Dynamic digital copyright protection method based on dual identity authentication
A technology for digital copyright protection and identity authentication, applied in the field of information security, can solve the problems of not supporting physical space migration, digital home network copyright protection not being extended, and inability to locate the identity of copyright users, and achieve the effect of dynamic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] Embodiments of the present invention will now be described with reference to the drawings, in which like reference numerals represent like elements.
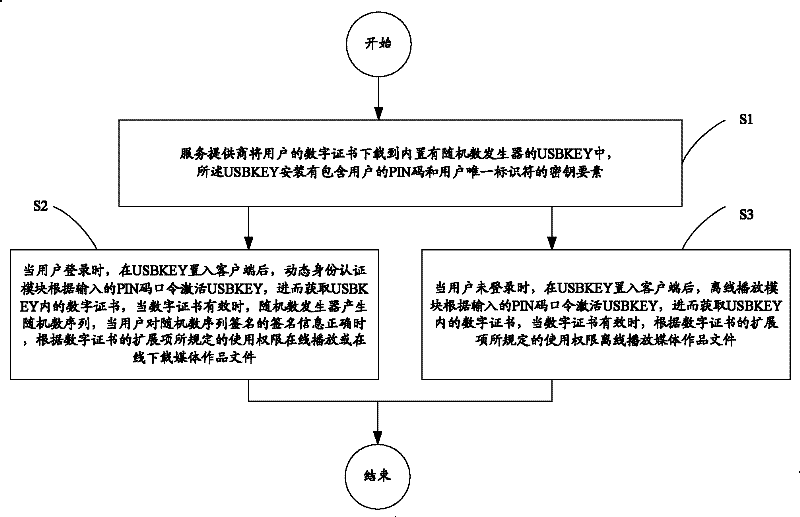
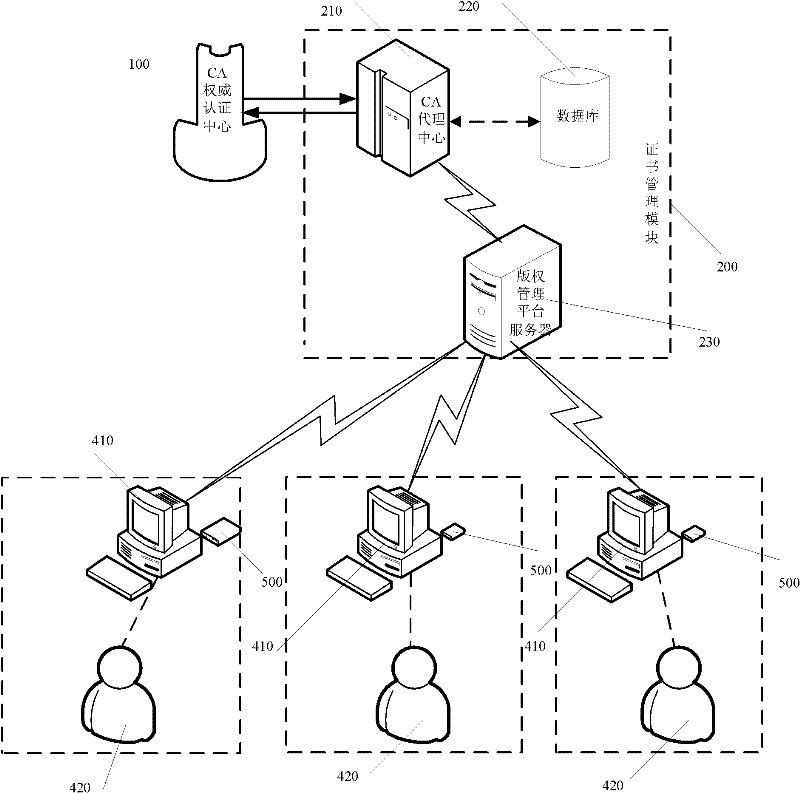
[0027] refer to figure 1 with figure 2 In this embodiment, the dynamic digital copyright protection method based on double identity authentication includes the following steps:
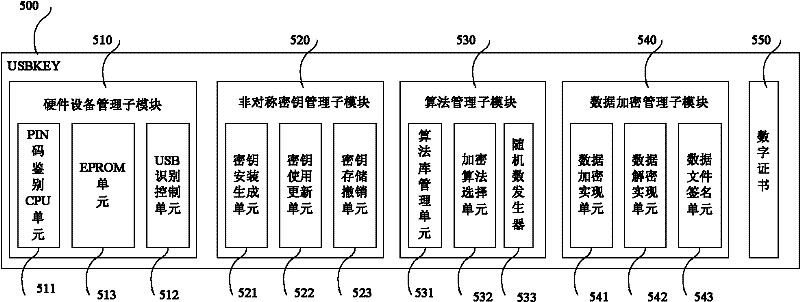
[0028] Step S1, the service provider downloads the user's digital certificate to the USBKEY (smart password key) 500 with a built-in random number generator, and then turns to step S2 or step S3;
[0029] Step S2, when the user logs in, after the USBKEY 500 is placed in the client (user PC) 410, the dynamic identity authentication module activates the USBKEY 500 according to the input PIN code password, and then obtains the digital certificate in the USBKEY 500, when the digital certificate is valid , the random number generator generates a random number sequence, and when the signature information signed by the user on the random number seque...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com