Link method and linker
A linker and compiler technology, applied in the direction of instrument, memory system, program control design, etc., can solve problems such as difficult implementation, complicated process, advanced users, etc., to achieve easy implementation, simplify complexity and difficulty, and reduce complexity and difficulty Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
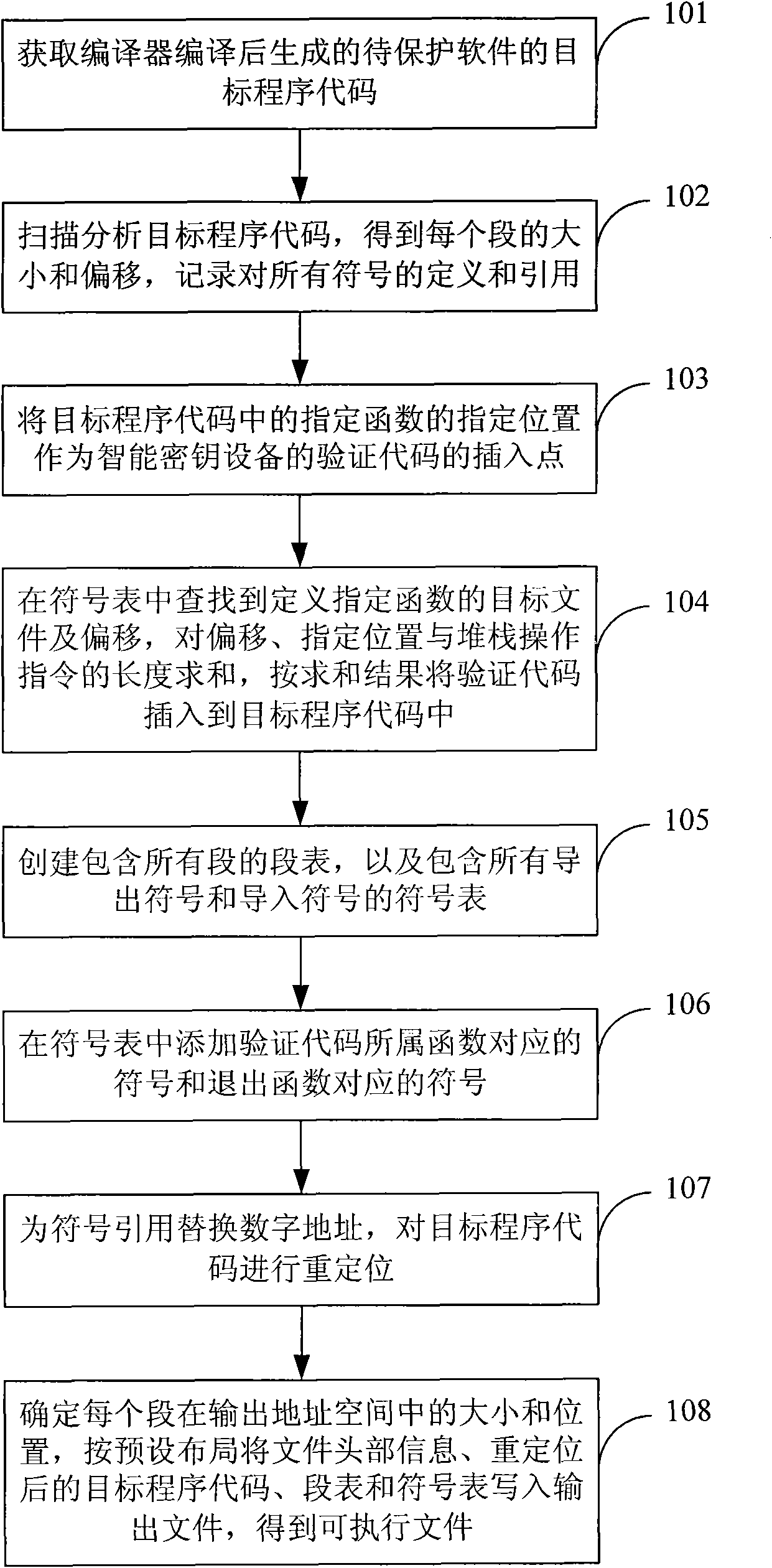
[0052] see figure 1 , this embodiment provides a linking method, specifically including:
[0053] Step 101: Obtain the target program code of the software to be protected, the target program code is generated by compiling the program source code of the software to be protected by a compiler;
[0054] Wherein, the program source code may be written in multiple high-level languages, such as C language, C++ language and other high-level languages. There are many kinds of compilers, such as gcc (GNU C Compiler) compiler.
[0055] Program source code is usually stored in the form of source files. If there are multiple source files, the compiler compiles each source file into a corresponding object program code, ie, an object file, so that multiple object files can be obtained.
