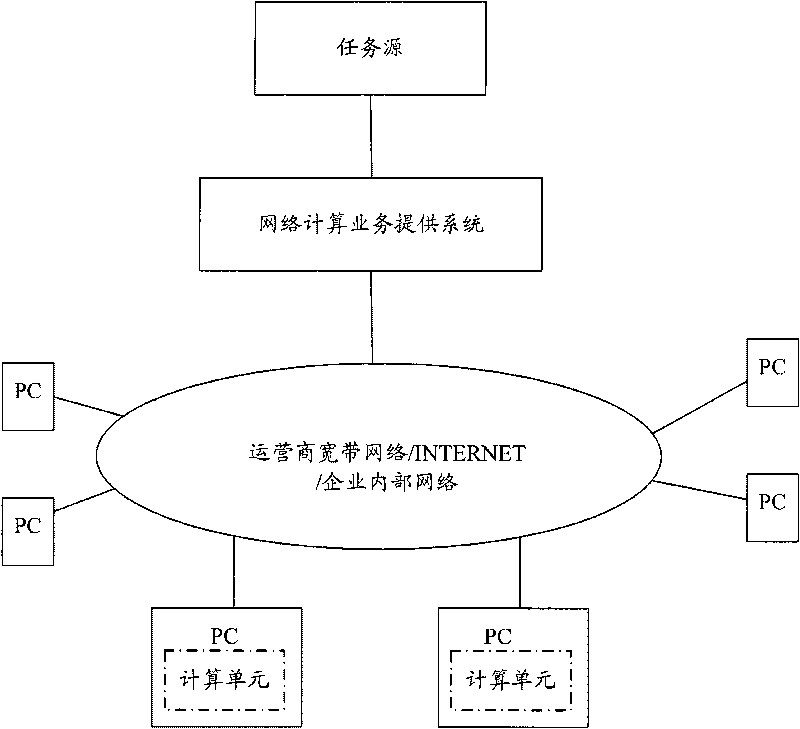
Counting method of network computing service and network computing service providing system
A technology for computing services and networks, applied in the field of communications, which can solve problems such as compensation for contributors who lack or cannot resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
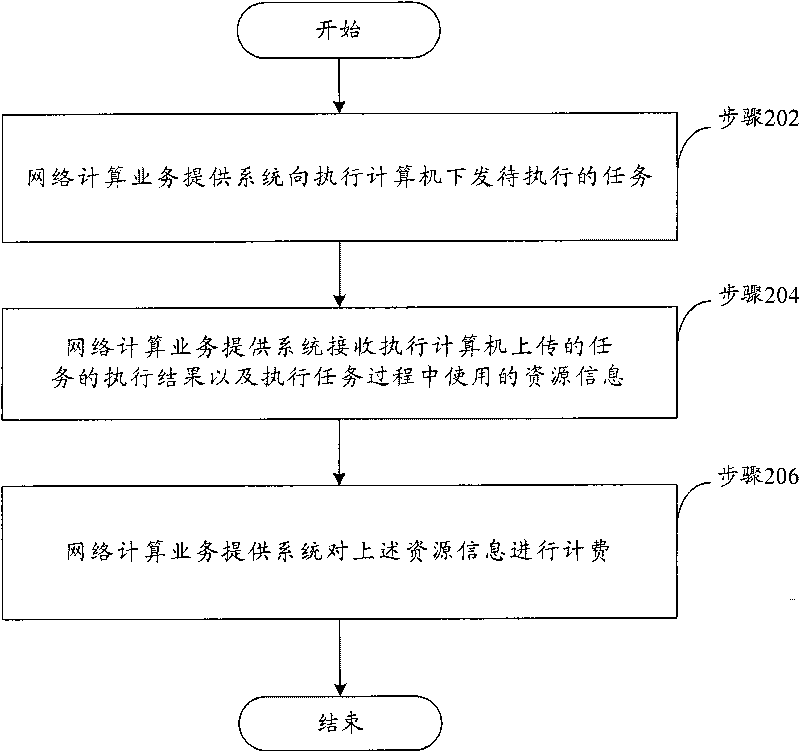
[0079] In this embodiment, the system for providing the network computing service may use any charging method for charging.
