File encryption method
A technology of file encryption and encryption algorithm, which is applied in the direction of instruments, electronic digital data processing, digital data protection, etc., can solve the problems of not being able to prevent piracy, unfriendliness, etc., and achieve the effect of eliminating illegal copying and piracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] A specific embodiment is listed below, which is only a specific application of the above principles.
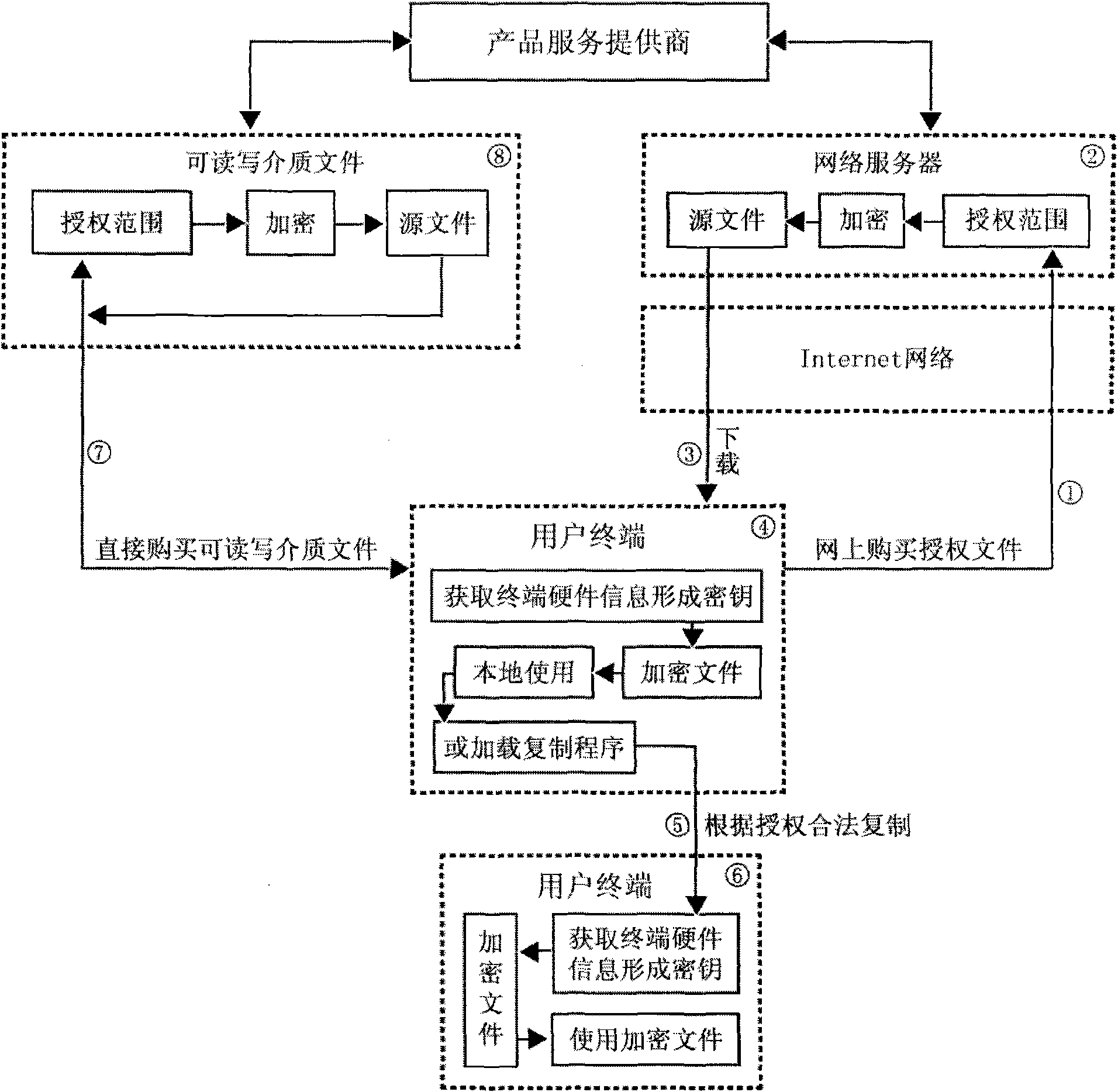
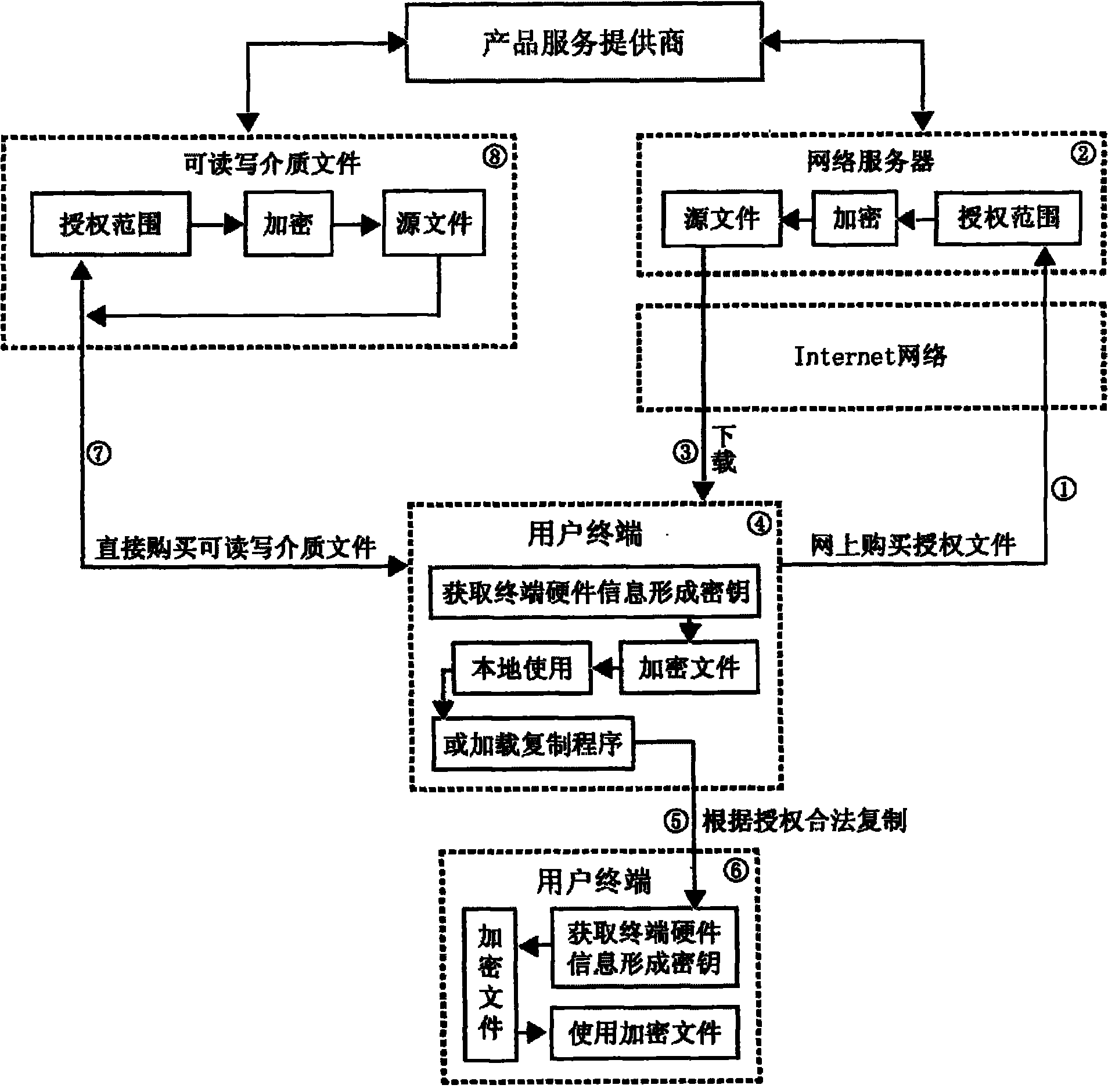
[0014] The present invention is composed of terminal, Internet, server, encryption program, source file, downloading and copying tool. Its specific workflow is:
[0015] Such as figure 1 As shown, the user using the terminal directly sends a request for the permission to use the source file (including the use time and frequency, etc.) through the Internet, and pays the corresponding fee (see figure ①). After the network server confirms the above information, the authorization permission is encrypted. The program is directly written into the source file (see figure ②), and provided to the user to download to the terminal.
[0016] After the encrypted file is downloaded to the terminal (see figure ③), the encryption program will automatically calculate the hardware information of the terminal, generate a unique machine code, and register it in the encrypted file (see f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com