Compile method
A compilation method and grammatical analysis technology, applied in the fields of instruments, electronic digital data processing, platform integrity maintenance, etc., can solve the problems of complicated copyright protection methods and the target program cannot be well protected by copyright, so as to reduce the complexity and difficulty. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
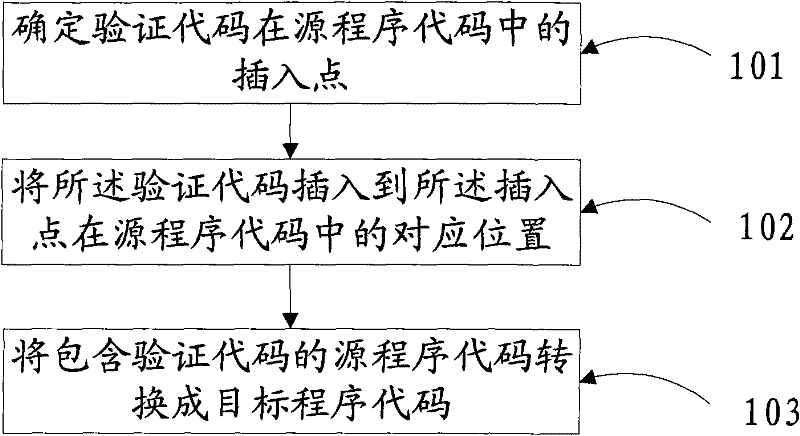
[0026] In order to simplify and reduce the complexity and difficulty of copyright protection, the embodiment of the present invention provides a compiling method, such as figure 1 As shown, the method includes:
[0027] 101. Perform preprocessing on the source program code, and perform lexical analysis and syntax analysis on the preprocessed source program code; determine the insertion point of the verification code in the source program code according to preset rules.
[0028] Wherein, the verification code can be a code for verifying the smart key device, and the verification code can also be a function call, and the function completes the function of verifying the smart key device, and the function can be implemented in a compiled library, or, the function is placed in the source program code in the form of source code;
[0029] The method for determining the insertion point of the verification code in the source program code is to determine the insertion point of the veri...
Embodiment 2
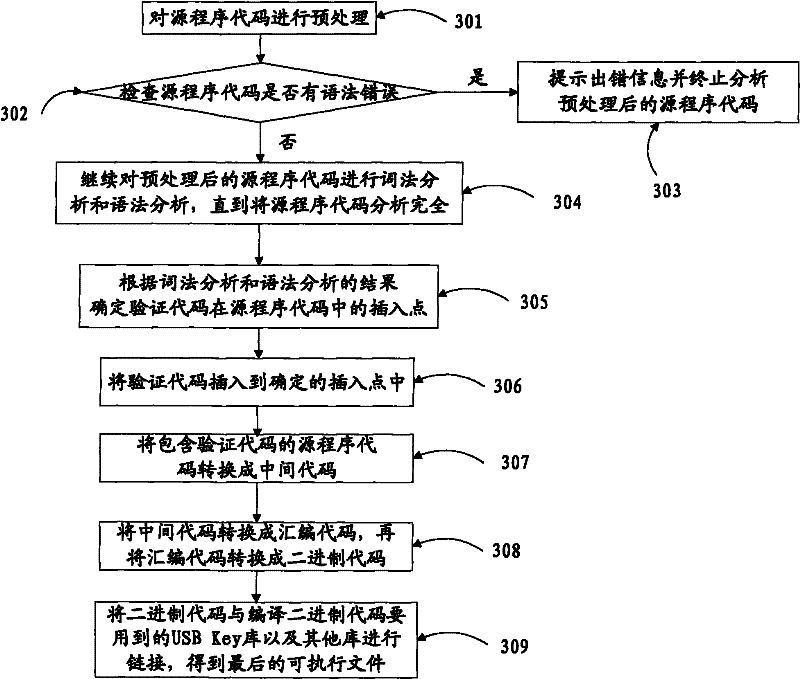
[0037] In order to introduce the technical solution adopted by the present invention more clearly, below in conjunction with the compiling process under the situation that adopts USB Key as the intelligent key device, further describe the present invention in detail, but, the present invention can also include other intelligent key devices Examples, this example is not intended to limit the present invention.
[0038] In this embodiment, the verification code is inserted into the corresponding position of the insertion point in the source program code to achieve the purpose of making the compiled target program code protected by the USB Key, such as image 3 As shown, the specific implementation includes the following:
[0039]301. In the process of compiling, it is first necessary to preprocess the source program code. The preprocessing process mainly analyzes the header files and precompiled statements contained in the source program code to obtain the preprocessed source pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com