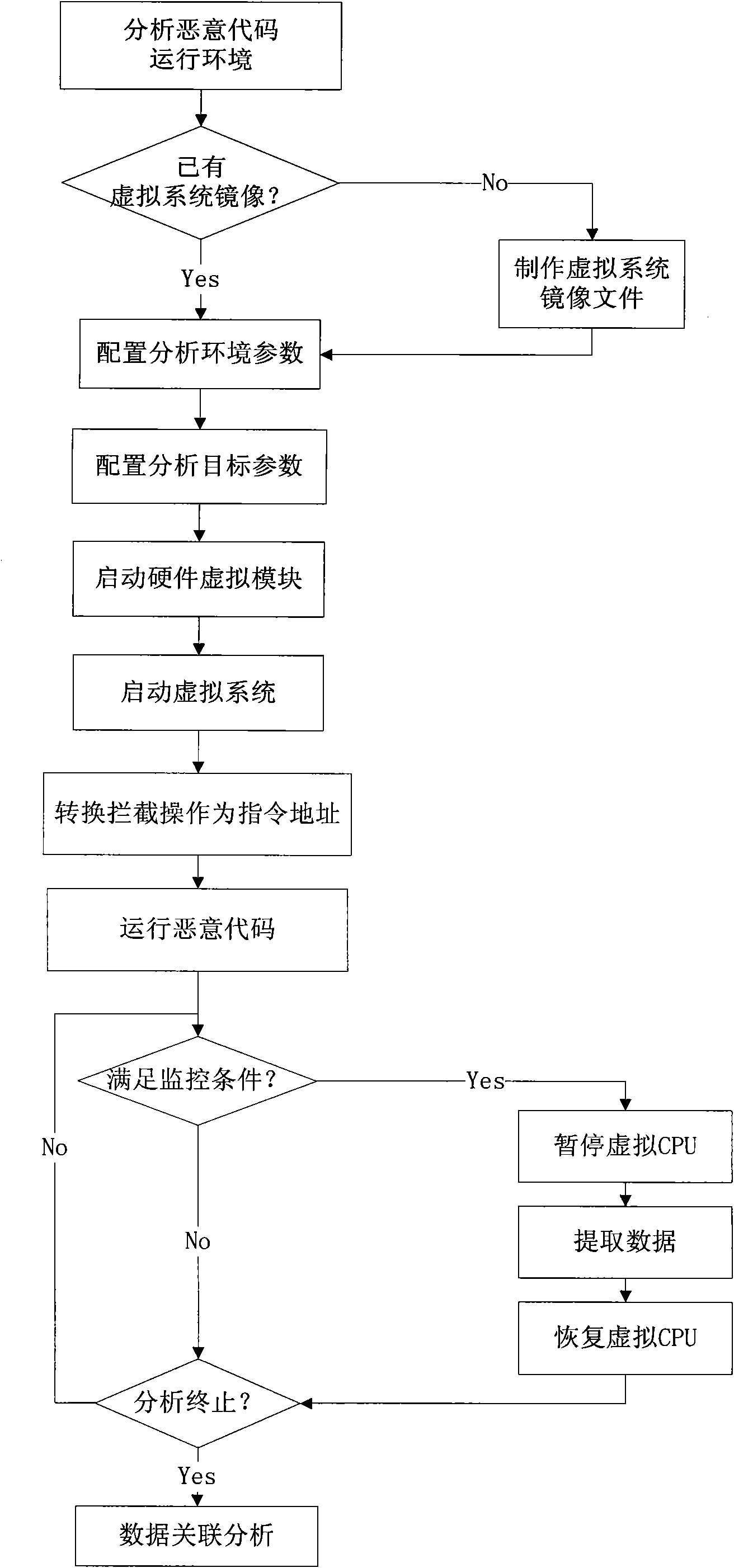
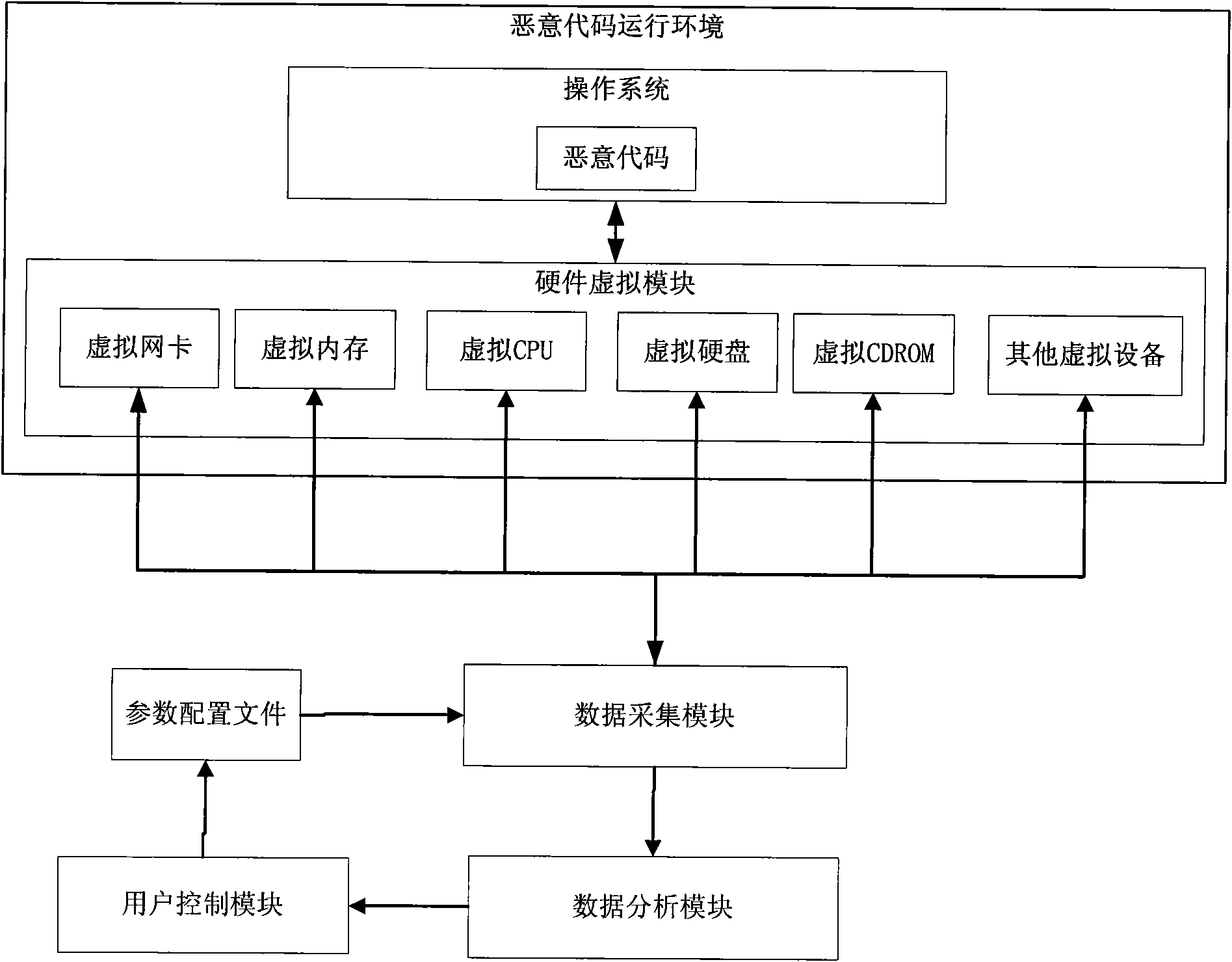
[0030] Analysts set up a malicious code operating environment, configure parameters such as the analysis environment and analysis target, start the hardware virtual module, load and start the operating system image required for the malicious code to run, and run the malicious code to be analyzed. According to the analysis target, the data collection module intercepts specific virtual CPU instructions and virtual hardware access operations, and collects and records related access data. The data analysis module integrates various data collected by the data acquisition module, displays the malicious code running information in real time through the user control module, and after the analysis process is terminated, correlates and analyzes all the collected data, and outputs the analysis results.
[0031] Reference attached figure 1 , the detailed ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com