Security guarding method for automatically calling to inform customer of logining, transferring and paying of internet banking
A technology for online banking and customers, applied in telephone communication, electrical components, instruments, etc., can solve problems such as inability to recover money, money loss of bank customers, etc., and achieve the effect of avoiding losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0012] The method of the present invention will be described in further detail below in conjunction with the accompanying drawings.
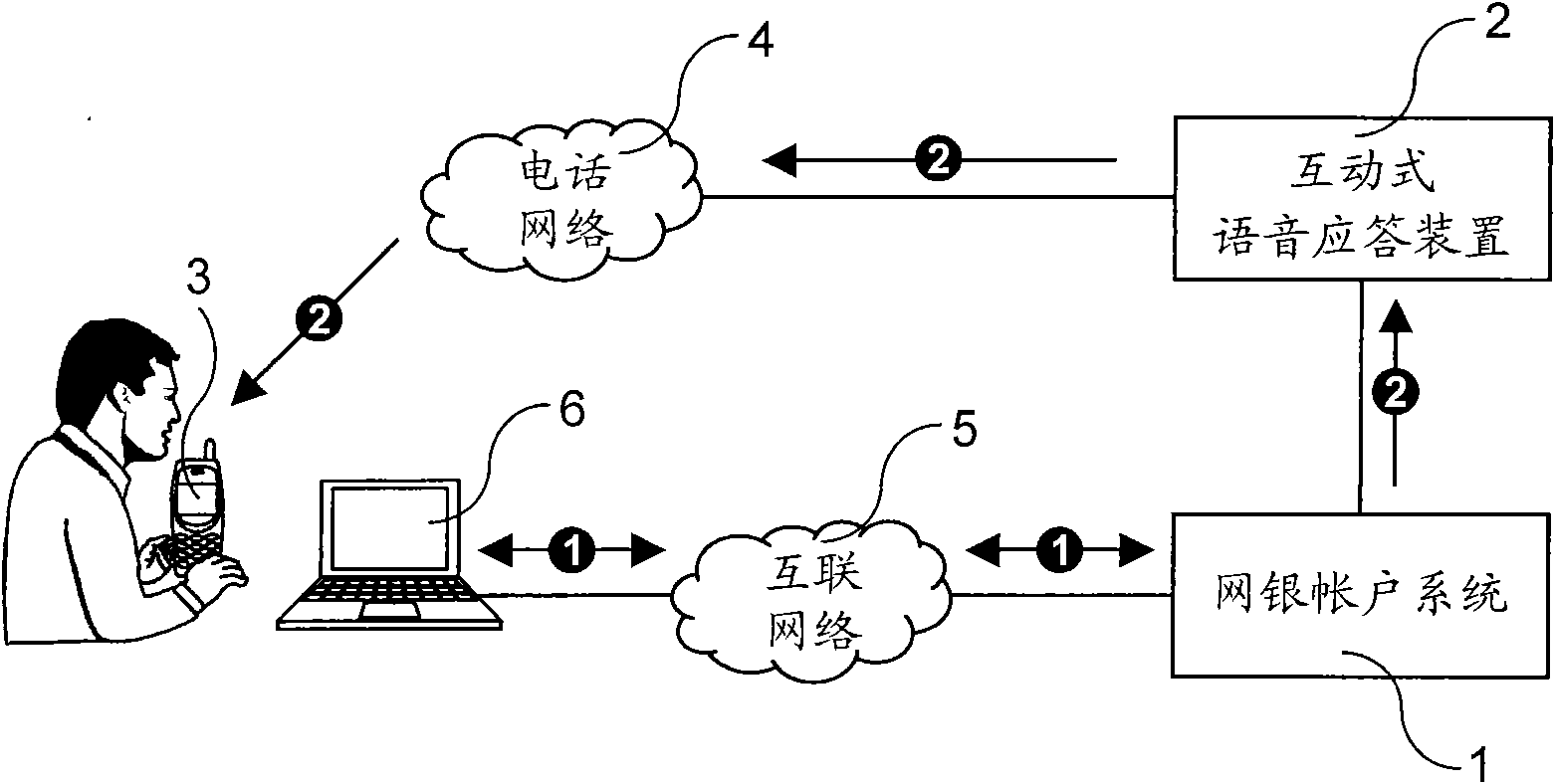
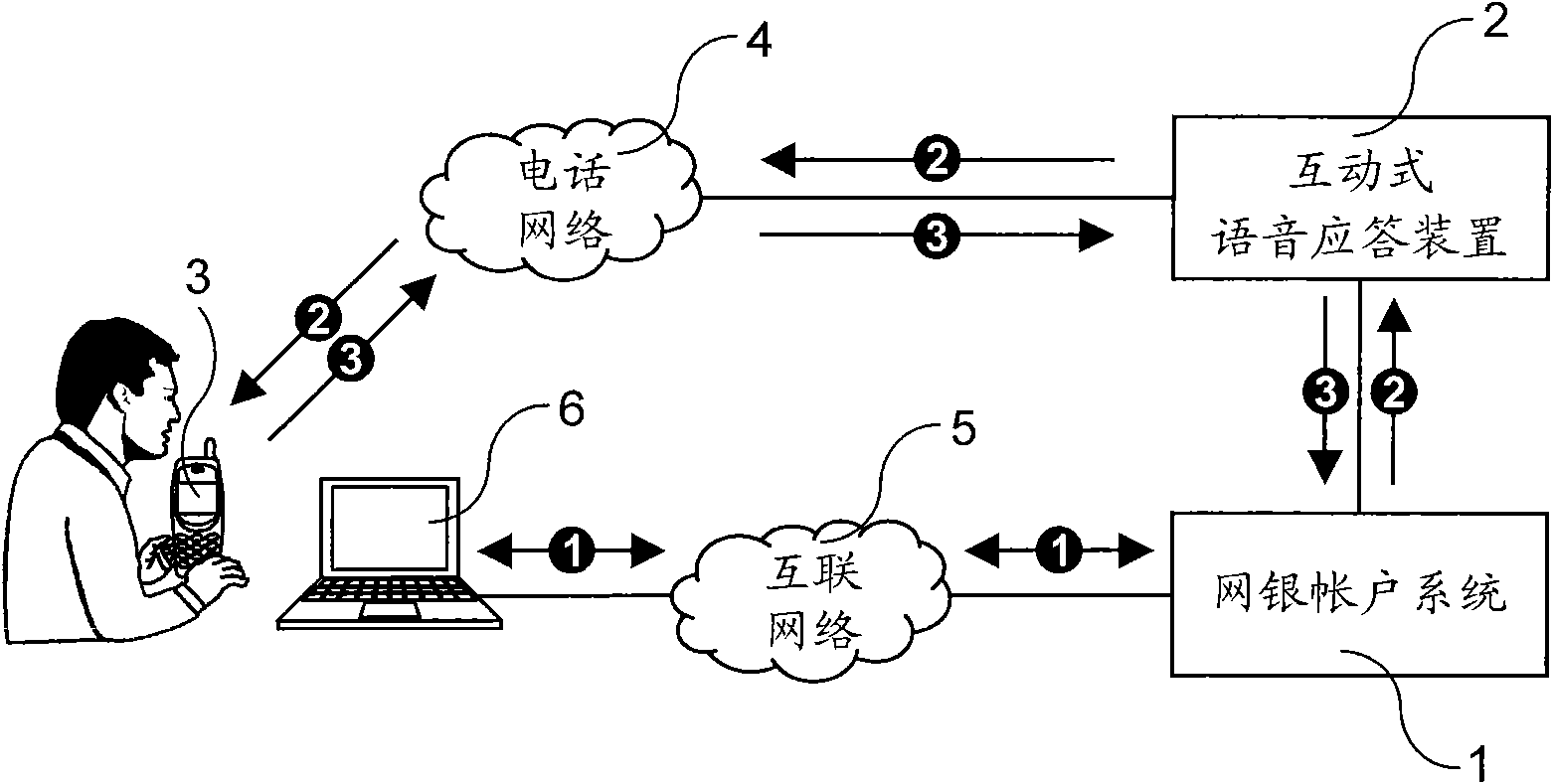
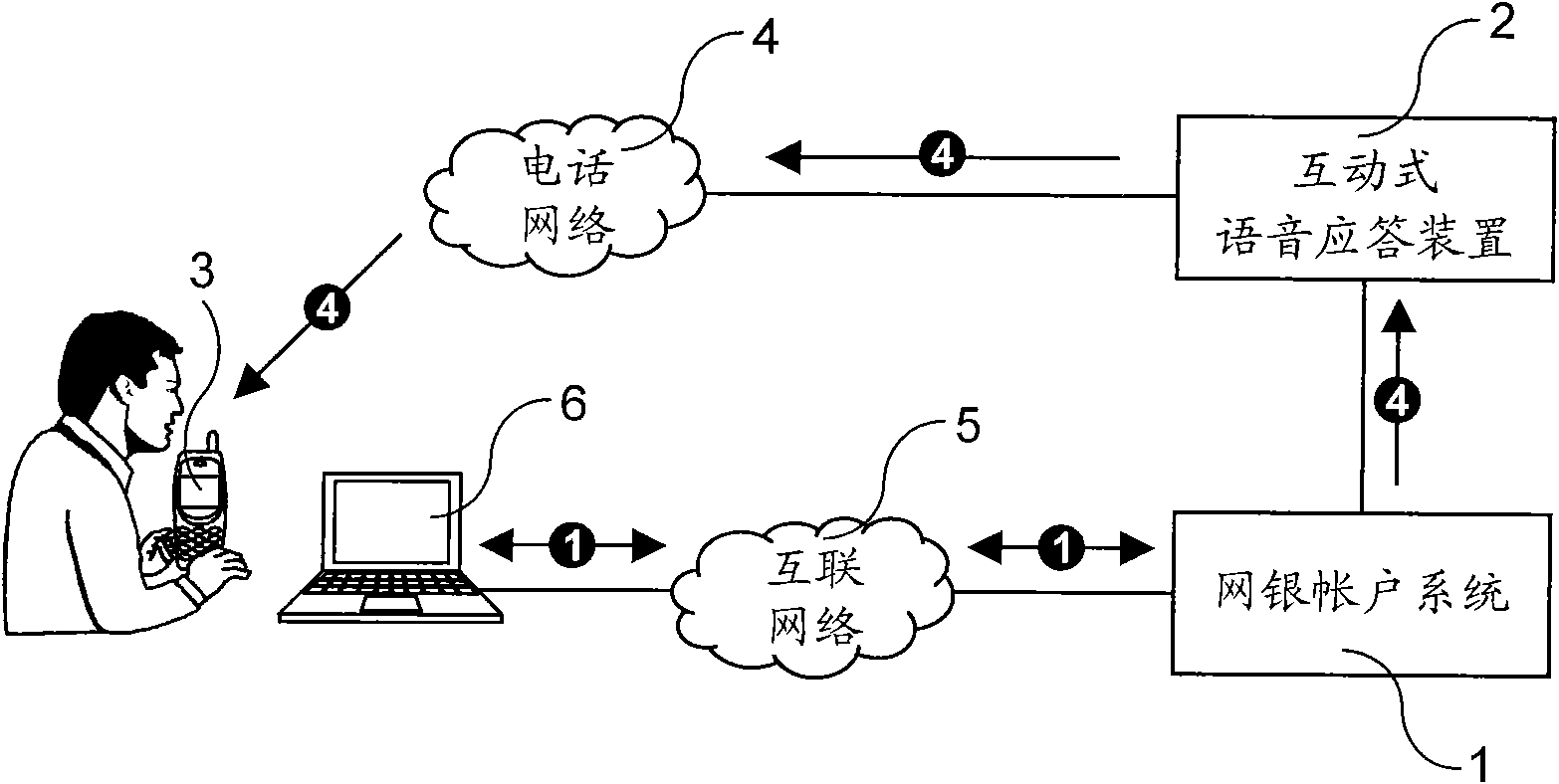
[0013] refer to figure 1 , figure 1 It is a schematic explanatory diagram of the steps of the online bank account security method of the present invention, which includes an online bank account system (1), an interactive voice response device (2) connected to the telephone network (4), a customer's mobile phone (3), Connect to the Internet terminal (5) of the online bank account system (1) through the Internet (6), wherein, the online bank account system (1) is provided with each customer's online bank account and records the mobile phone (3) of each customer phone number, and has a monitoring security program for monitoring the account activities of each online bank account. When the monitoring security program finds that the account activity of a certain online banking account is subject to monitoring, the monitoring security program will pas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com