Secrecy isolation hard disk and secrecy method thereof
A technology of hard disk and encrypted disk, applied in the protection of internal/peripheral computer components, instruments, electronic digital data processing, etc., can solve the problems of encrypted storage, lack of encryption and decryption function, hard disk data theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The security isolated hard disk and its security method proposed by the present invention are described as follows in conjunction with the accompanying drawings and embodiments.
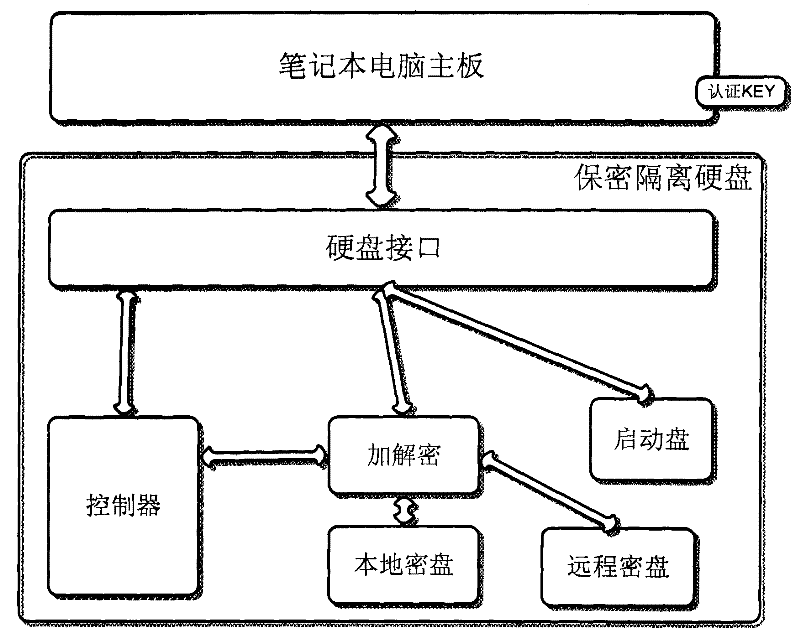
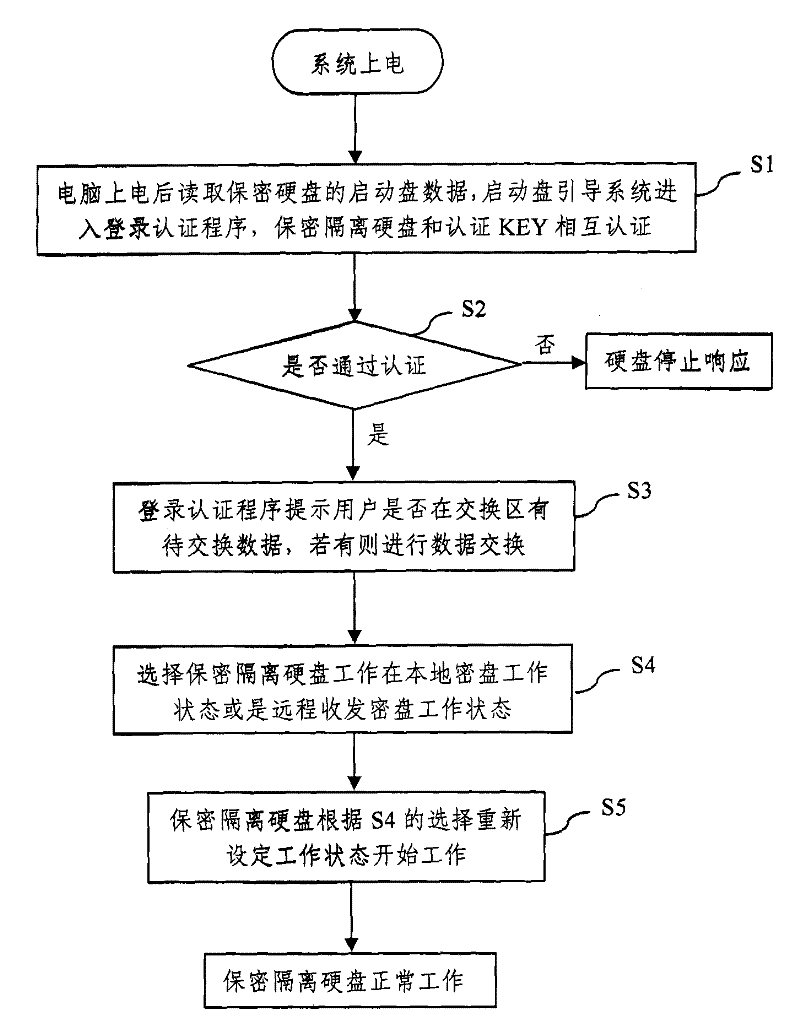
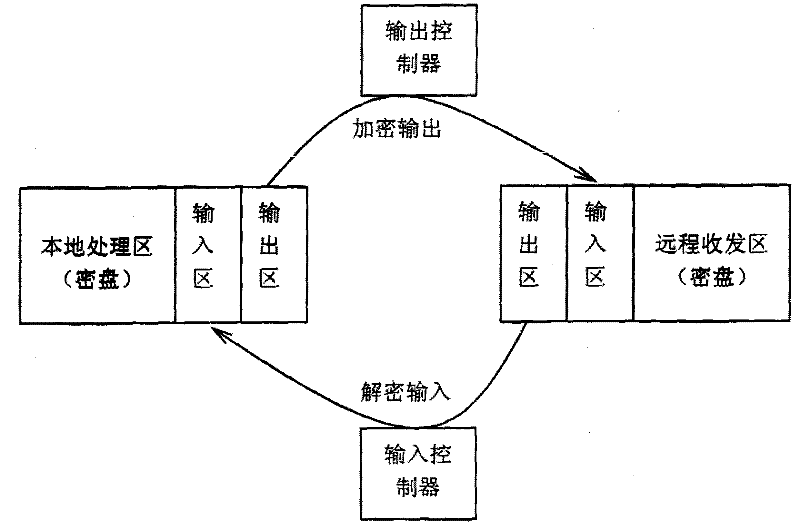
[0042] Such as figure 1 As shown, it is a structural schematic diagram of the security isolation hard disk of the present invention. Security isolation hard disk includes hard disk interface, boot disk, encryption and decryption module, controller, local encrypted disk, and remote sending and receiving encrypted disk. The hard disk interface is connected to the main board of the computer, and is used to provide the read / write interface of the external system to the hard disk, and the confidential isolation hard disk uses the SATA interface; the boot disk is connected to the hard disk interface, and the external system obtains the boot disk data through the hard disk interface to start the hard disk and the authentication program of the authentication key, the authentication key is generally a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com