Anti-peep password input method
A password input and anti-peeping technology, applied in the information field, can solve the problems of high implementation cost, restrictions, and increased investment in terminal equipment, and achieve the effect of reducing password leakage and reducing opportunities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
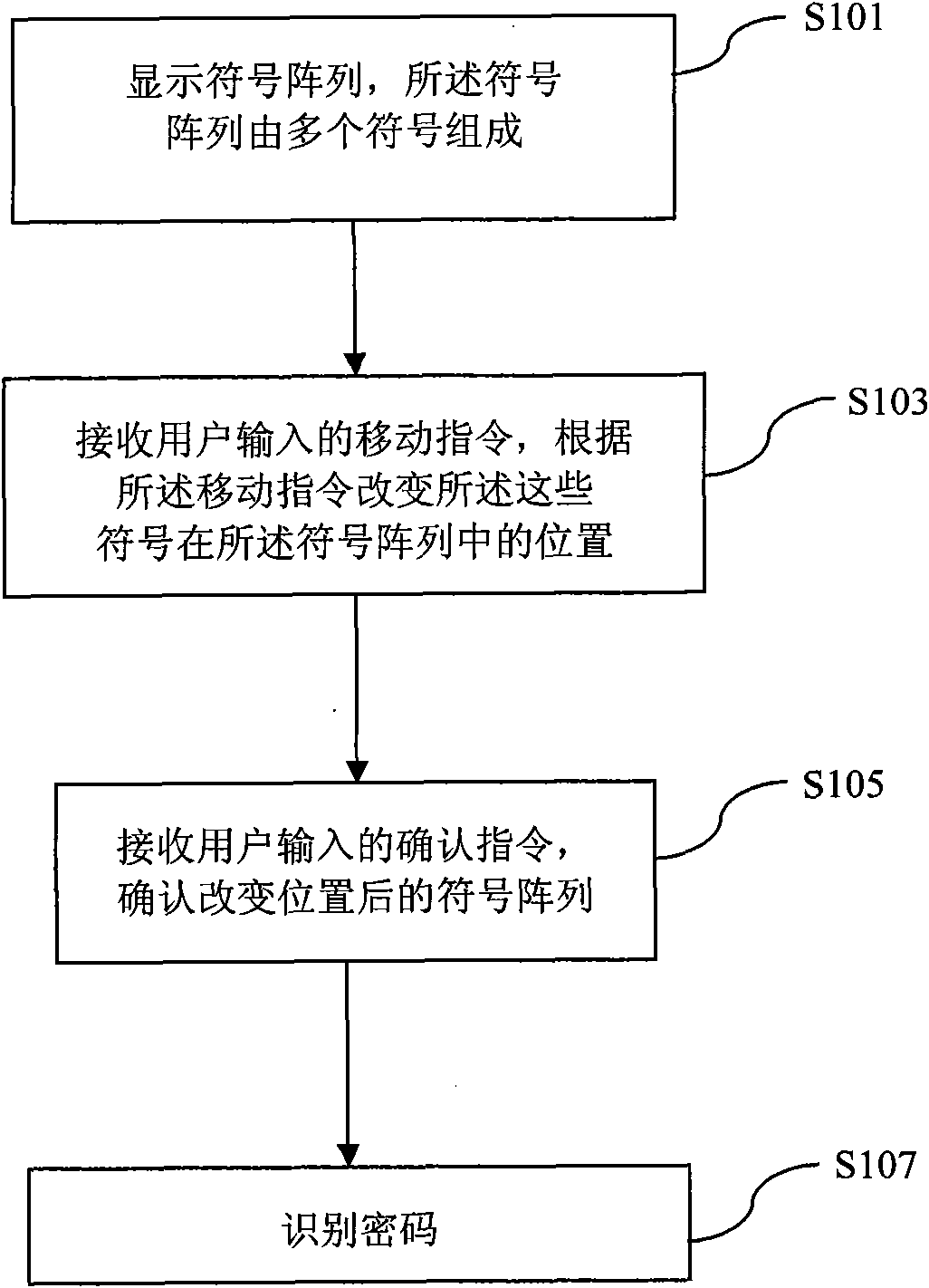
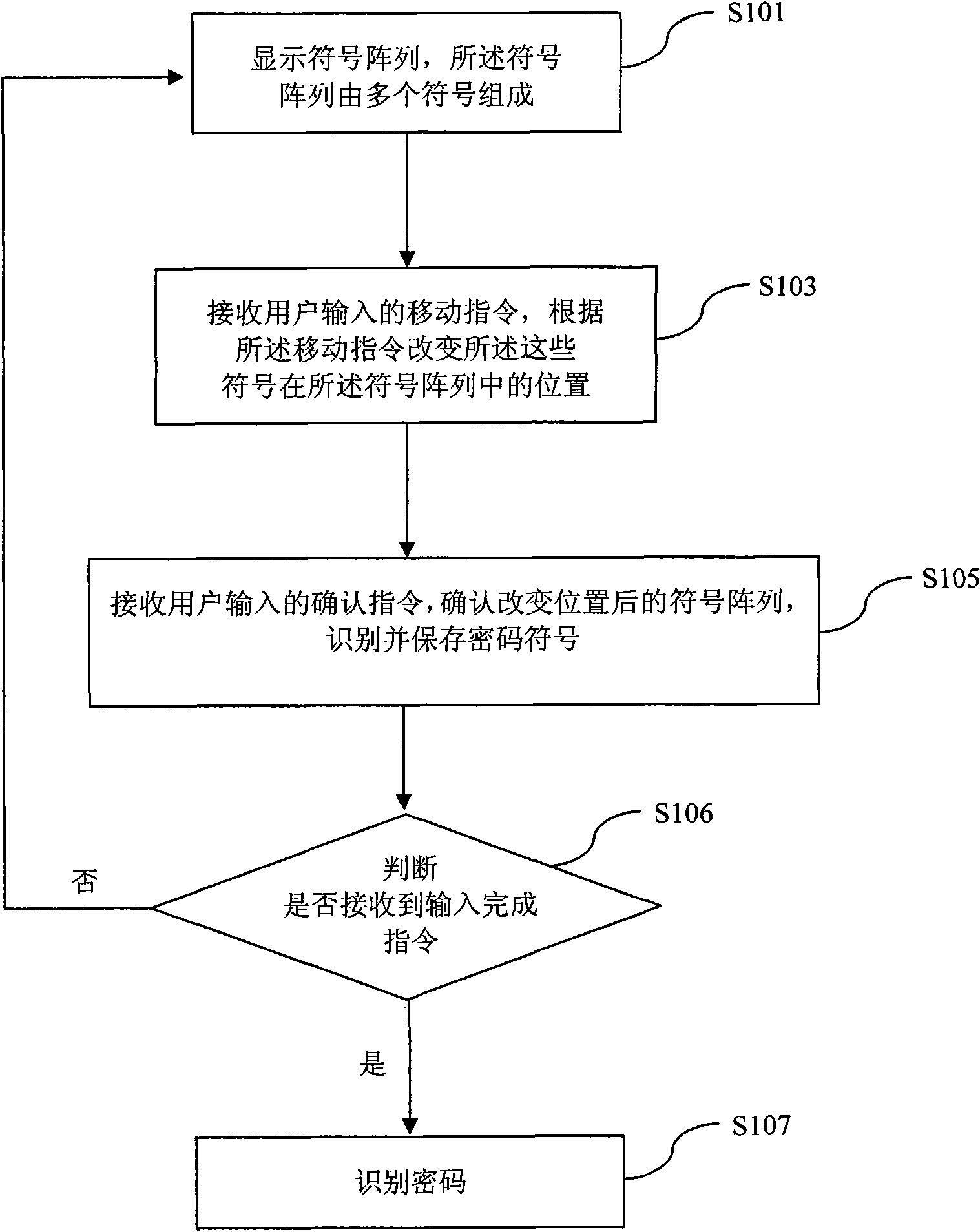
[0016] Such as figure 1 As shown, the present embodiment provides an anti-peeping password input method, the method comprising:
[0017] Step S101: displaying a symbol array, the symbol array is composed of a plurality of symbols;
[0018] Step S103: receiving a movement instruction input by the user, and changing the positions of the symbols in the symbol array according to the movement instruction;
[0019] Step S105: receiving a confirmation instruction input by the user, and confirming the symbol array after changing the position;
[0020] Step S107: Identify the password.
[0021] When the user starts to input the password in the above step S101, the password input device displays a symbol array on its display unit, the symbol array is composed of a plurality of symbols recognizable by human eyes, including the symbols constituting the user password. The symbols in the symbol array conform to the specified password symbol set, that is, the symbols displayed in the symb...
