Method for automatically acquiring user behavior log of network
An automatic acquisition and network user technology, applied in electrical components, transmission systems, etc., can solve the problems of low scalability and portability of log acquisition, and achieve easy deployment, high portability, and easy preprocessing and data mining. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] In order to understand the present invention more clearly, the present invention will be further described in detail below in conjunction with the accompanying drawings.
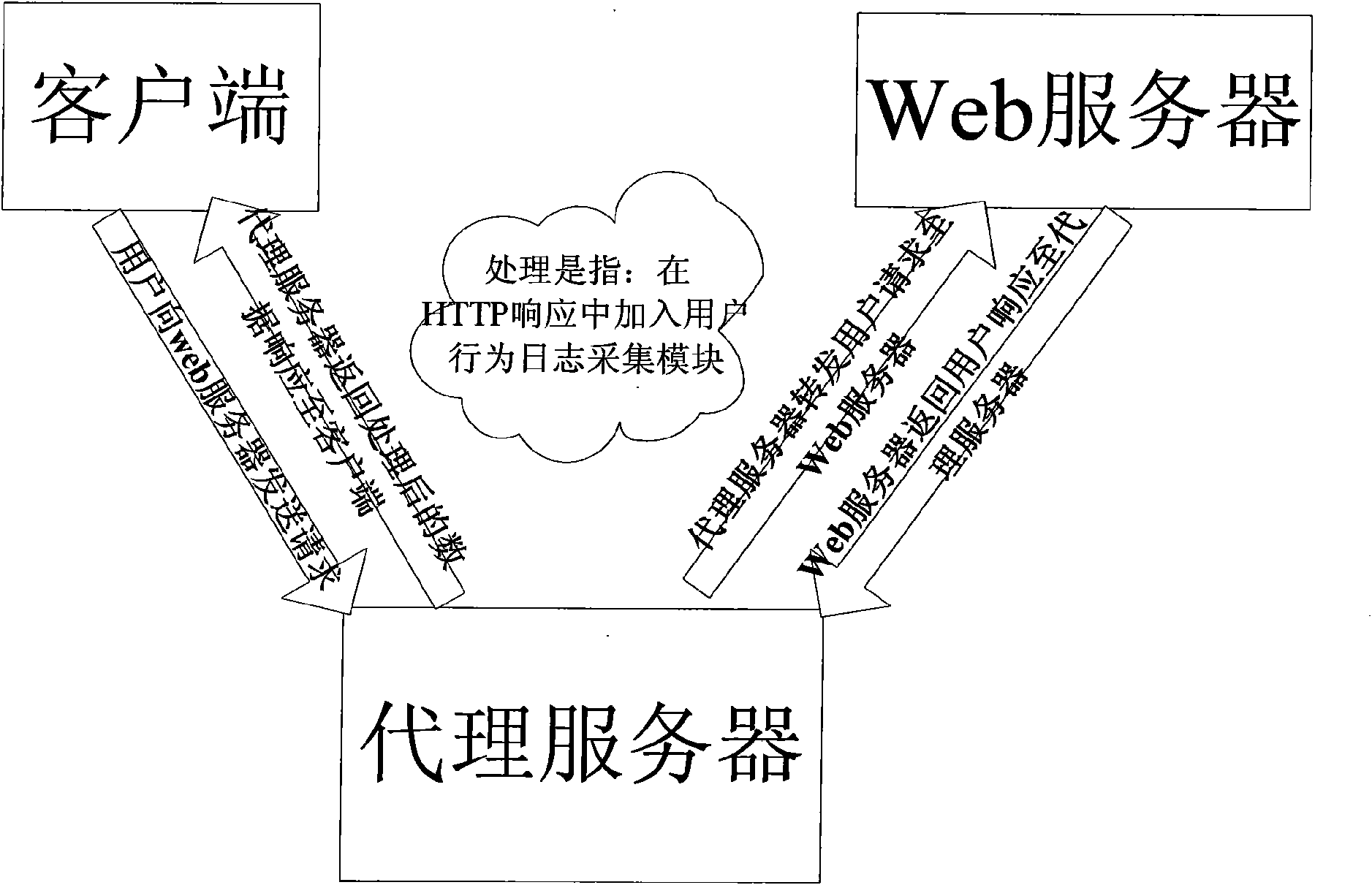
[0055] Such as figure 1 As shown, a "proxy server" is added between the client and the Web server, and the user sends a request to the Web server through the client; the proxy server intercepts the request and forwards it to the Web server; the Web server returns an HTTP response to the proxy server; The server processes the HTTP response returned by the Web server, and adds a user behavior log collection module to the HTTP response, and then sends it to the client.