[0080] Figure 5 It is a flow chart according to Embodiment 1 of the present invention. Such as Figure 5 As shown, the process specifically includes the following steps (step 501-step 505):
[0081] Step 501 , the network computing service provision system, after receiving the application request from the task source and performing relevant verification, accepts the application request, and performs tasks such as decomposition and allocation. Determine how many execution computer resources are needed, and send the decomposed related tasks to the relevant execution computers, and record that the relevant execution computers are in the execution state;
[0082] Step 502, the execution computer accepts the task, executes the task, and simultaneously records the resource information consumed by executing the task during the execution process;
[0083] ...
Embodiment 2
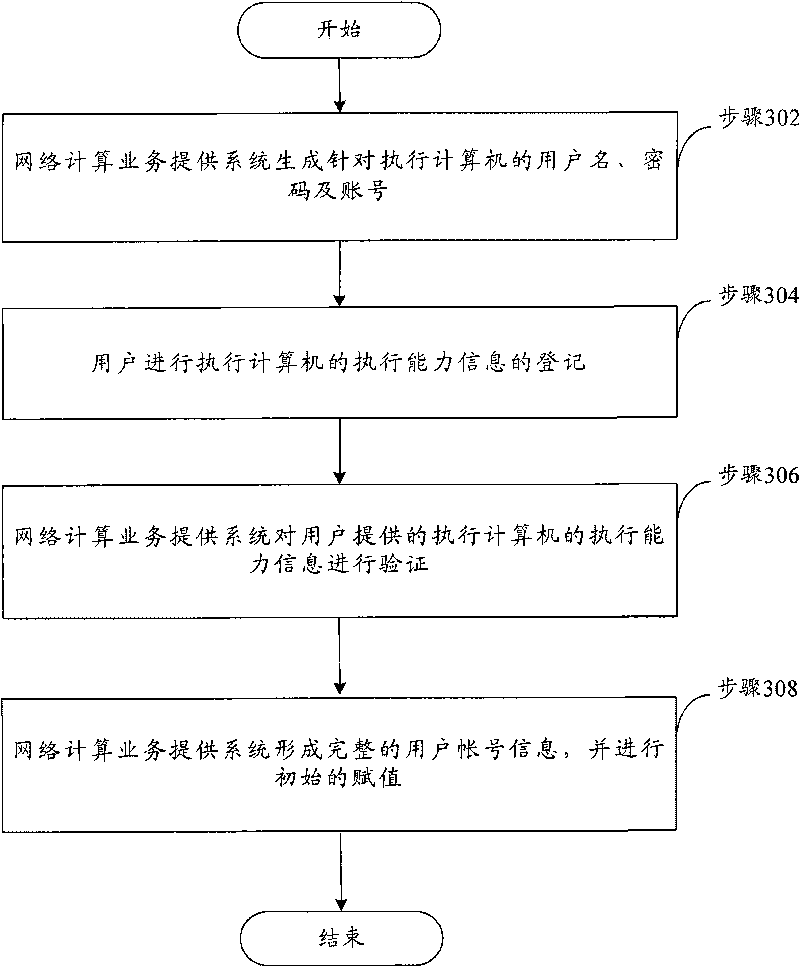
[0087] In this embodiment, the procedure for the user to register for the execution computer is introduced in detail. Figure 6 It is a detailed flowchart of user registration according to Embodiment 2 of the present invention, such as Figure 6 As shown, the registration process includes the following steps (step 601-step 607):
[0088]Step 601, the user logs in to the network computing service providing system (website), registers, and forms a user account and related user names and passwords. This account should be unique and credible, and it is used to settle the benefits that users can obtain;
[0089] Specifically, the identity of the user needs to be authenticated. It can be realized in a variety of ways, for example, users can open an account at the business outlet to form a username / password pair and register; or if the user is a legitimate user of the operator, they can cooperate with the operator to authenticate the user, etc.
[0090] Step 602, the user register...
Embodiment 3
[0097] In this embodiment, the procedure after receiving a task delivered by the network computing service provision system after the computer is logged in is described in detail.
[0098] Figure 7 It is a flow chart after performing computer login and accepting tasks according to Embodiment 3 of the present invention, such as Figure 7 As shown, the process includes the following steps (step 701-step 703):
[0099] Step 701. After the client program is installed, the owner of the execution computer logs in to the network computing service provision system when he is willing to provide execution resources. Specifically, he can log in in the following way: at any time after the execution computer is turned on, if the execution computer's The owner is willing to provide execution resources and log in to the network computing service provision system; the execution computer is turned on or restarted, and directly logs in to the network computing service provision system; or whe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com