Embodiment 2
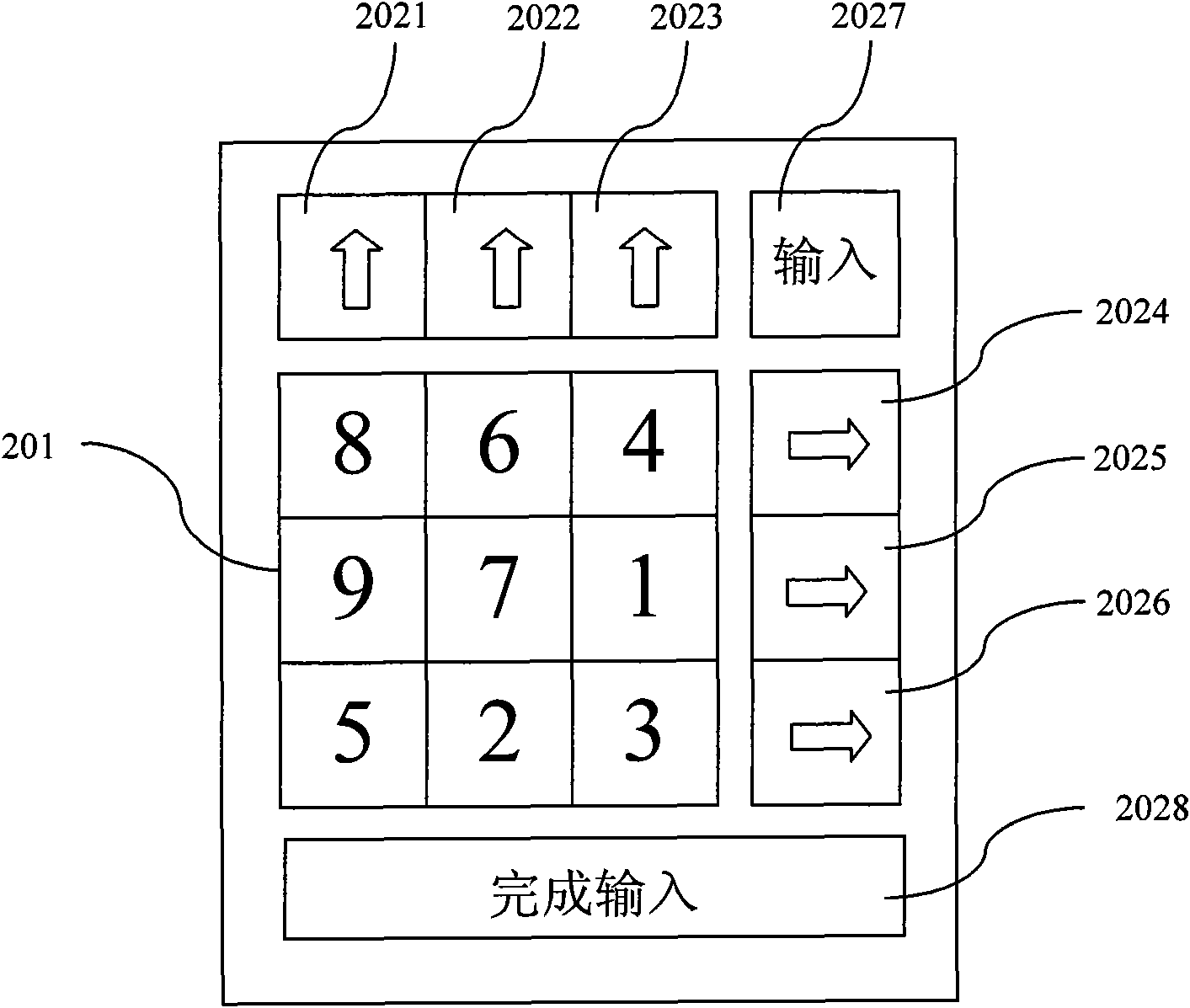
[0026] The method of this embodiment stipulates that in the symbol array confirmed in step S105, the password symbol is located at a specific position, and the specific position is preset by the user. For example, it is stipulated that the password symbol is located in the central cell of the symbol array, then in this embodiment, the password symbol needs to be moved to the center of the symbol array in step S103, that is figure 2 In the position of character ' 7 ', then click the input button 2027 to confirm the symbol array in step S105, and step S107 reads the password symbol from the central position of the confirmed symbol array according to the preset position regulation.
Embodiment 3
[0028] In yet another embodiment of the present invention, reference symbols and a preset relative positional relationship are used to assist input to avoid password disclosure caused by directly clicking on the password. The relative positional relationship refers to the position of the reference symbol and the password symbol in the symbol array. In terms of the relationship between display positions, intuitively, "diagonal relationship", "upper and lower adjacency", "left and right adjacency" and the like can be preferred. The system stipulates that in step S103, the user needs to select a reference symbol, and set the positions of the password symbol and the reference symbol to conform to the preset relative positional relationship. For example, the preset relative positional relationship is "the reference symbol is below the password symbol, and the two are adjacent up and down", then in figure 2 In the symbol array shown, if you want to enter the password '1', the execu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com