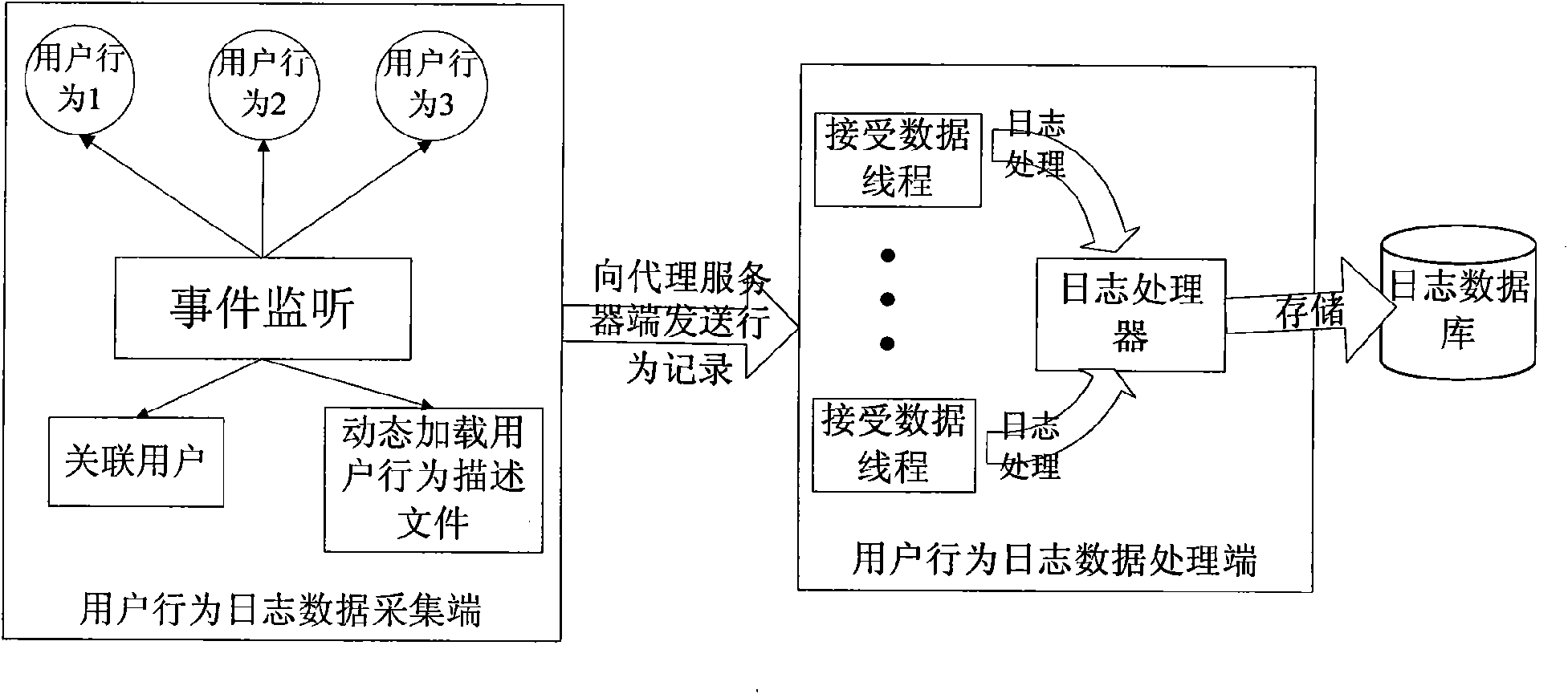
[0056]The present invention adopts C / S mode, considers extensibility, these two characteristics of transplanting, the method for user behavior log acquisition mainly comprises the design of two aspects: the data collection end of user behavior log and the data processing end of user behavior log (such as figure 2 shown). To be describ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com