Method and device for preventing neighbor discovery (ND) attack
A legal and purposeful technology, applied in the field of preventing ND attacks, it can solve problems such as hidden dangers of Internet architecture, inability to carry out network communication, network slowness, etc., and achieve the effect of preventing NDNS/NA attacks, NDDAD attacks, and NDRA attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
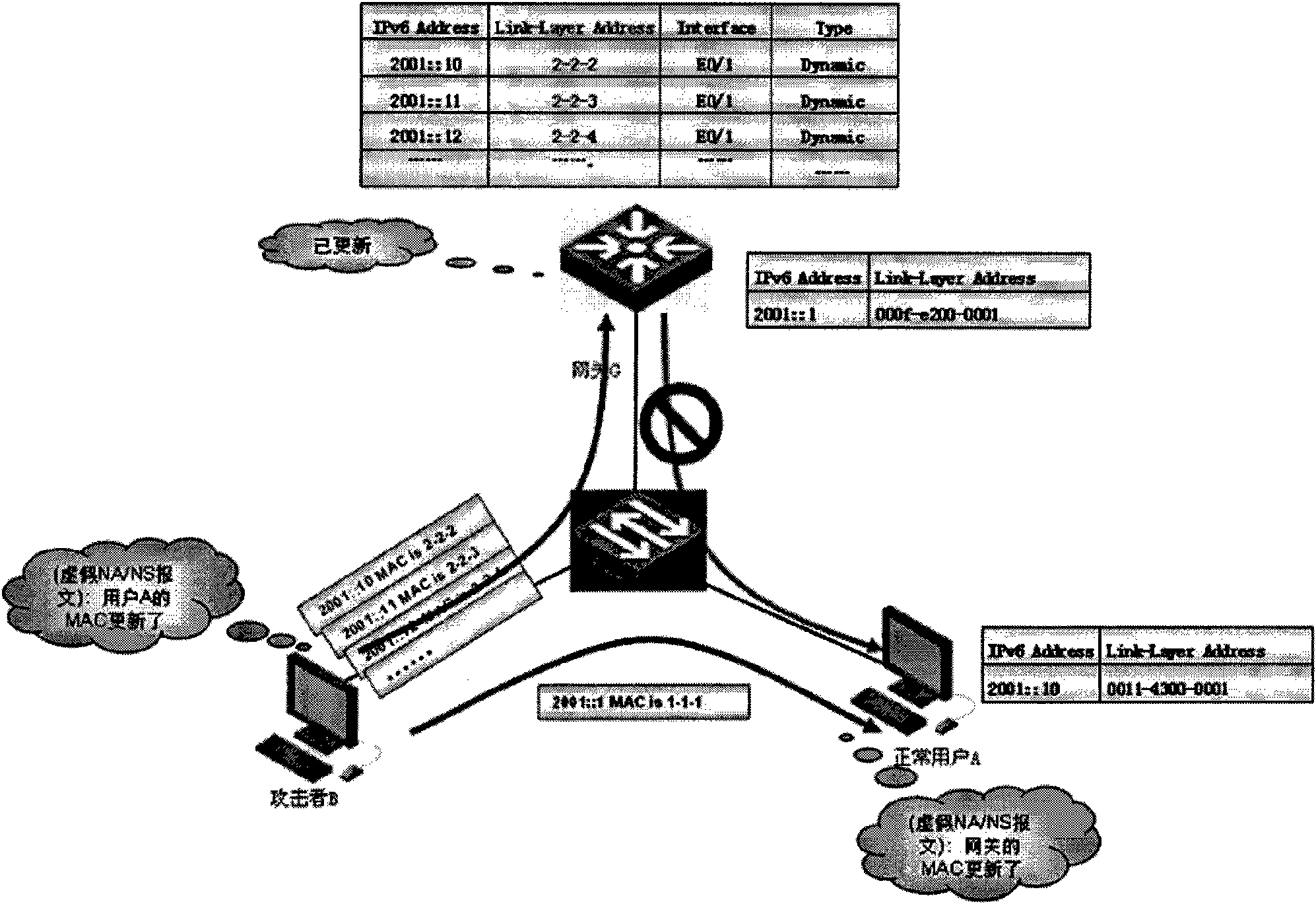
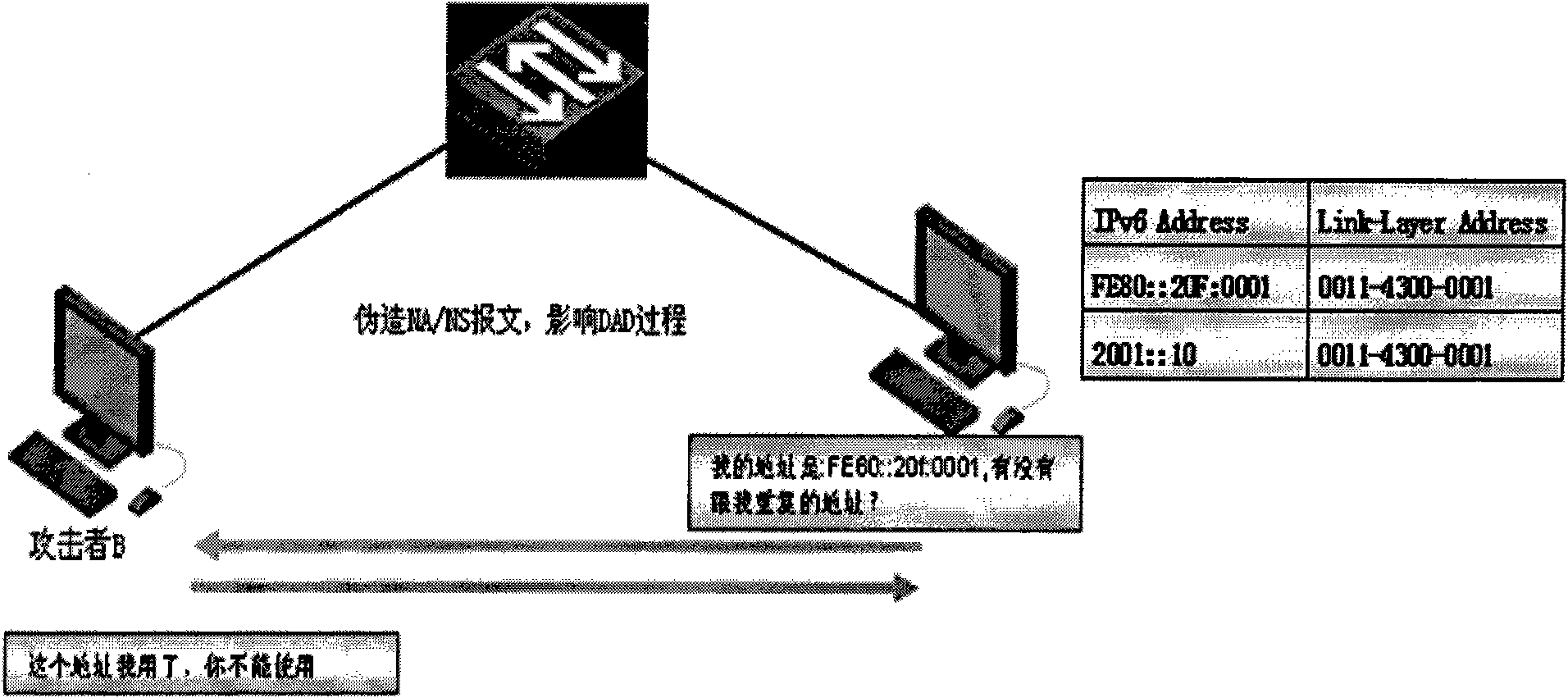
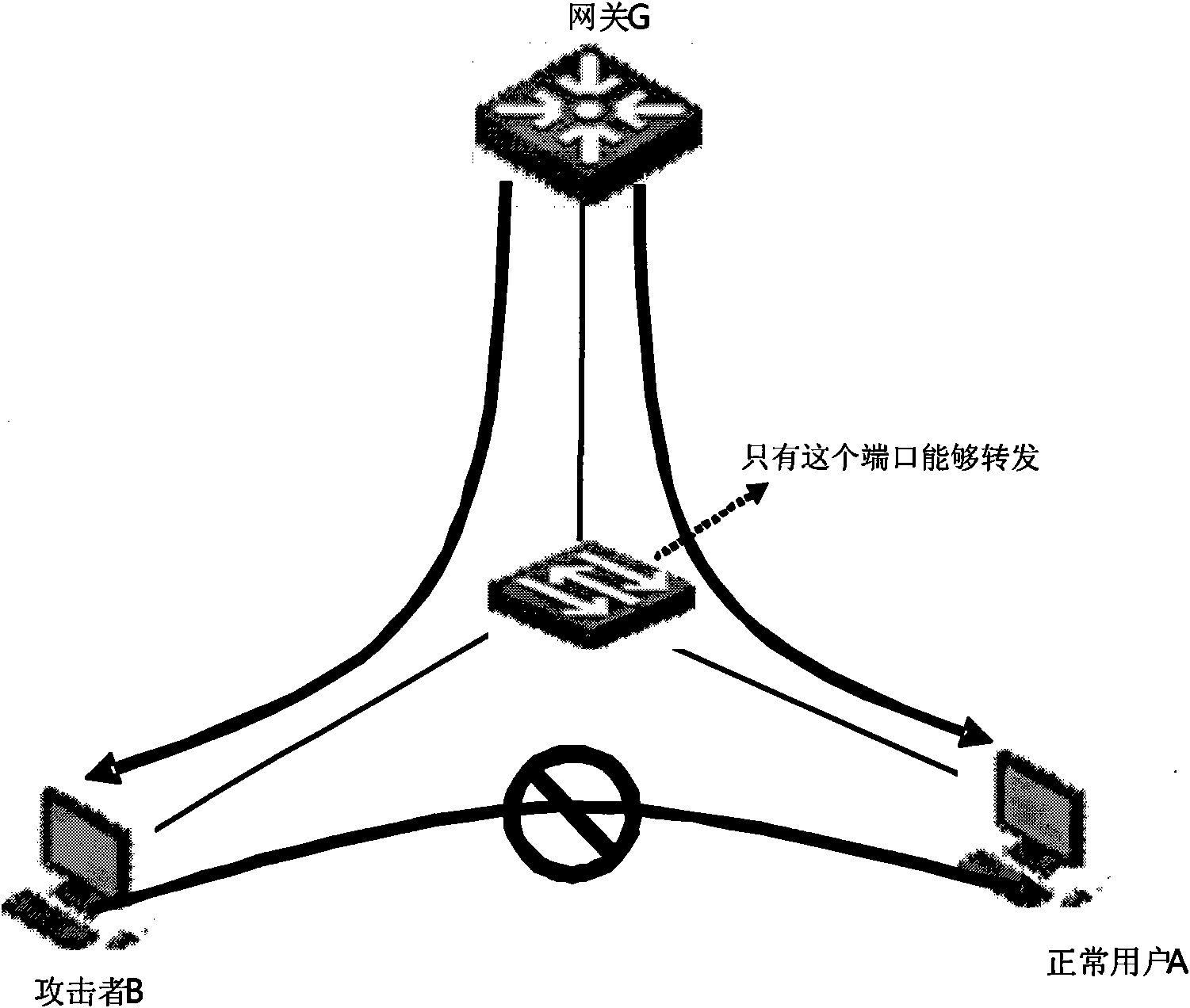
[0055] The basic idea of the present invention is that the access switch obtains and stores the authentication information of the terminal during the authentication process of the terminal, that is, stores the authenticated terminal identity information in the access switch. When an ND message is received, the terminal identity information in the ND message is obtained, and the terminal identity information is compared with the authenticated terminal identity information, thereby judging whether the ND message is a legal terminal (authenticated terminal ) sent by a legal terminal, the ND message is processed, otherwise, the ND message is discarded, so that the authentication mechanism (for example, 802.1X authentication mechanism, PPPoE authentication mechanism, PORTAL Authentication mechanism, etc.) combined with ND SNOOPING improves the security of the ND entry learning mechanism and prevents common ND attacks.
[0056] Such as Figure 4 As shown, a method for preventing ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com