Method for detecting cognitive user in opportunity spectrum sharing system
A spectrum sharing and cognitive user technology, which is applied in the detection field of cognitive users in the opportunistic spectrum sharing system, to achieve the effects of effective collision suppression, low probability of conflict, and efficient spectrum sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
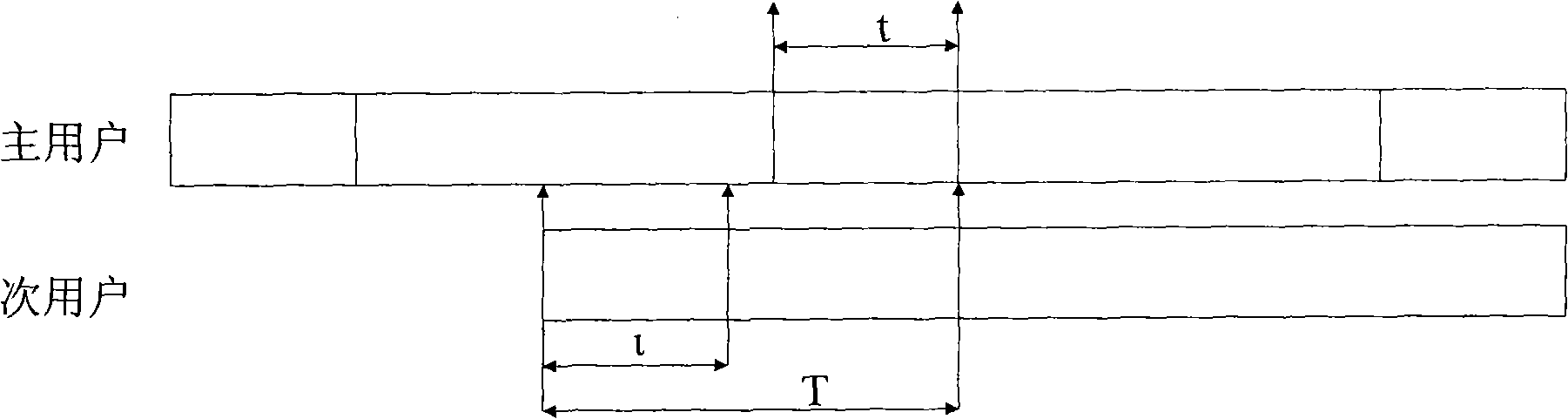
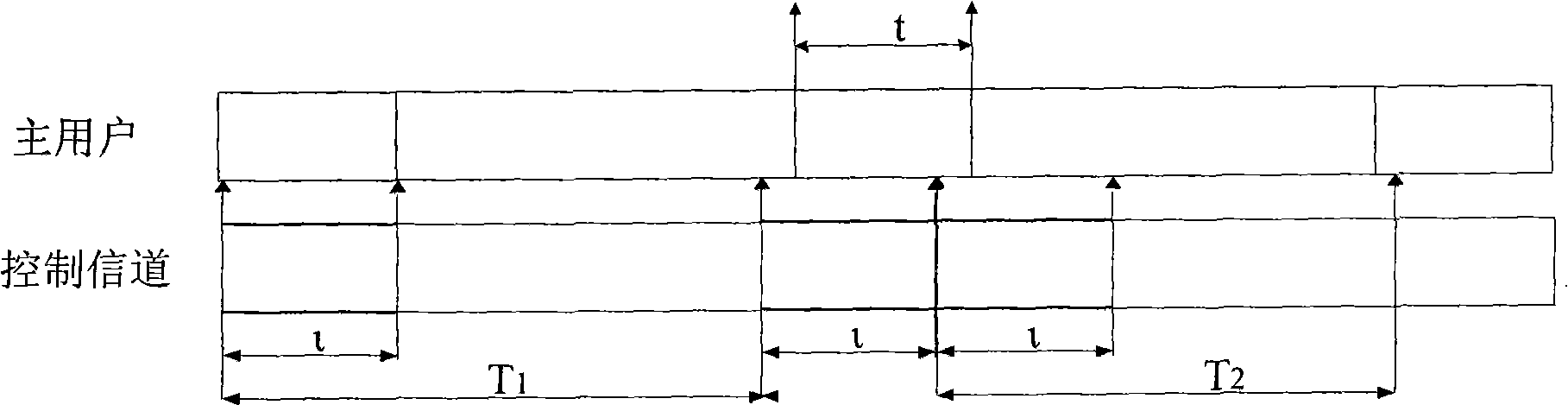
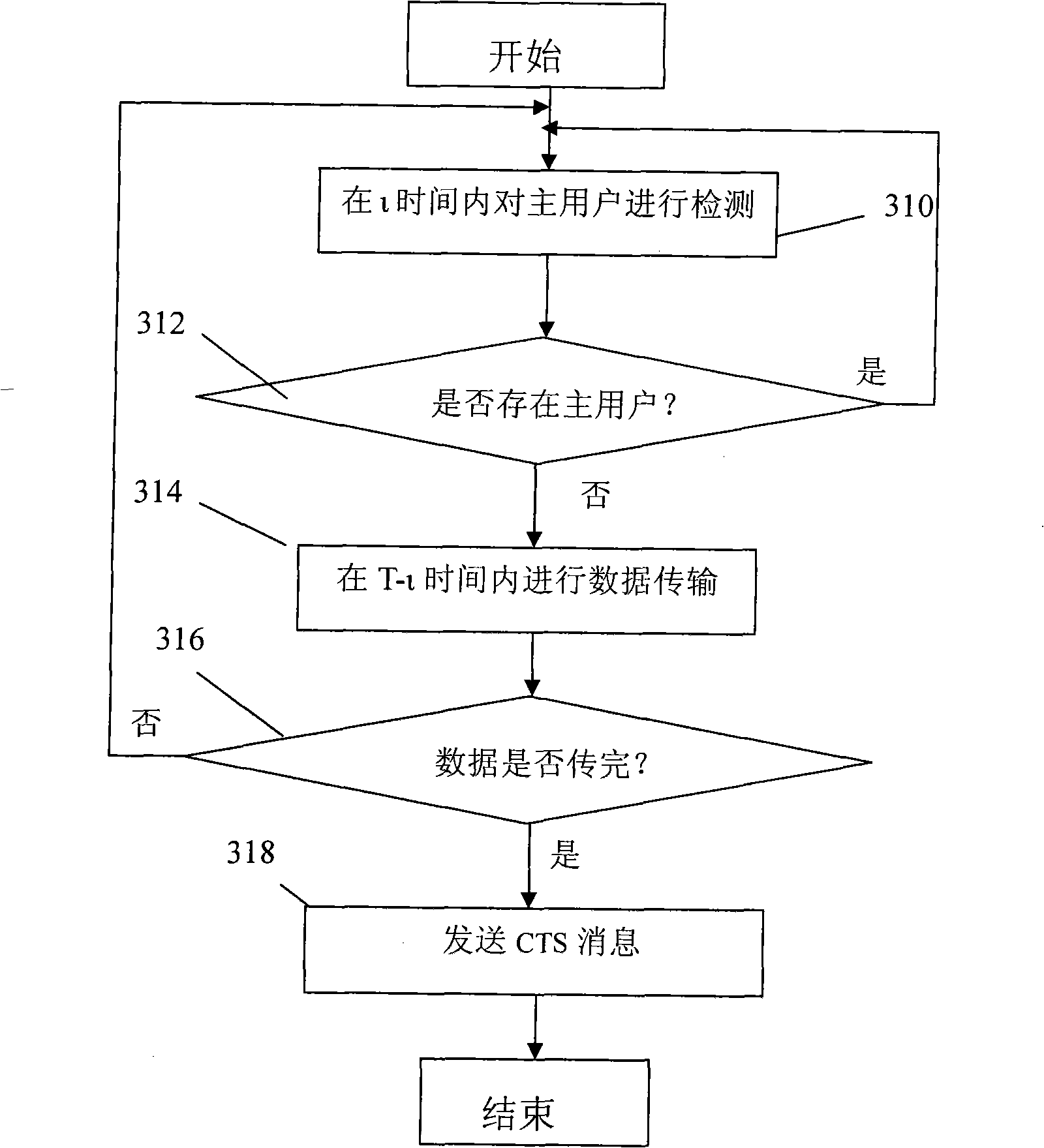
[0026] figure 1 It shows a frame structure example in which a single primary user occupies the authorized channel and a single secondary user detects the authorized channel and transmits data on the authorized channel. refer to figure 1 , the primary user's occupation of the authorized channel conforms to the exponential on-off traffic model. In this model, the primary user occupies the channel, that is, the average duration of opening is β 0 . The primary user does not occupy the channel, that is, the average duration of off is β i , the time taken by the primary user from occupying the channel to releasing the channel is t, which obeys the exponential distribution. Assuming that the frame length of the secondary user is T, t milliseconds before data transmission is used for detecting the channel of the primary user. When it is detected that the primary user does not exist, the secondary user data is transmitted within T-i time. During the data transmission process, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com