Disk FDE (Full Disk Encryption) system and method
A full-disk encryption, disk technology, applied in the field of disk full-disk encryption systems, can solve problems such as data leakage, and achieve the effect of preventing leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
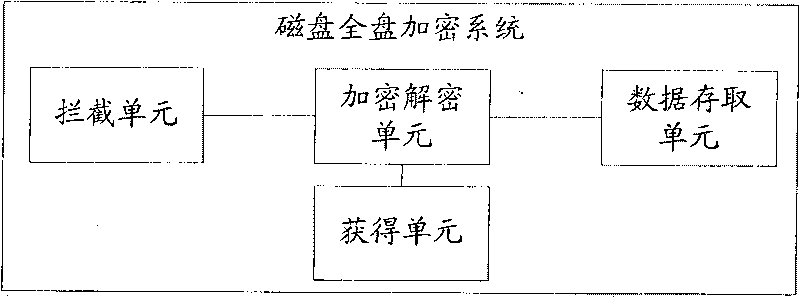
[0016] Embodiment 1: the system provided by this embodiment, see image 3 As shown, it includes: interception unit, acquisition unit, encryption and decryption unit and data access unit.
[0017] The interception unit is configured to intercept data read and write requests to the local disk.
[0018] The obtaining unit is used to obtain the verification item provided by the user.
[0019] The encryption and decryption unit is used to decrypt the file pointed to by the read request and encrypt the file pointed to by the write request through the verification object.
[0020] The data access unit is used to read the undecrypted file pointed to by the read request from the local disk, and decrypt it by the encryption and decryption unit; and write the file encrypted by the encryption and decryption unit pointed to by the write request to the local disk.
Embodiment 2
[0021] Embodiment 2: Based on the above embodiment 1, the processing procedures of each unit during the computer startup process are described in detail in the form of a flow chart.
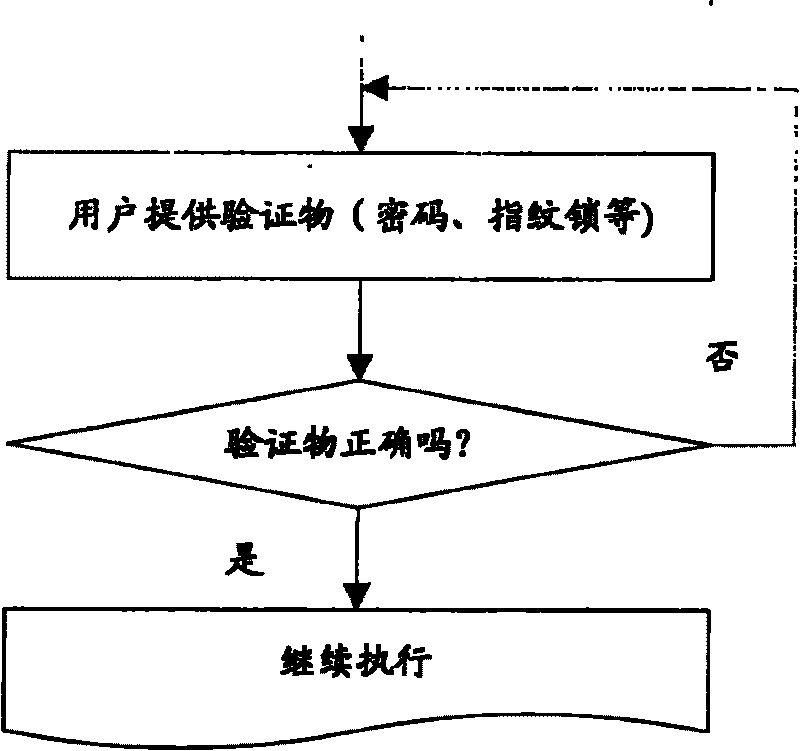
[0022] First, after the computer is started, the operating system program is loaded, that is, a read request is sent to the local disk, pointing to the operating system file. At this time, the interception unit can intercept the read request and prompt the user to input a password. In the password input stage, although it is similar to the appearance of the prior art, the main purpose of its verification password is not to prevent other people from using the computer, but to The password is used as a verification object for the subsequent decryption process.
[0023] Secondly, after the user inputs the password, the acquisition unit acquires the password and uses it as a verification item.
[0024] Afterwards, the data access unit reads the undecrypted operating system file from the local disk, ...
Embodiment 3
[0027] Embodiment 3, following Embodiment 2, the processing of each unit when the user stores video and audio files to the local disk after the computer starts up normally.
[0028] First, the user copies the video and audio files to the local disk, and the interception unit intercepts the write request at this time.
[0029] Secondly, the acquiring unit uses the password provided by the user when the computer is normally started as the authentication item.
[0030] Thereafter, the encryption and decryption unit performs a one-way hash operation on the verification object to obtain a hash value. And use the hash value to encrypt the unencrypted video and audio files with a preset encryption and decryption strategy (that is, a disk-level or file-level decryption method).
[0031] Afterwards, the data access unit writes the video and audio files encrypted by the encryption and decryption unit to the designated location of the local disk.
[0032] Finally, the encrypted audio a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com