[0056] Step 102: Scanning and analyzing the obtained target program code, obtaining the size and offset of each segment in the target program code, and recording the definitions and references of all symb...
Embodiment 2
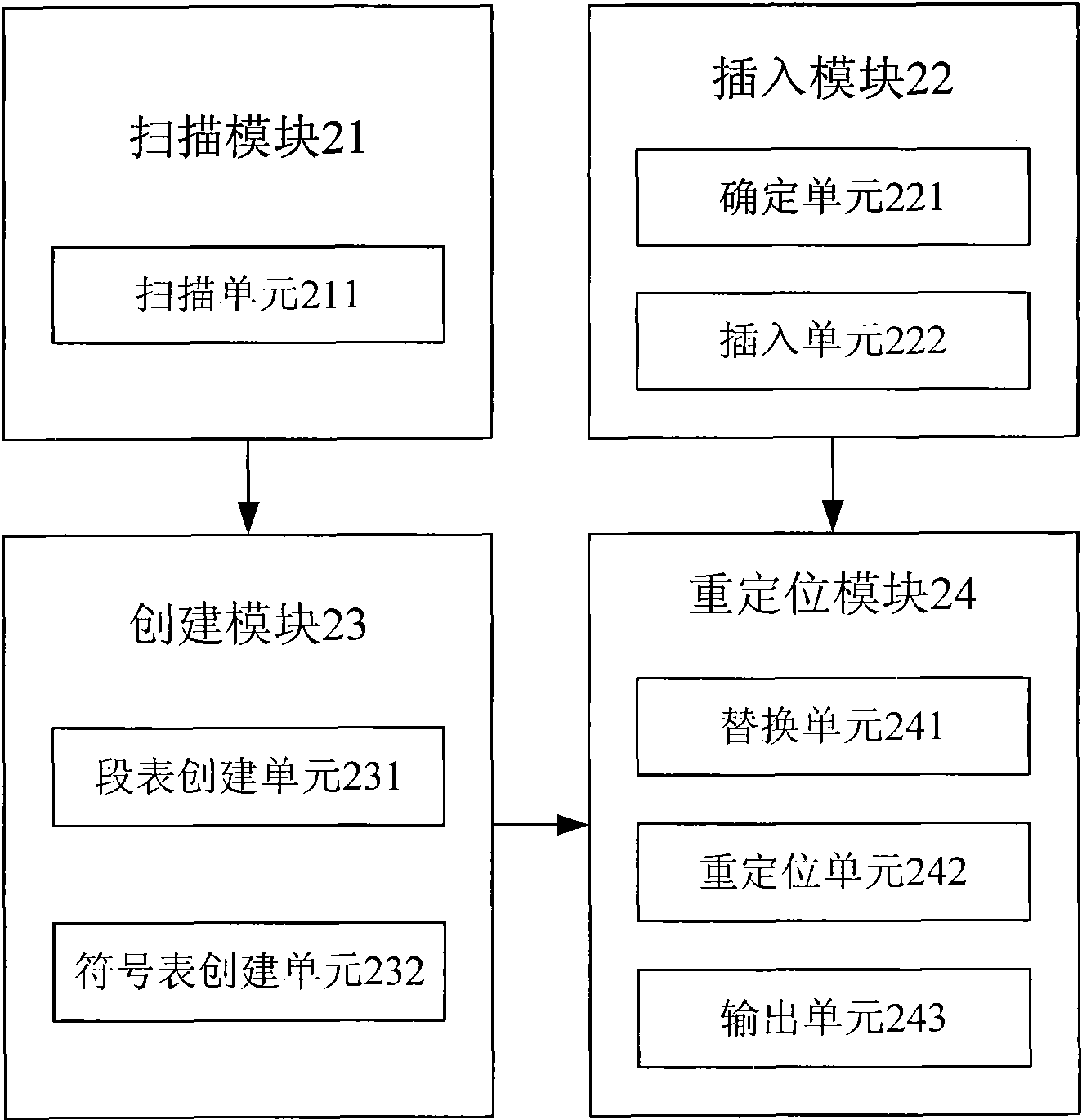
[0157] see figure 2 , this embodiment provides a linker, specifically including:
[0158] The scanning module 21 is used to scan the target program code of the software to be protected generated after compiling by the compiler;
[0159] The insertion module 22 is used to determine the insertion point of the verification code of the smart key device in the target program code, and inserts the verification code into the target program code according to the position corresponding to the insertion point;
[0160] Create module 23, be used for creating segment table and symbol table according to the information that scan module 21 obtains, add the symbol corresponding to the function that verification code belongs to and the symbol corresponding to exit function in symbol table, the function that verification code belongs to is used for when running software to be protected When verifying the smart key device, the software to be protected is allowed to run when the verif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com